Since its inception, Perception Point has been scanning billions of emails, URLs and files every week. Most of the time, Perception Point clients already have at least one email security solution in place.
Whether they are using on-premises Exchange and an SEG vendor (such as Proofpoint, Mimecast, Symantec) or the built-in security capabilities of Office365/Gmail Workspace, they all still see phishing and malware reach their end users. In the best case scenario, they get a report by a good employee. But in some cases what triggers the SOC team is an alert coming from the endpoint solution. This means a payload already reached the users’ computer and maybe even opened.
In this article we list a few (not all) of the most-used techniques by hackers to bypass email security solutions. We hope this helps people understand better how to prevent ransomware, phishing, and other cyberattacks.
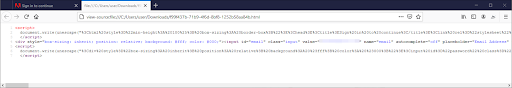
Problem 1. Login forms hidden inside local web pages
Not able to detect phishing scams and credential theft attempts that use a login page inside a local html page attached to the email instead of hosting the login page online.
Why it’s hard for solutions to detect?
Because there’s no suspicious link inside the email, all engines based on reputation (URL reputation, domain legitimacy and so on) are not valid. Also solutions such as URL rewriting in Office365 will not help.
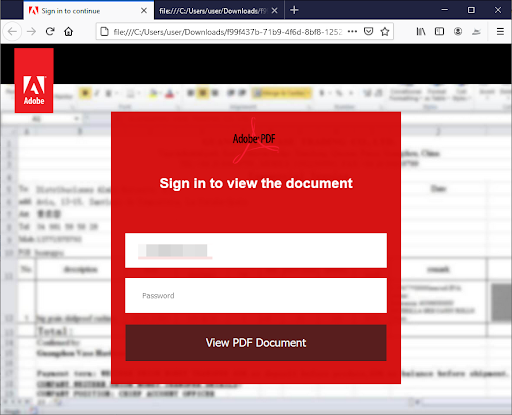


They don’t need to worry about hosting a phishing site online. They’re not afraid that their site will be shutdown. They just send an html file, and wait for a click, the page is then rendered locally on the victim’s computer, only after the attacker writes his or her credentials in the fake login page, there will be a JavaScript code (usually obfuscated) that will upload this information online straight to the attackers’ hands.

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERTS
- Utilize AI-driven anomaly detection
Deploy AI models that establish a baseline of normal communication patterns within your organization. By doing this, the system can flag any anomalous email that deviates from established patterns, such as a sudden email from a third-party vendor asking for financial details, even if it appears to be coming from a legitimate source. - Leverage deep-learning-based image recognition
Phishing attacks increasingly use images to bypass text-based filters. Implement deep-learning-based image recognition to scan for brand logos, login forms, and other visual elements that are commonly used in phishing attempts. This can be particularly effective against sophisticated attacks mimicking corporate portals. - Implement robust domain-based message authentication protocols
Strengthen your email authentication by implementing SPF, DKIM, and DMARC with stringent policies. Regularly monitor your DMARC reports to identify unauthorized use of your domains. Additionally, consider implementing BIMI (Brand Indicators for Message Identification) to provide an added layer of visual trust. - Implement machine learning-based file fingerprinting
This approach compares incoming attachments against a vast repository of known benign and malicious files using machine learning. Even if a malicious file has been slightly altered to evade traditional detection, file fingerprinting can still identify it as a variant of a known threat. - Implement security awareness training
Run training sessions focused on emerging threats and recent phishing techniques. Use real-world examples and simulations to keep employees sharp and reduce the chances of them falling for sophisticated phishing attempts.
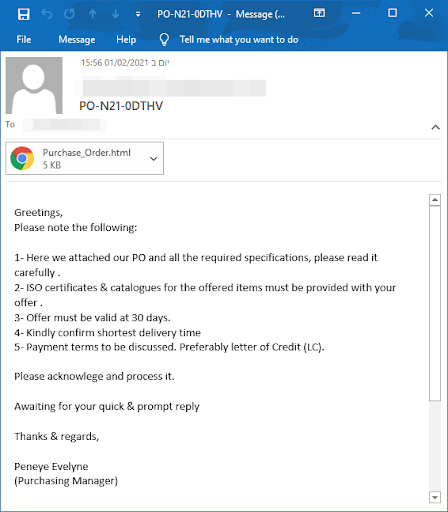
Problem 2. Malware hosted on file-sharing services.
Not able to scan malware hosted on OneDrive, Google Drive and other file-sharing services.
Why it’s hard for solutions to detect?
There are a lot of file-sharing services, and most of them offer free packages, giving an attacker a chance to upload his payload for free. File-sharing services work by using link sharing, where essentially they give you a link (coming from their own, good reputation domain).
Then the attacker crafts the email and puts the link inside. The solutions then scan the URL, and there is nothing suspicious inside, usually the link will lead to the legit website, requires user to click on a special “download” button, so the site itself is safe (it’s the sharing service website), but if you download the file, you’re screwed.
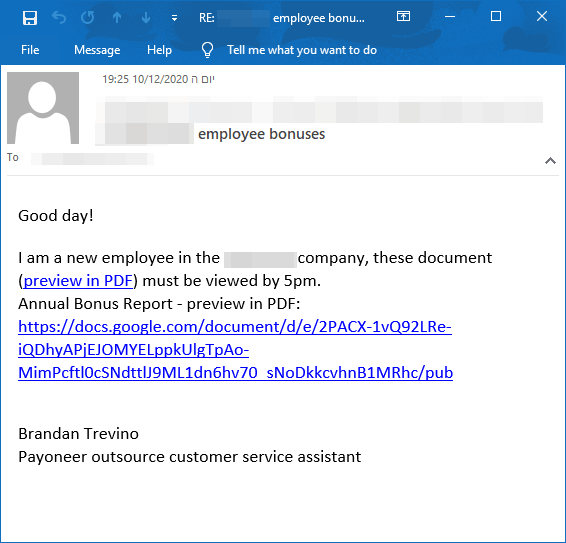
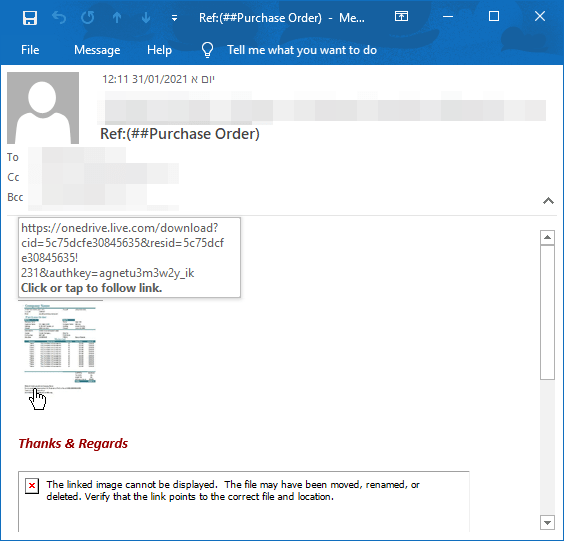
Problem 3. Spotting Spear Phishing.
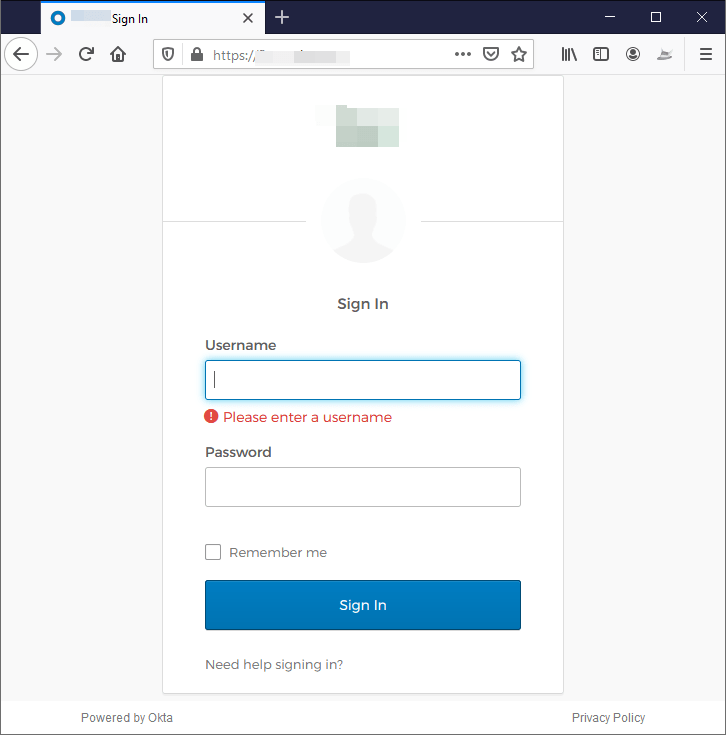
Attackers nowadays will try to trick users into thinking they landed on a well-known internal company portal. If an attacker finds the 3rd-party services a company uses, he or she can easily mimic it and create fake versions of it.
Why it’s hard for solutions to detect?
This is a highly effective technique. Since employees expect to see these email types as internal only, they won’t pay too much attention to signs of phishing.
Some company portals are even reachable from the internet—making hackers’ lives even easier to spoof them. In this example, we can see a fake Okta login page. It contains all visual elements and the company’s logo (and it’s even SSL encrypted), just waiting for the user to enter his or her credentials (an action done several times a day). A large portion of phishing campaigns sent to companies are actually an impersonation of their own brand.
Legacy solutions might be good at detecting the generic kind of phishing, but highly targeted and tailor-made attacks will likely go undercover to user’s mailbox.
Related content: Read our guide to email attacks.
Problem 4. Blacklisting email security vendor IP addresses
Hackers are blacklisting email security vendors’ IP addresses. When hackers create phishing websites, either manually or with a prepared Phishing Kit. They are well aware that their target is highly fortified, and they assume email security solutions will scan their website before it will reach the end user.
Why it’s hard for solutions to detect?
By fingerprinting the different email security solutions, a hacker can understand what the IP addresses are of the email security provider services. Once fingerprinted, they can easily blacklist their IP.
Problem 5. Can’t Detect ATO
No ability to know if dealing with a compromized third-party vendor.
Why it’s hard for solutions to detect?
It is very hard to detect ATO because the email is coming straight from the vendor’s IP and the actual mailbox. The attacker then reads all email communication, waiting for the right time to inject a message where he sees the request for fund transfer. He will usually reply back with a signature that’s identical to the vendor’s and will ask for you to transfer money to other bank accounts.

Email attacks have evolved to bypass traditional defenses. They now require organizations to set up
protection, not only at the gateway, but also beyond it. Every business needs to deploy the right
combination of technology and people to have effective email protection. To make sure your organization stays attack-free, it’s important to find a tool that dynamically scans every single email for all known and unknown threats before being delivered.
At Perception Point, we stop malware, phishing attacks, logical exploits, hardware vulnerabilities, macro-based attacks, ransomware, APTs, spear phishing, and N-day and zero-day attacks.
Related content: Read our guide to email security solutions.
– Problem 1. Login forms hidden inside local web pages
– Problem 2. Malware hosted on file-sharing services
– Problem 3. Spotting Spear Phishing
– Problem 4. Blacklisting email security vendor IP addresses
– Problem 5. Can’t Detect ATO
























