Up in the cloud
In recent years the increased reliance on cloud collaboration channels has incentivized cyber attackers to exploit a new threat landscape. With many enterprises now using cloud-based applications to host their systems and workflows, the attack surface only continues to expand.
Perception Point’s Incident Response (IR) team understands the depth of attacks and what to look for in order to identify them. Comprised of cybersecurity experts on high alert 24/7, our IR team keeps the pulse on novel attack trends and works in real time to prevent them. Our IR team recently investigated a malware campaign targeting OneDrive, caught by our advanced threat detection for cloud storage.
OneDrive joins the RAT attack pack
In this blog post, we review one of the latest malware examples that we caught.
An njRAT was sent to one of our clients on OneDrive. Because our advanced threat detection platform scans 100% of our customers including URLs, files and more, regardless of a file’s perceived threat level, we were able to catch the RAT, or Remote Access Trojan.
How it works
The malware was delivered in a VisualBasic script file. Once executed, the RAT retrieves the data from the file hosted on the site and executes that data. The RAT then creates a folder in the user’s ProgramData folder and applies persistence by creating a scheduled task that runs every three minutes, executing the malware.
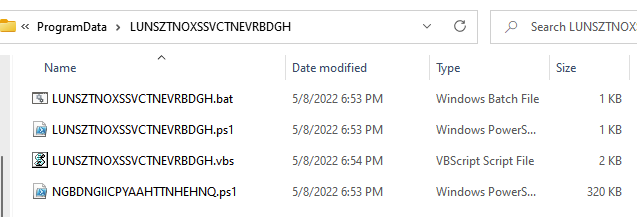
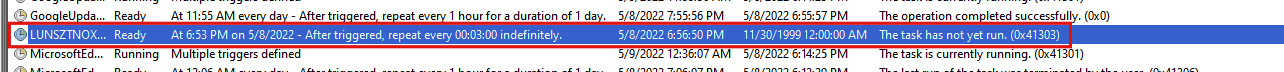
The RAT then injects itself into aspnet_regbrowsers.exe, which is a legitimate process signed by Microsoft:
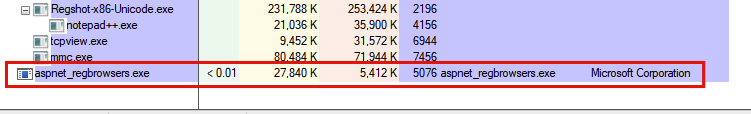
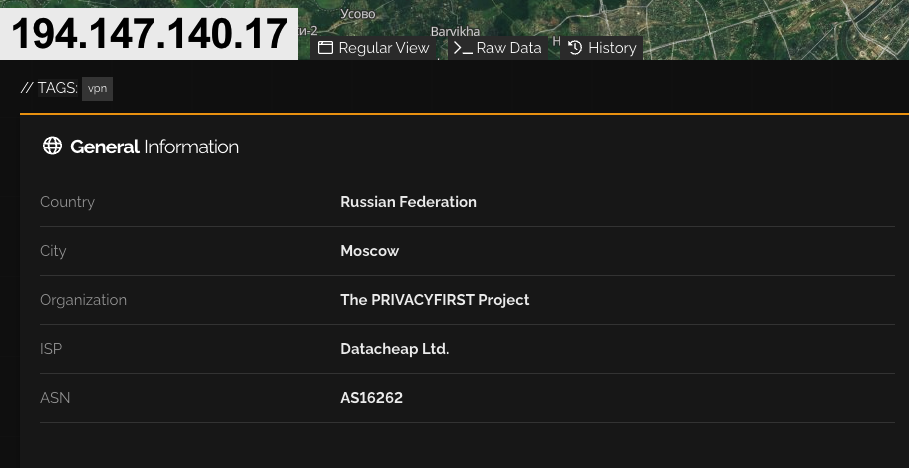
Last but certainly not least, the RAT eventually connects to the IP address 194.147.140.17 on port 9400;
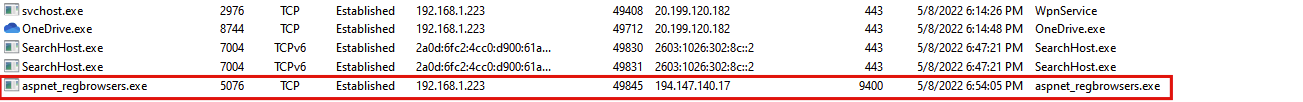
Our IR team tracked the IP address to Russia, despite displaying as a VPN:
Why we care
Catching a RAT before it can corrupt a client’s OneDrive is significant. If left uncaught, a RAT can enable bad actors to not only gain access to the victim’s data and files, but also their local hardware. This means the attacker could gain remote access to the victim’s camera, microphone, and even track keystrokes. Attacking OneDrive is just the vehicle to gain access to a user’s entire computer.
For our IR team, preventing an attack with such potentially harmful ramifications is always a win. But the real jackpot of this attack was the host site itself. The RAT was obfuscated inside a powershell script hosted on this site: https://corpernaija(.)com/xv/Serverr(.)txt. If you review the site’s directory, you will find many more files used for attacks hosted on the site: https://corpernaija(.)com/xv/.
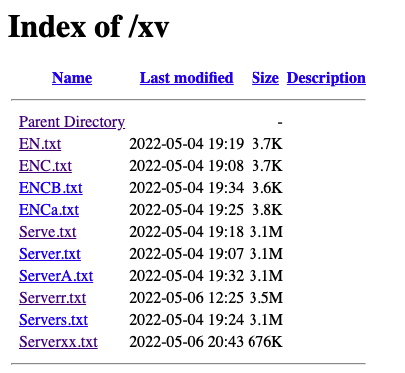
What is so unique about this site is that the attackers use it to host a full folder of malwares. Because our RAT attack was only uploaded in the past month, we can see that the site is active. Additionally, the site itself appears to be legitimate, but due to its content it was likely exposed to a Local File Inclusion (LFI) vulnerability, used by the attackers to upload malicious code to their site.
Our IR team posted the site to a threat intelligence database (VirusTotal), giving the site a bad reputation and warning others of its malicious content. We also added the information from the site to our threat intelligence, strengthening our detection platform to protect against more malware attacks in the future.
For more information on securing your cloud-based storage and collaboration channels, please refer to our resources page here.
A special thanks to Igal Lytzki and the Perception Point IR team for their research.






























