API & Data Security with Perception Point
Perception Point’s easy-to-deploy API ensures data security and prevents the transmission of malicious files, URLs and social-engineering attacks through your in‑house communications, cloud collaboration apps, and services. Utilize the proven, state of the art technology of Perception Point to safeguard all entry points from content-based attacks.

A Tailor Made Solution for Your Specific Data Security Needs
As businesses evolve, they need customized solutions to support their day-to-day operations. And quite often, this requires development of internal tools and cloud services that share content with customers, suppliers and between employees. However, the flip side of these apps’ functionality is the lack of data security.
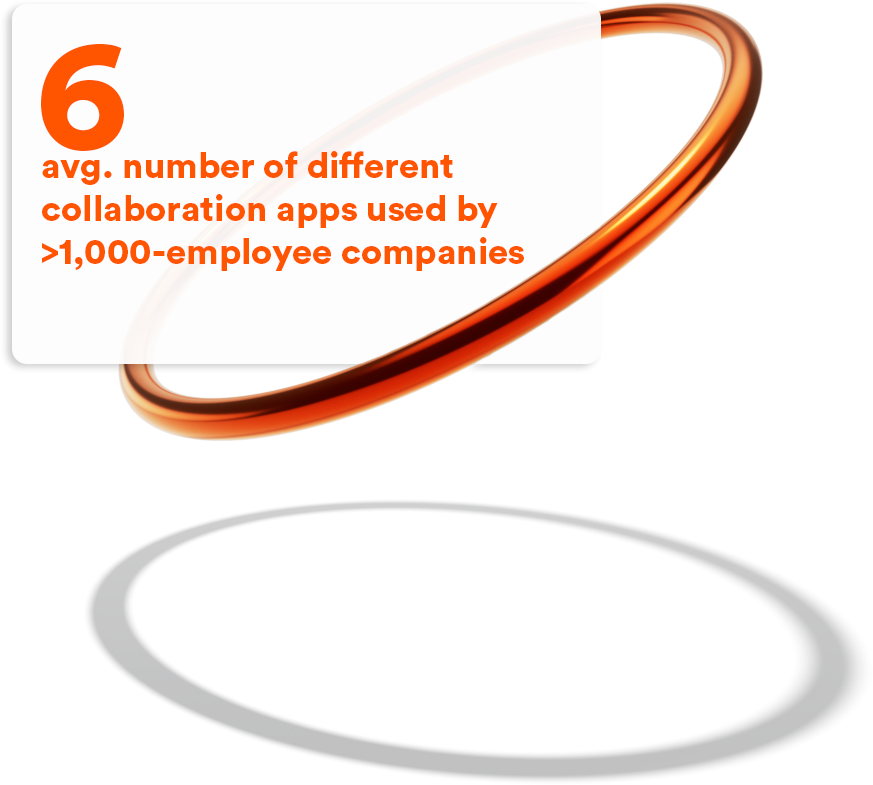
With companies reporting the use up to 20 different apps in a single enterprise, leaving these apps unmonitored is like sticking your head in the sand, and a data security breach is only a matter of time.
The Data Security Analyzer
In addition to our API, you can gain access to our data security Analyzer – a unique service that allows you to independently upload suspicious content on a case-by-case basis. Received an unfamiliar file or a suspicious link? Simply “Drag & Drop” into the Analyzer and receive a clear, binary verdict in up to 30 seconds.


Complete Your CASB with Content-based Security
CASBs are designed for monitoring access and data leakage, and enforcing policies that will ensure controlled exposure of private and sensitive organizational information. They are especially relevant for customized, in-house apps since they monitor traffic and can be cannel agnostic.
However, CASBs are not designed for threat detection, including the detection of malicious files, URL or social-engineering attempts, nor are they able to provide forensics on any such attacks. If an organization is only reliant on a CASB for their in-house apps’ data security, a content-based attack is GUARANTEED.
This is why we developed an easy-to-deploy API which integrates with any customized app and service. With Perception Point solution you can dynamically scan any file and URL to ensure unprecedent protection, without compromising on user experience that your app was built to support.
Our API can interact with any communication and collaboration you have developed.
Deployed in a single click, our solution can integrate with any popular cloud app without creating any overhead to your IT employees.
We use al engines on all content, either from an off-the-shelf app or in-house built tool, to provide max protection against any attack and ensure data security.
Highly designed viewer allows a centralized view of all protected applications. Different views are customized to serve different personnel: the CISO, IT Managers and Security Analysts.
Proven Results
See Perception Point in action!
Other Related Products
Easily combine our email security platform with these other unique products from Perception Point
Full coverage against any email-borne attacks, including phishing, BEC, malware, and APTs.



Cloud Apps
Stopping any content-based attack via any of your cloud-based collaboration apps in real-time.



Cloud Storage
The only solution to provide cutting-edge technology to stop malicious files and URLs from being uploaded or downloaded to your cloud storage.




























