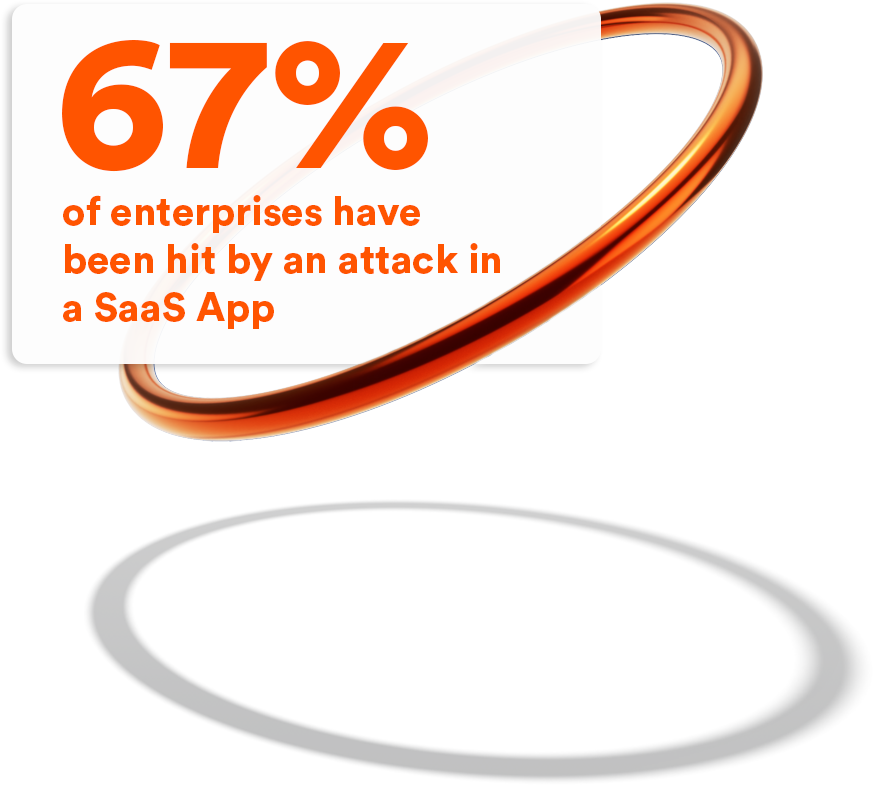
Cloud Apps & File Sharing Security with Perception Point

As the exchange of files & URLs moves to new channels, so does the potential for malicious content.
CRM Apps, Enterprise Social Networks, Shared Virtual Workspaces – they are all the new must-haves in the digital transformation era.
However, they pose a great threat. Perception Point’s next-gen cloud-based solution scans content exchanges in real-time to block every level of threat, from APTs to phishing, without creating delays for cloud apps and file sharing security.

Cloud Apps &
File Sharing Security
Today’s modern, data-driven enterprise relies on the collaboration of data as a key pillar to deliver its services to the end user.
Cloud & File Sharing Applications, such as MS365 apps, Zendesk, Salesforce, HubSpot, and any of the other hundreds of apps out there, are great in sharing content and data.
Yet, this is a double-edged sword: they are also great in spreading malware.

Landing Page Malware
Attacker posts a request on an enterprise’s landing page that includes a malicious link. Once logged into the system, an employee accidentally clicks on the embedded link and initiates the malware.
Social Networks Post
An attacker posts a malicious phishing link in a company thread to share with specific employees in the Financial or Legal departments.

Sync
& Share
A supplier (unknowingly) sync a malicious file with a shared folder used to transfer files via a shared virtual workspace where documents on a deal is finalized.
Complete your CASB with Cloud Apps and File Sharing Security
Cloud and File Sharing Apps are already being used by attackers. And it’s not going to stop in the upcoming years. It’s time for you to take action and protect all entry points to your organization from content-based attacks. Unlike CASB that focuses on monitoring access and data leakage, and enforcing policies, we take a look inside the data to make sure it is safe.
Simply think about it like it’s your email. It’s really the same.
Perception Point’s Cloud Apps & File Sharing security solution takes the advanced detection capabilities used today only in email and expands it to each and every cloud app you might use in your organization.
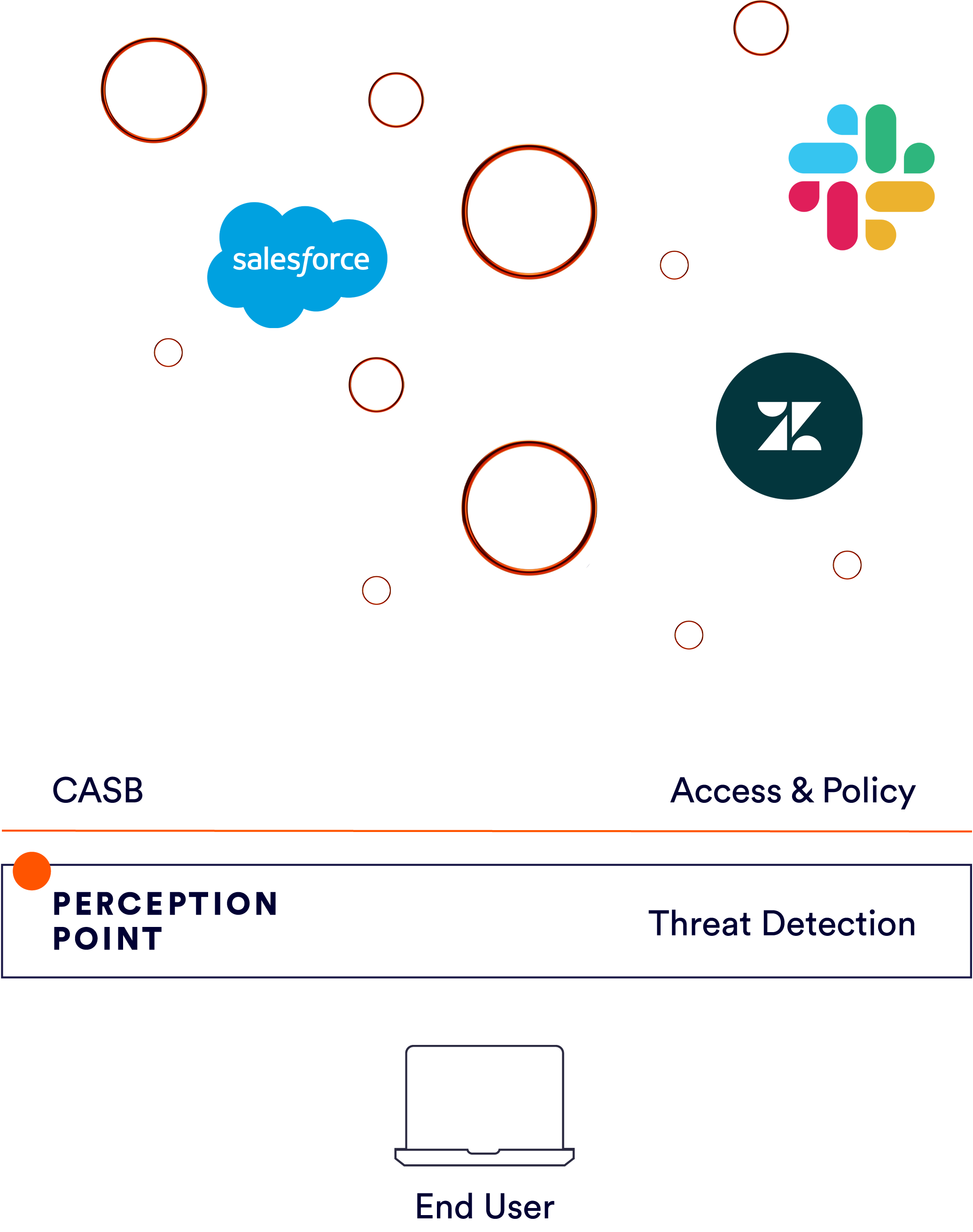
Whether it’s a CRM, Social Network or Shared Virtual Workspace app, we can scan it. No caveats, no restraints.
Deployed in a single click, our solution can integrate with any popular cloud app without creating any overhead to your IT employees.
Cloud-native solution enables unprecedented scan time, allowing your employees to work at the pace they need to deliver best business results.
Highly designed viewer allows a centralized view of all protected applications. Different views are customized to serve different personnel: the CISO, IT Managers and Security Analysts.
Proven Results
More and more companies choose Perception Point Advanced Threat Prevention
Case Study
-
Global Financial Services Firm Replaces Proofpoint A global financial firm faced challenges with preventing phishing attacks from reaching their users. Despite investing in security awareness training, the security leadership was concerned about phishing emails that were successfully bypassing their Proofpoint deployment.
-
Enhancing Microsoft Email Security to Prevent Advanced Phishing & BEC Attacks Perception Point’s Advanced Email Security for Microsoft 365 helps a global food distributor achieve seamless and comprehensive protection against advanced email-borne attacks including phishing and BEC.
-
Red Bull Augments Microsoft EOP to Prevent Attacks When given the opportunity to put our solution up to the test, Perception Point’s Advanced Email Security proved to be a cut above the rest.
-
Flow Control: Manufacturing Leader Selects Perception Point to Optimize Their Advanced Threat Protection With Perception Point’s consolidated solution protecting the customer’s email, browser, and Microsoft 365 suite, Flow Control Group benefits from simple deployment and holistic management capabilities.
See Perception Point in action!
Other Related Products
Easily combine our email security platform with these other unique products from Perception Point
Cloud Storage
The only solution to provide cutting-edge technology to stop malicious files and URLs from being uploaded or downloaded to your cloud storage.
Full coverage against any email-borne attacks, including phishing, BEC, malware, and APTs.
API
Integration with any other application where files or URLs are exchanged. Custom development per client needs.


























