In a phishing campaign dubbed “Uncle Scam,” threat actors impersonate United States government agencies to deliver fake tender invite emails to hundreds of American enterprises.
Prevented by Perception Point’s Advanced Threat Prevention platform, Perception Point security researchers investigated this campaign, uncovering advanced interactive kits, LLMs, and the abuse of Microsoft’s Dynamics 365 marketing platform. This blog explores how attackers created this highly realistic, multi-step phishing operation.
From Uncle Sam to Uncle Scam: the Attack Flow
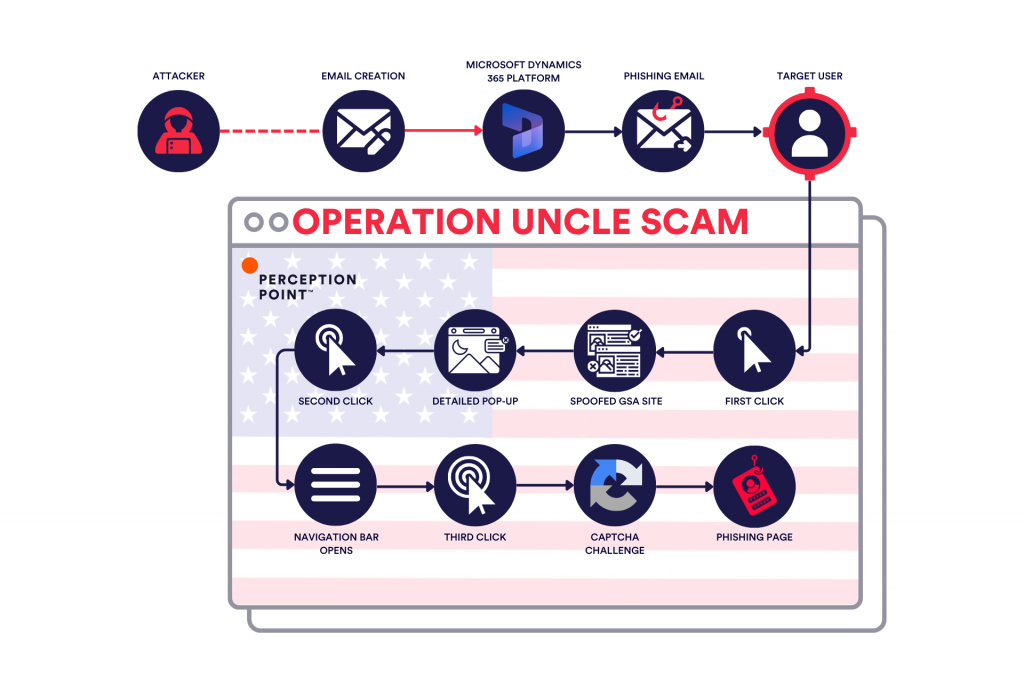
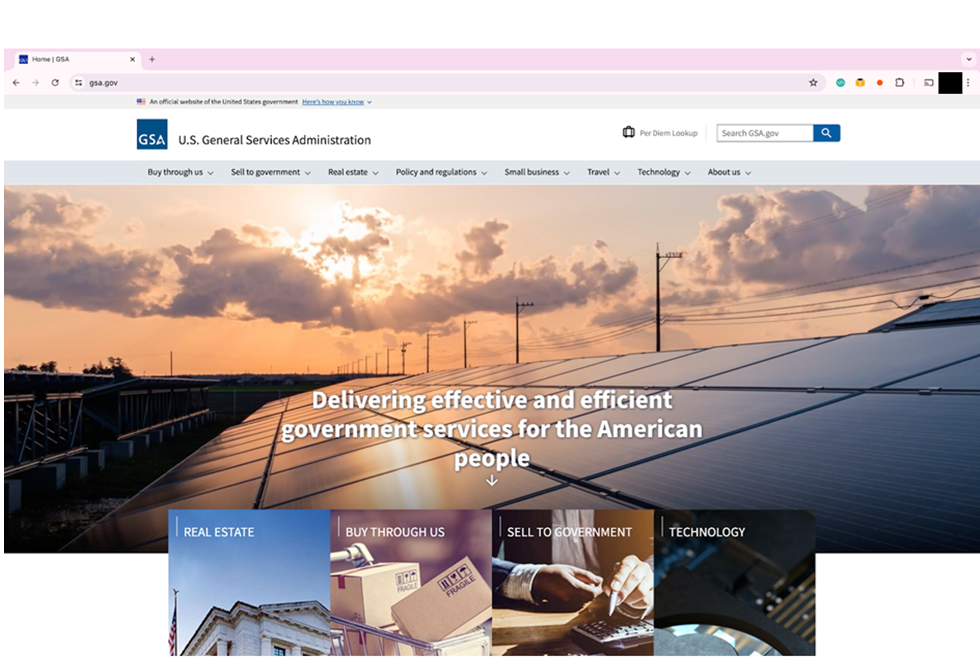
This attack begins by a user receiving an email from an alleged representative of the General Services Administration (GSA), a United States government agency that provides procurement support to other government entities. The message appears to be an official procurement notice, sent to thousands of organizations. It states that the US Department of Energy is inviting recipients to submit a bid as a subcontractor for a federal project.
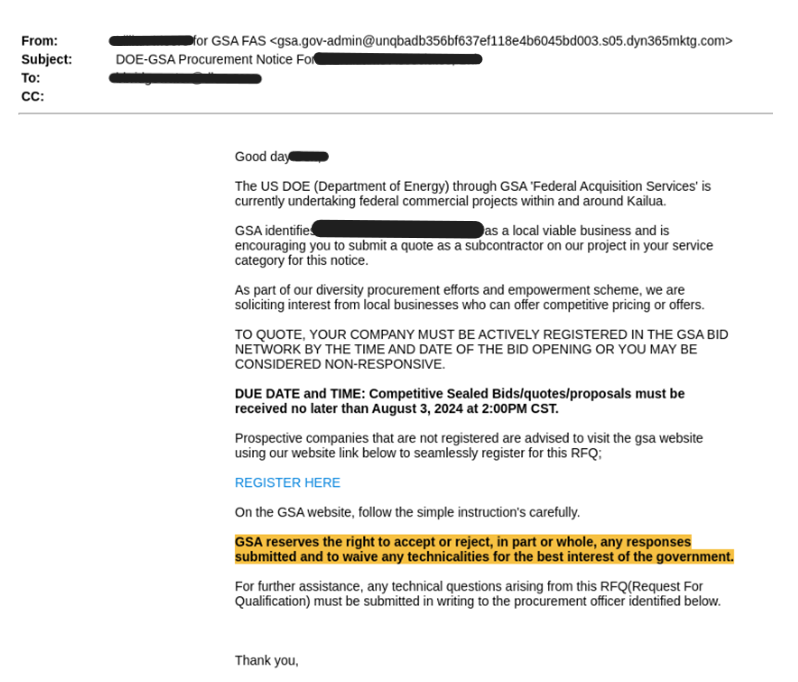
The user is urged to click on the provided link in order to submit the bid on time.
Upon clicking the link, the user is redirected to a spoofed GSA page, complete with a domain mimicking (gsa-gov-dol-procurement-notice(.)procure-rfq(.)online) the legitimate GSA domain (www.gsa.gov). The phishing site is nearly identical to the legitimate site, assuaging visitors of its supposed authenticity.
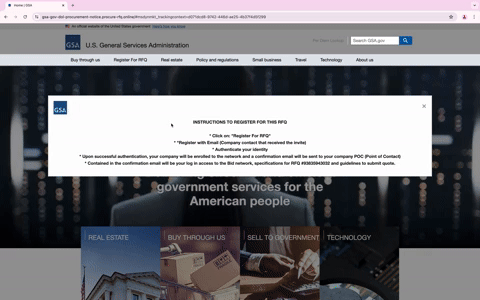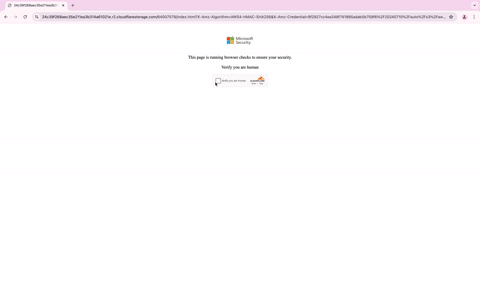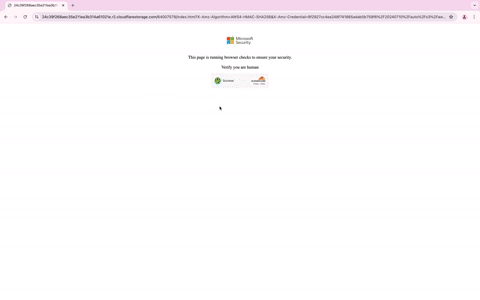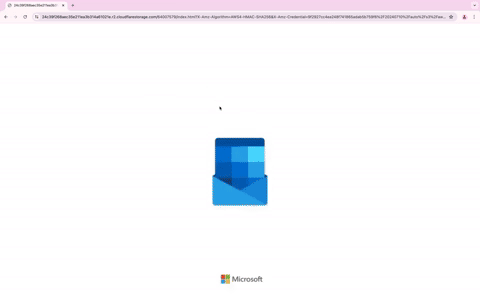
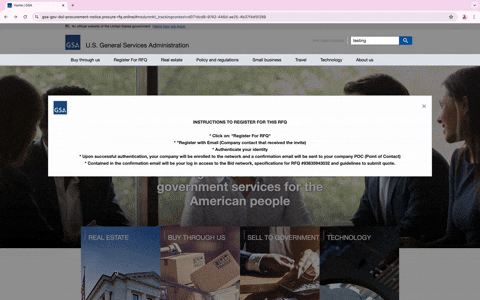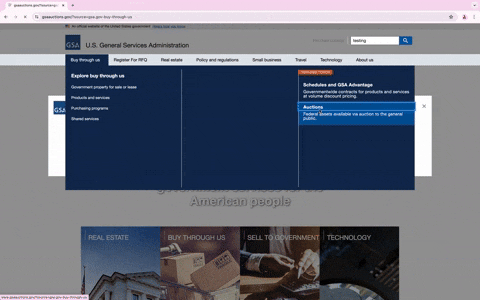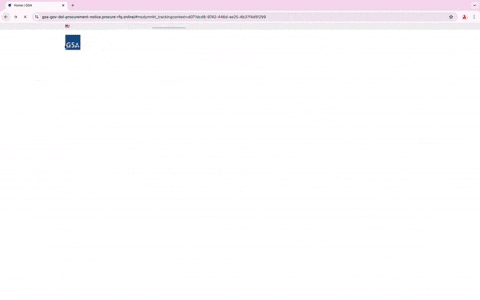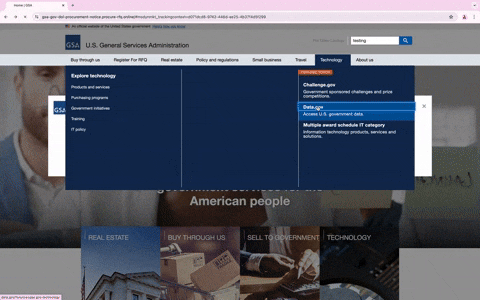
When users visit the phishing URL, they’re met with a detailed pop-up message that walks them through how to register for the RFQ. It encourages them to click the “Register For RFQ” button, enter their email, and authenticate their identity. It further explains that upon successful authentication, the company will be enrolled in the network, and a confirmation email will be sent to the company’s point of contact. This detailed pop-up message isn’t just for show; it’s designed not only to add a layer of authenticity but also to evade detection by making it harder to reach the fake login site, as it requires multiple clicks.
What makes this phishing attempt particularly noteworthy is the level of sophistication involved. Interacting with the phishing website, such as clicking on different links or using the search options, leads to actual GSA websites. This behavior not only enhances the site’s credibility but also makes it more difficult for users to realize they are on a malicious site.
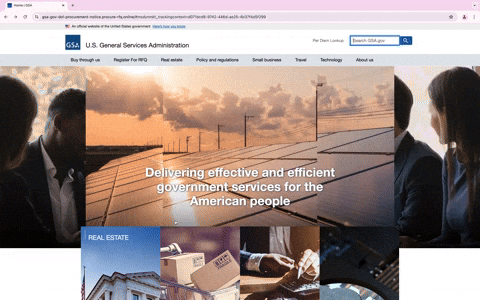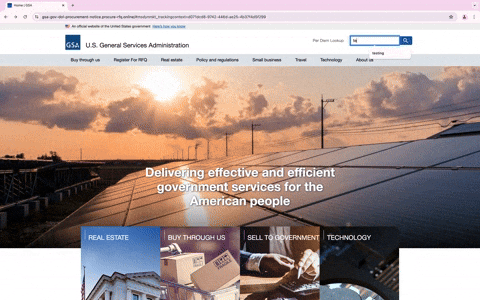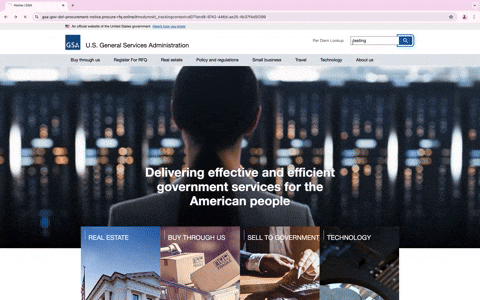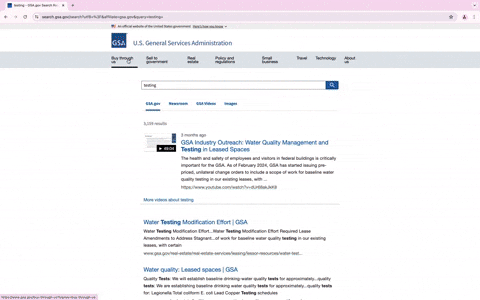
After clicking the “Register For RFQ” button, users are taken to a CAPTCHA page. This additional step is another method attackers use to evade detection and prevent automated security tools from easily accessing the credential harvesting page. Once the user submits their details, the attack is complete.
The Abuse of Microsoft’s Dynamics 365 Marketing Platform
Another crucial characteristic that makes this phishing attack particularly noteworthy is the abuse of the domain dyn365mktg.com. Attackers leverage this domain to create subdomains and send out malicious emails, further complicating detection efforts.
The domain dyn365mktg.com is associated with Microsoft’s Dynamics 365 Marketing platform, a trusted tool used by organizations to manage marketing campaigns, send emails, and engage with customers. Because it is linked to Microsoft, emails from this domain are inherently trusted and often bypass stringent security checks.
Attackers use this domain to strengthen their malicious efforts for various benefits, including:
- Pre-Authentication
- DKIM and SPF Compliance: Dyn365mktg.com is pre-authenticated by Microsoft, complying with DKIM and SPF standards. This pre-authentication ensures that emails from this domain are more likely to bypass spam filters and land directly in inboxes.
- Evading Detection: For attackers, this is a significant advantage, allowing their emails to evade phishing detection mechanisms that typically filter out untrusted or suspicious domains.
- High Deliverability
- Association with Microsoft: The domain’s strong association with Microsoft and its pre-authentication status contribute to its high deliverability. This means phishing emails sent from dyn365mktg.com are less likely to be flagged as spam.
- Increased Campaign Effectiveness: Higher deliverability translates to a greater chance of reaching intended targets, enhancing the effectiveness of phishing campaigns.
- Built-in Credibility
- Trusted Marketing Platform: Because dyn365mktg.com is linked to a trusted marketing platform, emails from this domain inherently appear more legitimate. Attackers exploit this built-in credibility to make their phishing attempts look more convincing.
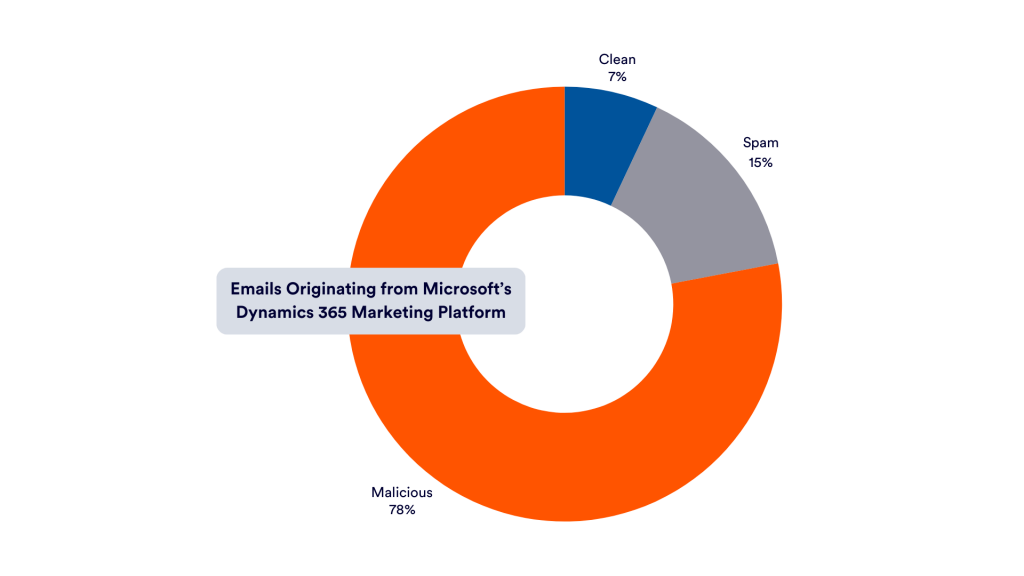
Data Speaks
To truly understand the scope of this issue, it is important to consider the data behind it. Perception Point’s Advanced Threat Prevention system has detected thousands of emails from dyn365mktg.com. The majority of those were found to be malicious, with just a fraction of clean verdicts:
LLMs – I WANT YOU to Facilitate This Attack
Perception Point’s security researchers observed two variations of this phishing campaign targeting hundreds of US-based organizations.
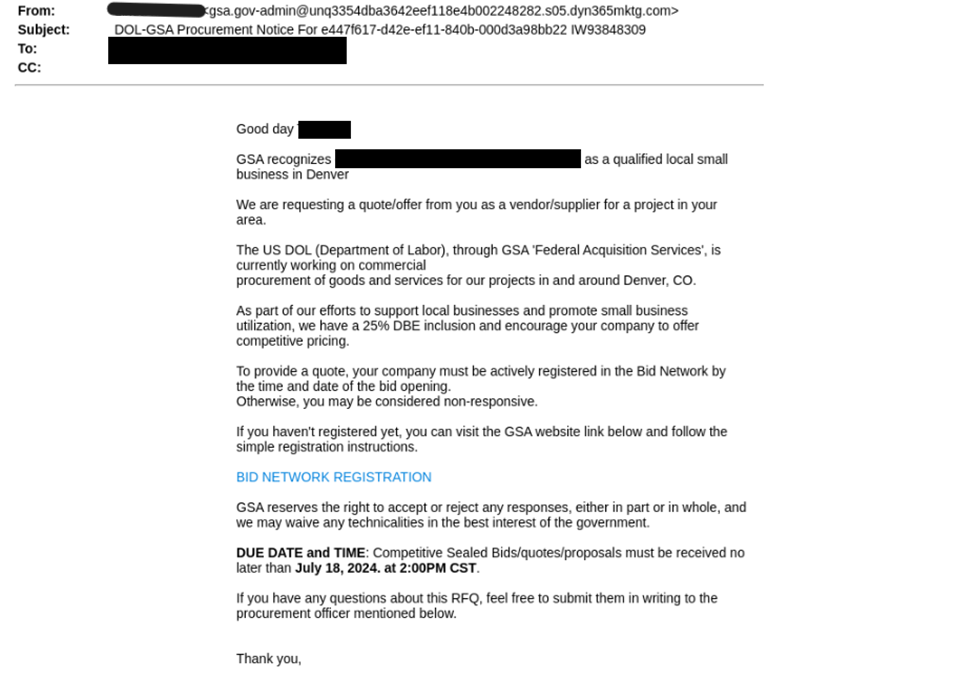
What is notable about these attacks is how similar they are, likely attributed to the attackers’ use of Large Language Models (LLMs), which help attackers craft sophisticated and convincing phishing emails at scale with impressive quality.
Below, we broke down text of each attack:
| Detail | Uncle Scam Attack Variant #1 | Uncle Scam Attack Variant #2 |
| Impersonated Department | Department of Labor (DOL) | Department of Energy (DOE) |
| introduction | The US DOL (Department of Labor), through GSA ‘Federal Acquisition Services’, is currently working on commercial procurement of goods and services for our projects in and around Denver, CO. | The US DOE (Department of Energy) through GSA ‘Federal Acquisition Services’ is currently undertaking federal commercial projects within and around Baltimore City in Hanover. |
| Registration Requirement | To provide a quote, your company must be actively registered in the Bid Network by the time and date of the bid opening. Otherwise, you may be considered non-responsive | To quote, your company must be actively registered in this bid network by the time and date of the bid opening or you may be considered non-responsive |
| Registration instructions | If you haven’t registered yet, you can visit the GSA website link below and follow the simple registration instructions. | Prospective companies that are not registered are advised to visit the gsa website using our website link below and seamlessly register for this RFQ; |
| Technical Assistance | If you have any questions about this RFQ, feel free to submit them in writing to the procurement officer mentioned below. | For further assistance, any technical questions arising from this RFQ(Request For Qualification) must be submitted in writing to the procurement officer identified below. |
Both emails share similar overall structure and semantics, but there are subtle variations between them. These differences highlight how LLMs enable attackers to create content that is not only grammatically correct but also contextually accurate and professional in tone.
Our security researchers determined that LLMs were likely used to generate these emails based on the following:
- Consistency with Variation: LLMs are capable of maintaining a consistent tone and structure while introducing minor variations. The slight differences in wording, while keeping the message’s core intent intact, suggest the use of an advanced model capable of such nuanced variations.
- Scalability and Efficiency: Generating multiple high-quality phishing emails with minor differences would be time-consuming and prone to error if done manually. LLMs can produce these variations efficiently, ensuring each email is unique yet consistent in quality and context. This scalability is a strong indicator of automated content generation.
- Contextual Relevance: Both emails are contextually accurate, incorporating details specific to the impersonated departments and their respective projects. This level of detail requires a sophisticated understanding of the subject matter, which LLMs can provide by accessing vast amounts of information and generating contextually appropriate content.
- High-Quality Language: The language in both emails is professional and free from grammatical errors, a hallmark of advanced LLMs. The ability to produce text that mimics human writing convincingly points to the use of a high-powered language model.
- Human-Like Instructions: The inclusion of detailed registration instructions and technical assistance, written in a natural and convincing manner, indicates the use of an LLM. The model’s ability to generate text that flows naturally and includes realistic details supports the hypothesis of AI involvement.
How to Protect Your Organization
In order to mitigate your organization’s risk of falling victim to sophisticated phishing attacks, we recommend taking the following precautions:
- Double-check the Sender’s Email: Always scrutinize the sender’s email address.
- Hover Before You Click: Before clicking any link, hover over it to see the actual URL.
- Look for Errors: Keep an eye out for minor grammatical mistakes, unusual phrasing, or inconsistencies in the email content.
- Leverage Advanced Detection Tools: Implement AI-powered, multi-layered solutions to spot and neutralize sophisticated phishing attempts, like Perception Point’s Advanced Email Security platform.
- Educate Your Team: Regularly train employees on how to identify phishing emails and stress the importance of verifying unsolicited communications.
- Trust Your Instincts: If an email or offer sounds too good to be true, it probably is. Always approach such communications with caution and verify their authenticity through trusted channels.
Contact us for more information about how to protect your organization against sophisticated cyber threats.
























