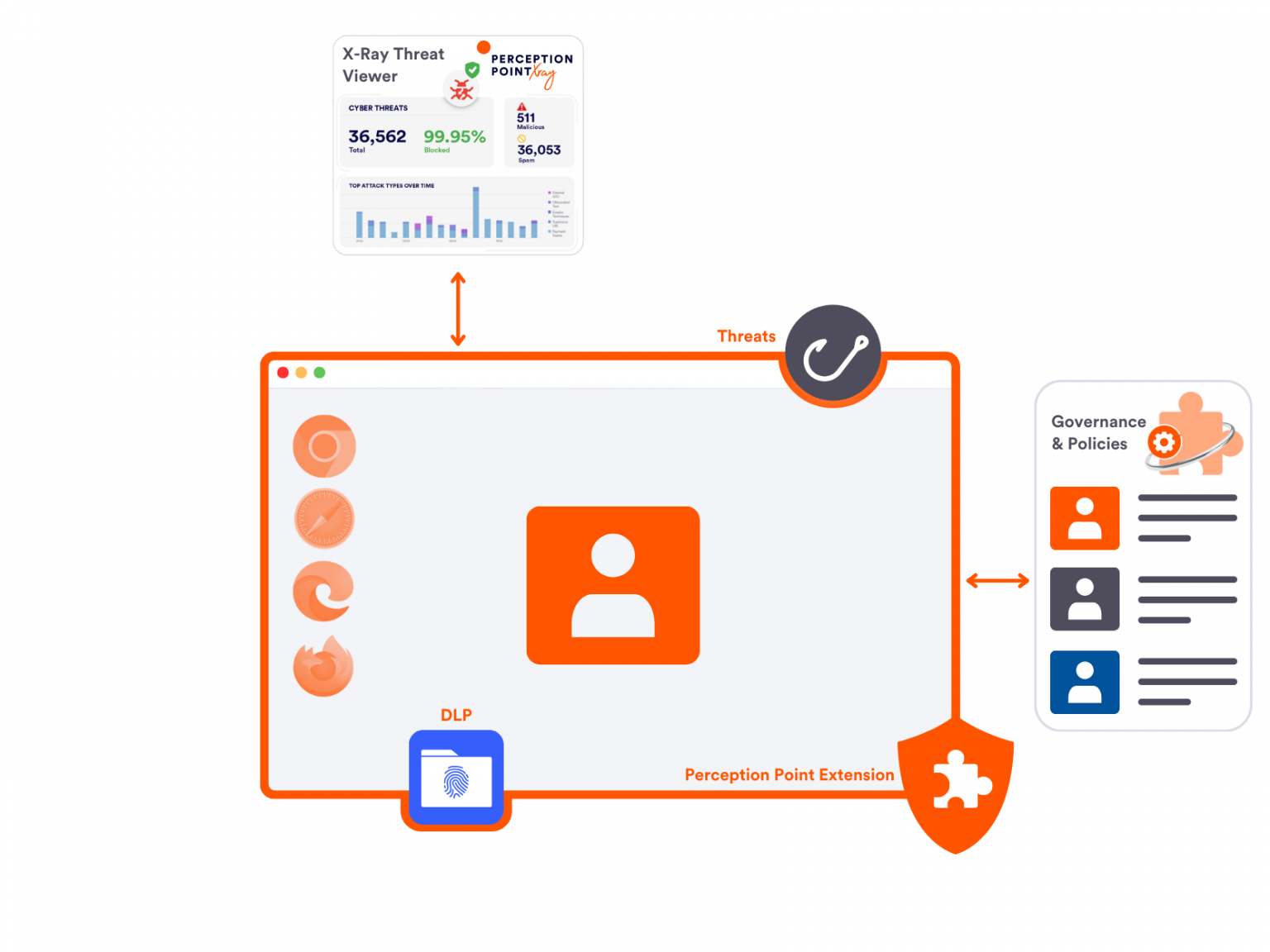
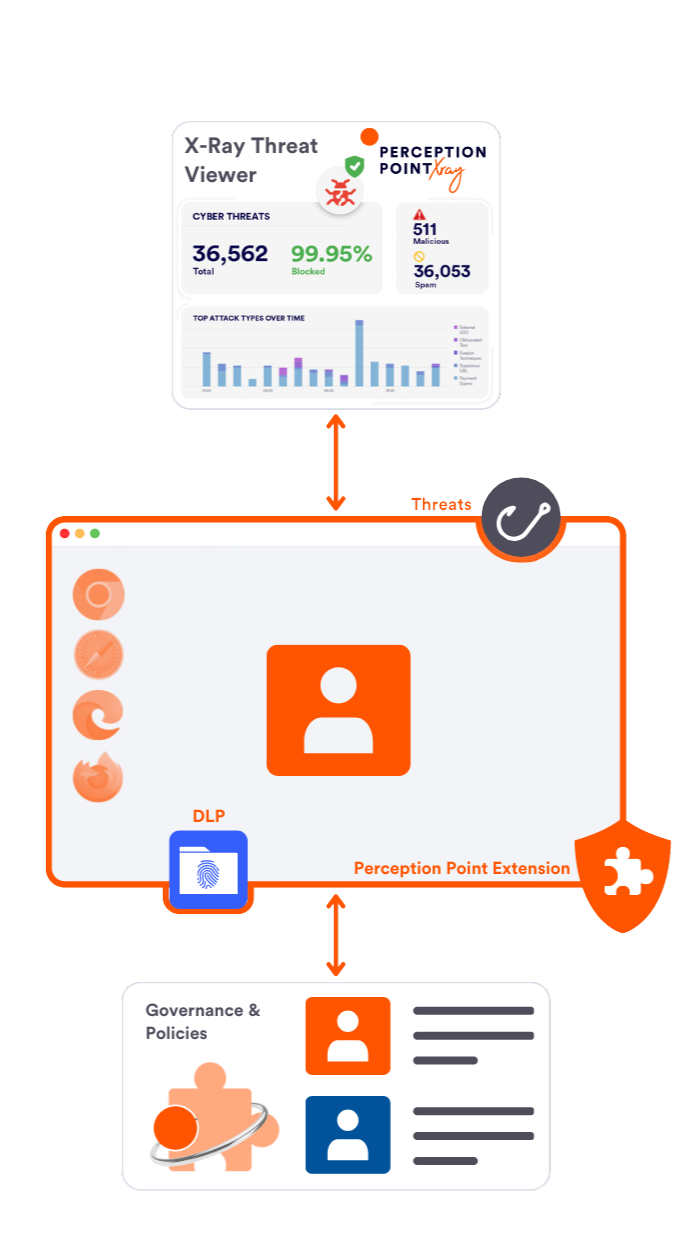
Refreshing Browser Security & Control
Advanced Browser Security with Perception Point

Protect your enterprise browser and SaaS apps against external web threats, data breaches and employee-related risks. Regain control and visibility over your users’ last ungoverned workspace with Perception Point Advanced Browser Security extension.


Safe Browsing
Prevent phishing, evasive malware, zero-days, and harmful browser extensions from compromising your users and data

Safe Access & DLP
Enforce safe access to your SaaS apps on managed and unmanaged browsers, stop data leaks, malicious insiders and 3rd party threats

Browser Governance
Transform any browser into a secured workspace with granular browser-level controls and 360° visibility
The Browser is the Most Used App in Your Company
and that’s why it is a…

Targeted Channel
Browsers are popular targets of cyber attacks that circumvent traditional detection tools like secure web gateways (SWG). From phishing to malware and zero-days, threat actors exploit the browser’s accessibility to launch attacks on users and their devices.

Source for Data Loss
The very nature of browsers, designed for information access and sharing, makes them a go-to vector for data exfiltration. Whether via unintentional actions by employees or deliberate attempts by malicious insiders, browsers facilitate daily unauthorized transfer of data and files out of the enterprise.

Governance Challenge
Interactions between users and their browsers are a significant blind spot for endpoint and network security measures. This leaves IT teams without the ability to enforce policies or detect anomalous behavior within the browser environment.
Perception Point delivered immediate value at the get-go of the POC. Detection rates were superb, and the fact that the Incident Response service is baked into the solution was a huge benefit.
GRANT WALSH, DIRECTOR OF IT – INFRASTRUCTURE , OPERATIONS, & SECURITY AT FLOW CONTROL
Advanced Browser Security for the Modern Enterprise
Protect More
Catch threats at the point-of-click
Using textual and image recognition AI models, proprietary anti-evasion and a patented sandbox, Perception Point instantly identifies and blocks web borne attacks, from evasive phishing sites to malicious file downloads and XSS exploits. Protecting your employees, data and endpoints.

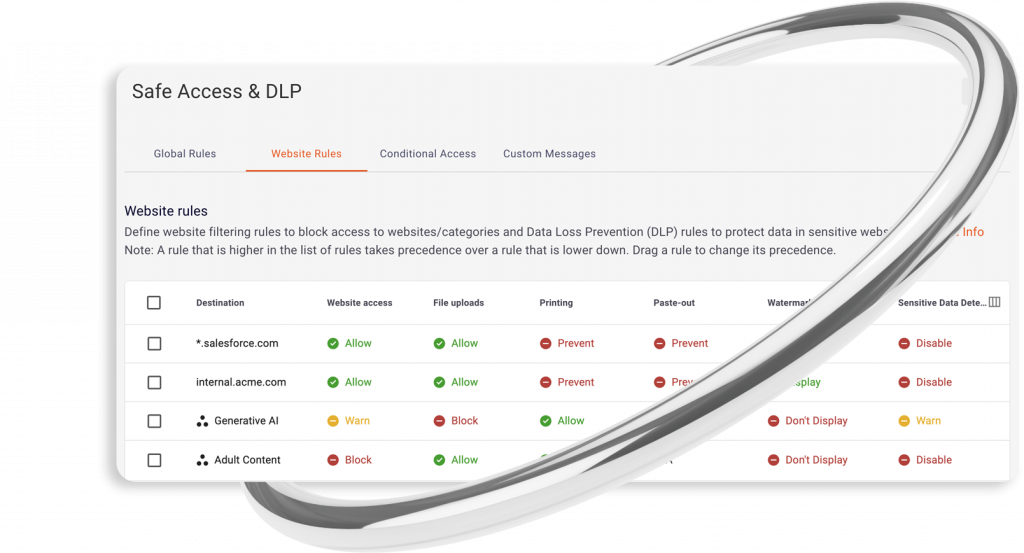
Control More
Enforce safe access & prevent data loss

Advanced Browser Security equips you with a wide set of tools and granular policies over your users’ window to the internet, no matter where they are. Secure access to and prevent risky activities on your organization’s web apps and SaaS solutions across managed and unmanaged devices
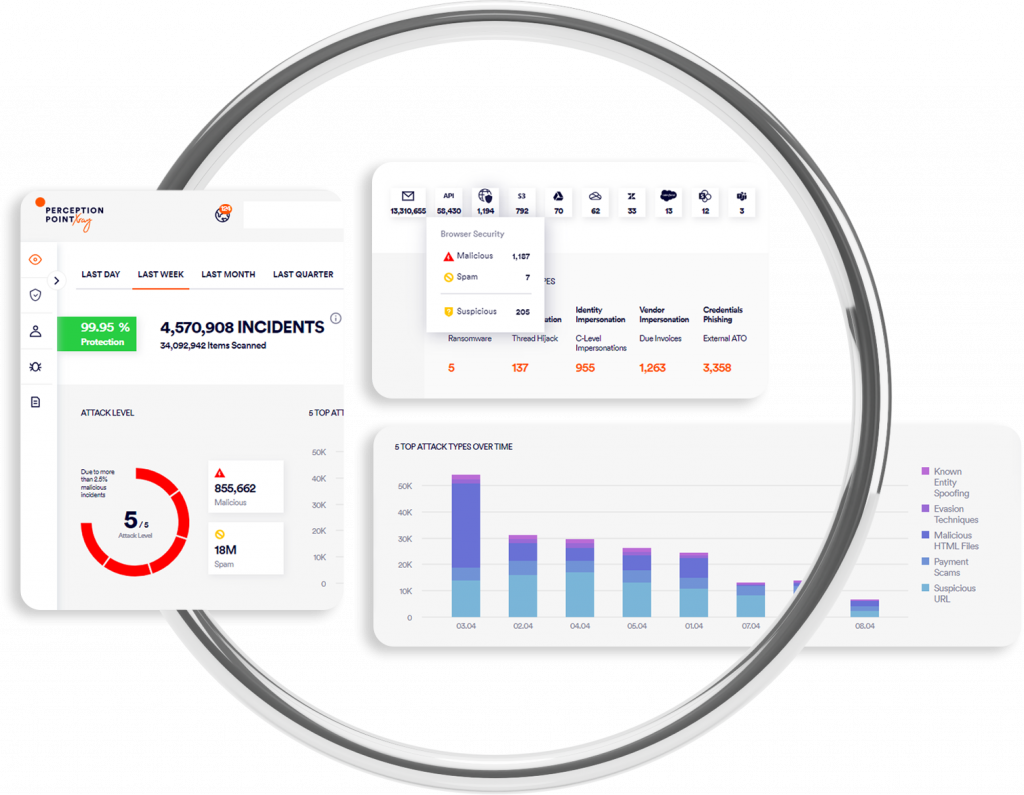
See More
Get better visibility to browsing behaviors

Natively integrating with your existing enterprise browsers, Advanced Browser Security allows for full visibility and effective monitoring of risky browsing events, user login activity, 3rd party extensions behavior, sensitive data uploads, risky use of ChatGPT-like tools and more.

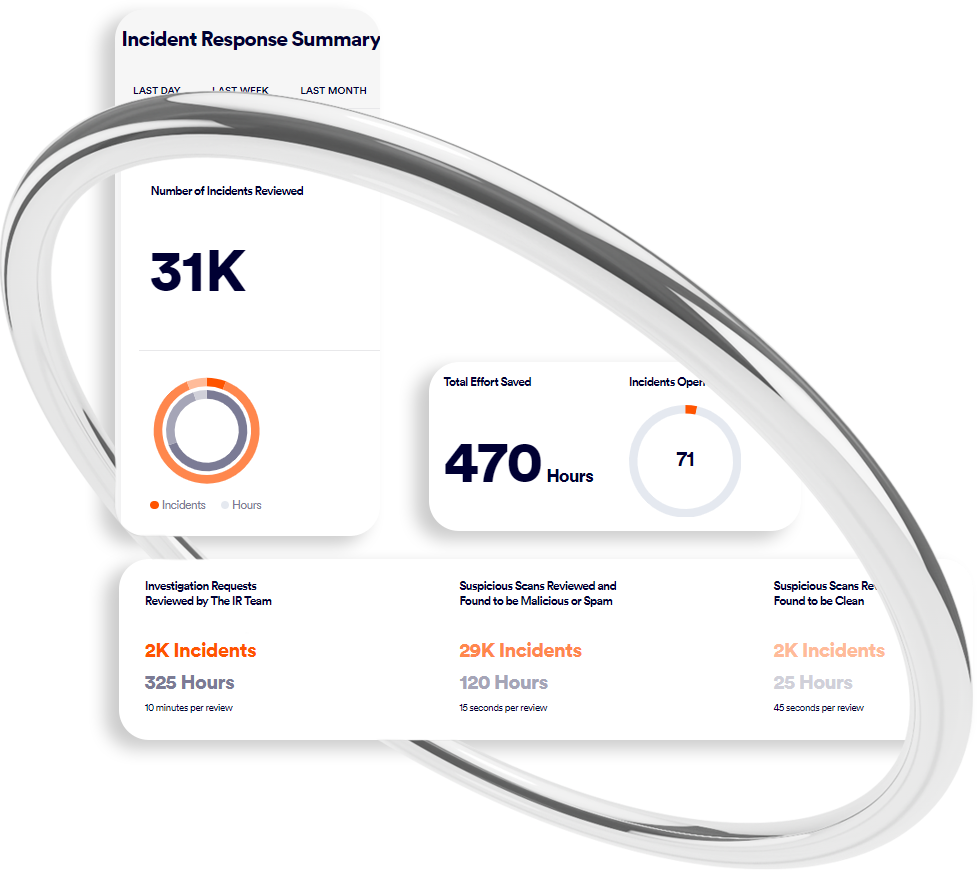
Manage Less
The first managed browser security solution

Perception Point’s managed incident response and support service alleviate the overhead and fully support your SOC/IT teams or MSP staff 24/7, to provide top-shelf browser security and save up to 75% in resources.
Uncompromising Workspace Security and Productivity

Centralized
Control
Configure and enforce all website rules and policies from Perception Point’s intuitive cloud management console.

Rapid
Deployment
Onboard employees and contractors easily via a lightweight browser extension compatible with any standard browser.

Unhindered User Experience
Allow your users to continue working with their existing browsers. Unless a web-borne threat is detected, they won’t feel the extension is there.

Workspace
Security-Ready
Combine with Advanced Email Security and cloud-apps protection, to holistically protect your user-centric attack vectors against any advanced threat.
Testimonials
With the strongest results on the market, we decided to select Perception Point as our advanced email security provider. Rollout was smooth and well supported. Perception Point continues to work closely with our team, and we value Perception Point as our long-term partner in protecting our users, business and brand.

Because Perception Point’s IR service digs into incidents, really investigating them, our team does not need to invest time and resources to ensure the best protection for the users. I know that the IR team has my back. Perception Point, unlike other vendors we were also in POC with, impressed us almost immediately, it was really a no-brainer for us; the tool just works really really well.

Perception Point Advanced Email Security protects the company from all the attackers’ attempts via email that can put our company at risk. We also use their API to send les and URLs to the Perception Point next-gen sandbox for rapid investigation. As a result, we manage fewer incidents, and leverage the Perception Point IR service to offload our SOC team.

We needed to augment Salesforce security with advanced threat protection capabilities, not available with standard anti-virus solutions, for all content uploaded to Salesforce. By deploying Perception Point’s Salesforce advanced security solution we know that our organization is fully protected from all content-borne threats.

We aim to protect our business and our customers in a fashion that does not tamper with files or hinder the customer experience. Perception Point delivers ease of integration and high detection rate at the speed and scale we need, allowing us to instantly and effectively dynamically scan our files to prevent content-based attacks.