Perception Point’s Added Value
Perception Point offers
Prevention-as-a-Service.
On top of providing the best detection rates on the market, we are committed to act as your trusted advisor, helping security experts and IT managers to better intercept, analyze, and understand any attack.
No long admin guides. No integration downtime. No fuss.
Our Services
Our 360-degree framework is comprised of a complete stack of added-value services, covering the everyday needs of the modern SOC, IT, and security teams.
Incident Response
The X-Ray
Reporting
End-user Reporting
Auto-deployment & Updates
24/7 Support
Incident Response
Machine learning, automation, and cyber experts act as your SOC Multiplier
Your security team faces a growing amount of challenges. Between monitoring content traffic, analyzing incidents, managing false positives, interacting with end users, and learning about new attack trends, your team is bound to face burnout. Perception Point’s Managed Incident Response Service is here to solve these problems for you.
Combining machine learning capabilities, autonomous LLM models, and close interaction with our human cyber experts, we make sure every incident is analyzed, creating a safe content-sharing environment.
Autonomous Detection with
GPThreat Hunter™
GPThreat Hunter™, powered by OpenAI’s GPT-4, revolutionizes our incident response service by autonomously resolving ambiguous cases, significantly speeding up detection and remediation. This integration ensures rapid evolution against workspace cyber threats, fusing AI precision with human expertise for superior workspace protection.
“Phone a Friend”
Business Streamlining
(the “Where is My Email?!” issue)
Our Advantages
Machine Learning
System Health Check
Training
Elevating Incident Response with GPThreat Hunter™
Integrating GPThreat Hunter™ into our managed incident response service sets new standards in threat detection and remediation, offering autonomous precision that significantly cuts down response times and empowers our experts to focus on complex investigations.
This innovative tool, powered by OpenAI’s GPT-4, continuously learns from each interaction, enhancing its detection capabilities and ensuring our services evolve to meet the challenges of the dynamic cybersecurity landscape.
GPThreat Hunter™ fuses the best of human expertise with cutting-edge genAI, delivering unmatched prevention and personalized attention to secure your workspace against emerging threats.
The X-Ray
The ultimate SOC operations tool
Insights
Analyzer
Manage Policies and Rules
Conduct Forensics
See the X-Ray
in Action
Check out this demo of our X-Ray and see why major enterprises use Perception Point’s Advanced Security to protect their content-exchanges.
Reporting
Customized reports within a click
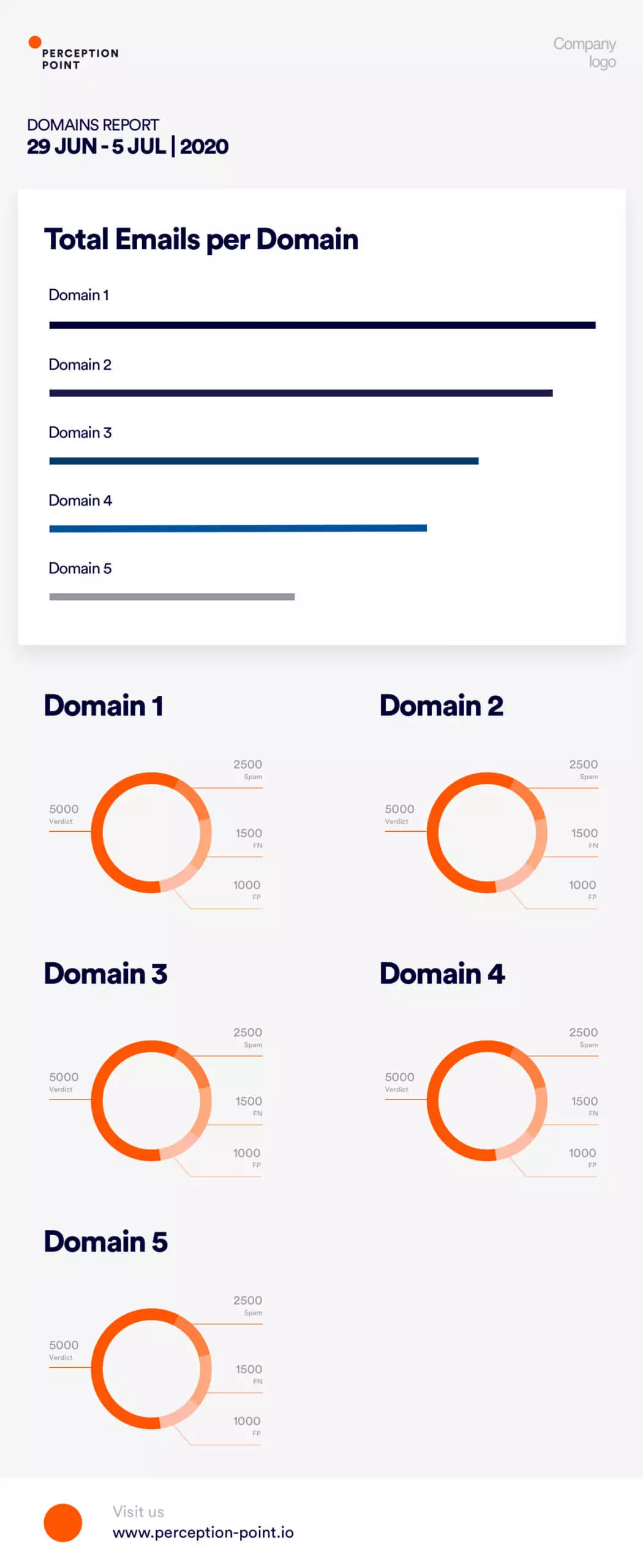
Perception Point offers various types of reports:
IR reports
Ad-hoc incident reports on unique incidents, daily digests for VIP clients, and weekly/monthly reports on attack trends.
Customized reports in just a click
Scheduled concierge reports
Weekly, monthly, and quarterly reports, including aggregated summaries of all activities and trends based on real life data.
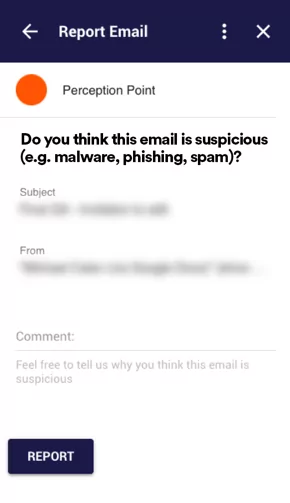
End-User Reporting
Transforming your employees to an active line of defense
Integrated within your employees’ email interface, a simple button allows your employees to report any suspicious emails directly to our platform. With this capability, your employees become part of your security stack, helping you to prevent the next attack.
Once an end user reports a suspicious email, our Incident Response team is alerted with all the relevant data to investigate the potential incident. In the event that the email is deemed malicious, you will receive a detailed report and the system will automatically retrieve all similar emails from all relevant email inboxes.
More Services
Auto-deployment
& Updates
Cloud-native platform ensures maximum availability and efficiency.
- • Ongoing detection updates
- • Direct access to cyber experts
- • Research publications
- • Enhanced user experience
24/7 Support
- • Designated customer success engineer
- • Ongoing feature requests
- • System health management
- • Access to our Research team























