In this blog, we will show one way of how attackers leverage SendGrid, a prominent platform that helps send marketing emails, in order to attack companies across the US and EMEA.
Overview.
This exciting anti-phishing blog encapsulates 2 interesting, sophisticated trends:
- Evasion – how attackers use trusted domains and brands for targeting enterprises.
- Human learning – how attackers can research and find the weakest links – either between enterprises or within the enterprise.
The Disguise.
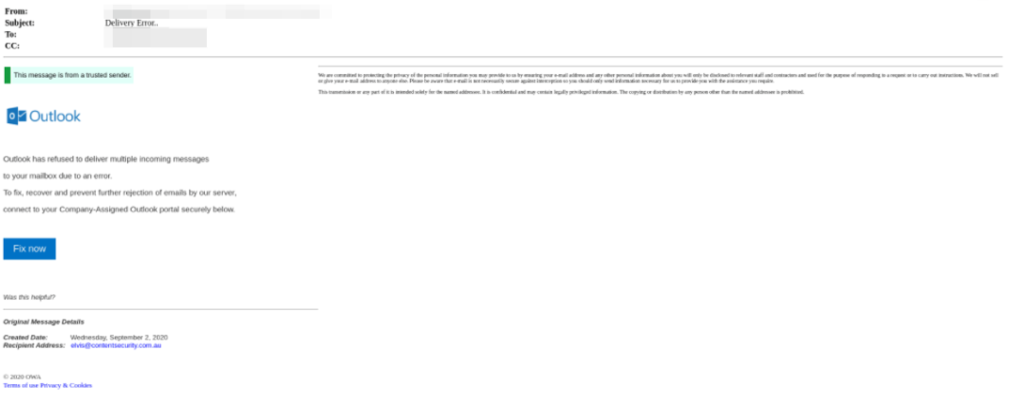
We will start with an example. The attack below was intercepted by Perception Point’s service, identifying that the email is actually an attempt to steal credentials.
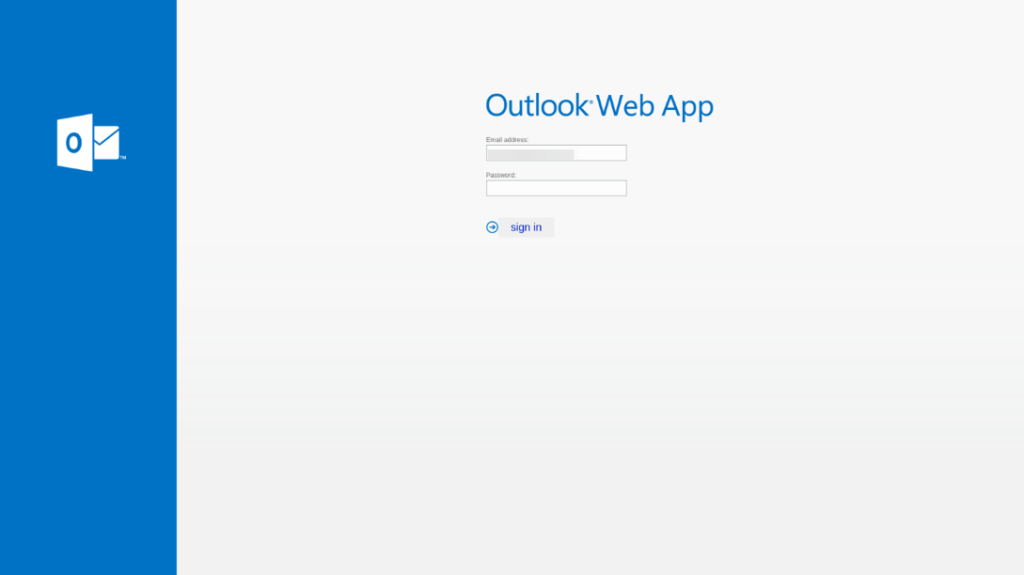
In this email, the attacker impersonates Microsoft, stating that there is a problem with the user’s Outlook account. Accordingly, the user is required to hit the “Fix now” button to solve the problem. However, once clicked, the button will redirect the user to what appears to be a legitimate Outlook Web App, but is really a malicious phishing website attempting to steal the end-user’s credentials (can be seen in the second screenshot).
IOCs.
By looking at the IOCs of this specific example, we can see that the attacker is using SendGrid to hide the malicious link and to learn more about the targets. We outlined the benefits of this technique in the next section “The Campaign”.
- Subject: Delivery Error.
- Malicious URLs:
- https[:]//u4882271[.]ct[.]sendgrid[.]net/ls/click?upn=YFyCGXB2k7XEs51EAWvRp-2BQ6xaP5-2Bxv1vyI4sITyTp6VhtJSyiu7Ungt4CUf7KdGYIEL6EtBm54FuYN8n5lu1Owy6WZrDF87wSB9AzxWNsE-3DxTY2_-2FUzRtXaB-2Bbf6wd53NUnc175ijinyI2IksJK6WudGi6IvOE6zcWPOpaqVcGtapxJ2dZSn0t1Q6M85vjBlZ6GrjTcAOAcpq2P8XWJOa-2BqN3aw4eDu-2FS7pd4IIyMY-2FouUZJK9aAXoLP1UufUO629nv4zKWD9xKclW-2Fxeo46v7YtoAwO6Tclo3kZhklMOLWMH8v96JM6WOnoD5agI0KFdVghWTmzVBJ4c-2FHDy-2F0kyCFjO7Ub-2FVrWb9GPHLLyxgAZiASn
- https[:]//autodiscover98378789893[.]web[.]app/#
The Campaign.
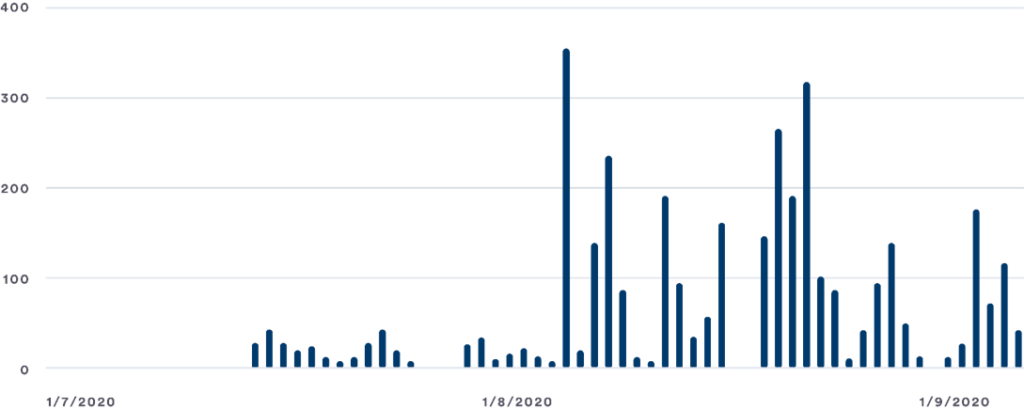
This is not a single attack. We see the use of SendGrid for malicious purposes time and time again. To be exact – since July 1st, 2020, Perception Point’s service prevented 3,420 different attacks that used this mechanism.
By looking at the chart below, one can see that there was an increase in the number of such attacks starting from the 2nd half of August. Based on our experience and analysis of the trend, we would expect to see more attacks like this during September (as we already see in the first week of the month) and even October. This is because when attackers see that a campaign works successfully for them, they will press on it as much as they can. Most email security vendors will need time to develop a solution.
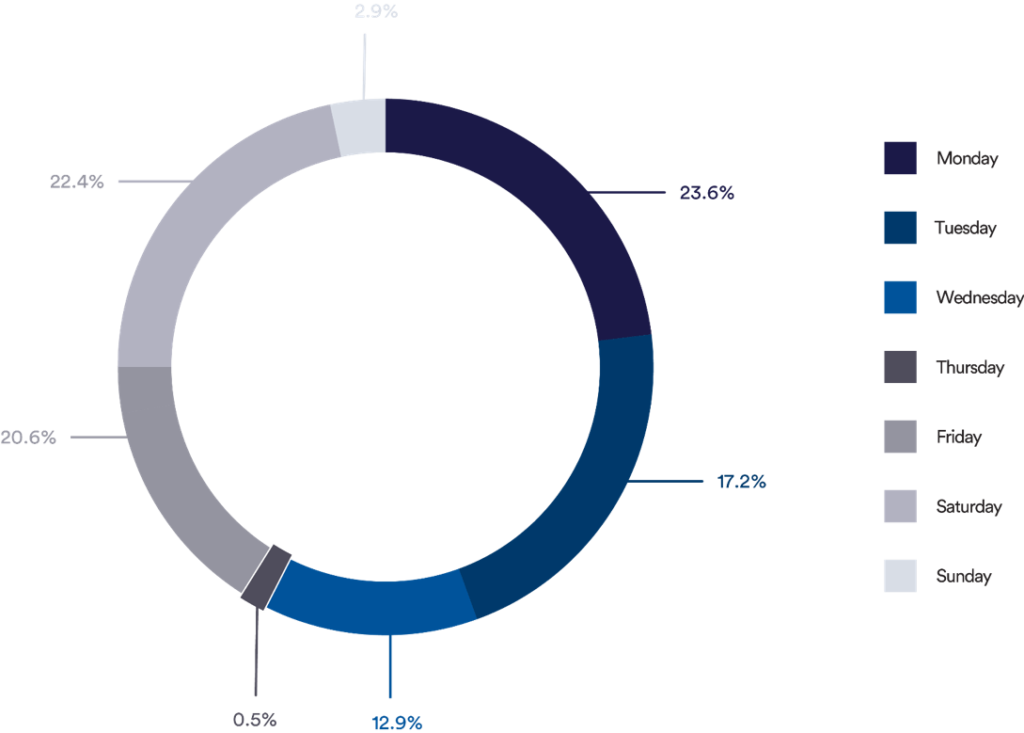
We also looked into the days in which the attacks were sent. Most attacks were launched in the first and the last days of the business week – Monday and Friday. On the other end, it is interesting to see that almost no attacks were launched on Thursdays while on Saturdays, although considered a weekend day, there was also high activity from attackers. This might suggest that the attacker pursues a trial and error process (see details below).
1st Added Value for the Attacker: The Evasion Mechanism.
The first benefit of this attack mechanism is the evasion element. While many email security vendors can protect against known phishing attacks, most of them can be easily evaded. By simply leveraging SendGrid, attackers “hijack” SendGrid’s reputation. With this trusted origin, some security vendors will prefer to either not scan the email at all, or use only basic, static mechanisms to check, leading to evasion.
In the example, we see that Microsoft’s email security not only flagged the email clean, but it also added a note that it came from a trusted sender. This shows that this hijacking technique is highly effective and can bypass many solutions on the market.
2nd Added Value for the Attacker: If at First You Don’t Succeed, Try, Try Again.
The second element is highly interesting. Every “above average” attacker would have to undergo a process of trial and error – much like every marketeer trying to reach potential leads. Attackers would design and plan an attack and then send it out to the world. Some of the attacks will succeed and some will not. By using SendGrid, the attacker can collect data and then optimize the attack in two vectors:
- Between organizations – analyzing which enterprises are less protected in comparison to others, and thus more prone to the phishing attacks. A targeted company with higher delivery and open email rates is less protected and more lucrative for the attacker.
- Within the organization – another analysis is checking who are the employees within the organization that are more likely to be fooled. This can be at the individual level (e.g. John Doe) or the department level (e.g. Finance or Legal teams).
In addition to mapping the targeted users, the attacker can try and understand when is the best time to launch the campaign – for example, workdays or weekend days? Morning time or late afternoon? By using data and follow-up analysis, attackers can find the best path for them to achieve their malicious goals.
Perception Point.
Perception Point’s service is highly fit to prevent such attacks, due to 3 main capabilities:
- Dynamic scanning – Perception Point doesn’t simply rely on IP reputation to decide whether a link is clean or not. By actively surfing to the website, the service can identify the malicious activity and prevent it, making the attempt to leverage another platform’s reputation (in this case, SendGrid) die in vain.
- Anti-evasion – Perception Point uses several anti-evasion engines that know how to follow the malicious payload, regardless of how deep it is embedded. The system will crawl and locate any payload and scan it to ensure full protection.
- 100% scanning – Perception Point scans all traffic. The system is pure scale agnostic and as such does not rely on statistics to decide whether it should be scanned or not.
We welcome you to check our anti-phishing capabilities and see how we can prevent the next attack on your organization.























