A report reveals that about 32% of cyber breaches start with phishing. This begins with the use of malicious emails that contain phishing links. And these links contribute about a 40% success rate to cybersecurity breaches happening around the globe.
Overview.
What happens if you take a pinch of social engineering, a grain of evasion, and throw some anonymization techniques into the mix? Well, you just conjured a perfect recipe for phishing. Now, you become an evasive magician.
This blog will show you a simple—but significant—example of how attackers steal credentials or information from your devices. Based on our experience, this kind of attack acts as the first stage of a more sophisticated attack that would include spoofing or even an account takeover (ATO) of a “trusted” user. Most times, it begins with a phishing link—an undetected, clickable unscrupulous link.
It is important to note that the example below is one of a large-scale campaign intercepted by Perception Point. These attacks target multiple organizations and innocent end-users.
Ingredient #1 – Social engineering.
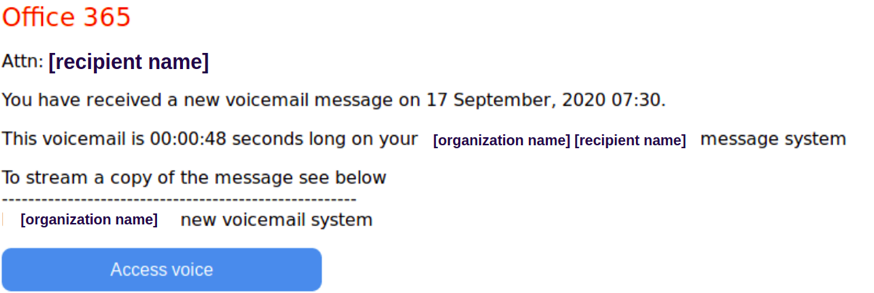
The first part of the attack is impersonation. Through social engineering techniques, the attacker tries to lure the end-user to click on the “access voice” button, which is a malicious link. This malicious link is the “phishing link.” In this attack, attackers use the company’s logo and relevant color palette to impersonate Office 365.
Ingredient #2 – Anonymization.
As an added touch, the attacker uses the right amount of anonymization. This is the balance between making the attack widespread but still appearing targeted or specific to the victim. The IOCs structure below depicts this illustration.
The attacker weaves the recipient name and organization domain (from the recipient address) into the email subject and the “from” header. This makes the attack appear authoritative and authentic. As a result, you won’t have any suspicion as an end-user.
- Subject: [organization domain] [recipient name mailbox] [time stamp]
- From: [organization domain] [recipient name mailbox] [some-mailbox@some-domain]
It’s important to note that the attacker chose not to spoof the specific organization’s brand and addresses to remain undetected, using nine different email domains and eight different IPs (all unknown by reputation mechanisms).
Ingredient #3 – NLP Evasion.
On top of the “ingredients” above—social engineering and anonymization, another unique technique attackers use is embedding the phishing link in the body of the email. Once you open the email and scroll down to the bottom of the email, you uncover a new text. This text contains an enormous bulk of automatically generated texts in over one language. And the link is a part of this chunk of texts.
The purpose of this is to evade email detection based on NLP methods. This technique is instrumental in avoiding email security vendors, as they do not analyze the context of the email body correctly to determine whether the email is malicious.

The Payload.
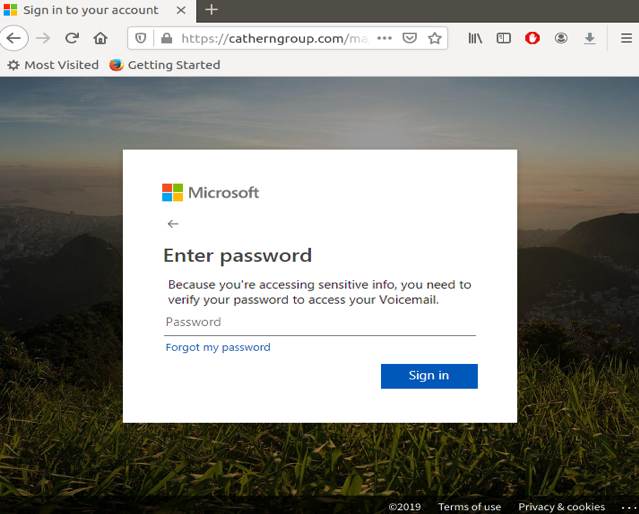
If the user clicks on the phishing link, attackers redirect him to a fake Office 365 login page that looks real. Once you punch in your login details thinking it’s Office 365 official page, attackers would steal your login credentials immediately. Then, the attacker uses a redirect mechanism to ensure that reputation-based anti-phishing engines do not block the attack.
Perception Point.
Perception Point’s service prevented this attack using advanced anti-phishing algorithms. This engine can detect even the most elusive phishing attempts and the slightest ones, such as phishing links. Our algorithms use dynamic scanning—we don’t rely on IP, sender, or domain reputation to decide if a link is clean or not. By actively surfing the website, the service can identify malicious activity and prevent it. This renders the phishing attempt useless.























