In a Nutshell
Perception Point has been identifying increasingly creative phishing campaigns that are leveraging Google services. The trend described below is composed of two techniques, requiring advanced anti-phishing software engines to detect them:
- Leveraging Google APIs and Google Sites as the hosts of phishing attacks
- Smartly designed phishing attacks using Google Docs and Google Forms
Explanation
Perception Point identified this new trend with our advanced email security service, leveraging an anti-phishing software engine along with data gathered by our Incident Response and Research teams. We spotted this attack across our customers, with over 100 attacks successfully intercepted in 7 days.
The examples provided below are only a few of many phishing campaigns we have seen targeting our customers and their key employees.
- “Google as the Host”:
In this example, we can see how attackers use Google APIs service for hosting phishing sites.
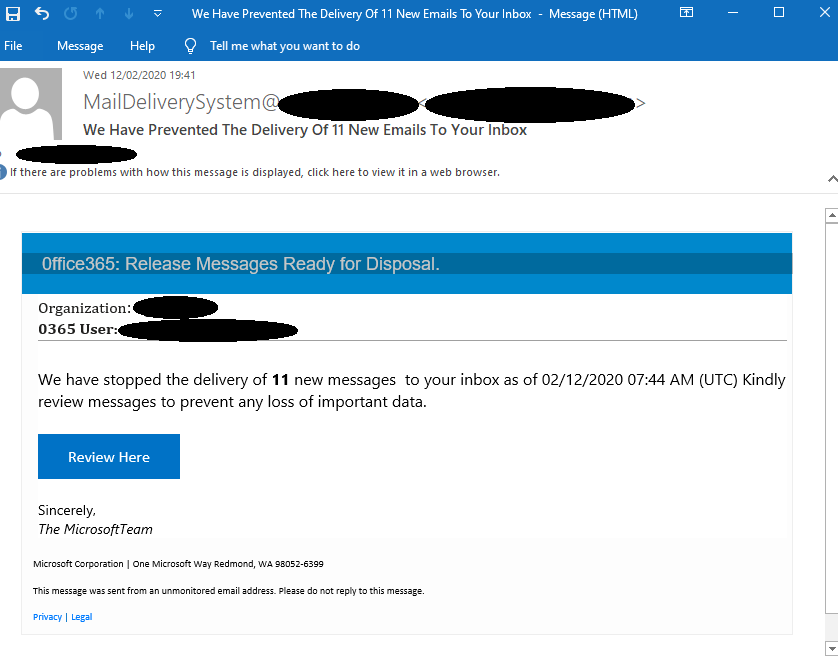
In the email above we can see how the attacker disguises himself as a Microsoft admin. This “innocent” email is actually a call for action, asking the targeted user to release emails, supposedly blocked by the email security system. However, this is a malicious email. Once the user clicks on the URL, the following phishing site is shown:
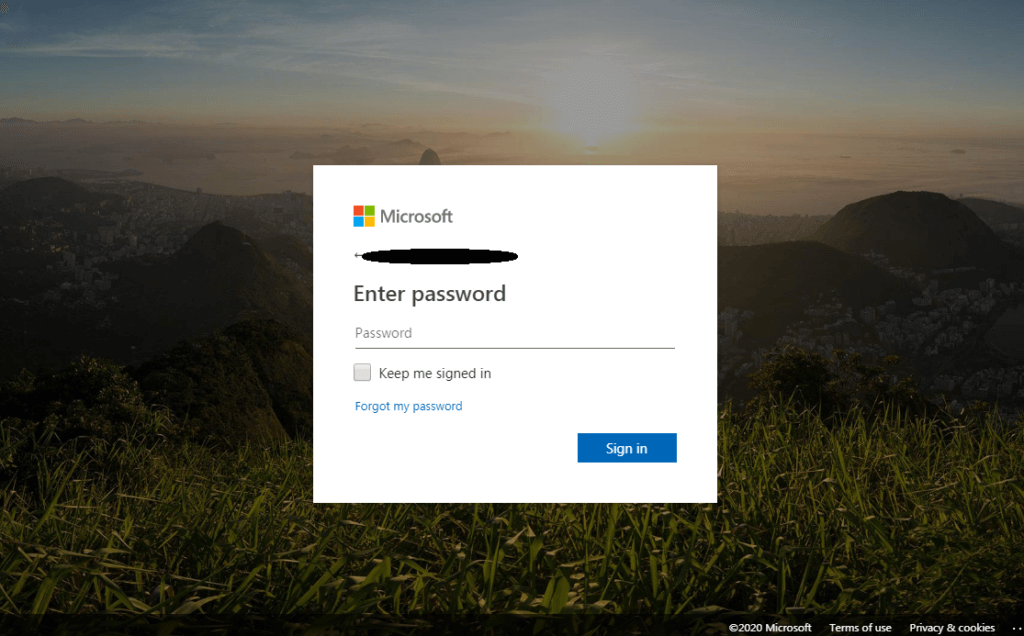
As you can see in the highlighted artifact in the picture, the attack is using the domain of Google APIs. Essentially, the attacker hosts the malicious URL on the Google APIs service. This technique is challenging for most email security systems which usually whitelist Google services, therefore, letting the attack slip through. These can be prevented with the Perception Point advanced anti-phishing software engine.
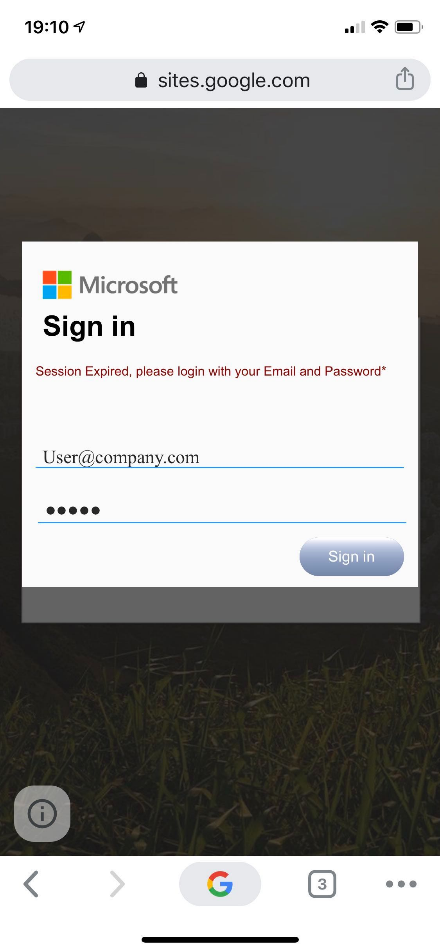
Another example is the use of the Google Sites service. Below, we can see a well-designed phishing site on which is using the “google.com” domain. This attack is very hard to detect as both the hostname of the site is reputable and the quality of the phishing look-and-feel is very high.
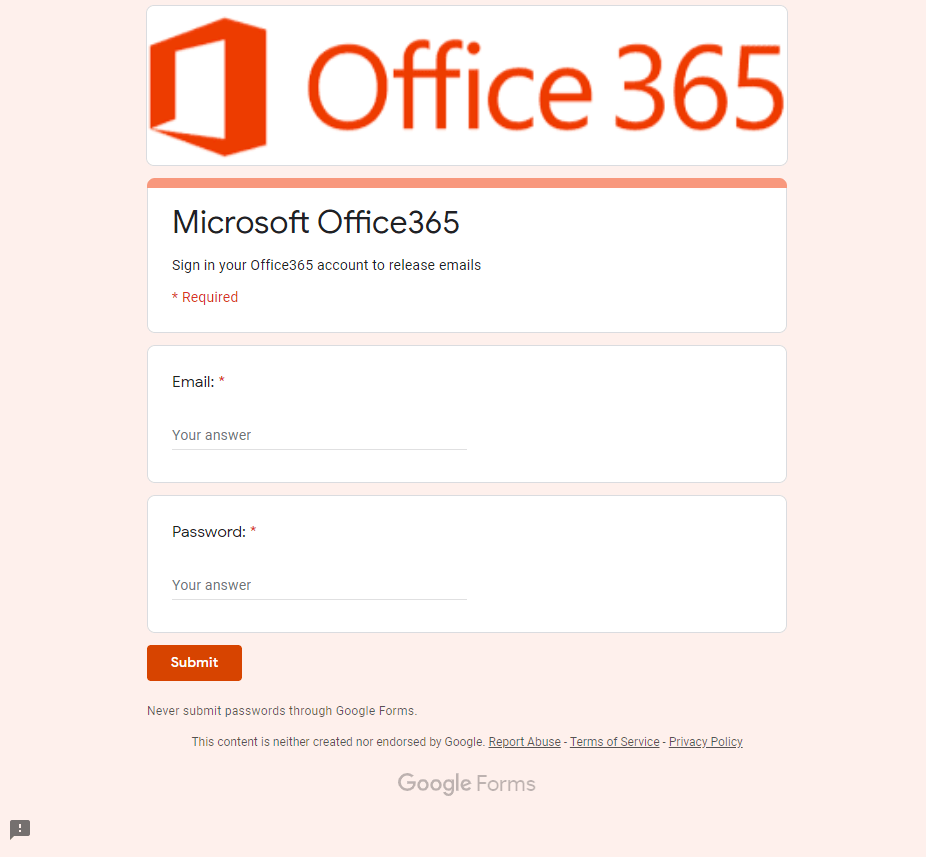
- Google is the “phisher”: In this case, the attacker turns Google into a phishing site. The attackers are now using Google Forms – a great tool to survey people and employees – to be actually a form for asking for user names and passwords. Again, since it is based on a legitimate concept, this attack can bypass the vast majority of email security vendors very easily. For example, notice how the attacker creates a fake Office 365 log-in page in Google Forms and tricks the users to enter their credentials. The interesting part is that Google is indeed aware of this threat and specifically mentions that users should “never submit passwords through Google Forms”. However, in real life, most people don’t notice this warning and are giving away their credentials to malicious actors. It is for this reason your emails security solution should support an advanced anti-phishing software engine.
Recommendations for CISOs
- Train your employees – Educate your employees on new types of phishing attacks and provide them with tools such that leverage anti-phishing software engines to identify how attackers work.
- Adopt solutions with an automated update mechanism – Since attackers always evolve and improve, we need to use technological solutions that constantly update and improve. Perception Point’s platform with its anti-phishing software engine is a SaaS and leverages this to easily update and improve its algorithms on a continuous basis. In addition, the included Incident Response team researches attacks in the wild, even before they reach our system.
- Dynamic scanning – Active scanning capabilities are key to preventing zero-day phishing attacks. Adopt solutions with anti-phishing software engines that can dynamically scan 100% of email traffic.























