We have recently identified a growing trend in the use of malicious Microsoft Office attachments to conduct attacks. The form of the attack varies (from ransomware to banking trojans), but the number of underlying techniques are limited.
For years, attackers embedded macros in Office documents to trick users and infect endpoints. However thanks to high awareness of this technique, many organizations have a strict “no macros” policy, so attachments with macros are automatically blocked – making it less attractive for hackers.
Now, attackers have found new ways to run malicious code. Rather than macros, they leverage
old, built-in features in MS office apps, accessing zero-day vulnerabilities in Office documents and 3rd party applications to embed malware inside a document. They initiate these attacks with specific exploitation techniques.
Below are the new techniques that were detected by Perception Point’s engines:
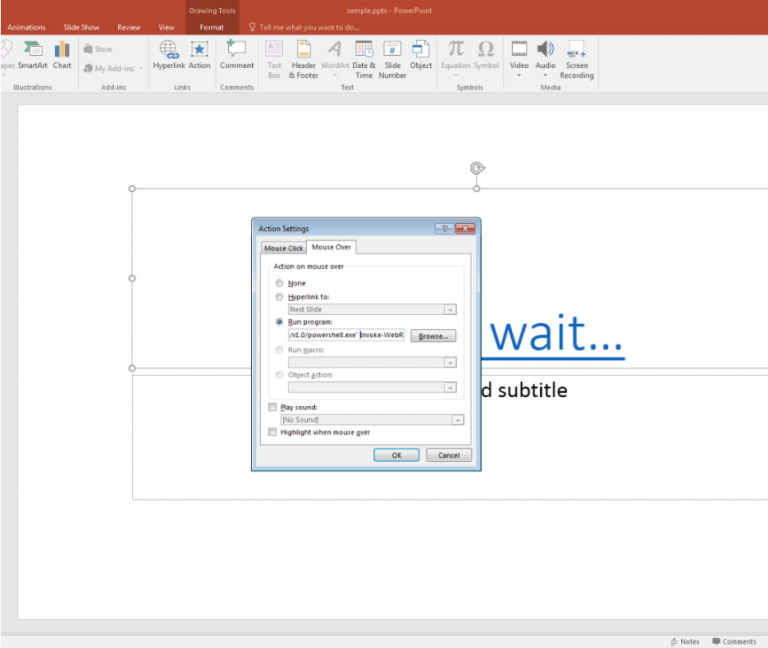
Mouse-Hover Link Attack in PowerPoint.
There is a built-in PowerPoint feature that attackers love. It enables them to create a hyperlink with a “run program” action upon a mouse click or just a hover. As simple as it sounds, once you hover your mouse over the link, malicious code executes on your computer. This is not a sophisticated attack method and it doesn’t require any hard-core hacking skills. Yet it is highly effective against untrained employees that open attachments from unknown sources.
DDE Attack 1 on Excel, PowerPoint & Word.
DDE (Dynamic Data Exchange) is an old subsystem in Windows that is used for communication between two processes. The DDE feature allows MS office programs to load data from other office programs. Attackers take advantage of this feature in order to run a command prompt with malicious commands. Microsoft won’t fix the issue because they see it as a feature and not a flaw. Documents that contain DDE look clean, do not contain any macro code, and can easily bypass common static signatures.
External Links Attack in Excel.
MS Excel has a feature called External Links, which should be used for giving referrals to external documents. Attackers use this feature to run malicious PowerShell commands. This is another method of running code from an office app without using macros.
HTA (CVE-2017-0199) attack on Word.
A vulnerability found in MS word lets an attacker embed an object into a docx file, While the document is loading this object is downloading malicious code from the internet and runs it on the victim’s computer. This kind of attack also works in Microsoft Browsers and can be sent as a link to malicious websites.
Flash embedded in document (CVE-2018-4878) – Attacks PowerPoint, Word & Excel.
The source of this attack is actually a vulnerability found originally on Flash player and not in MS office programs. Flash objects can be embedded inside office documents and attackers are then using this vulnerability. This vulnerability has been found not long ago and it is now widely used as users don’t update their Flash version. Even when Flash is disabled inside the browser – it still might run from an office app.
What can you do about this?
Attackers are always changing and enhancing their techniques in order to bypass traditional cyber security solutions. They use both simple logical bugs and advanced zero days that require high reverse engineering expertise. Once an attachment hits a victim it might be too late to stop the attack. Be sure to pen test your email system against these types of attacks, to ensure you are covered.
Perception Point’s engines detected all of these types of attacks without any prior knowledge or modifications required. If you would like to see how we can help protect you, contact us for a free demo!























