Intro.
At first glance, the ATO threat described in this blog seems like a simple, plain vanilla cyber-attack seen on a daily basis via the email channel. However, by looking into both the context and details of the attack, one can see the uniqueness of this attempt and why account takeover protection is so important:
- Email account takeover (ATO). The mail is part of a legitimate email correspondence between the targeted company and an outside stakeholder. The “injected” email and malicious payload to the ongoing email exchange indicated that the stakeholders’ email was compromised, which can lead to further attacks against other suppliers, customers, investors, and more.
- Evasion measures. The attackers jump through many loops in order to avoid detection.
Recommendations.
- The email threat landscape is vast and evolves rapidly. The only way to stop them is by taking a multi-layered approach that covers all types of attacks – “basic” and “advanced” altogether.
- Employ DMARC to authenticate email domains and minimize the opportunity for domain abuse, reducing the risk of spoofed emails.
- ֿConsider deploying internal email security solutions to scan intra-domain traffic. This will allow the organization to ensure that once an account has been breached, the attacker won’t be able to spread the malicious message across the organization.
IOCS.
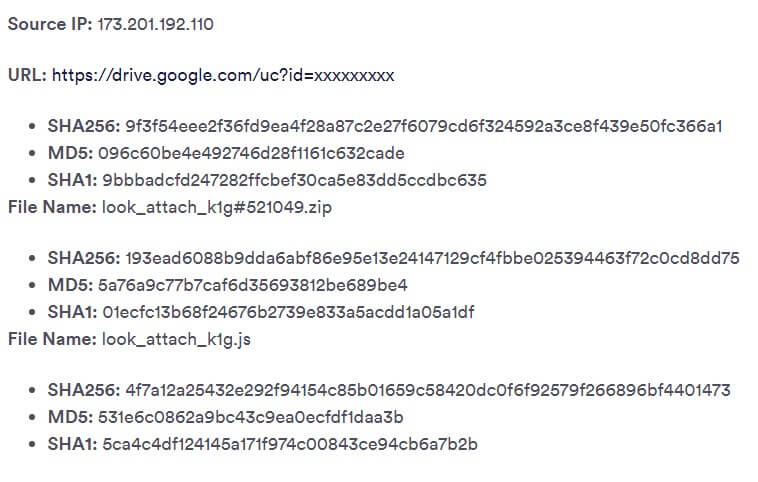
The Email.
The weaponized email was sent from a known business associate of the victim and contained a conversation thread that the victim has been having with that business associate over the past few months. We aren’t sure how the attackers intercepted the original email but we can assume that one of the business email accounts on the thread has been compromised.
However, our account takeover protection successfully identified that the attackers sent the email using an email server that isn’t associated with the business associate’s domain, triggering the Perception Point BEC Protection layer.
The IP address used, has a good reputation so traditional threat intelligence platforms would not have picked up on it. However, our account takeover protection saw this as a discrepancy since the IP has never been associated with the domain it poses to be, and could immediately identify this email as suspicious.
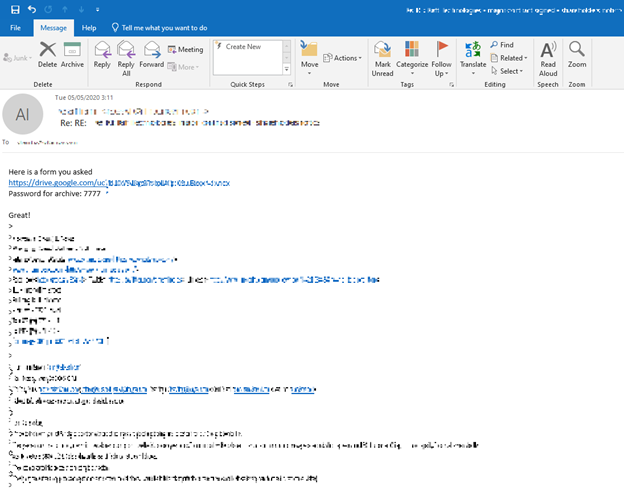
The Link.
The attackers kept it short and simple: they included a link to an archive file that they stored on the Google Drive platform. By associating Google, they aim to circumvent any suspicions the victim might have and to bypass legacy email security solutions that they thought the target company might have. We’ve seen a significant increase in the use of trusted cloud storage platforms such as OneDrive, Google Drive, Box, and Dropbox in such attacks (see examples on this blog). The Perception Point Recursive Unpacker engine interacts with each platform accordingly and retrieves the payload. This identifies the attacker’s attempt to conceal the attack, ensuring that the Perception Point platform scans every piece of content sent.
The Encrypted Archive.
The attackers encrypted the archive and provided the victim with the password in the body of the email. This is most likely done to circumvent security solutions that inspect the file such as firewalls and antivirus software. Again, the Recursive Unpacker successfully decrypts the encrypted archive with the provided password and continues unpacking the content within, rendering the attackers attempt to hide the malicious payload useless.
The JS file – The Actual Malware.
Down the rabbit hole we go, arriving at the final stage of the attack; a JavaScript file. This file is heavily obfuscated and writes a file to the disk and executes it. This essentially is the end of the Exploitation stage or Delivery stage and from here the malware installed communicates with its operators and performs malicious tasks on their behalf.
Summary.
Multilayer attacks require multi-layer defenses like account takeover protection. Three detection layers in our platform flagged this attack:
- BEC layer. Identifies suspicious activity in the email and source IP level.
- The Recursive Unpacker. The unfolding and uncovering of deeply embedded attacks and other evasion measures, which include extracting content from archive files, decrypting password-protected files.
- The HAP. A next-gen dynamic engine that intercepts advanced attacks in the exploit stage.
This example evidently shows how attackers are continuously evolving to avoid detection. Security and email experts should prepare their organizations with sophisticated account takeover protection.























