In the past few weeks, there has been a rise in XML-related phishing attacks. These attacks begin when attackers send unsuspecting users malicious emails containing XML files. When opened, the file displays a fake login page with a blurred document in the background. The user is then asked to enter their email password to view the document. This is the beginning and the end to a classic phishing attack.
What is XML?
If you’re unfamiliar, XML is a simple, text-based format for representing structured information, like documents, data, configurations, books, transactions, and invoices. XML is one of the most widely used formats for sharing structured information today—between programs, people, and computers both locally and across networks. Receiving an XML file like the one in this attack shouldn’t raise any red flags for you…but it should for your email security provider.
TTYL XML
This new XML attack was caught by a set of rules, defined within Perception Point’s advanced threat detection platform, that determine suspicious email behavior. The content of the malicious email itself is simple: it directs the user to open the attached XML file in order to view a document or PDF. The novelty of this attack is that once a user opens the XML file, they are redirected to a phishing site via hidden HTML code (refer to Figure 5).
Usually, cyber defense systems recognize the XML file in its intended form (data), rather than executing the HTML script embedded within the file. This method of disguising an HTML phishing site as an XML file allows attackers to bypass and evade most means of detection. However, the only way to open an XML file is with an XML viewer. Since most users don’t have XML viewers, our platform approached the document like a user would: opening the file in a browser. By doing this, we were able to see the HTML and the phishing site, just as a user would.
Attack Breakdown
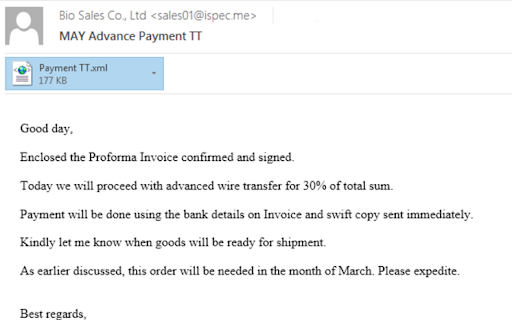
Figure 1: The user receives the malicious email with the attached XML file.

Figure 2: What appears when most systems open the XML file.
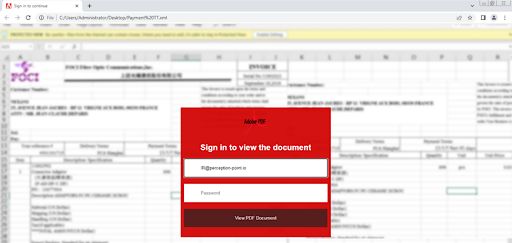
Figure 3: When opening the XML file in a web browser, a spoofed Adobe login page appears with the username already filled in. This is a known tactic used by attackers to deceive users. When an individual sees their username on a login page, oftentimes they enter their password automatically without thinking about the legitimacy of the site.
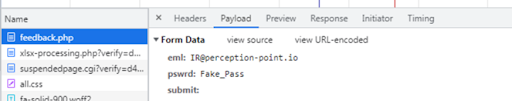
Figure 4: After filling in their password, the user prompts a post request, which is sent to the hacker with the victim’s credentials
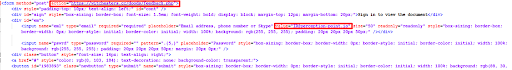
Figure 5: Upon investigating the HTML code, Perception Point’s team of researchers identified the “injected” HTML form. The recipient’s email address is already part of the HTML code; their credentials are sent directly to the attacker (feedback.php) when the scam is complete.
This phishing attack isn’t unique in its objective, but its technique is something to pay attention to. As hackers get more creative in their means to bypass defenses, so too must those behind the detection technology. Attack attempts like these enhance Perception Point’s advanced threat detection platform by preparing and informing it to stop similar attempts in the future.
For more information on attacks like this one, check out our blog.
A special thanks to Din Serussi, Igal Lytzki and the Perception Point IR team on their research for this post.























