If you read our last post, it will be no surprise to you that attackers have taken advantage of the COVID-19 pandemic. More COVID-19-themed cyberattack campaigns have popped up, featuring methods like malware, phishing, and BEC. In this post we provide more examples of COVID-19 campaigns, caught by our advanced threat detection platform and analyzed by our Incident Response team. Read on to learn more.
Malware Campaign 1:
Executable file inside of a disk image
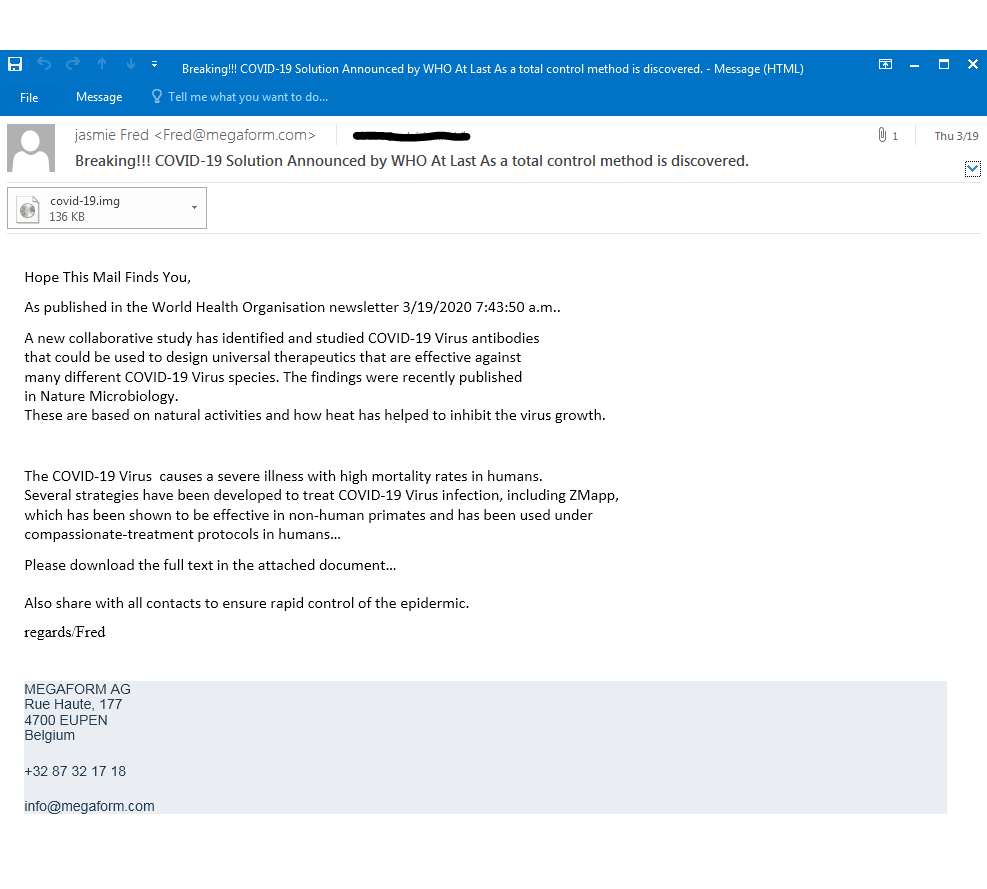
In this attack the attacker claims to be an employee of a European company and is attempting to spread fake news that the COVID-19 vaccine has been found. The attacker asks recipients to download the attached document for full access. However, once the recipients open the file, the malicious executable below is waiting for them:
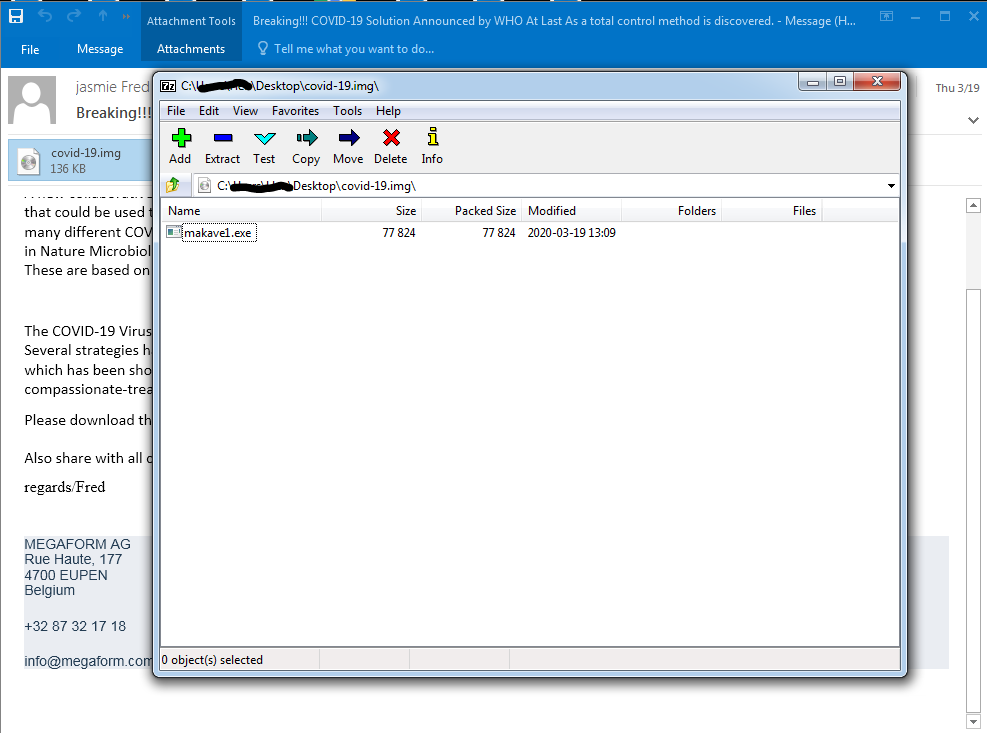
Malware Campaign 2:
Compressed executable file by WHO
Next, this attack combined two techniques: malicious payload on top of impersonation. In this attack the attacker spoofed the domain to look like the email was sent by the World Health Organization (WHO).
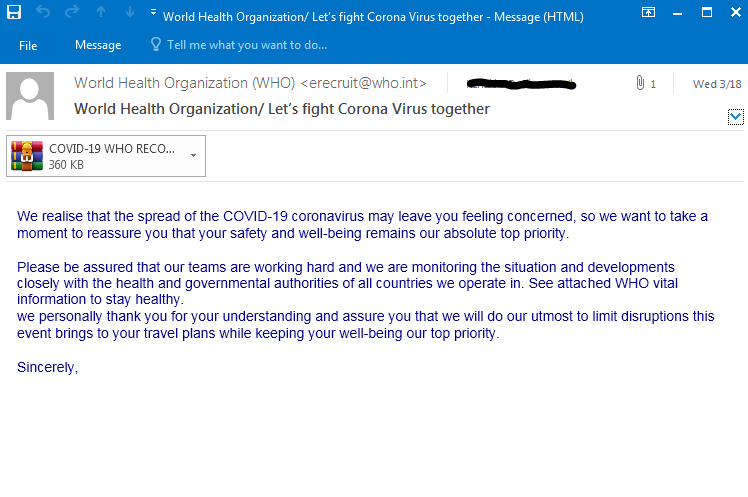
Our IR team came across this campaign on March 18, 2020 sent to several different global clients. In this campaign, the attacker claims to be part of the World Health Organization and attaches a file that contains “official WHO vital information”. If the recipient opens this file, they will find the below malicious executable file:
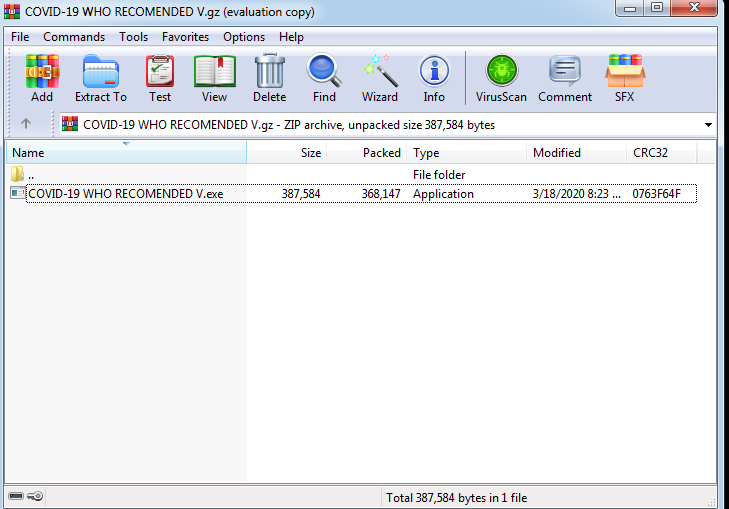
Conclusion
The examples above show the emergence of a new type of attack. As adapt to the COVID-19 pandemic, we must also face the reality that attackers aim to leverage such a devastating situation for their own benefit. We can see and we will continue to see attackers using the pandemic as an asset in their cyberattacks. Whether it is by using domain-spoofing to look like a trusted source or installing malicious malware within “critical and informing” files/links.
Learn more about protecting your organization in our detailed guide to cyber security strategy.























