Technology is only as good as the people behind it. Our highly skilled Incident Response team provides the essential human element to our cybersecurity solution. Often referred to as an “extension of our SOC team” by our customers, the IR team is available 24/7 to engage with end users and monitor, analyze, and maintain safe content-sharing networks. Let’s see the latest cyber scams analyzed by the Perception Point IR team.
The Roundup
Every day, our Incident Response team reviews hundreds of emails and files intercepted and flagged by our system, analyzing new attack trends and sometimes intervening in real-time to remediate attacks. In this article, we share a few recent examples of interesting attacks hailing from different regions around the globe that our advanced email security solution prevented, which were then analyzed by the IR team.
Postmasters Beware: A Phishing Attack that Leverages a Chatbot in both English and French
Canada is the first stop in our phishing tour of the world wide web. Written in French, the sender poses as the Canada Post, a seemingly official and trustworthy source.
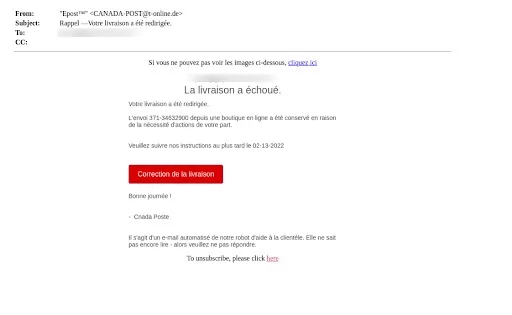
Figure 1: The end user is alerted to a “failed delivery” and is told to “fix delivery.”
When the end user clicks on the malicious link to “fix delivery,” they are transferred to a website and prompted to interact with a chatbot:
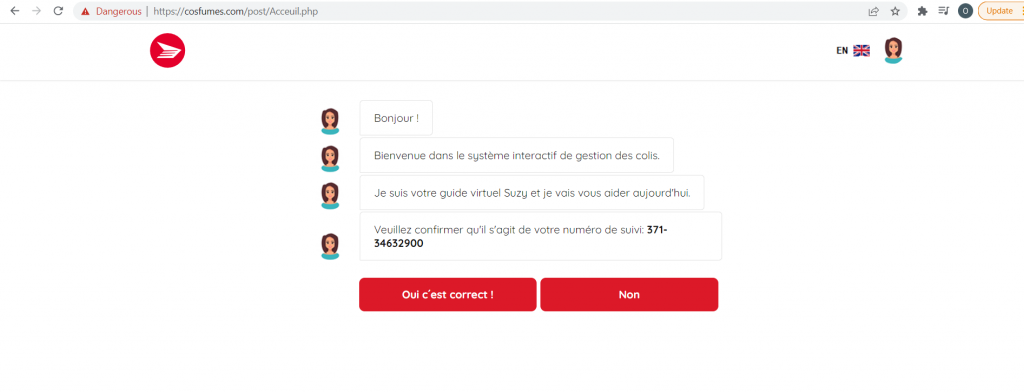
Figure 2: Chatbot conversation begins on the phishing site (French).
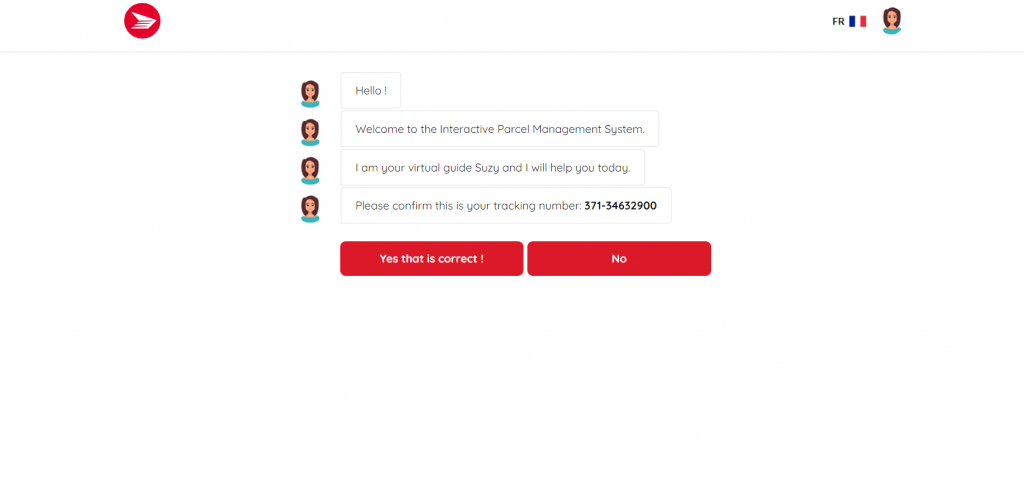
Figure 3: Chatbot conversation begins on the phishing site (English).
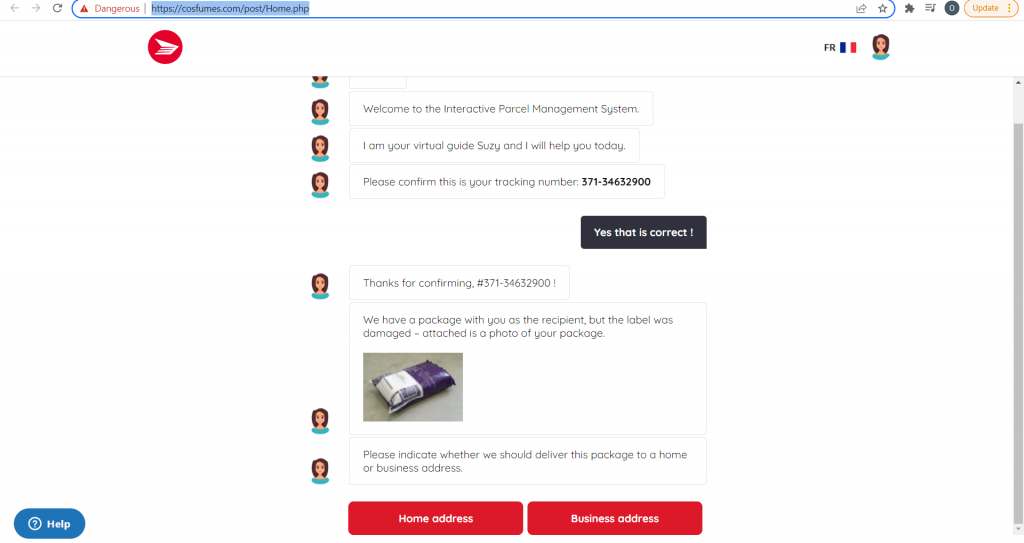
Figure 4: The chatbot asks the user where the package should be delivered.
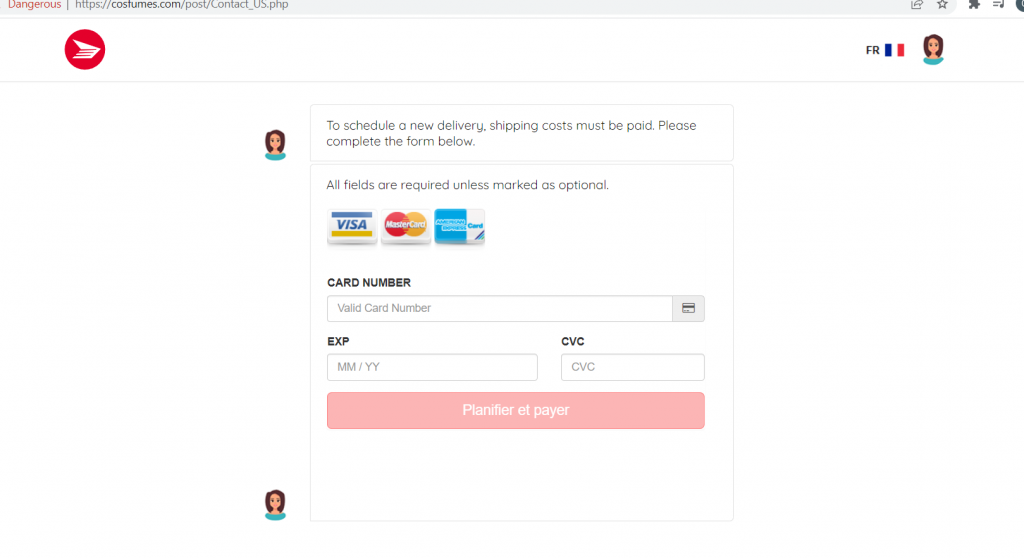
Figure 5: The chatbot requests a payment method for the new delivery.
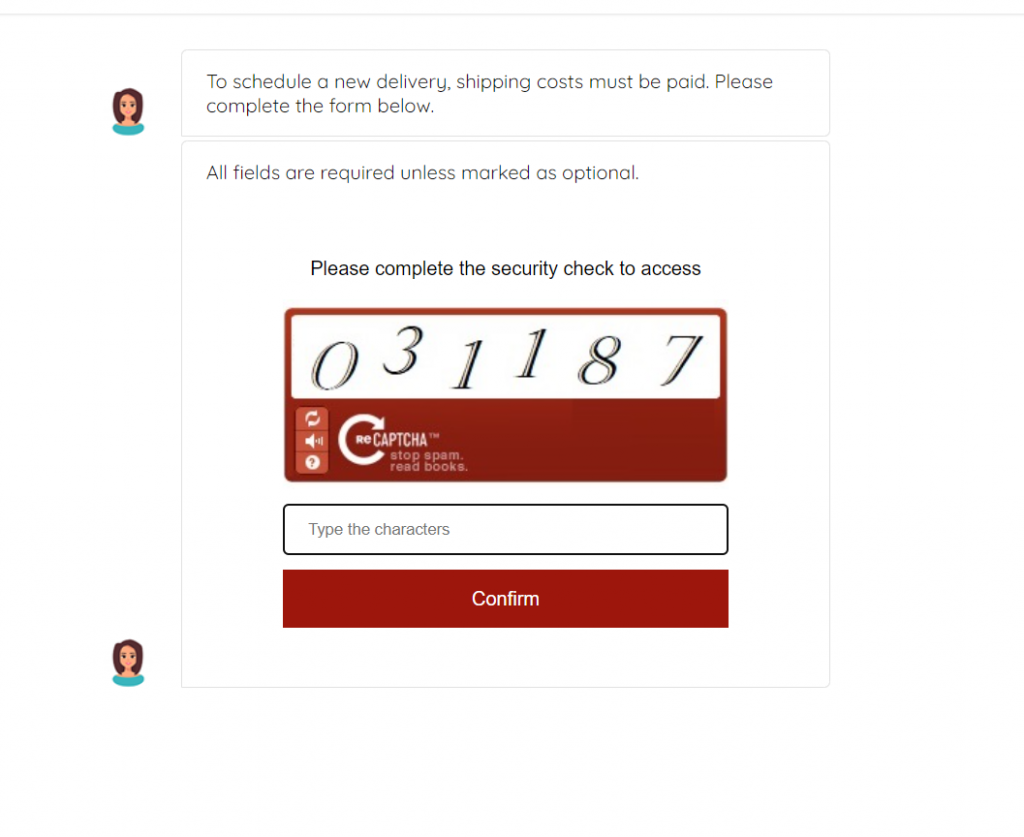
Figure 6: To add another layer of “legitimacy” to this phishing scam, the user is asked to complete a “captcha” security check to confirm the transaction.
This is one of the first times our IR team has seen such a complex phishing attack in both French and English, coming from a “post office.”
Multiple Login Options for More Credibility
We head South to the United States for these next interesting phishing campaigns.
The first phishing attack spoofs Dropbox. What makes it different from other phishing campaigns requesting credentials is its inclusion of multiple login options.
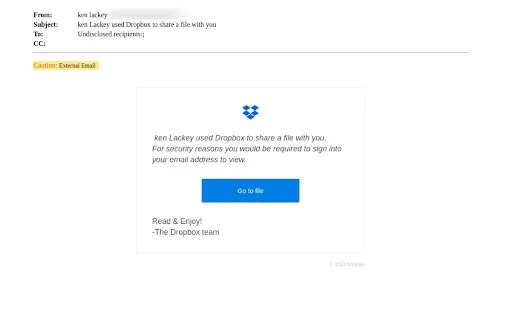
Figure 7: The user receives an email appearing to be a file-sharing notification from Dropbox.
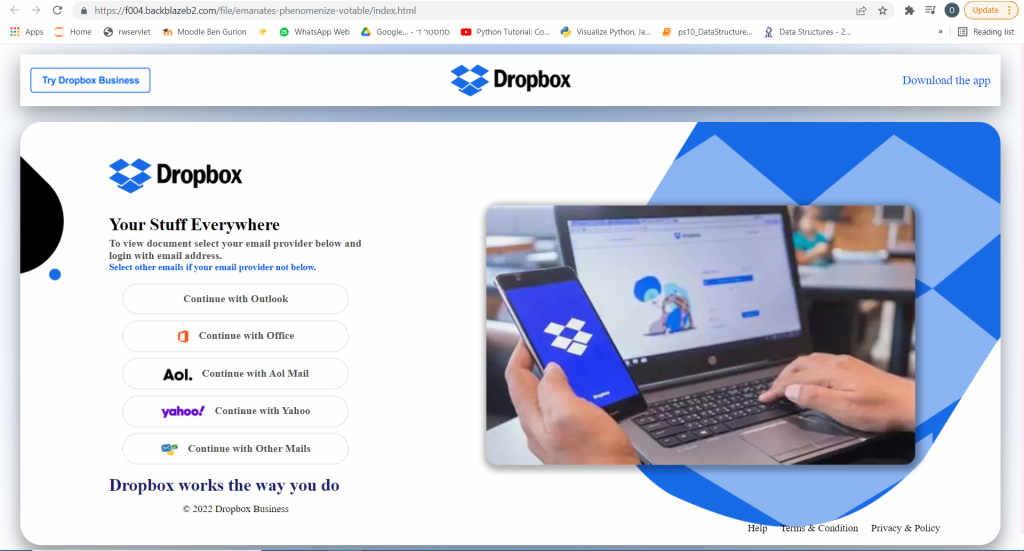
Figure 8: After clicking the link, the user is directed to a Dropbox login page with five different login entry options.

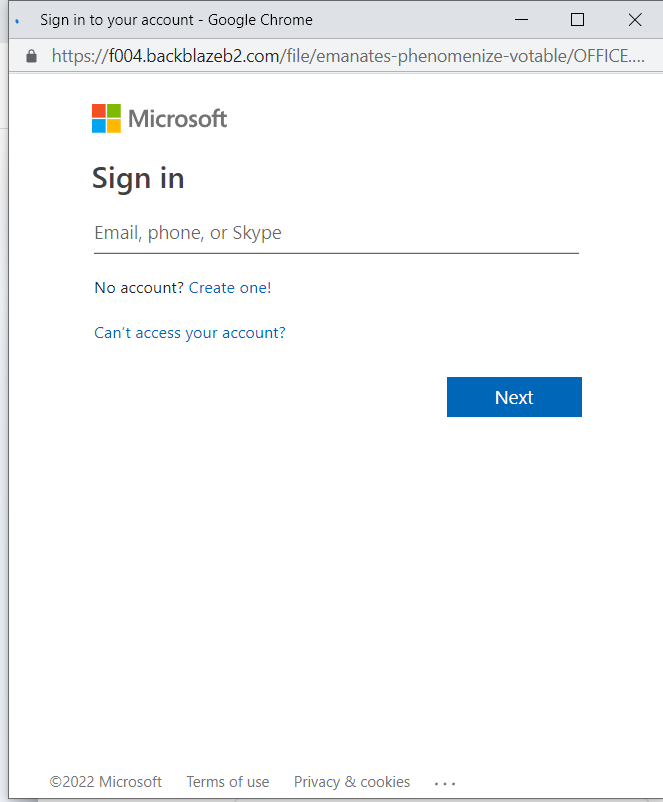
Figure 9 &10: When clicking on a login option, the user is redirected to an option-specific login page.
By offering these login options, the phishing attack appears more legitimate to the user. These options also increase the number of credentials given to the attacker by not limiting the entry point.
Personalization to Trick the Victim
In this next attack also focused in the United States, the cyberattackers impersonate WeTransfer, a major file-sharing service. More than just sending out a generic WeTransfer login page, the scam goes further by personalizing the spoofed site for the recipient.
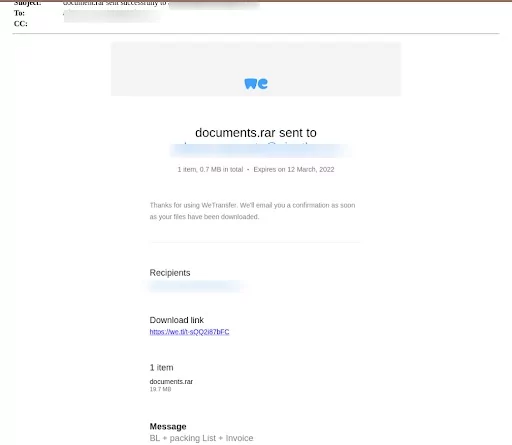
Figure 11: The user receives a fake email from a spoofed address, claiming a file has been shared with the user.
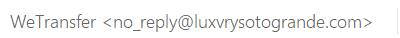
Figure 12: The sender appears as “WeTransfer,” yet when expanded it is clearly a spoofed email address.
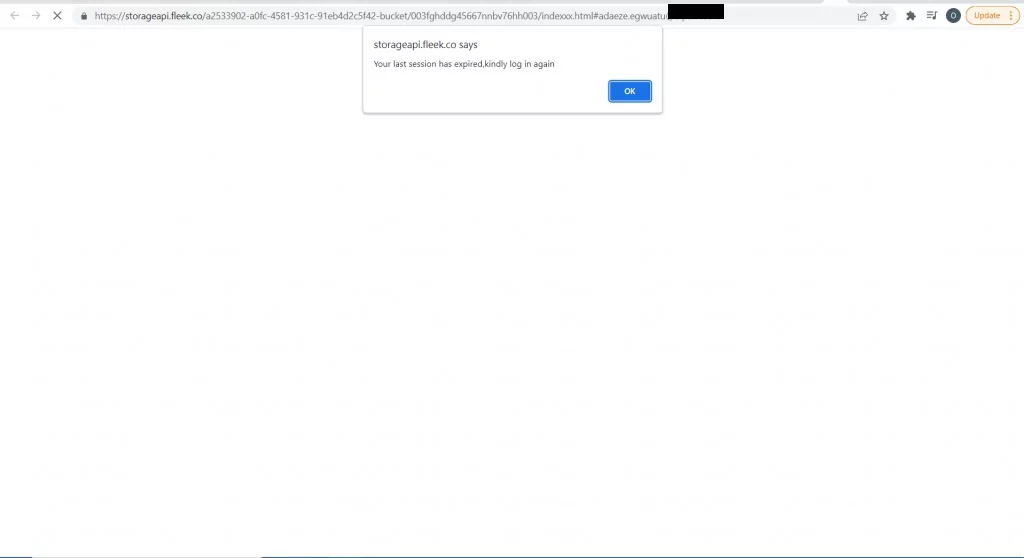
Figure 13: Once the user clicks on the link embedded in the email, they are directed to a WeTransfer site and asked to log in again.
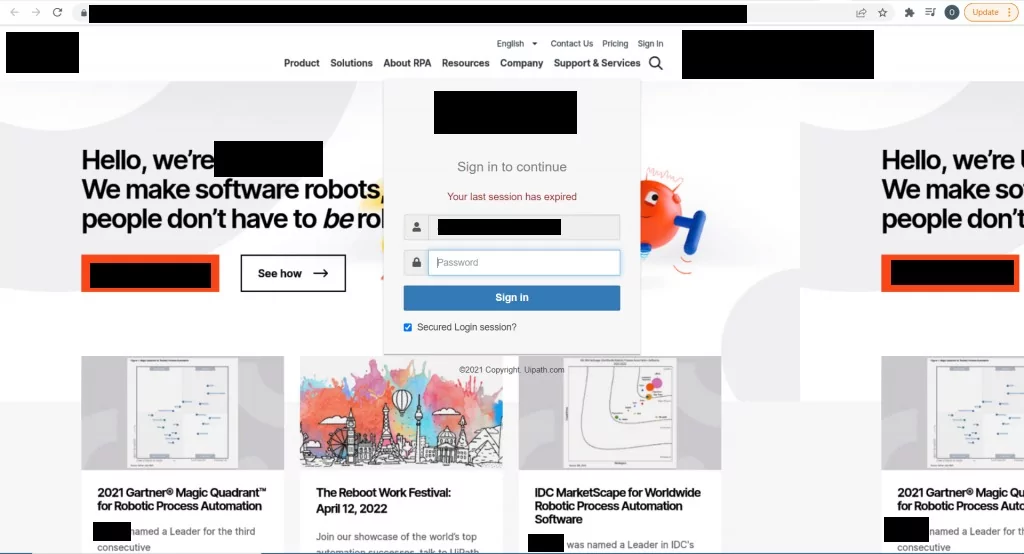
Figure 14: The user is then directed to what appears to be their organization’s website, where they are asked to enter their login details.
What is unique about this attack is that instead of requesting credentials for a more general website like Office365, the attackers personalized the site to mimic the recipient’s company site, adding another dangerous layer of “authenticity” to the phishing scam.
Buongiorno, Banks!
Our next stop is across the Atlantic, situated on the Mediterranean. These next phishing attacks are conducted in Italian.
Here, the sender impersonates UniCredit:

Figure 15: The email directs the user to enter missing information by March 12, 2022 or their account will be suspended.
This sense of urgency which plays on the victims’ emotions, is a typical tactic used by attackers.
UniCredit wasn’t the only Italian financial institution targeted–cyberattackers also made sure to pose as Italy’s largest bank, Intesa Sanpaolo:
This phishing attack uses a spoofed website that is nearly an exact replica of the bank’s actual site.

Figure 16: The spoofed email address and the greeting “Gentile Cliente” (generalized, not personalized) are basic indicators that this is a malicious email.
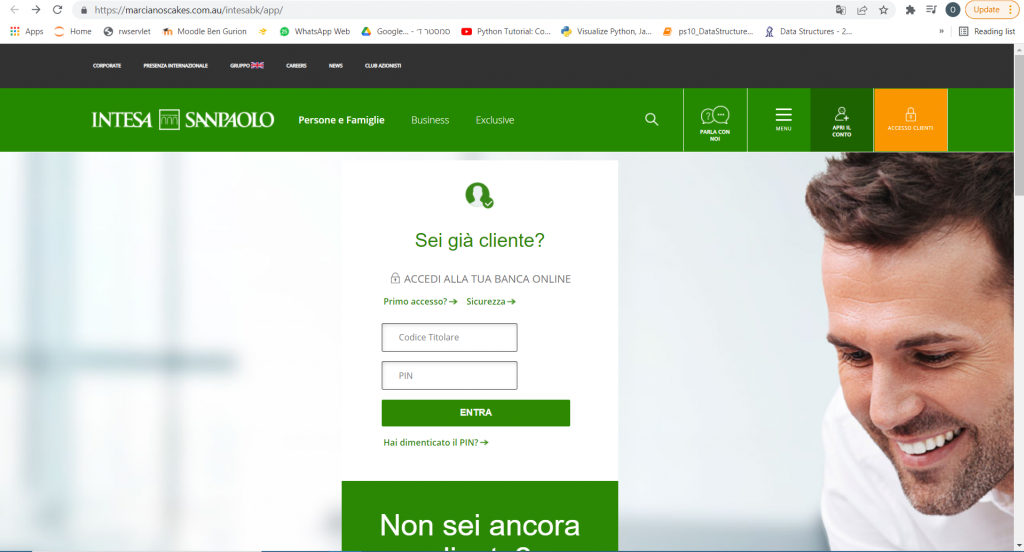
Figure 17: All of the links on the site work and lead to the real website.
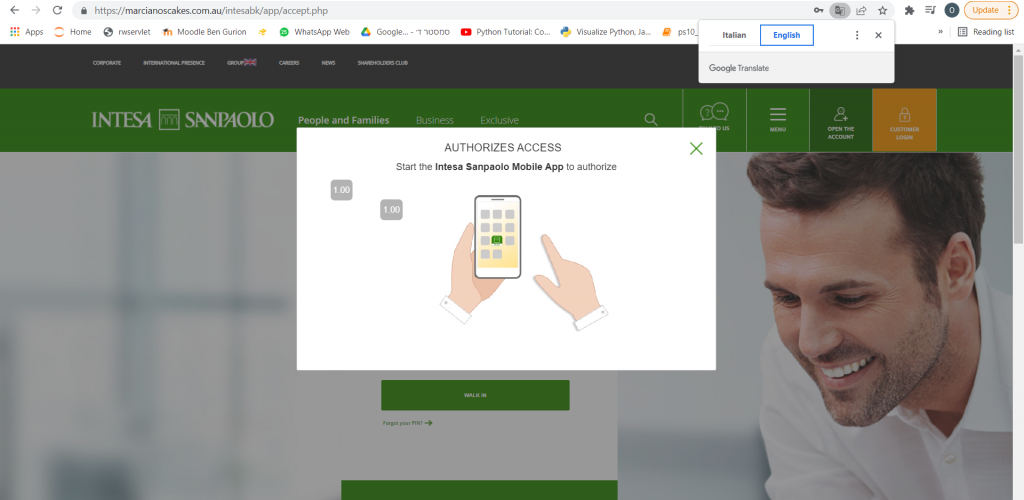
Figure 18: Once a user enters their information on the first page, a popup appears, asking for two-factor authentication and instructing the user to connect with the bank’s phone application.
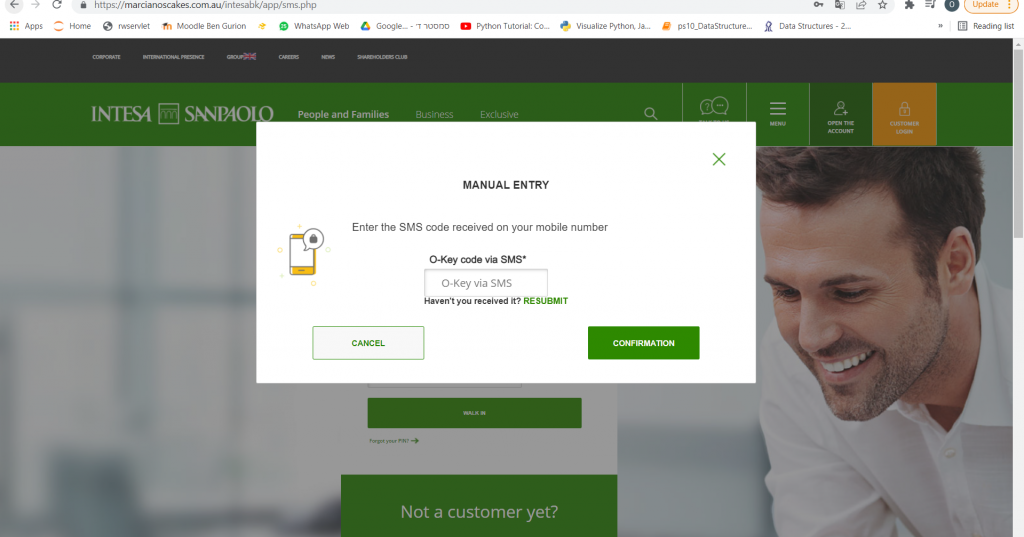
Figure 19: Two factor authentication
What makes this scam so realistic and seemingly legitimate is its incorporation of the banking application and the user’s phone, not just their bank login information.
If it were not for the URLs and the email content, this phishing attack would be nearly undetectable. Check out Intesa SanPaolo’s actual website here.
Plenty of Phish in the Sea
Our last stop is Japan, where there are some interesting ongoing local phishing campaigns.
The clock is ticking in this American Express phishing scam.
Upon first glance at the sender’s email, it is clearly not affiliated with American Express, yet the recipient likely only sees the name, not the full email address. The email says that a transaction must be authorized for the card 37XX XXXXXX XX003. If authorization is not given, the card and the account will be locked and removed.
What is particularly dangerous about this example is the sense of urgency felt by the recipient. It is a time-bound request from American Express, legitimized by the potential first and last digits of the recipient’s card.
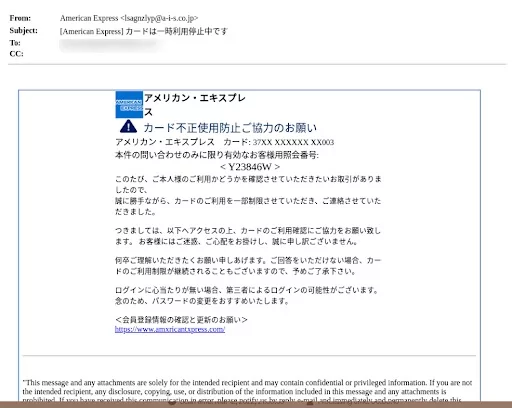
Figure 20: American Express phishing email – note the misspelled website at the bottom.
Yodobashi, a major Japanese electronic retail chain is impersonated by cyberattackers.
Like most phishing attacks, the email informs the user that since there has been an update in the system, the user must update his details.
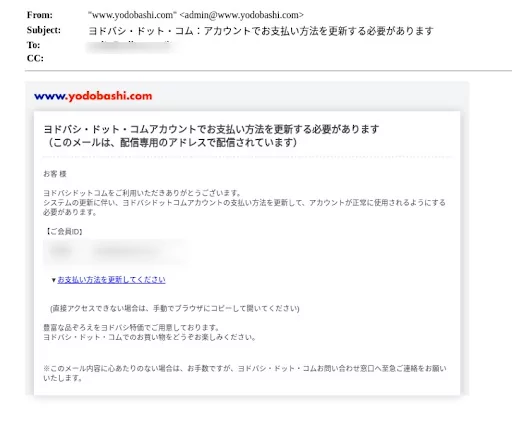
Figure 21: The user is prompted to enter their credentials into a malicious website posing as the electronic retailer’s official site.
Last but not least, a phishing attack poses as Japanese credit card company, UC Card
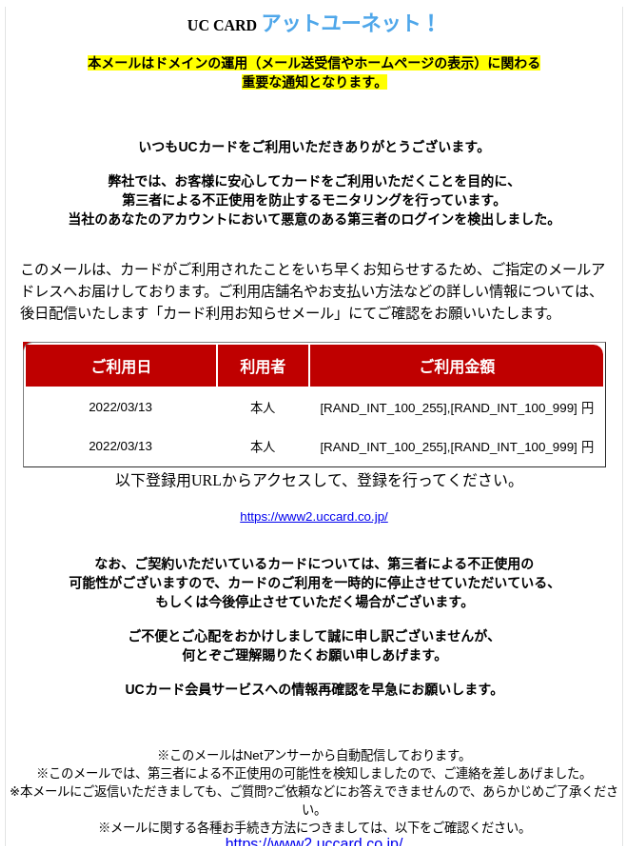
Figure 22: The email expresses that there may have been an unauthorized transaction on the user’s card, itemizing some of the purchases made (the red table) and making the situation seemingly more real to the user. Because of this unusual activity, the company has “canceled” the user’s card.
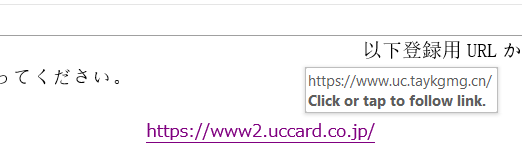
Figure 23: To reactivate the user’s card, the user must enter their information in the included link, which of course leads to a malicious site soliciting user credentials.
Summary
Cyberattackers and their phishing techniques are more creative, more sophisticated, and more widespread than ever before. It is the fine details that make malicious sites and spoofed emails so believable to end users. If our advanced email security solution hadn’t caught these attempts, they could have easily landed in our customers’ inboxes, prime for opening by an unsuspecting end user.
Want to learn more about our detection technology? Book a demo today!
Here’s some related content you may enjoy: How to Prevent Phishing
























