Overview.
In this campaign, the attacker has been relatively specific with his targets, by creating a targeted “Chase Bank” phishing attack. This email has been caught in several different clients of ours with certain elements in the “Subject” or “From” address changing slightly across each target but with the same link and threat. Thanks mainly to two of Perception Point’s unique engines, our Deep Scanning (the Recursive Unpacker engine) and our Image-Recognition phishing algorithms.
IOCs:
Subject: Theft Warning: Fraud Activity
From: Chase Online Team [email protected]
Source IP: 194.25.134.18
Extracted Links: https[:]//qiwi[.]io/eTk
Attack Breakdown.
As can be seen below in the original email screenshot, the attacker has attempted to look like the real Chase Bank in a few tactical ways:
- From Address: At first glance, the end-user is seeing a genuine looking from name that they are familiar with: “Chase Online Team”.
- Subject: The attacker is making the email seem urgent and try make the end-user act fast and miss the little details. The title “Theft Warning:Fraud Activity” coming from your bank makes one not think twice.
- Body of Email: The attacker has used the real logo of chase bank and made a generic Chase Bank email template scaring the end-user that unusual activity has been detected in their account and offers them a way to directly check this activity.
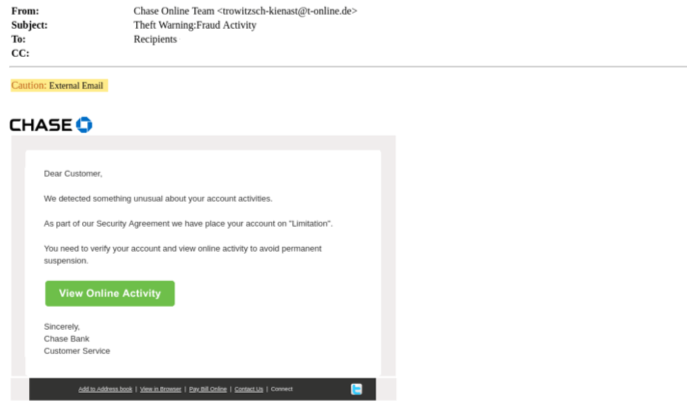
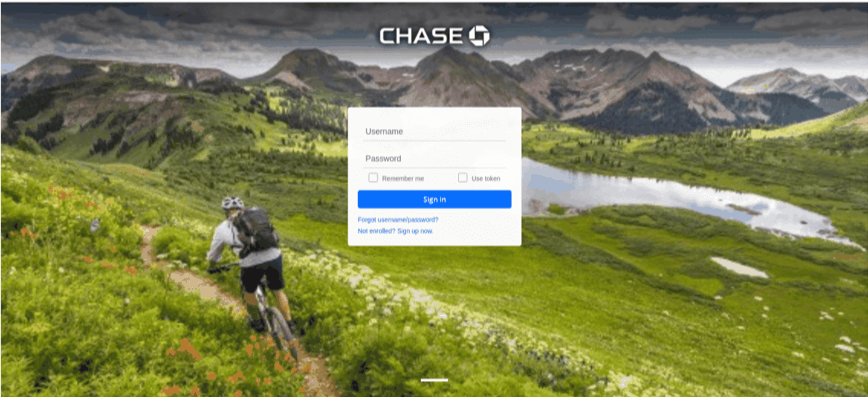
The unsuspecting end-user is deceived into clicking on the button in the body of the email, which takes them to the below legitimate looking website. From first look it is the Chase Bank log in page, however this is just a phishing website. Once the end-users attempt to “log-in”, the attacker will steal their credentials, giving the attacker direct access into the end-users’ bank account.
Here’s some related content you may enjoy: How to Prevent Ransomware























