Our Incident Response team has selected their “Top 4 fake it till you make it” phishing tricks that they have seen over the months of September and October. The tricks and techniques that attackers are using continue to become more creative, manipulative, and more difficult to recognize by the end-user.
1. Brand Identity
Brand identity is the collection of all elements that a company creates to portray the right image to its consumer. Your brand identity is what makes you instantly recognizable to your customers. Think of the two yellow arches of McDonald’s or the Nike “swoosh.” This instant recognition is what attackers take advantage of.
The attacker wants to earn the end-user’s trust as early as possible, without causing suspicion. In order to do so, the attacker attempts to disguise himself as much as possible to aesthetically look like a legitimate, trusted, global brand. There are many levels of professionalism/research in these types of phishing “tricks” and several different aspects, such as Typography, Color Palette, Form/shape, Logo, and more that are used to achieve this.
A good example can be seen below. In this attack, the attacker is attempting to look like DHL and trick the end-user into opening a malicious Excel. One can instantly see the use of the logo, the high-quality picture, and the formality of text. The attacker even took the time to sign the email with a different color, making it look like the original emails DHL sends.
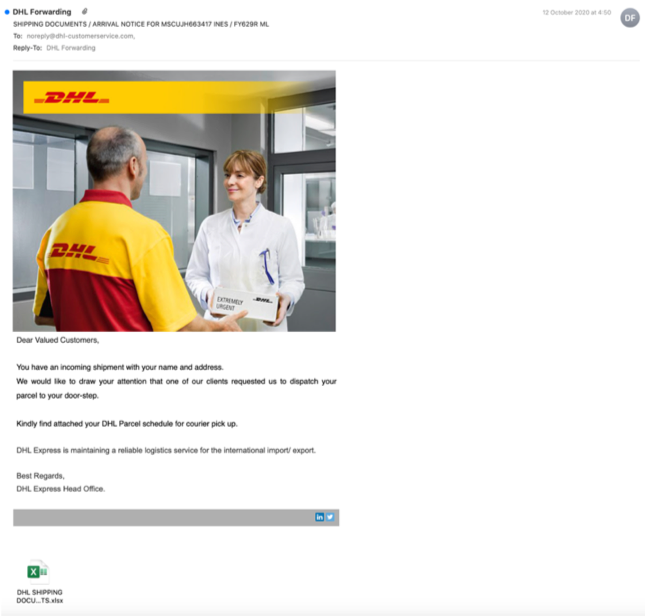
2. Domain Impersonation
The domain impersonation technique is when the attacker successfully disguises their sender domain with a legitimate, trusted brand’s domain, in order to gain the recipient’s trust and perform malicious behavior, such as credential theft. The top-5 impersonated brands we saw in the months of September-October are Microsoft, WeTransfer, DHL, GitHub, and American Express. This shows that attackers don’t focus on one industry, but are using brands across different industries to attacks targets.
In the example below, we can see great use of the domain impersonation technique. The attacker has not only displayed the name “American Express Online Service”, but even the domain address that he is sending from also looks to be legitimate “@americanexpreess.com” (note the extra ‘e’).
Domain impersonation and domain address spoofing are both strong tools in the attackers’ toolbox – and using both of them in the same attack, increases the chances to trick end-users even more.
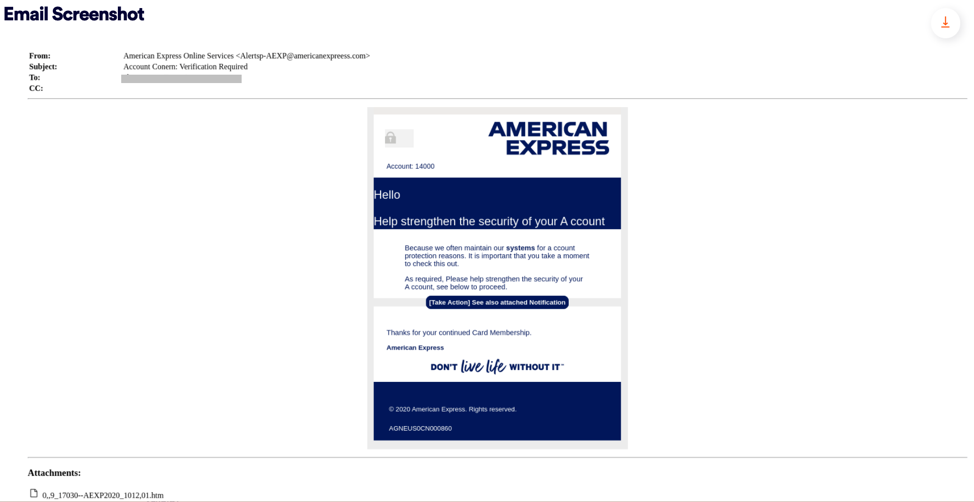
3. Evasion Techniques
There are many different evasion techniques that are utilized by the attacker. A popular one for this month is when the attacker tries to embed malicious content within files/URLs, in order to bury/hide the malicious payload from security vendors and the end-user. It is very difficult for most vendors to scan multiple objects within an email, even if not concealed, and it’s even more true when they are deeply embedded. For that reason, the attacker attempts to put many different layers of legitimate links/documents before getting to the actual payload. Some other popular “hiding” techniques include:
- Files delivered via cloud storage platforms
- Archive files in almost any format
- Links in calendar invites
- Links inside images and QR codes
A complex and unique version of embedment can be seen in the example below caught in the Perception Point system. The attacker has tried very hard to hide the malicious payload within multiple legitimate URLs and documents.
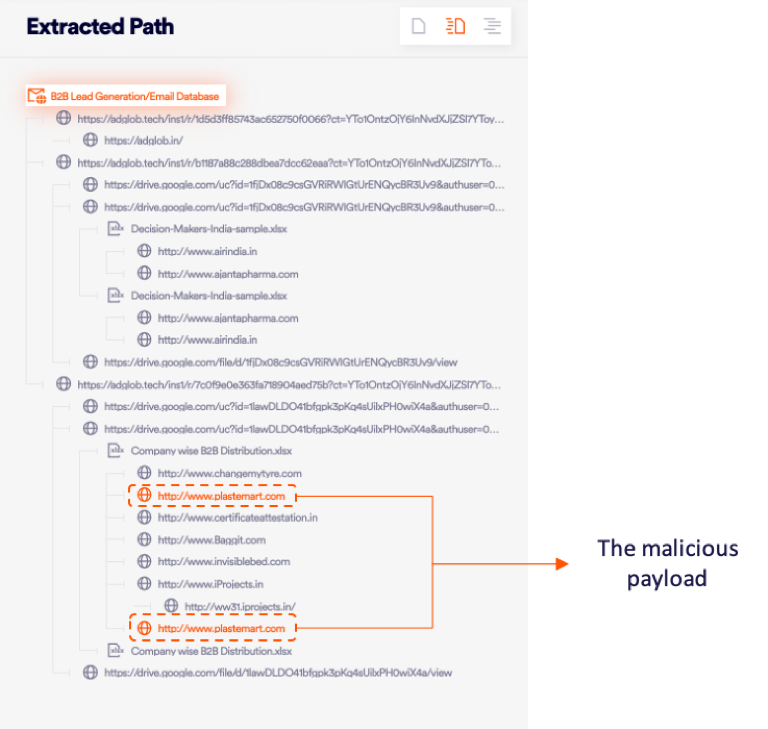
4. Body of the email
So far, we have talked about the more “design,” or the “framework,” aspects of the attacker’s phishing tricks. The next one is purely tricking the end-user with text in order to perform some kind of action, such as clicking on a link, opening a document, etc. There are many different fake reasons and styles for this type of trick, some of them include:
- The friend tactic
- The billing problem
- The expiration date
- Bank password change
- Email stuck in quarantine
- HR problem
As can be seen in the below email body, the attacker has used several of the “framework” techniques (domain impersonation, sender impersonation, logo, etc.). However, the attacker chose a different path to trick the end-user – relying on the text itself to create the manipulation. Professionally, this is called a payload-less attack – i.e. it does not involve a payload (File/URL). Instead, the attacker has attempted to construct a well-written text in the body of the email in order to convince the end-user into donating for the WHO organization, due to the COVID pandemic – although it’s simply an attempt to steal money to the attacker’s personal crypto-currency account.
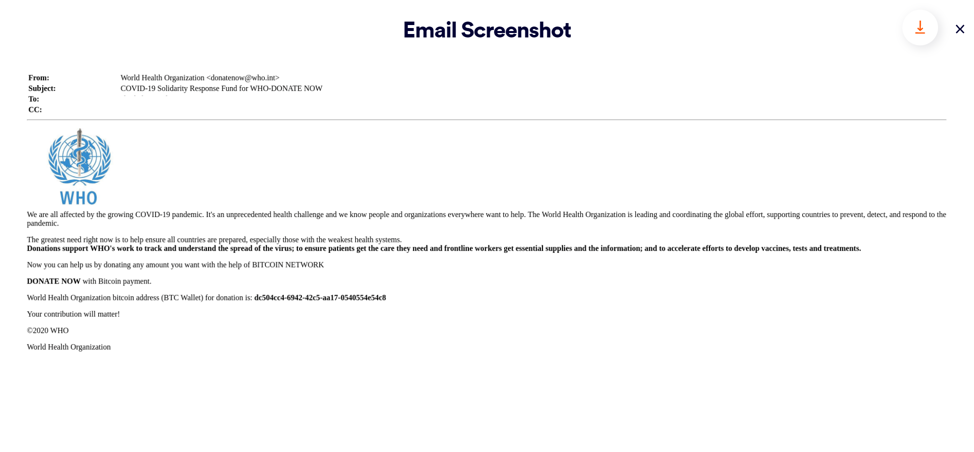
Perception Point – In a nutshell
Perception Point deploys 7-layers of prevention in order to protect against all types and techniques of malicious attacks entering an organization. Perception Point’s unique AI-powered BEC engine, image-recognition anti-phishing engines, and the ultimate anti-evasion engine – The Recursive Unpacker, all worked together in order to successfully prevent the above “Fake it till you make it” type attacks from entering our global clients.
We encourage you to learn more about the topic in previous posts we have published and to learn about what we can do to protect your organization from either phishing or BEC attacks.























