Perception Point Researchers Discover New Evasion Technique
On May 2, 2022 our team of expert security analysts and researchers discovered a new evasion technique aimed to bypass email security systems. The technique utilizes the “@” symbol to conceal malicious sites and evade detection. Our IR team noticed the technique employed in cyberattack attempts across multiple organizations. While the actors are still unknown, our IR team was able to identify the IP address 202.172.25.42, originating in Japan.
How We Found It
Our Incident Response team first identified this evasion technique when they noticed an irregular URL embedded in an email. The email itself is a standard example of phishing. The threat actor sends an email spoofing Microsoft and prompts the user to click on the link included within the email. The user is then redirected to a fake Microsoft login page, where the goal of the attack is made clear: gain user credentials.
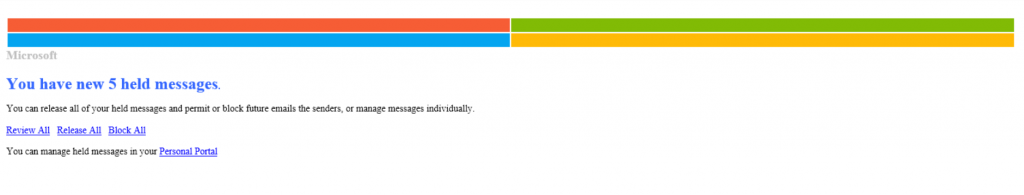
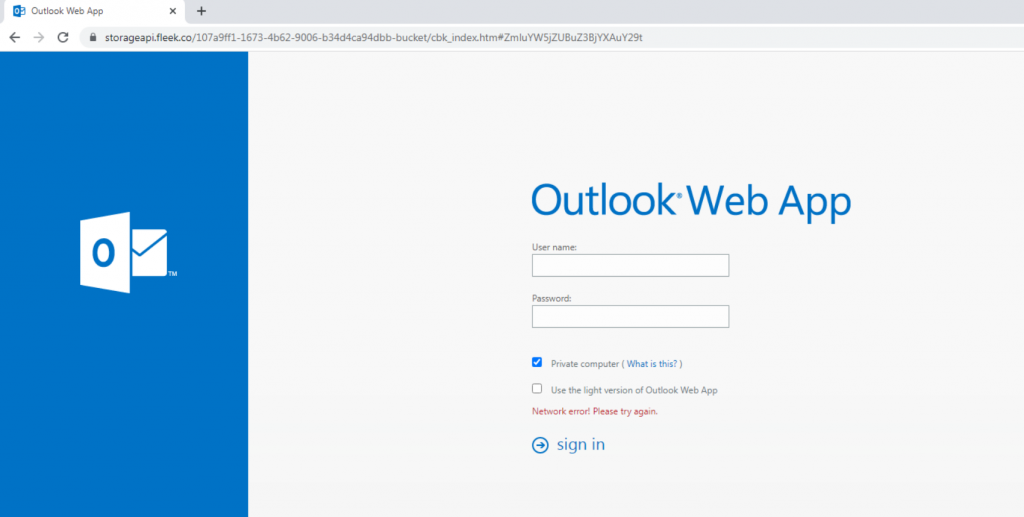
Attack Structure
The email phishing sequence is something we know well. What we aren’t as familiar with is detecting phishing attempts when they are concealed by this new evasion technique. Threat actors use an irregular URL structure to evade detection:
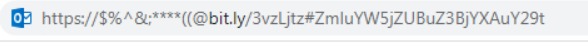
What stood out about this link is that it is not constructed like a normal URL. Normal URLs contain https://, the domain, and a TLD (.com, .org, .gov, etc.). Unlike the standard format, this web address features the “@” symbol. A threat actor follows the “@” symbol with the malicious site. When the address is entered into a web browser, the browser recognizes it as a URL and opens it automatically, knowing to ignore the “@” symbol:
Most email detection platforms cannot recognize this address as a URL, and instead see it as a comment. If this type of malicious link is not detected within an email or piece of content, any user can easily click on it and be redirected to a spoofed site (in our case, a fake Microsoft login page). The seemingly small addition of the “@” symbol enables threat actors to exploit web browsers’ ability to recognize this evasion technique as legitimate and conceal the malicious site in plain sight.
How it Works
Threat actors utilize the ability to include usernames and passwords in HTTP and HTTPS URLs. They use the following URL syntax: http(s)://username:password@server/resource.extention. Microsoft explains that the URL syntax is intended “to automatically send user information to a Web site that supports the basic authentication method.” What this means is that the mechanism is designed for legitimate use, but it can also be exploited by attackers like in the malicious examples that we caught.
Web browsers like Internet Explorer do not support this URL syntax because it is known that threat actors can use it for malicious purposes. Despite this knowledge, web browsers like Chrome and Firefox still recognize this URL syntax, expanding threat possibilities for attackers.
In Summary
Unlike other email security platforms, and detection technologies, the Perception Point Advanced Threat Protection can detect this evasion technique embedded within an email, and can prevent end users from clicking on URLs with this syntax.
See our detection capabilities for yourself by scheduling a demo today!
For more information on the construction of this attack, please refer to the following links:
https://en.wikipedia.org/wiki/User_(computing)
https://en.wikipedia.org/wiki/Dot-decimal_notation























