This summer, Business Email Compromise (BEC) attacks were rampant. These attacks have the potential to cause major financial and/or reputation damage. One of the most harmful types of BEC attacks is thread hijacking, which involves the infiltration and manipulation of ongoing email conversations for fraudulent purposes. In this blog we look at real-life examples of thread hijacks, caught by our Advanced Threat Prevention platform before they could cost our customers over $1,951,000!
What is Thread Hijacking?
Thread hijacking attacks exploit the trust established within an email conversation. Cybercriminals gain unauthorized access to an existing email thread, usually by compromising one of the participants’ email accounts. This usually begins by a user falling for a phishing campaign and then becoming the victim of an account takeover attack (ATO) once the attacker gains access to the account with stolen credentials.
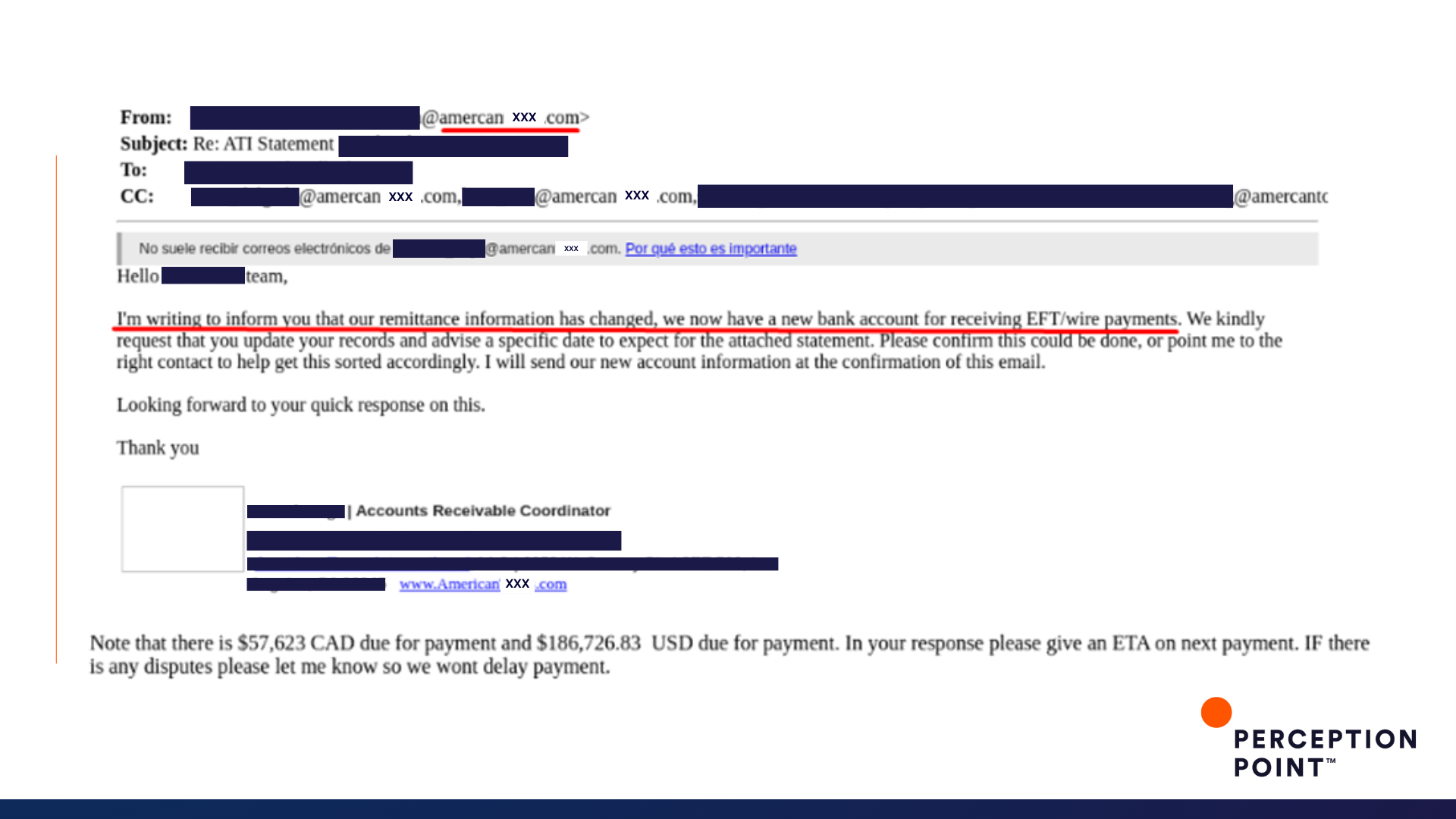
Once inside the mailbox, the attacker will monitor the victim’s email conversations and wait for the right opportunity to make a move. When an attacker identifies a relevant conversation, they jump into the thread by sending fraudulent messages. Attackers often impersonate one of the legitimate participants in the thread, like a colleague, superior, or vendor.
Once inside the thread, they subtly manipulated the conversation, introducing fraudulent content or changing transaction details to divert funds or sensitive information to their accounts. Attackers rely on the trust built within the thread, making it challenging for participants to recognize the manipulation, as the emails seem to come from trusted sources.
Now that we know what thread hijacking is, let’s take a look at some sophisticated examples that were prevented by Perception Point before they could cause any harm to our customers.
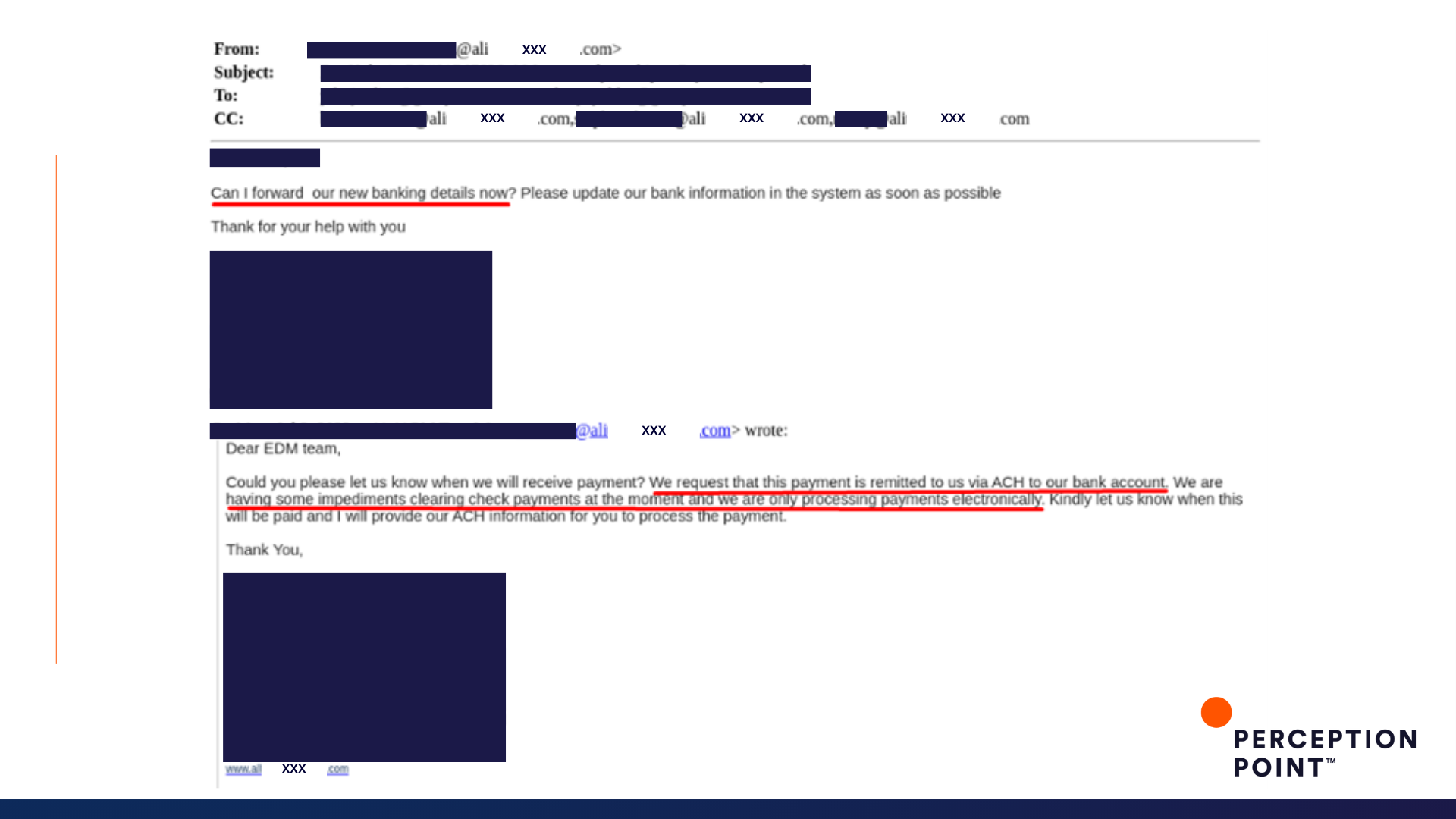
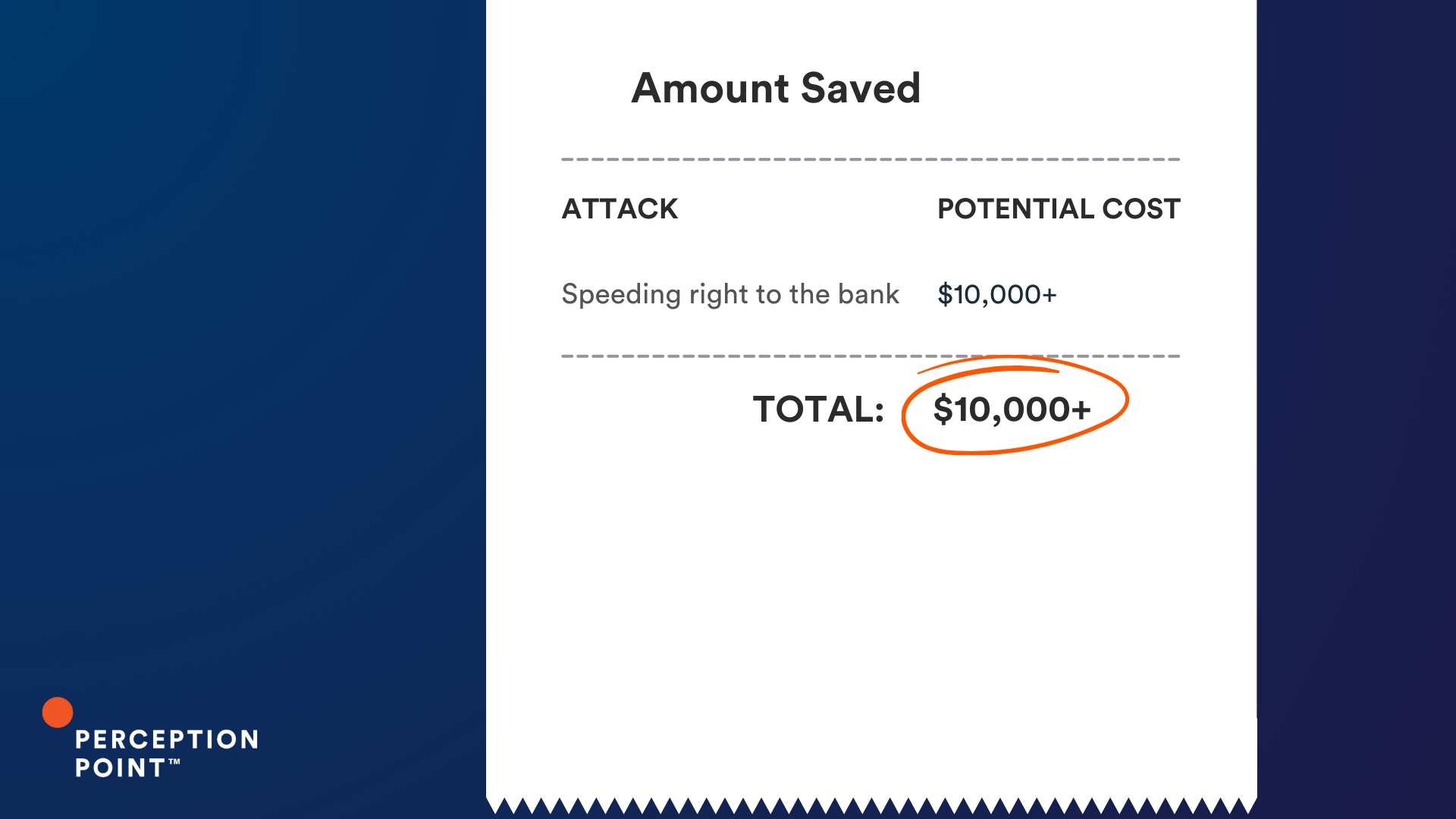
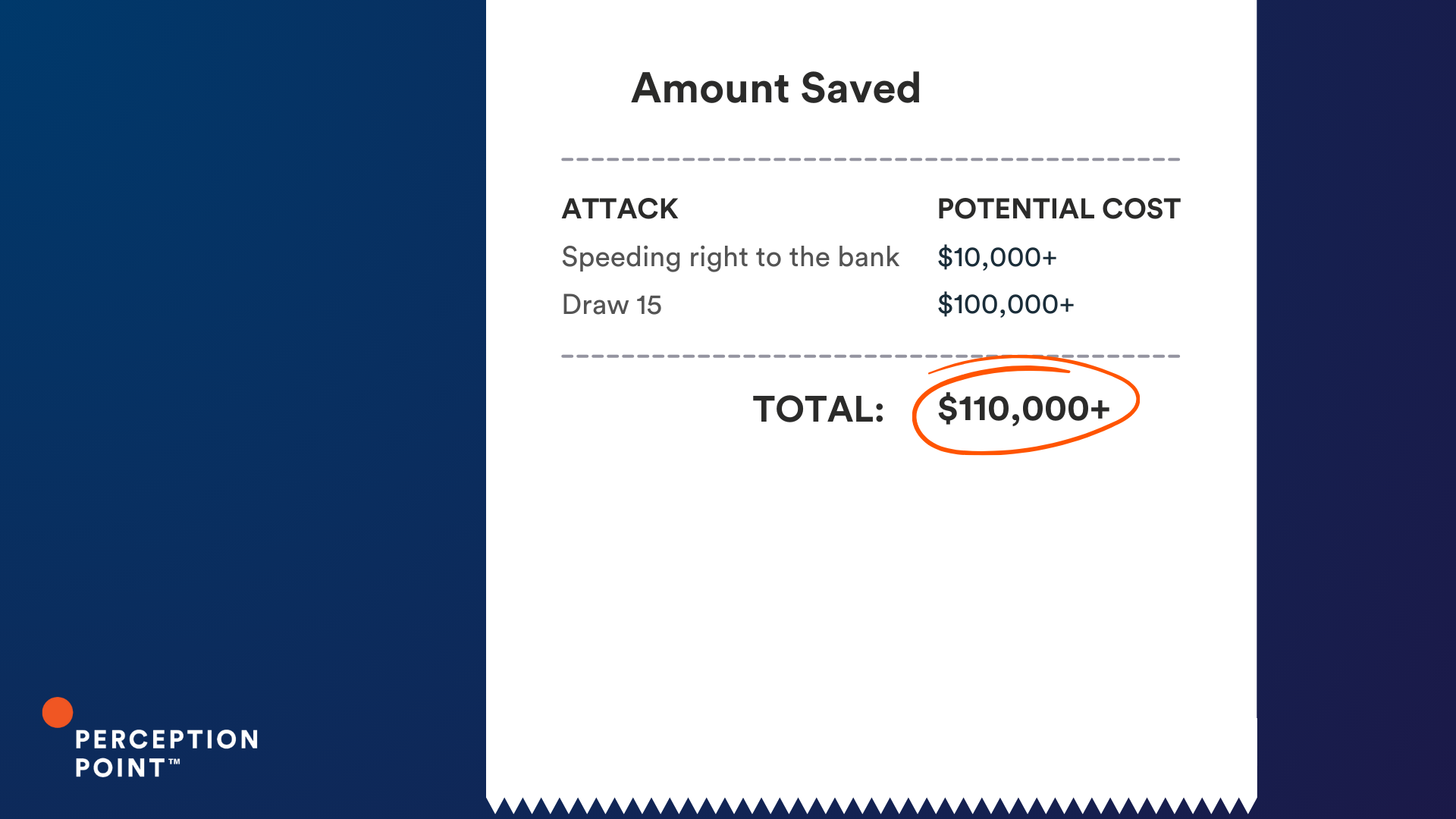
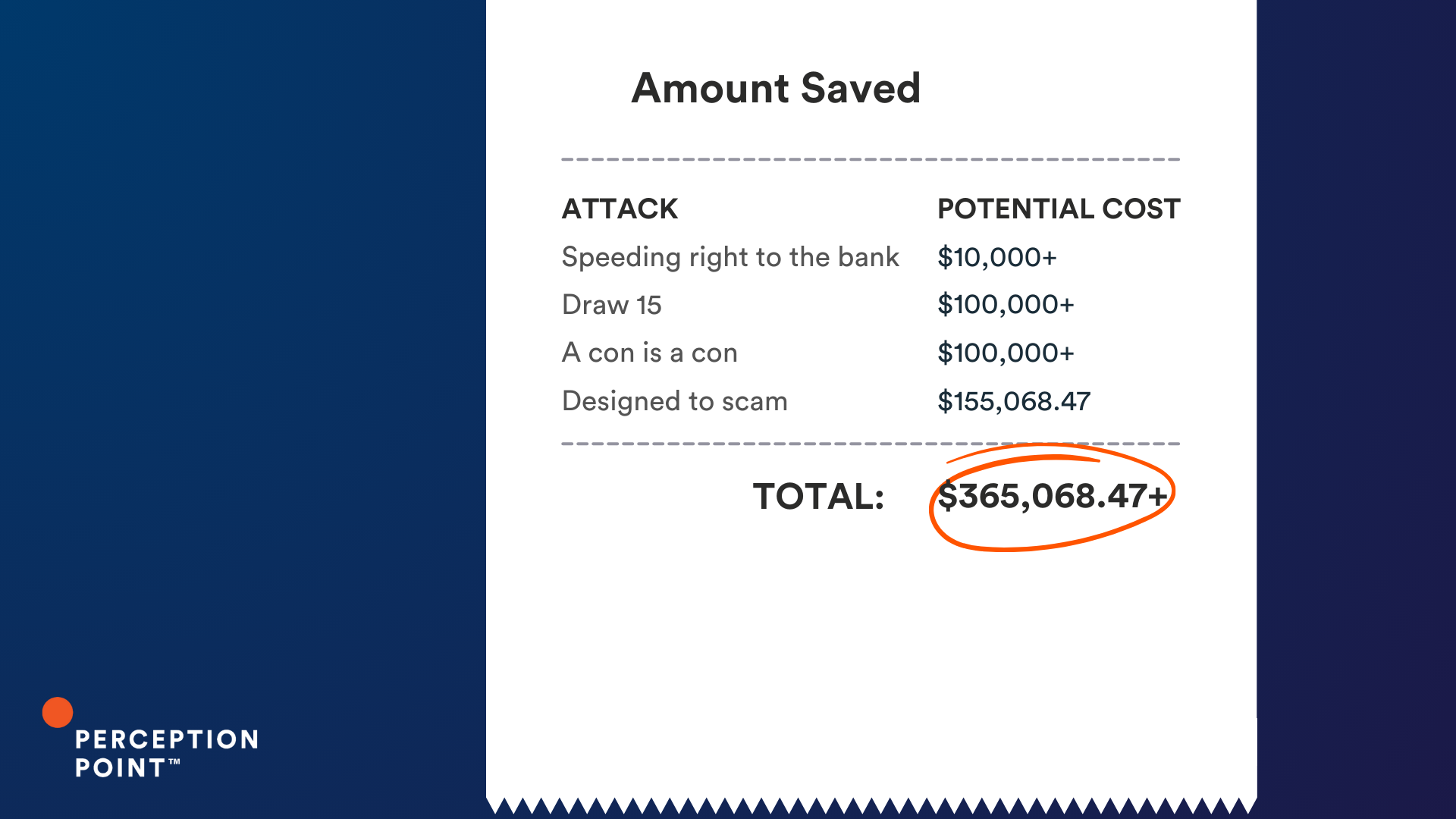
1. Speeding right to the bank


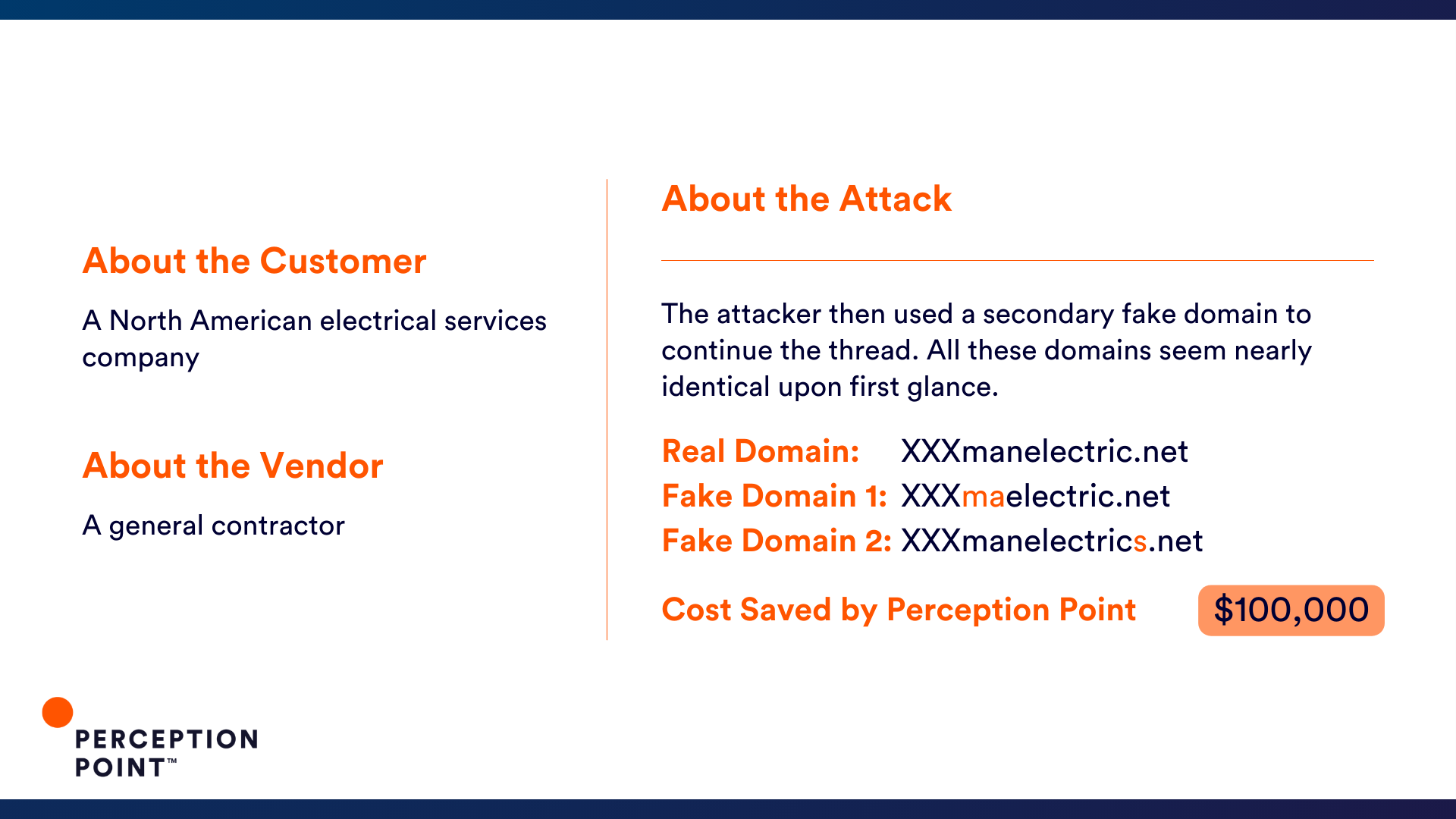
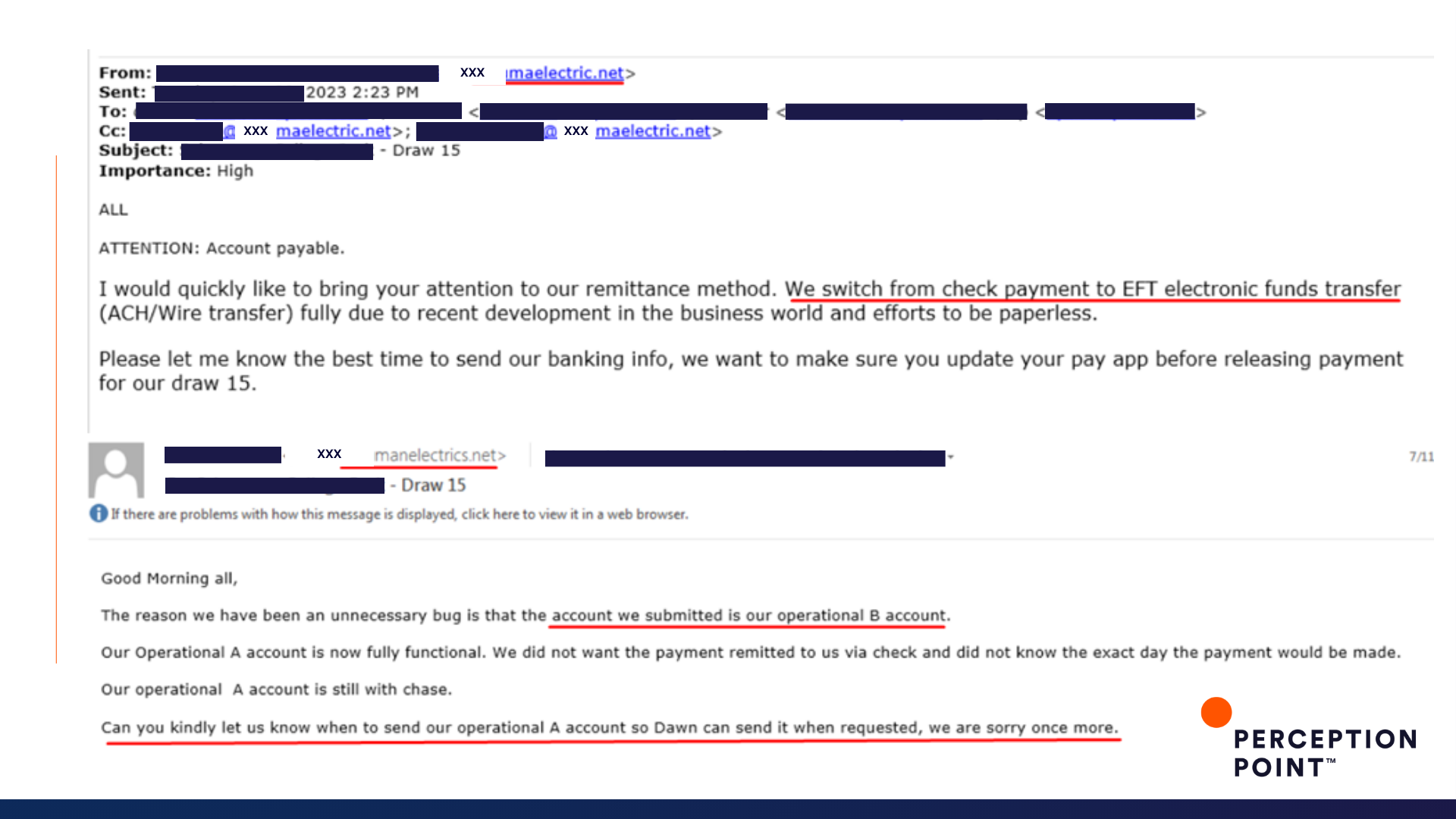
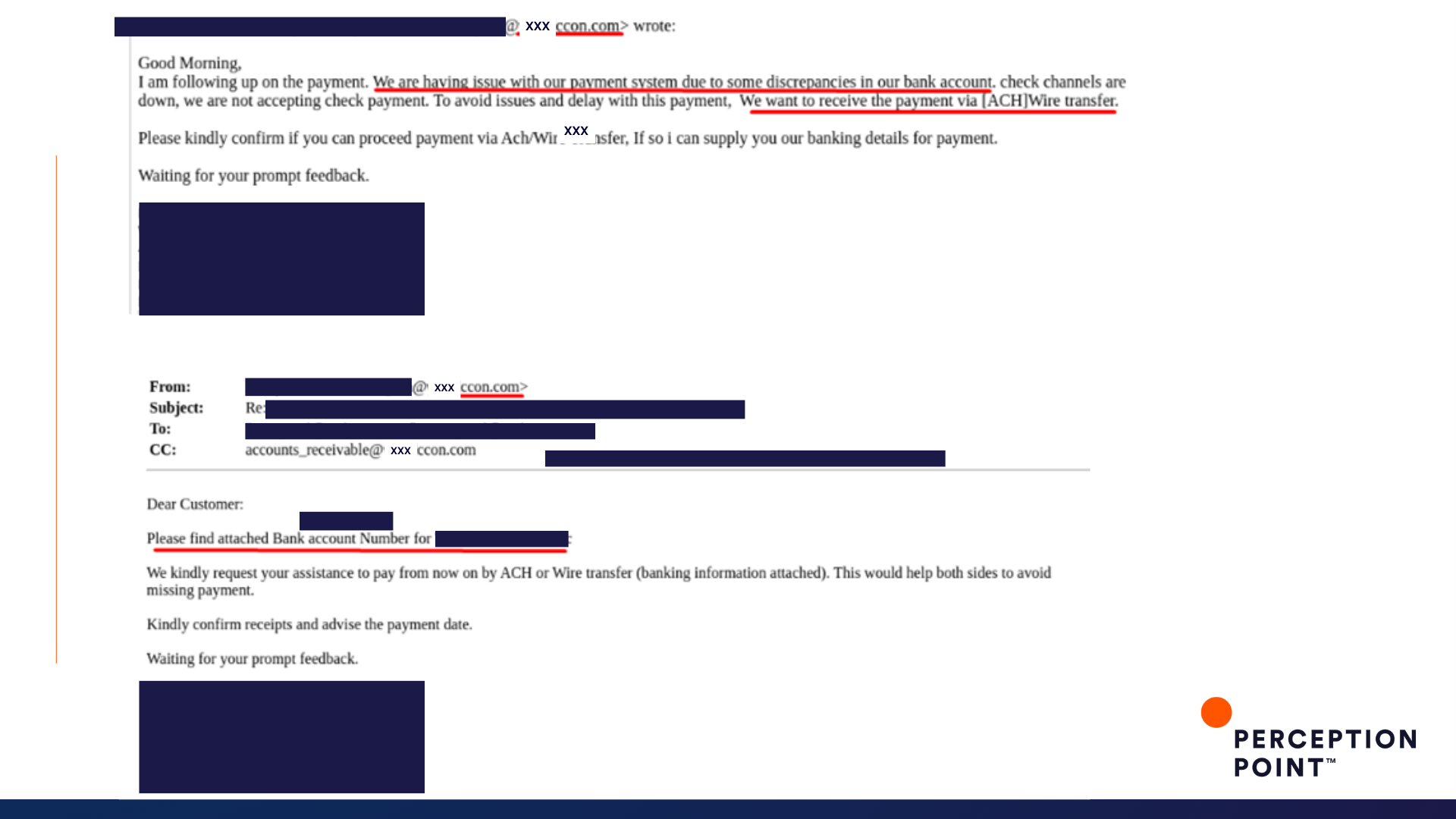
2. Draw 15

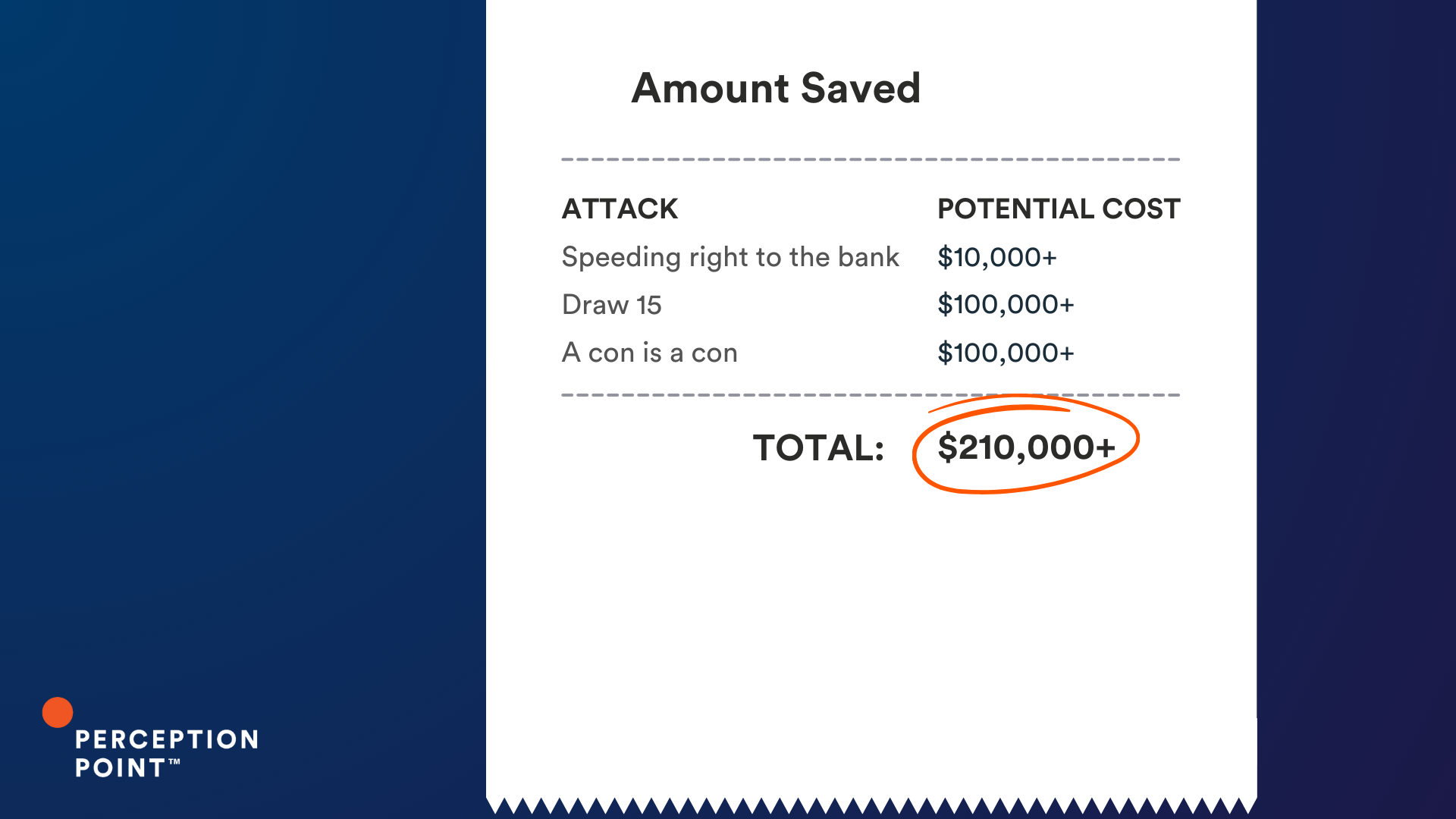
3. A con is a con



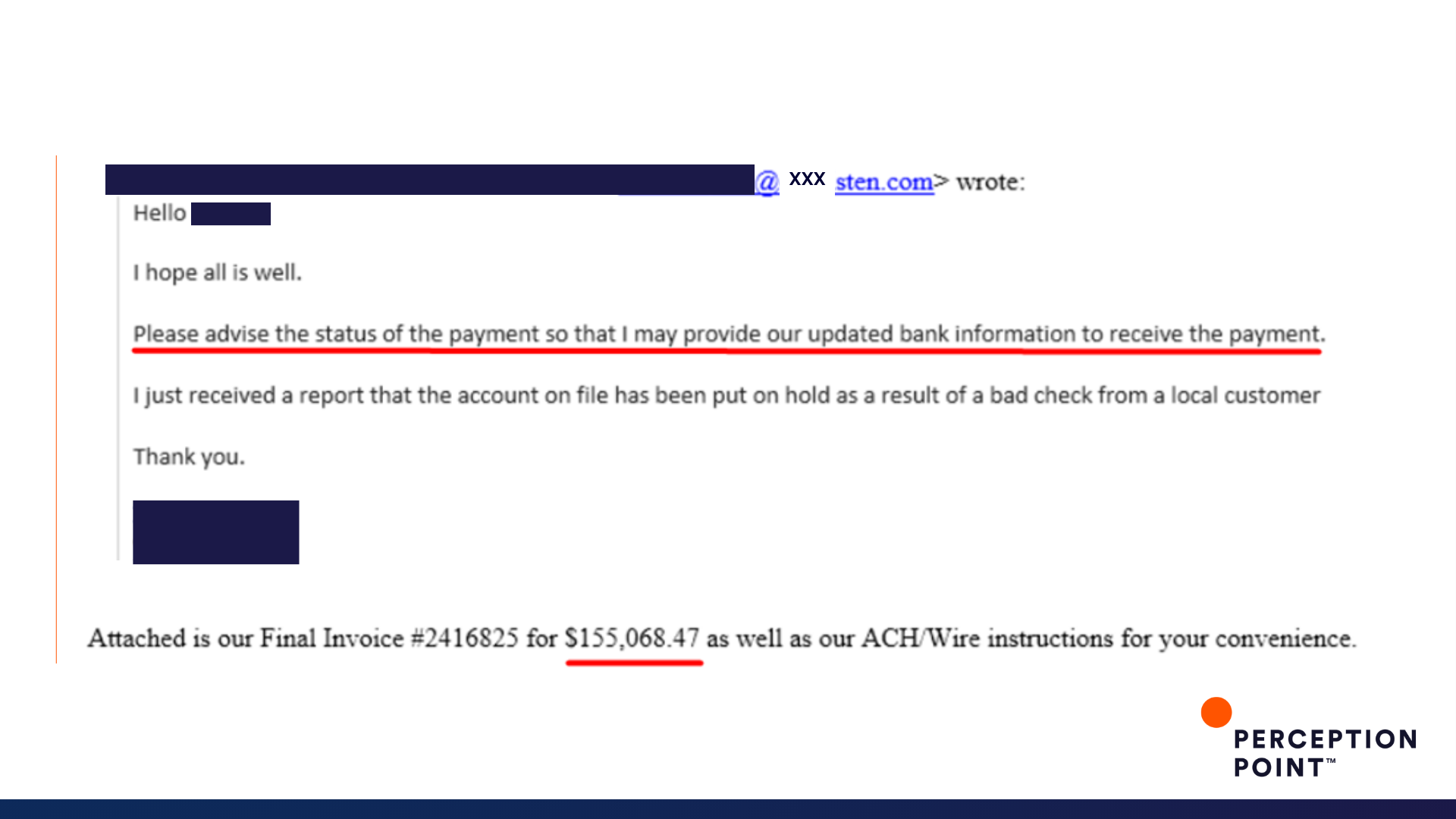
4. Designed to scam


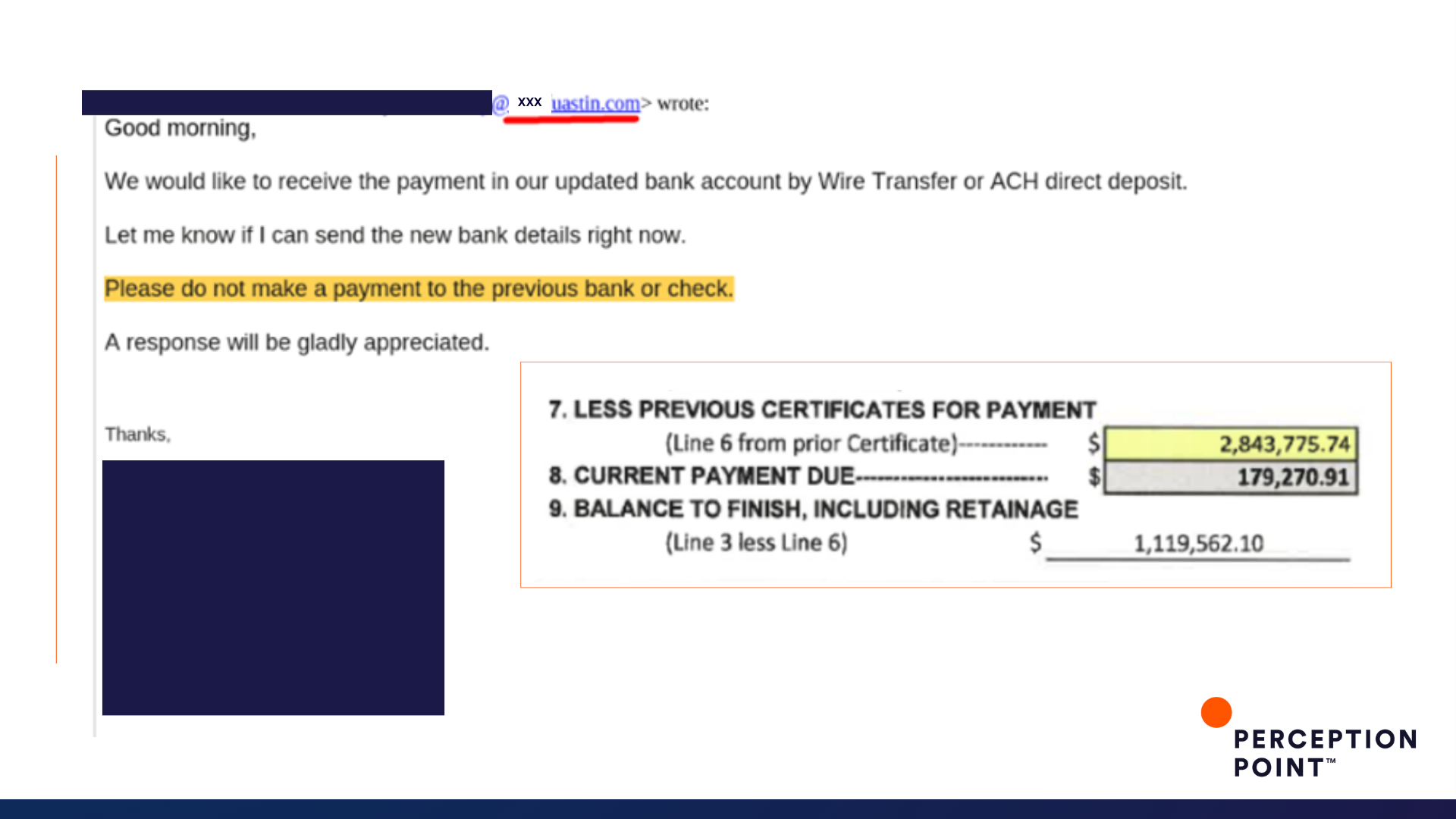
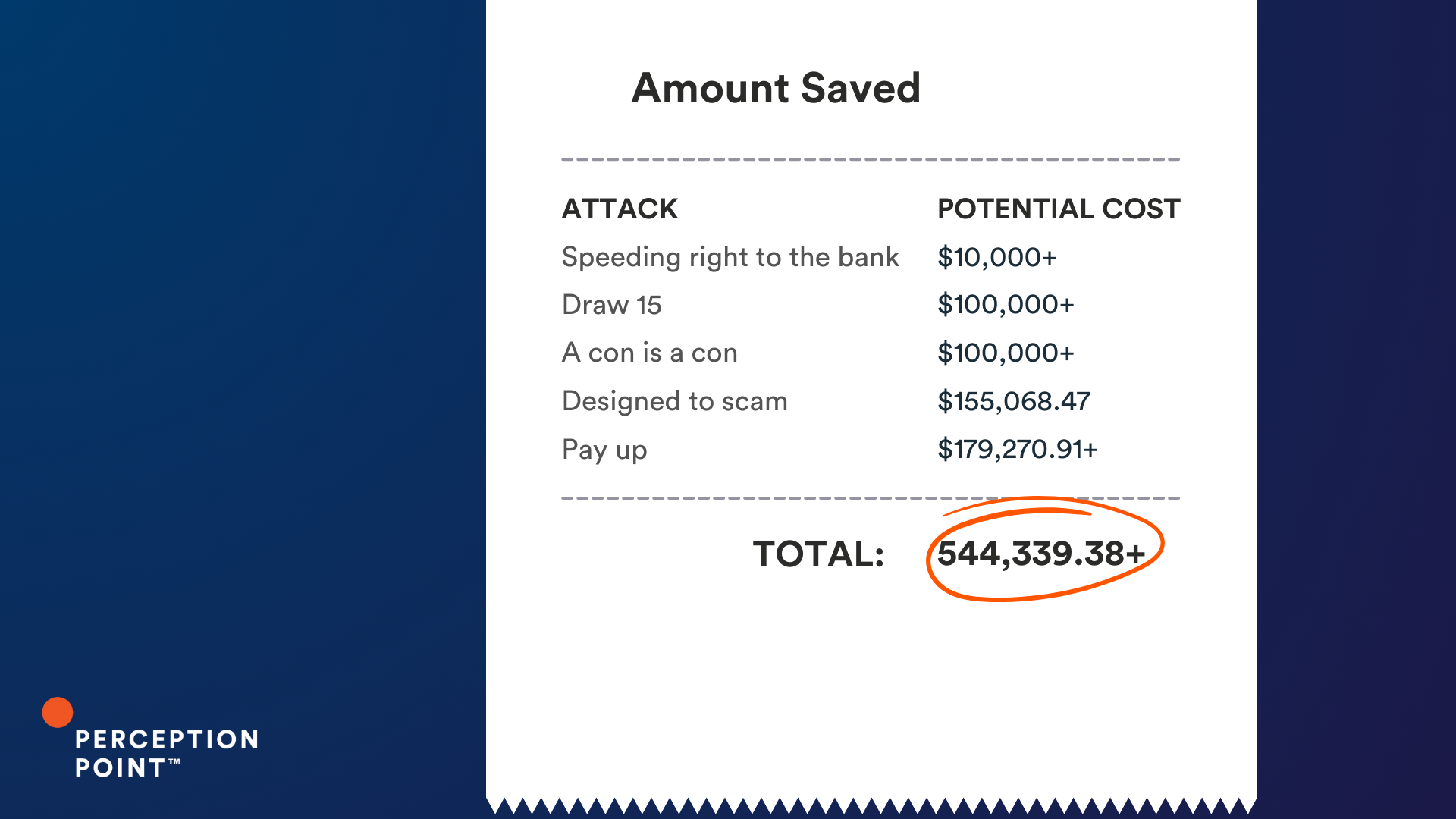
5. Pay up


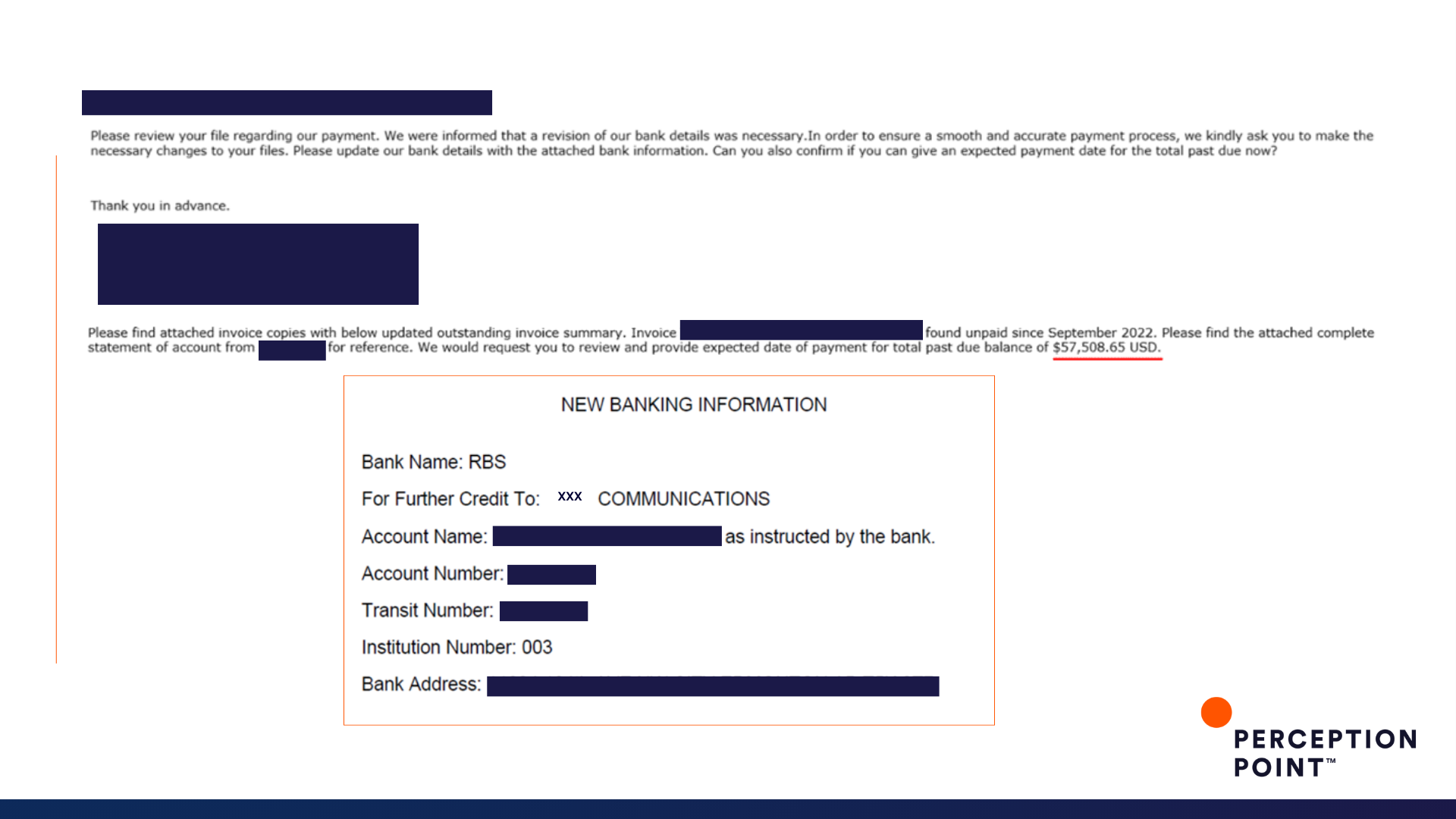
6. Telephony


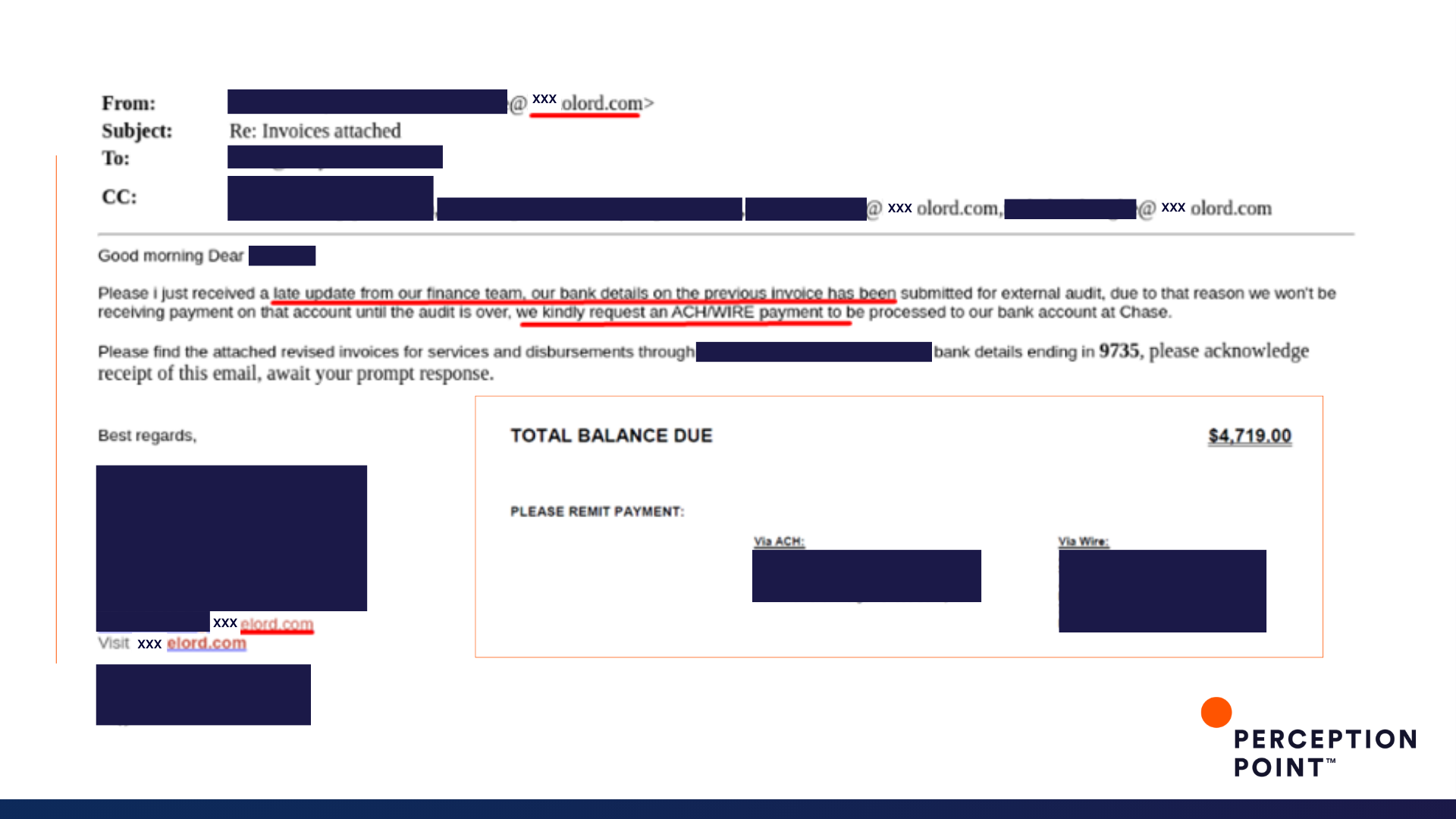
7. Oh, Lord!


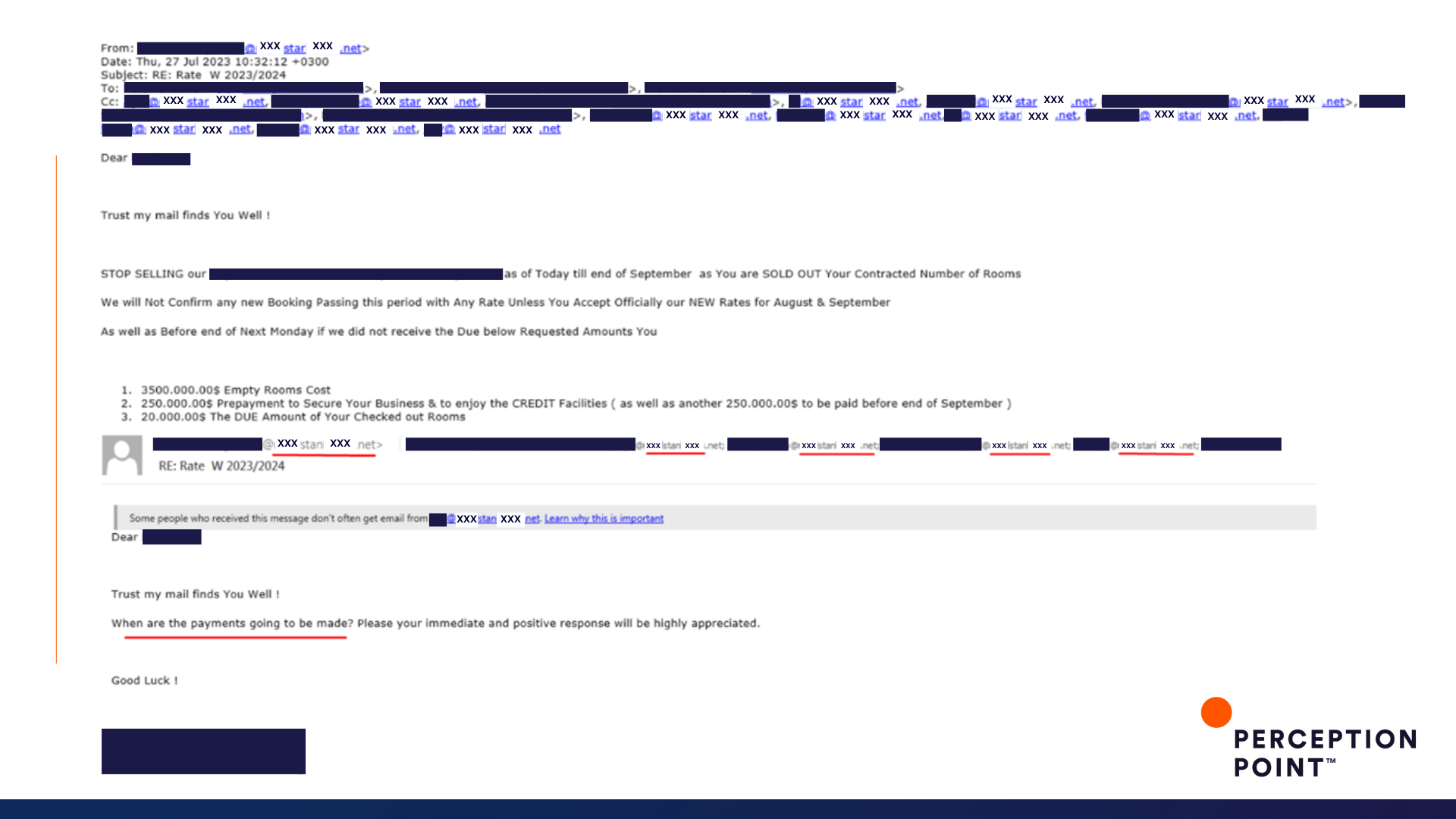
8. Not so hospitable


9. Don't fly away (with the money)


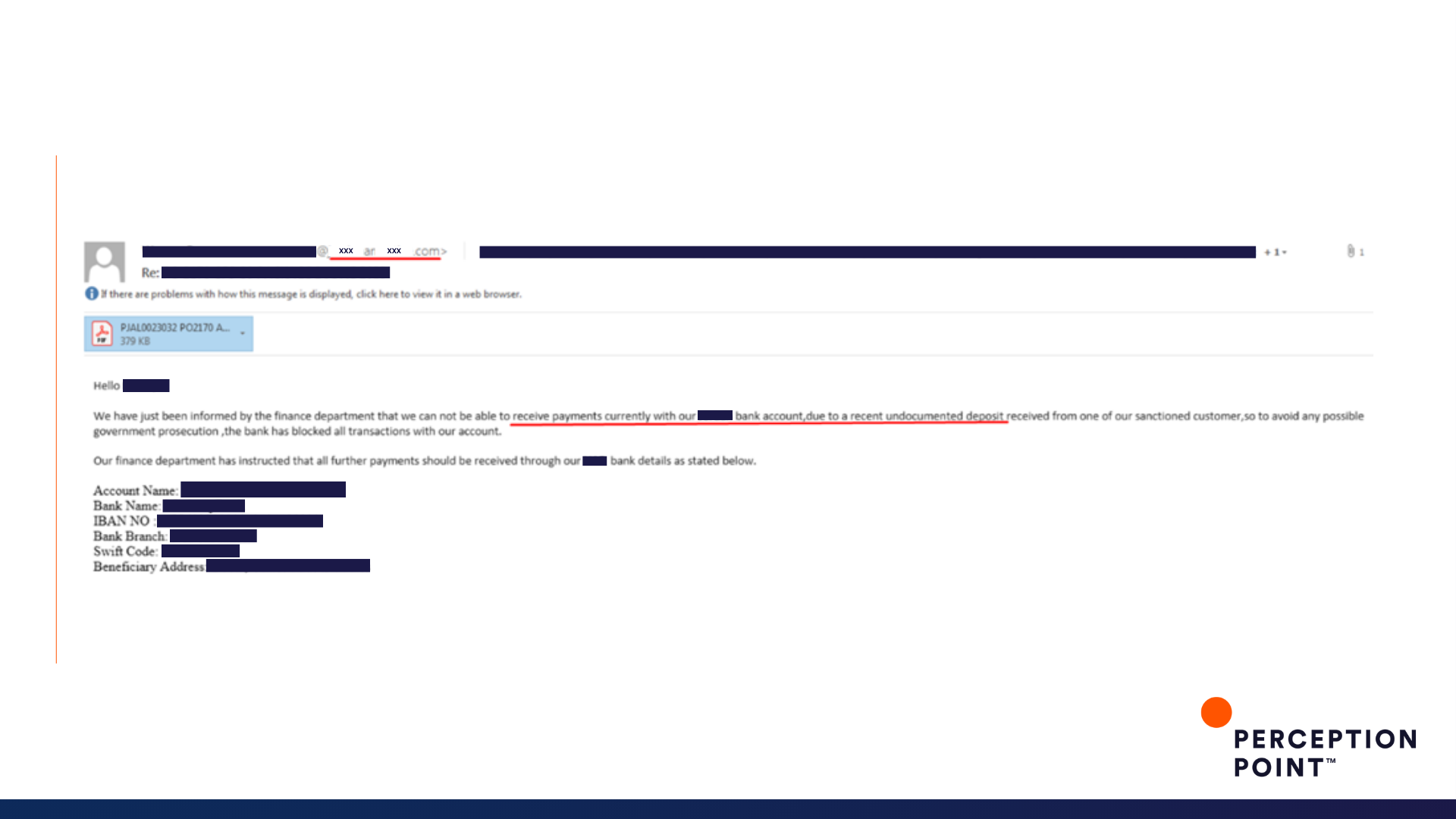
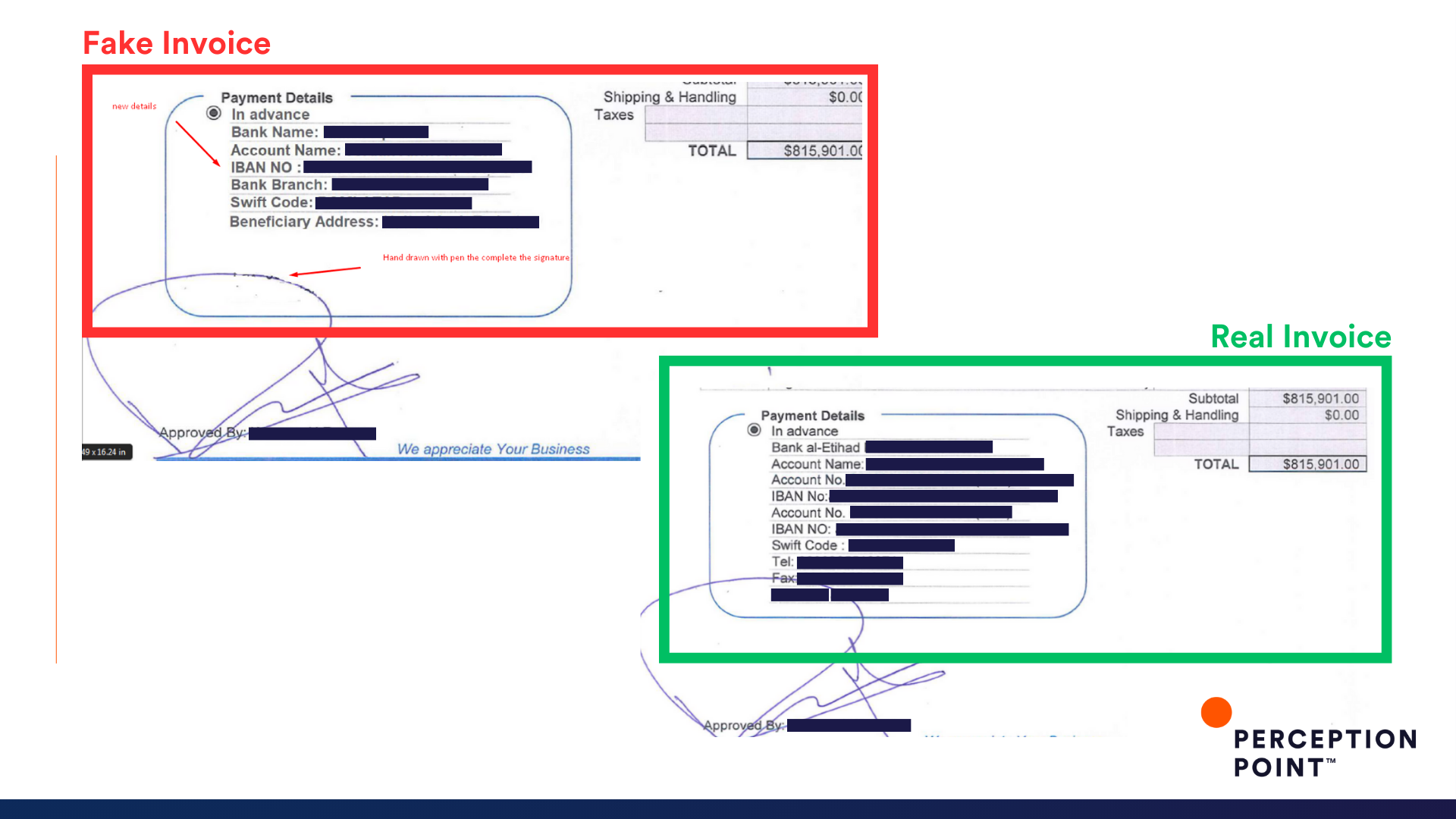
10. You (Ameri)can't do that!


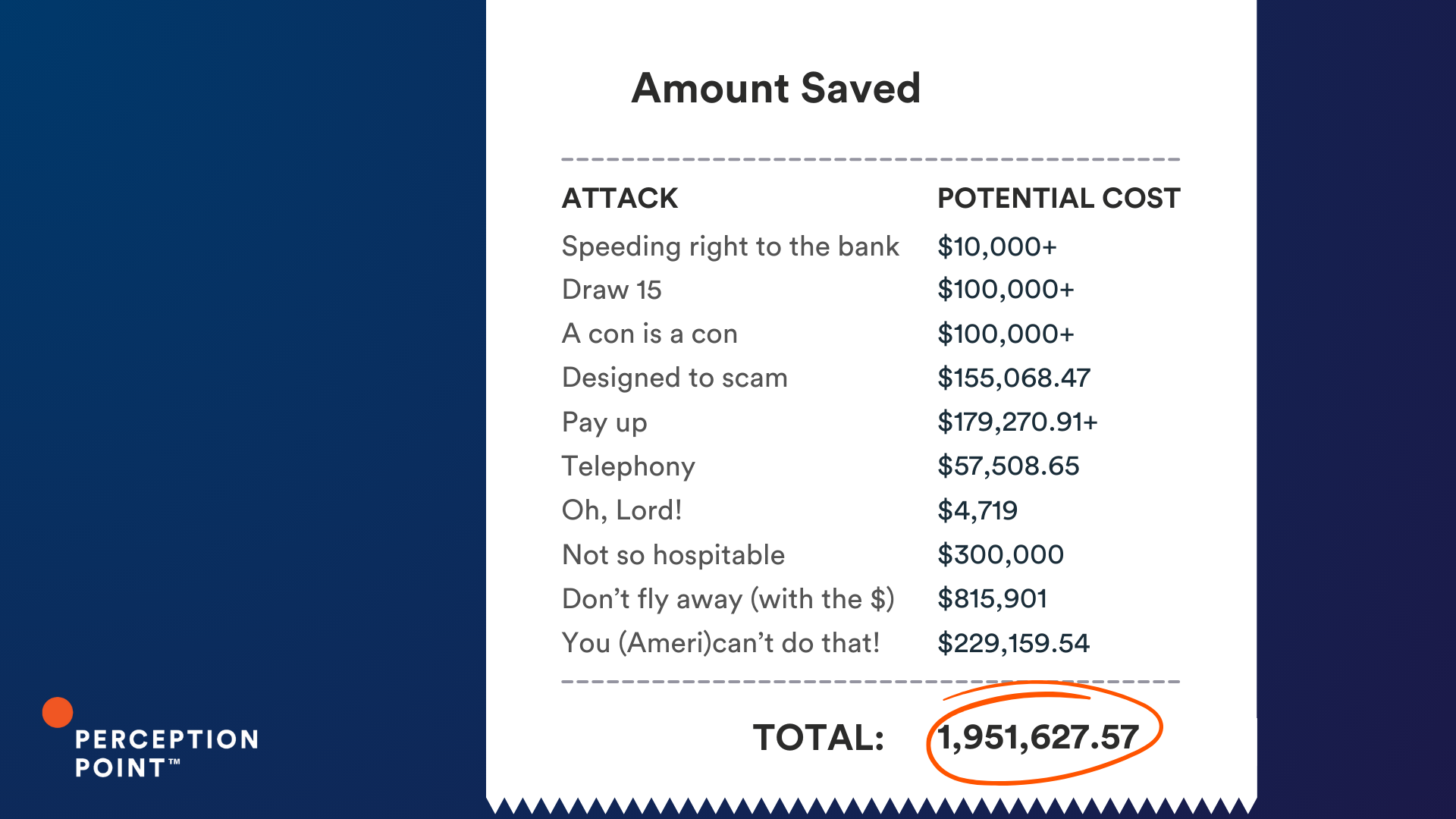
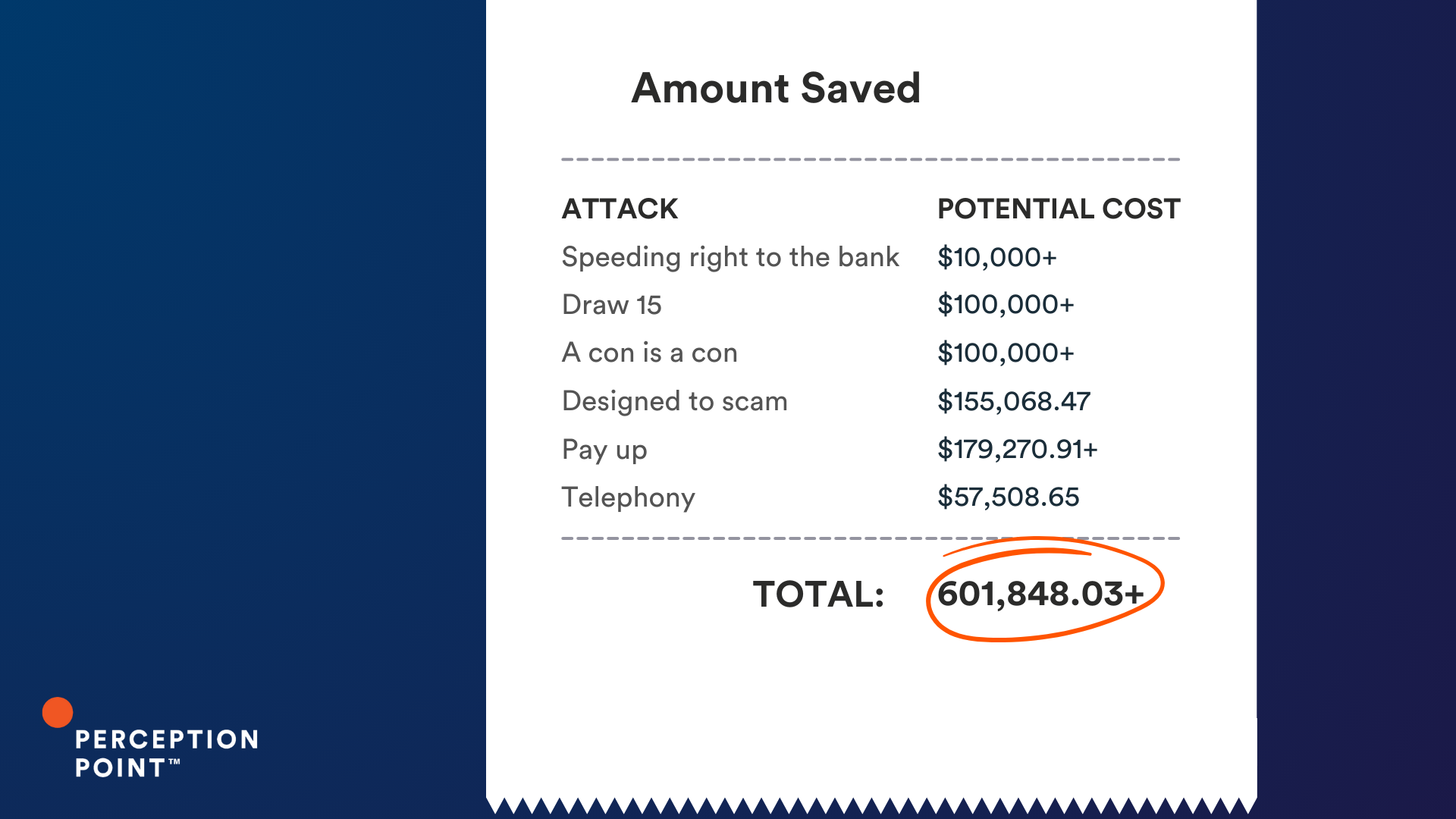
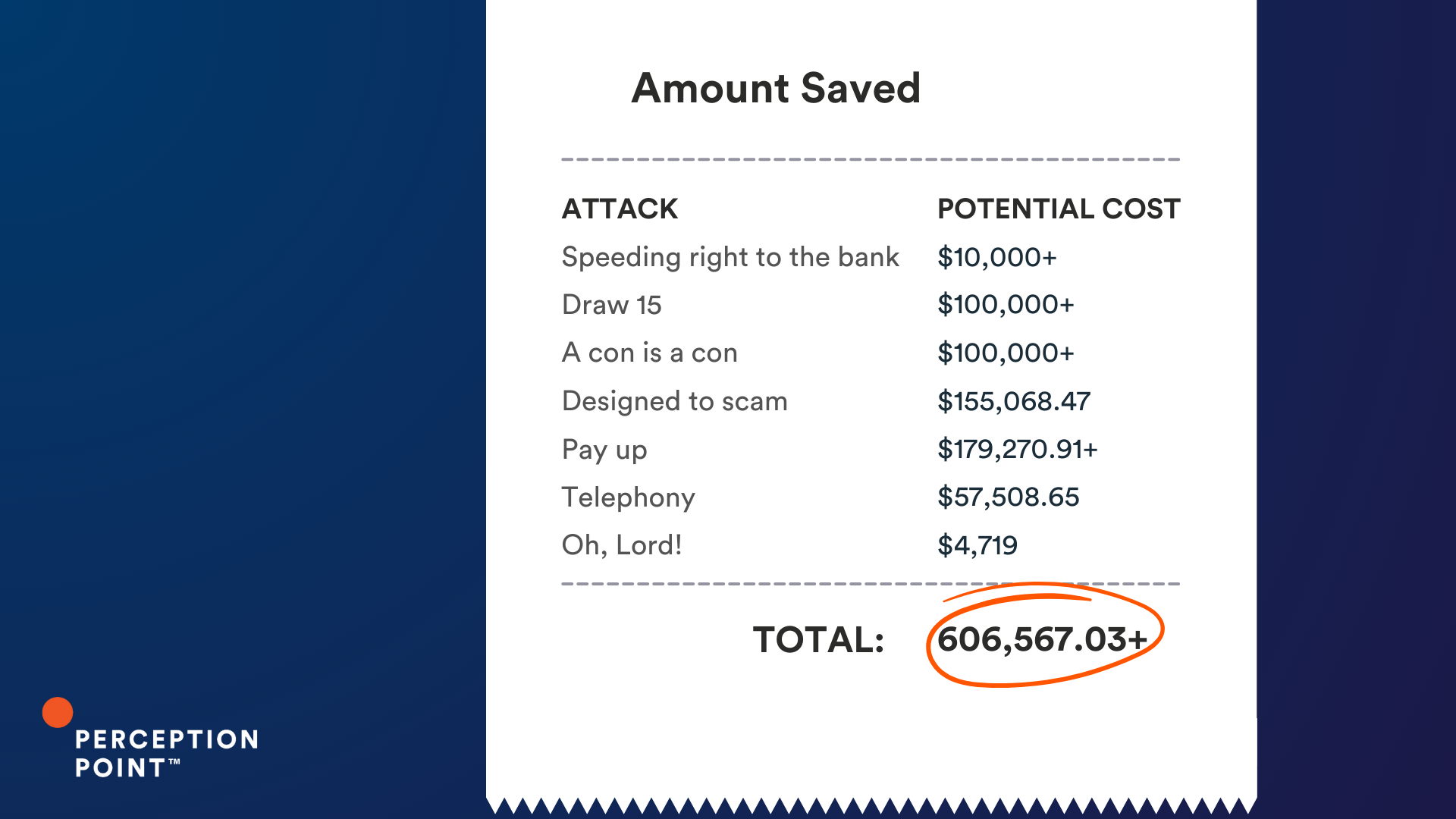
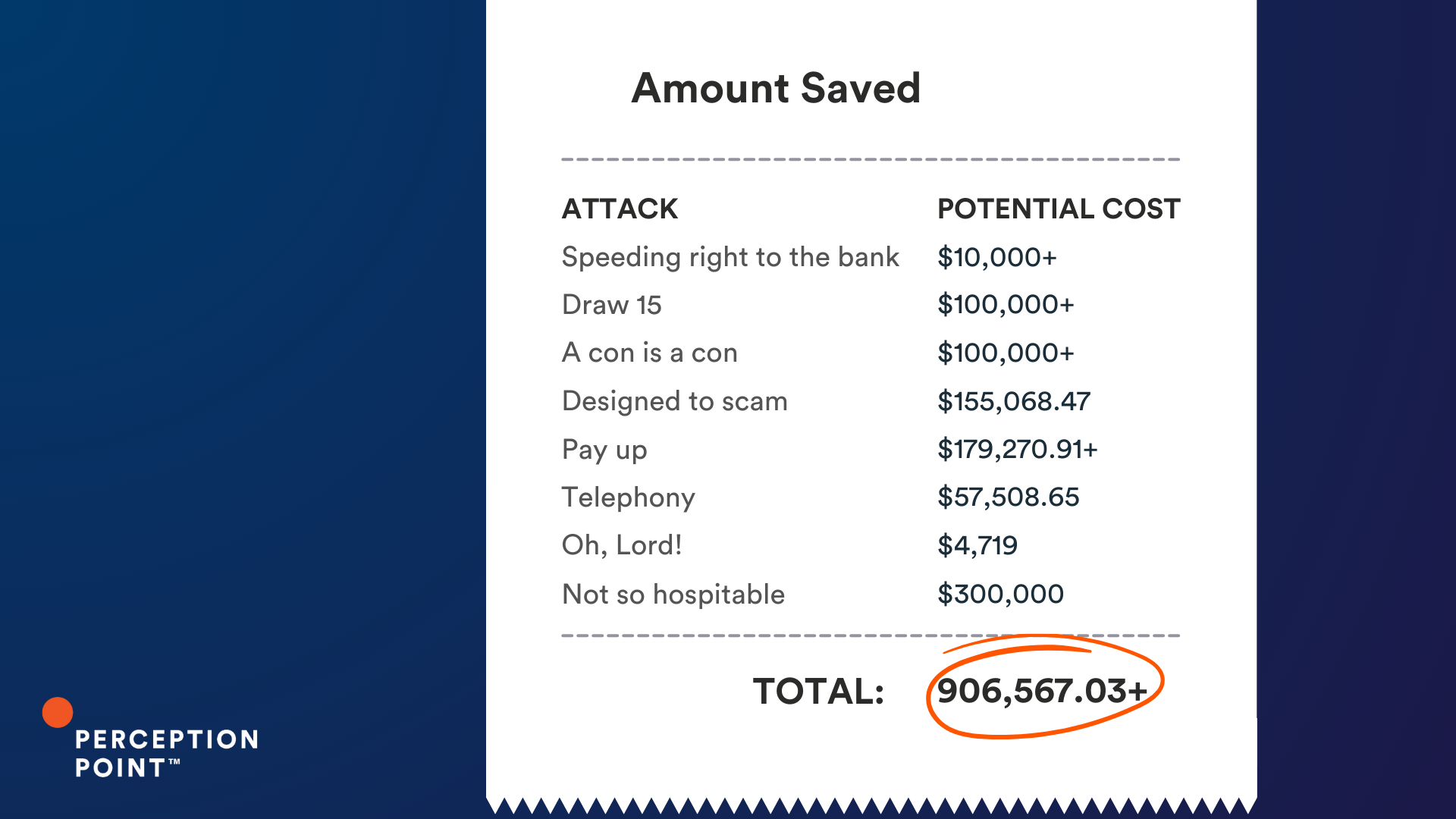
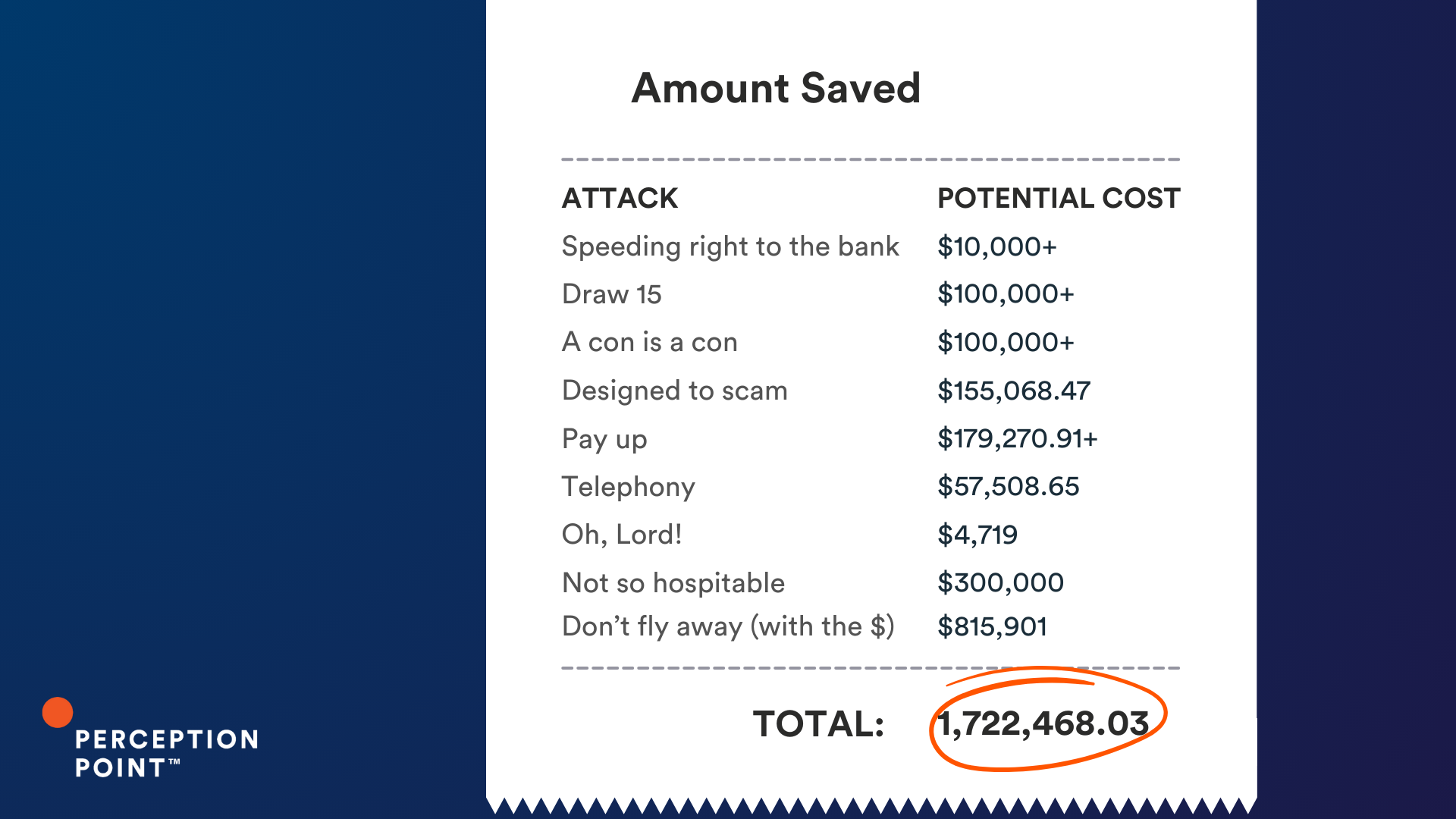
The Cost of a Thread Hijack Attack
These examples are just a few of the thousands that Perception Point’s Advanced Threat Prevention platform scans and catches everyday.
Perception Point Advanced Email Security employs multiple proprietary ML algorithms and AI models to prevent any type of BEC attempt, including thread hijacking, from reaching end users. One of the unique features of Perception Point’s anti-BEC prevention involves supply-chain recognition. This means that the platform analyzes business communications to automatically identify domains belonging to an organization’s business partners, trusted vendors, and known associates. This capability combined with domain-spoofing correlation algorithms prevents conversation hijacking and vendor impersonation attempts, like the ones included in this blog.
So what is the cost of a thread hijack attack? It varies, but these ten examples could have cost our customers just under an impressive $2 million, had Perception Point Advanced Email Security not intervened.
For more information on how Perception Point can protect your organization against the most advanced threats, book a demo today!























