Imagine a world where cybercriminals offer their victims better customer support than your favorite coffee place. Phishers never stop innovating with increasingly sophisticated social engineering tricks that circumvent security measures and human reasoning alike. In this blog, we investigate a phishing attack that leverages the inherent trust we put in live-human-chat support.
Genie in the (Chat)Bot
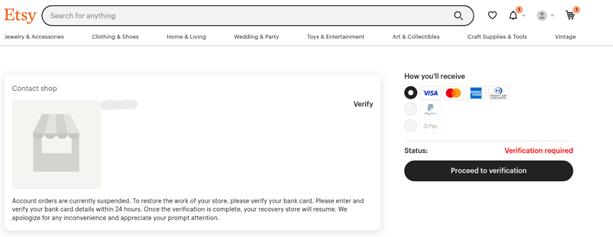
In June 2024, Perception Point’s security research team came across a phishing webpage with an interesting function: active live chat support. The phishing page was set up to impersonate a buyer/seller marketplace payment page, imitating platforms like Etsy or Upwork. The intended targets were the business owners, attempting to claim their payment from goods or services they had provided to their own customers.
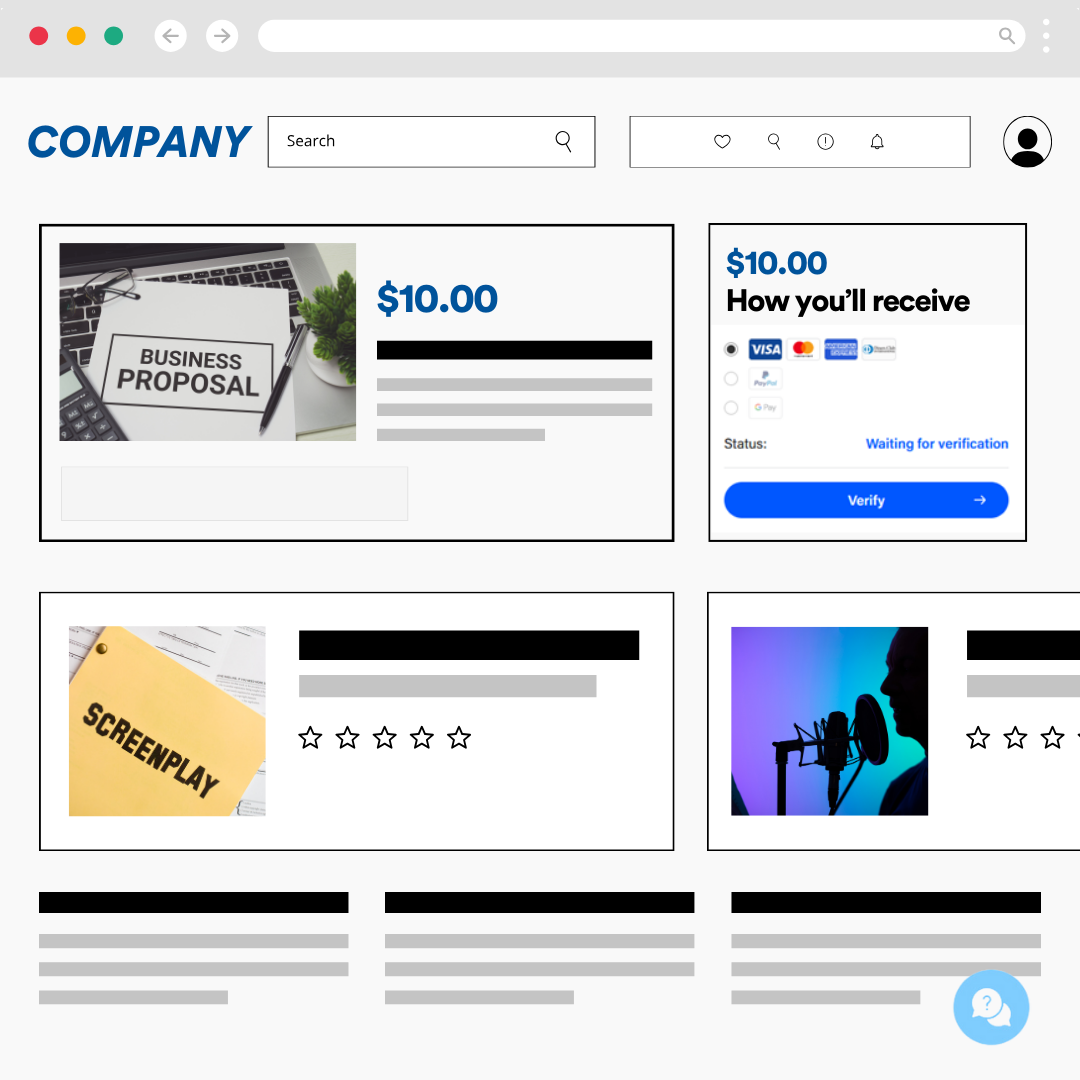
The intent of the page is straightforward: it urges the targets to click the “verify” button to claim their payment.
When the victim clicks on the button, they are led to a spoofed Stripe page, a popular payment processing platform. There, the victim is prompted to enter their credit card details. When they press submit, they receive an error message, and their credentials are as good as gone, sent straight to the attacker.
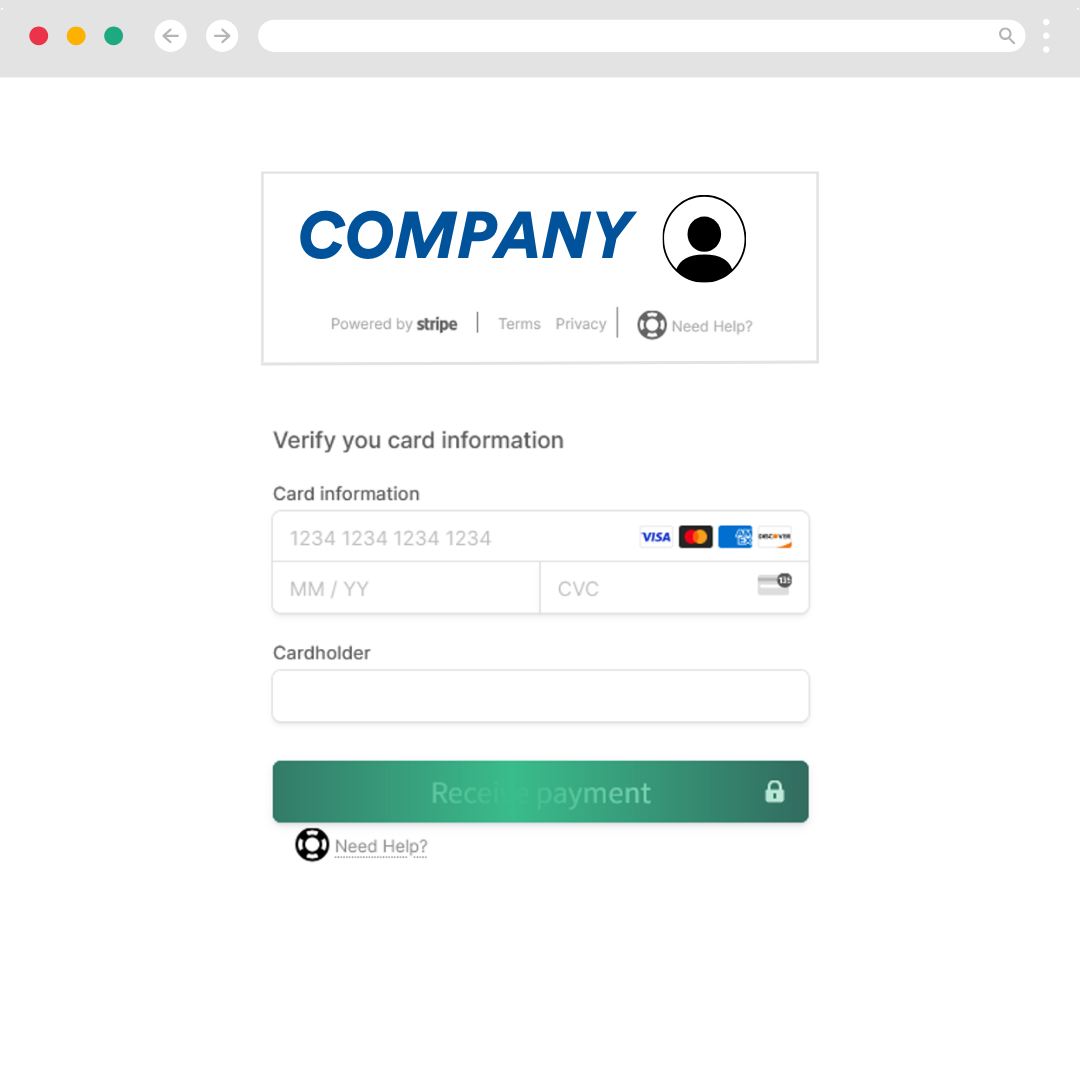
Fully-Managed Phishing Scheme – Who’s in the Chat?
While this may seem like a relatively standard multi-stage phishing attack, what interested our researchers was the chat button at the bottom of the initial phishing page.
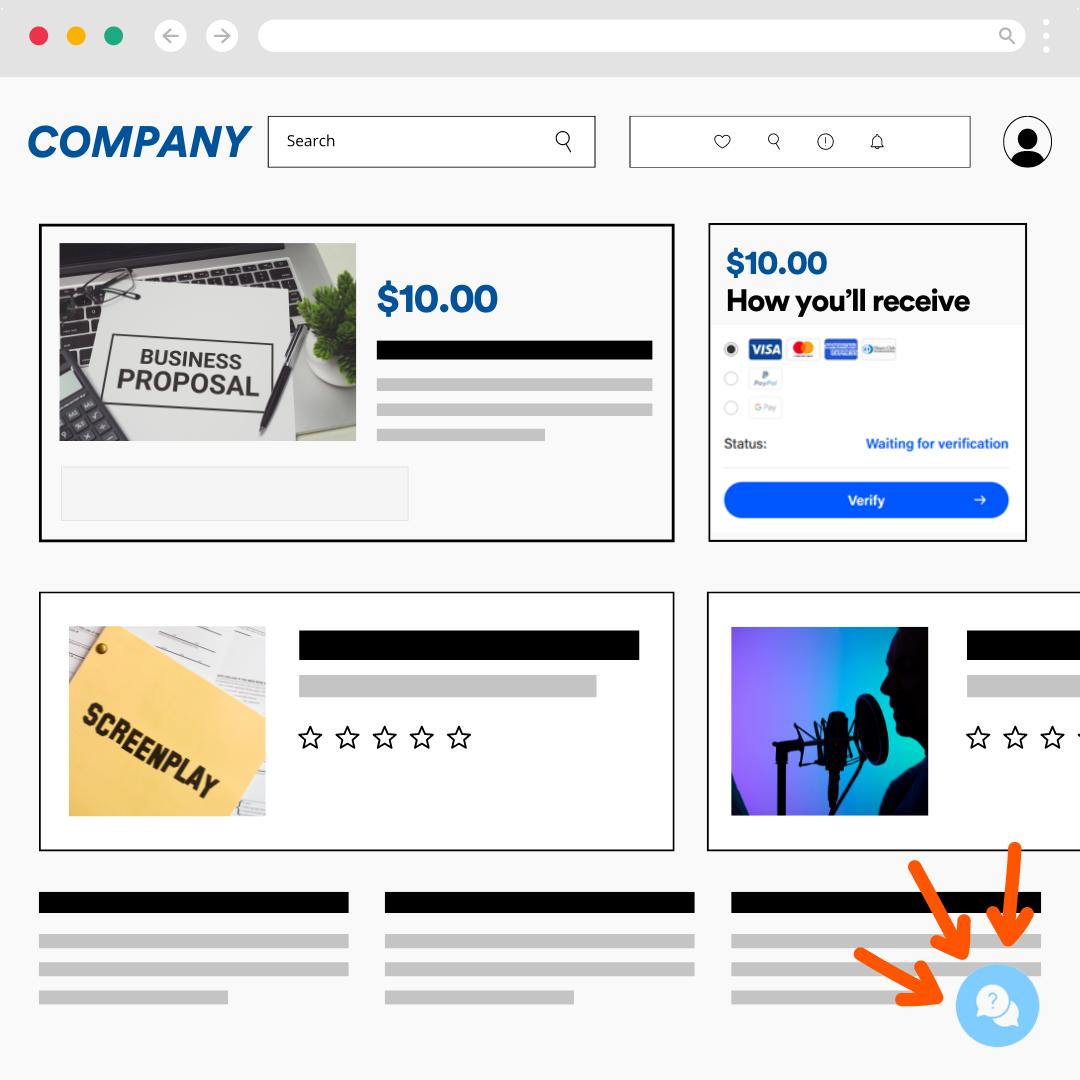
Many phishing pages contain cosmetic and clickable elements to reinforce their “authenticity” to potential victims. Some phishing pages even include pre-programmed chat functions. What sets this particular phishing campaign apart is that it doesn’t use a scripted bot. Rather, when the Perception Point researchers began interacting with the chat, they received human responses in real-time.
The phisher on the other end posed as the spoofed site’s support. When our researchers engaged with the chat, they were strictly instructed to click on the link provided and enter their bank details.
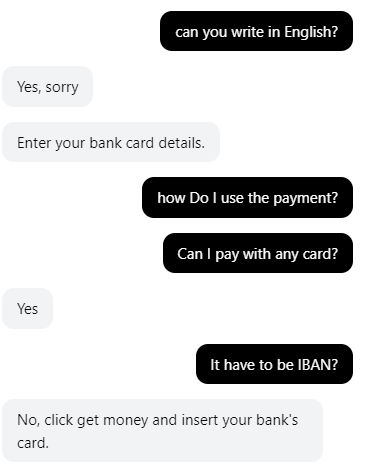
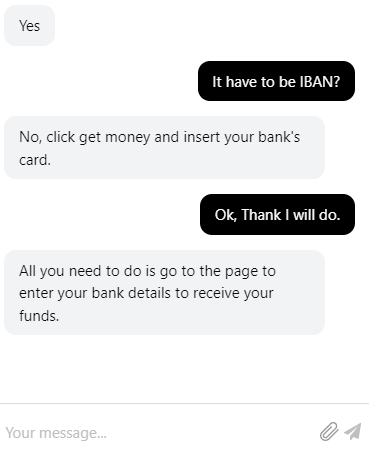
The attacker employed a social engineering tactic to convince the victim that they were on a legitimate website with authentic support. Since the attacker was actively monitoring the chat, it also meant that they were ready to steal the victim’s credentials in real time.
Many phishing campaigns aim to harvest credentials to sell to other cybercriminals or use at a more opportune time. This campaign was built to phish quickly and use the credentials from the point of submission.
It’s a Kit!
Upon inspecting the code behind the chat, our researchers revealed that the chat function is part of a sophisticated phishing kit.
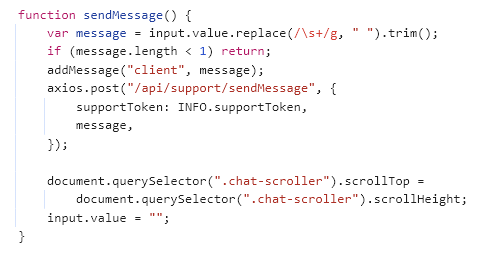
This kit is designed to be versatile, allowing attackers to conduct the same phishing campaign across a range of marketplaces, such as Etsy, Reverb, Behance, and more.
The phishing kit simplifies the process for attackers, providing them with templates to target multiple platforms efficiently. This increases the scalability and reach of their malicious campaigns, making it more challenging for individual platforms to combat the threat.
One iteration even uses a PNG file with a QR code to further disguise the nature of the attack.

Recommendations & Takeaways
To combat sophisticated phishing attacks like these, we recommend taking the following precautions to safeguard your users:
- Verify Communications: Always verify the authenticity of messages received from support teams. Contact the support team directly through official channels if unsure.
- Avoid Clicking on Links: Be cautious of unsolicited links or QR codes. Instead, navigate to the website directly through your browser.
- Check URLs Carefully: Before entering any personal information, double-check the URL to ensure you are on the legitimate site.
- Enable Multi-Factor Authentication (MFA): Adding an extra layer of security can help protect your accounts even if your credentials are compromised.
- Stay Informed: Keep up-to-date with the latest phishing tactics and security best practices.
The increasing sophistication of phishing scams underscores the importance of vigilance and robust security measures. By understanding the tactics used by cyber attackers and implementing proactive security practices, you can better protect your users.
Perception Point continues to monitor these threats and provide solutions to safeguard users in the modern workspace. For more information on how to protect your organization, book a demo.
























