Our Incident Response team sees hundreds of attack types a day. In this blog post we round up four real-life advanced attack examples ranging in technique, industry, targets, and goals. While these attacks may all be different, they each share a similar malicious intent to exploit unsuspecting users. Keep reading to learn more.
1. Thread Hijack
In this first advanced attack example, a threat actor leverages vendor email compromise (VEC) to steal $50k from a CFO in the energy industry.
The attacker begins by creating a look-alike email address belonging to one of the target’s known vendors. The fake address differs from the legitimate one by just a letter, barely noticeable, and the real email address appears as the sender’s name in order to deceive the victim. With the deceptive address, the attacker then makes their move, hijacking an existing email thread between the vendor and the victim. The victim assumes that the vendor is continuing the thread, innocently asking to update their banking details. In reality, it is the attacker that has requested the change.
Perception Point’s advanced threat detection platform identified the correlation between the fake address and the original one, recognizing the message as a spoofing attempt. Furthermore, the content of the email asking for financial details raised additional flags, preventing the email from making its way to our customer’s inbox, thus preventing a successful VEC attack.
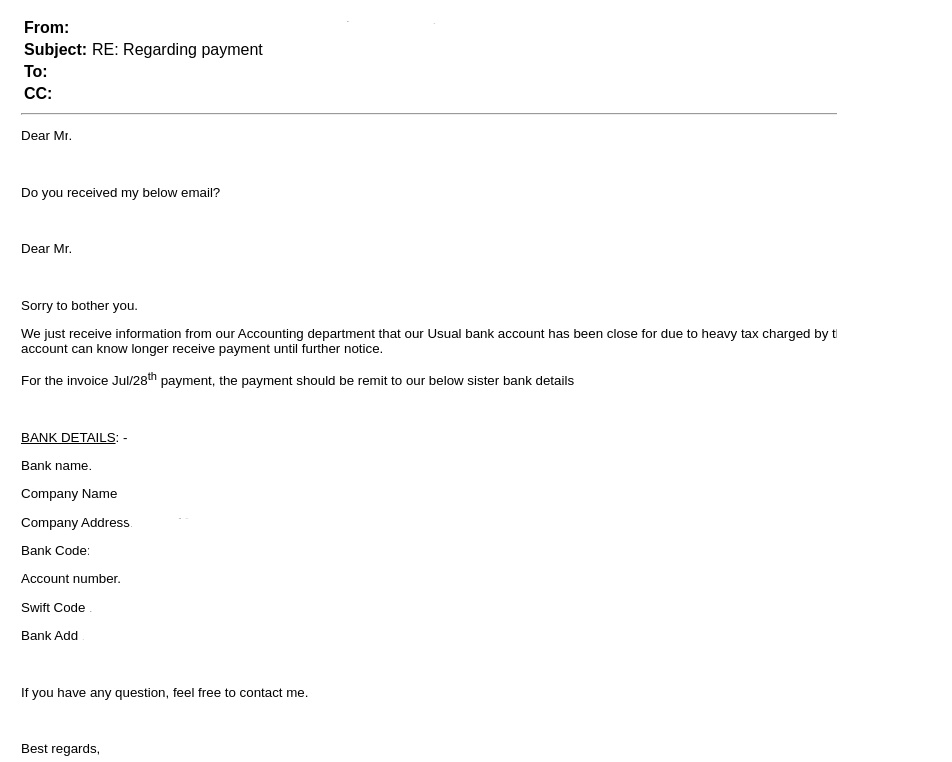
Figure 1: The thread hijack email
2. Gift cards gave it away
Next up is a familiar business email compromise (BEC) attempt. The attacker poses as a C-level employee in the automotive industry, asking a lower-level employee to purchase gift cards. This is a classic attack that we know all too well. Here’s how it happens:
- An attacker creates a fake Gmail account under an executive’s user’s name.
- The attacker sends an employee a request to purchase gift cards, via the fake email address.
If there are little to none advanced detection and protection mechanisms in place, then the attacker dupes the employee and disappears with the gift cards. In this case, content-based rules within our platform detected the gift card request and blocked the message, identifying it as an impersonation of an executive within the organization.
TIP: If you receive an email from a superior asking you to purchase gift cards, maybe call them to confirm before you become the next victim in this popular BEC scam.

Figure 2: The impersonation email
3. Compromised vendor goes phishing
This attack combines a few classic techniques, including account takeover (ATO) and phishing.
A vendor’s mailbox is compromised during an account takeover attack. The attacker uses the vendor’s account to execute a large phishing campaign. This attack utilizes a 2-step phishing approach, meaning that the target is redirected before being asked for their credentials.
The user receives an email from a trusted vendor, unaware that the vendor has been compromised. This adds another layer of legitimacy, as the user has nothing to suspect about the real identity of the sender. The attacker sends a fake invoice PDF attachment to the user. The document is hosted on Google Drive and contains a concealed shortened link. Once the user clicks on the PDF, they are redirected to a spoofed login page and asked to enter their details in order to see the document. Here, the attacker attempts to steal the user’s credentials.
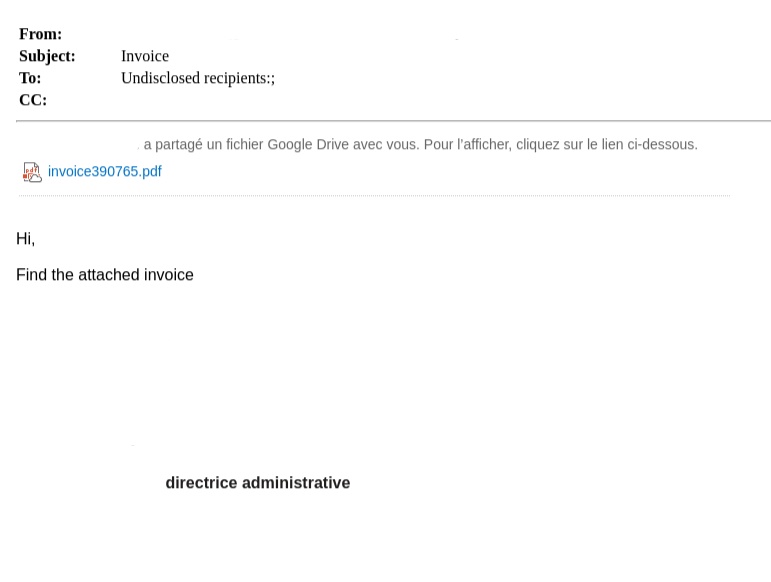
Figure 3: The compromised vendor’s email
To the untrained human eye, it is very easy to fall prey to such an attack. However, a next-gen detection platform can unpack embedded attacks like these, uncovering any attempt to evade detection.
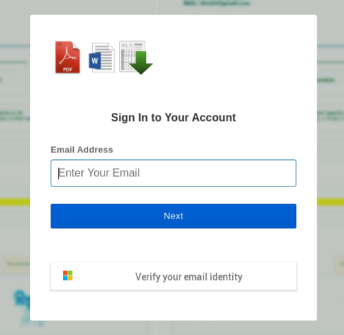
Figure 4: The spoofed login
4. Multi-level malware
This last advanced attack example involves a malware campaign targeting users in the hospitality industry with the aim of remote access control.
An advanced persistent threat (APT) group managed to hijack a hotel’s domain, using it as a legitimate source to deliver malicious payloads. The advanced threat we caught starts with an email, in which the sender requests help from our client. The email directs the recipient to a booking link, which actually auto downloads a ZIP file with LNK.
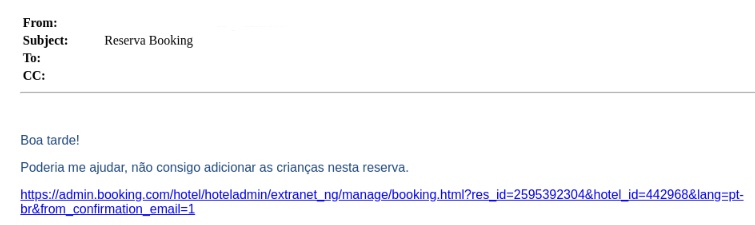
Figure 5: The compromised hotel email
The LNK file launches and the attack chain begins, leading to AsyncRAT. AsyncRAT is a remote access trojan (RAT) designed to remotely monitor and control other devices through a secure encrypted connection.
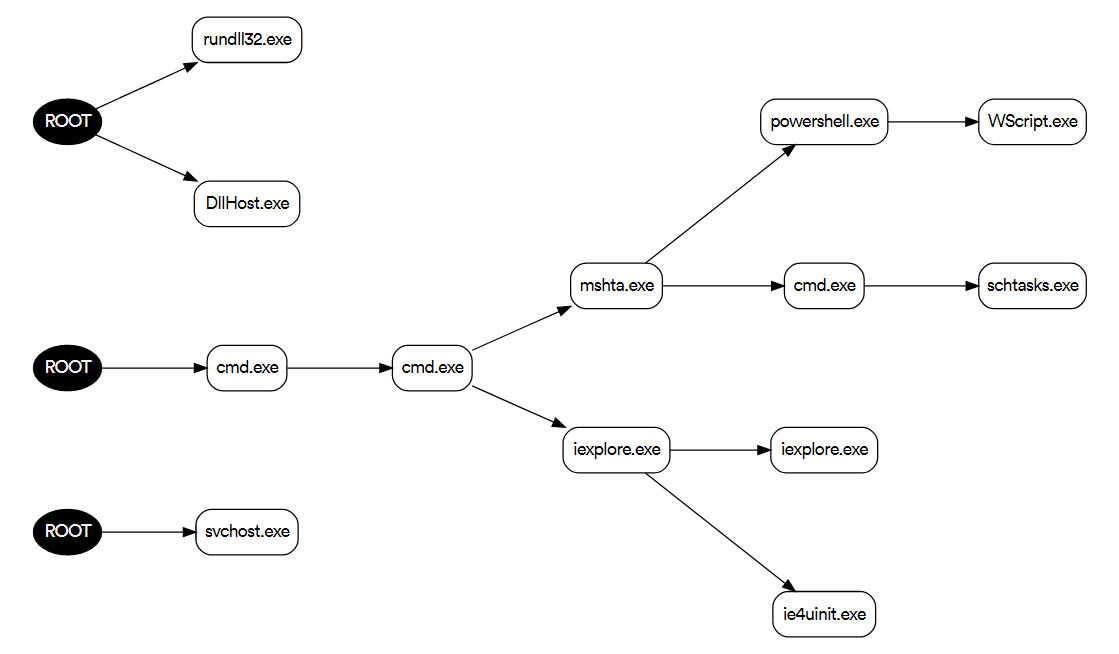
Figure 6: The attack chain
Our platform identified this malicious behavior with static and dynamic analysis, stopping the attack before the attacker had a chance to harm our client.
Now what?
As you can see from these examples, advanced attacks come in all shapes and levels of complexity. Attackers continue to find new and sophisticated ways to exploit innocent users. Awareness is the first step to mitigate you and your organization’s risk. However, to be truly protected we recommend finding a holistic solution that is able to isolate, detect, and remediate any threat on any channel.
Learn more about how to best defend your organization against advanced threats here.























