In the following update, one can see that attackers have been improving their messaging and are using the pandemic as a “background story” to the ongoing business handled between them and the targets. Opposed to previous attempts we caught at Perception Point that encourages users to see documents or links about the virus itself or a new “vaccine” to treat the disease.
Please feel free to share this info with colleagues, CISO’s, IT Admins etc in order to better prepare for these types of attacks.
Phishing Campaign 1:
“Hope you are safe”
OVERVIEW.
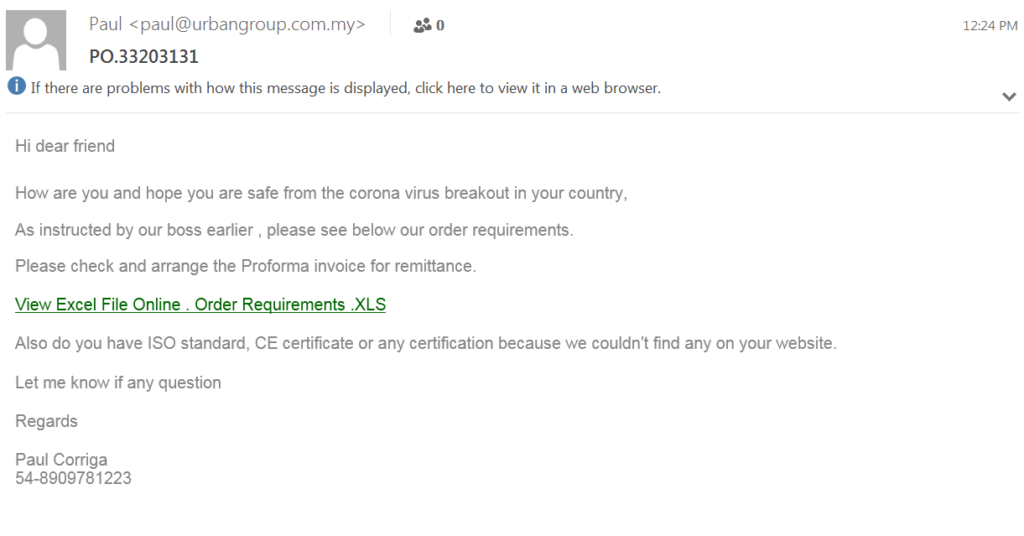
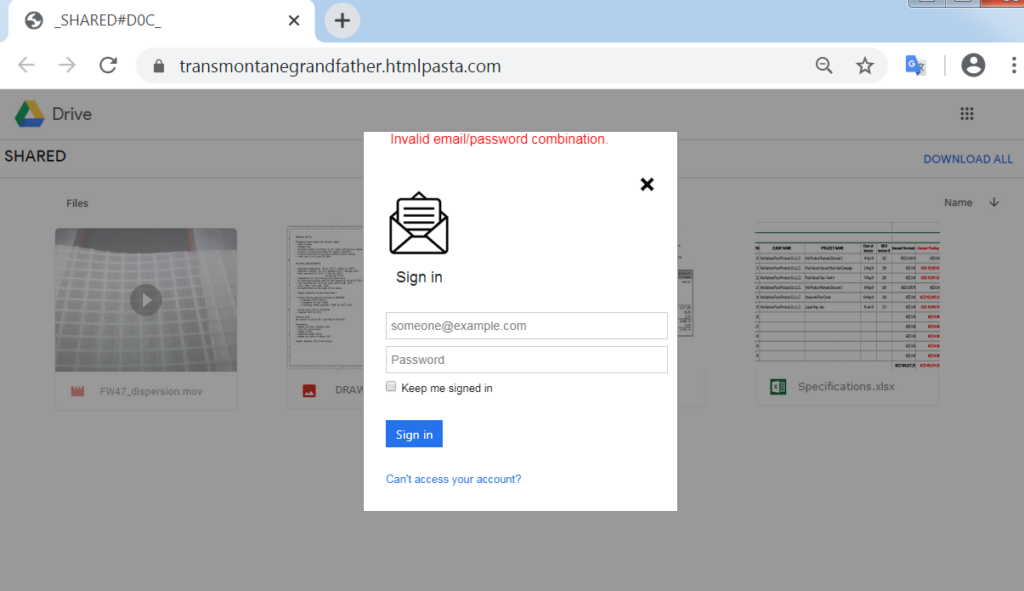
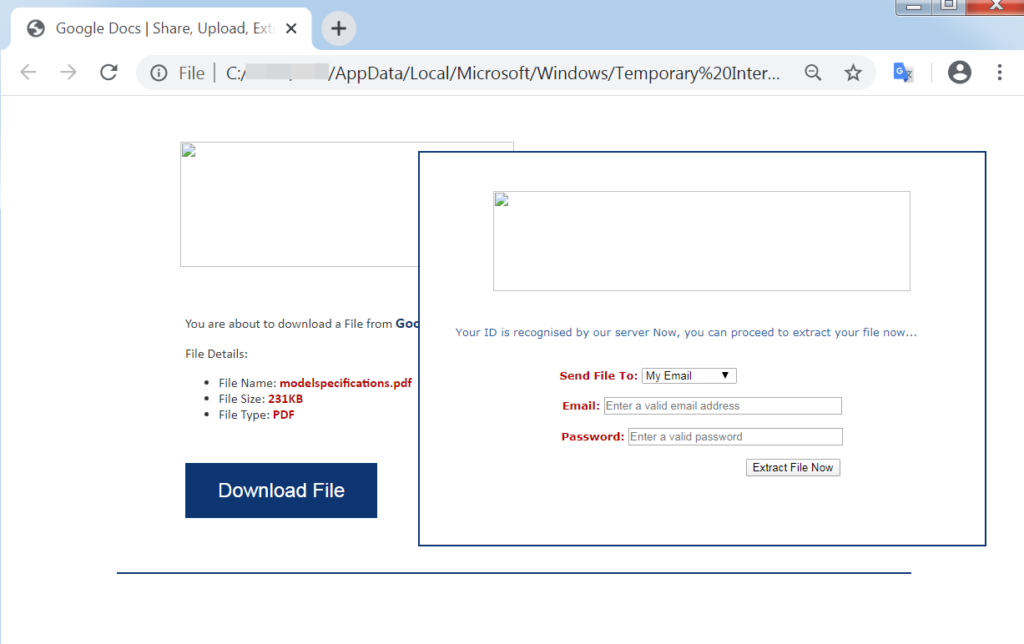
In this campaign, the use of the Coronavirus topic is used only to provide the recipient with sense of previous knowledge between the two sides (“I hope you are safe from the pandemic breakout”). This, coupled with a back story that makes the recipient feel that he already knows what he has to do, can trick the employee to act wrongfully and open the file. In this attack, once the user will click on that link, a well-designed log in page pops up (with fake images in the background of documents), aiming to steal the victim’s credentials.
IOCS.
Subject: PO.33203131
From: Paul <[email protected]>
Source IP: 124.150.141.124
Extracted Links: https[:]//transmontanegrandfather[.]htmlpasta[.]com/
Phishing Campaign 2:
Watch Out for Bank Transfers.
OVERVIEW.
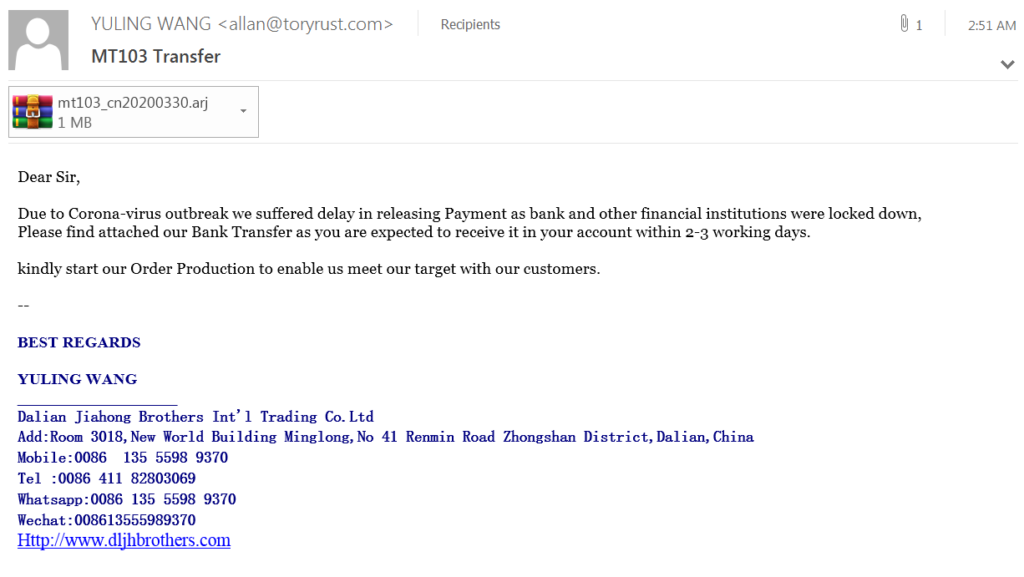
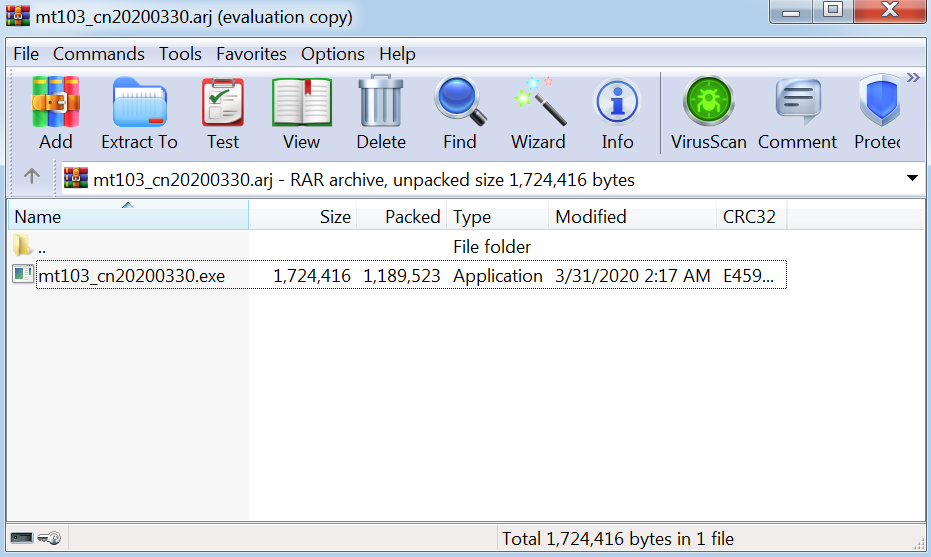
In this campaign, the attacker pretends to be a customer of the target who had to delay the payment to the target due to the “unordinary circumstances”. In the email, the attacker tries to trick the recipient to open the file which includes a description of the expected wire transfer. However, the attached file, which is zipped in order to bypass/evade email security solutions, has a malicious executable inside. This shows that the attacker has done their “re-con” and knows organizations block .exe files through polices but unable to handle archived files. In the case that the targeted victim would have opened the file, a malicious code runs on the background of the end-user’s host.
IOCS.
Subject: MT103 Transfer
From: YULING WANG <[email protected]>
Source IP: 94.177.232.126
Filename: mt103_cn20200330.exe
SHA256: 64f61dd41ec3a411e647f6371b8500666db3c96cc57a8cb0c16d47cceaf12aa9
Phishing Campaign 3:
Short and to the Point.
OVERVIEW.
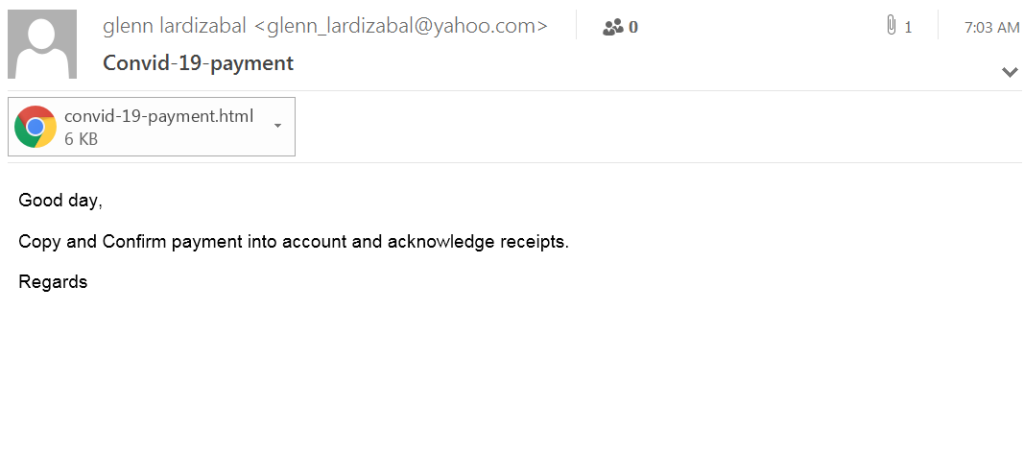
In the example below, the attacker tries to make an impression that the attack is actually a regular, “ordinary course of business” email, short and to the point, trying to lower the target’s guards. The attacker asks the recipient to confirm a payment related to COVID-19. Yet, the attacker attached a html file which is essentially a phishing attempt, to steal the victim’s credentials.
IOCS.
Subject: Convid-19-payment
From: glenn lardizabal <[email protected]>
Source IP: 106.10.241.109
HTML SHA256: a6d2ea20e45b0a3cf0981134a924033acc5fb0aa1d44311130e9bb0093f2f238
Learn more about protecting your organization in our detailed guide to cyber security strategy.























