As the Coronavirus continues to keep organizations world wide working remotely, Perception point continues to see more and more “COVID-19” themed attacks. As always, they are improving in their sophistication and evasion.
Campaign 1 Malware: “Technology Solution For COVID-19”.
OVERVIEW.
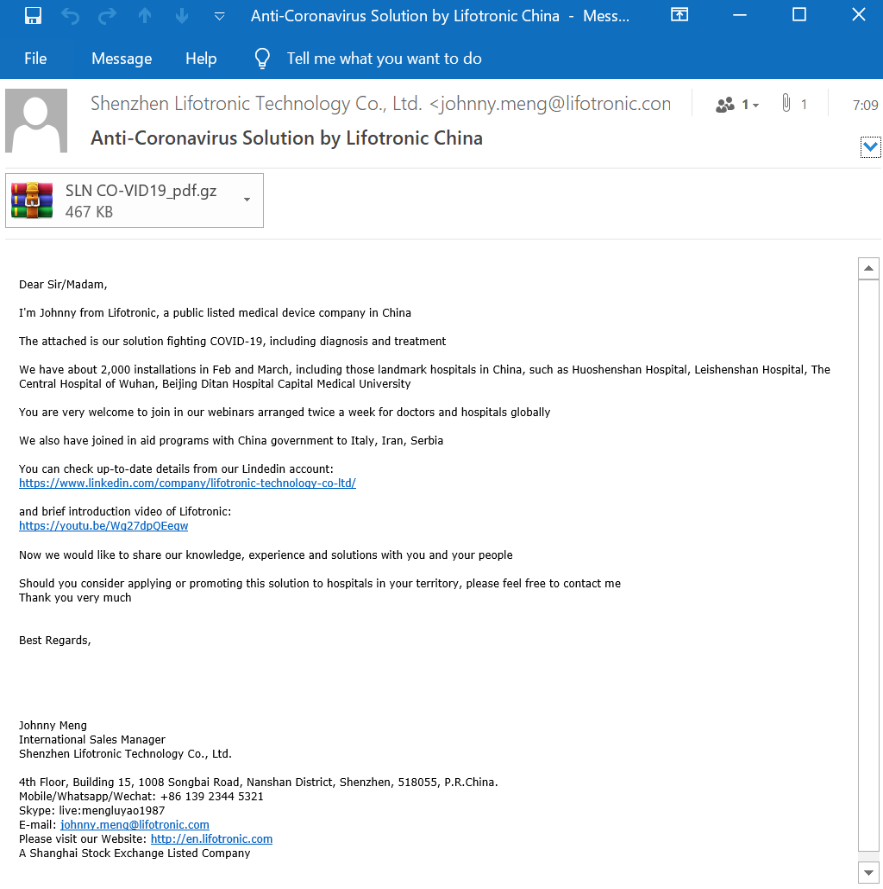
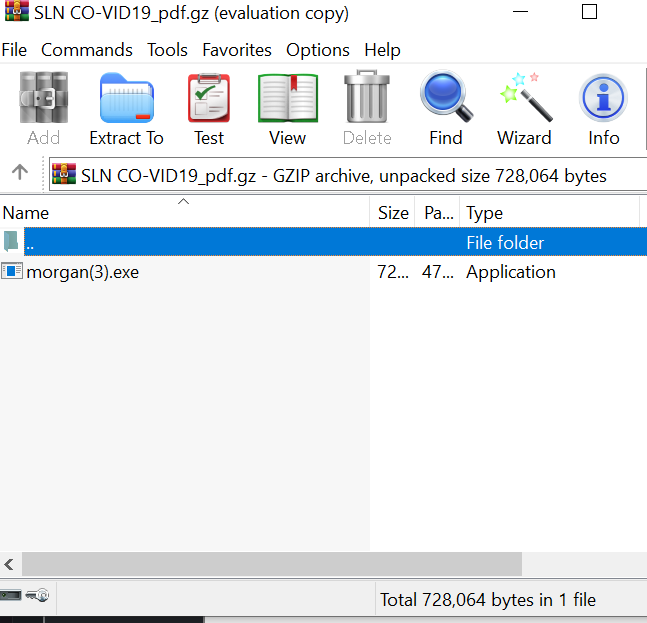
The attacker in this incident has masked themselves to look like a Lifotronic, a legitimate technology company that manufactures medical devices. The text in the email invites the recipient to click on the attachment which is their “solution for fighting COVID-19”. The attached .gz file (like a zip) but has been masked to look like a PDF by titling the attachment “SLN CO-VID19_pdf”. The attachment opens up a compressed .exe file called “Morgan” which installs the Remcos RAT.
IOCS.
- Subject: Anti-Coronavirus Solution by Lifotronic China
- From: “Shenzhen Lifotronic Technology Co., Ltd.” <[email protected]>
- Source IP: 133.18.3.102
- Filename: morgan(3).exe
- Files Hash: 2671331e959904644b8ba770fc1f380382ae397af1abdf63dc5962d5409857c4
MALWARE ANALYSIS.
The malware file is packed, which means the actual malicious code resides inside a second program which purpose is to conceal its payload and only reveal it upon execution. This method is used to evade static AV engines, by continuously changing the “outer layer” i.e the packer, the malware authors can change the signature and evade detection.
Once unpacked, malware spawns a child process of itself and injects malicious code into it. This method is another technique devised by attackers in order to evade AV software that inspects processes during runtime. By injecting code dynamically, the malware authors try to evade the radar of AV software.
Once injected, the code starts its true intentions which is data theft, mainly credentials for known FTP/Browser/Mail clients that might be installed on the victims computer (Here’s the actual list of software: Cyberfox, Pocomail, Google Chrome, Ipswitch WS_FTP, The Bat!, Flock, FileZilla, FlashFXP, Internet Download Manager, k-Meleon, SeaMonkey, IncrediMail, jDownloader, WinSCP, Comodo IceDragon, Opera Mail, BlackHawk, Internet Explorer, Microsoft Outlook, Postbox, Opera, Mozilla Thunderbird, FTP Navigator, OpenVPN, CoreFTP, Mozilla Firefox).
Additionally, the malware interacts with the wireless LAN (if present on the computer). A move we suspect and attribute to ‘lateral movement’ – perhaps it will try to spread to other hosts on the network or send the information to the attackers in order to attribute where they have “landed”.
To summarize, this is a land and expand operation, a weapon built to gain as much information on initial access and prepare for expanding into the rest of the organization.
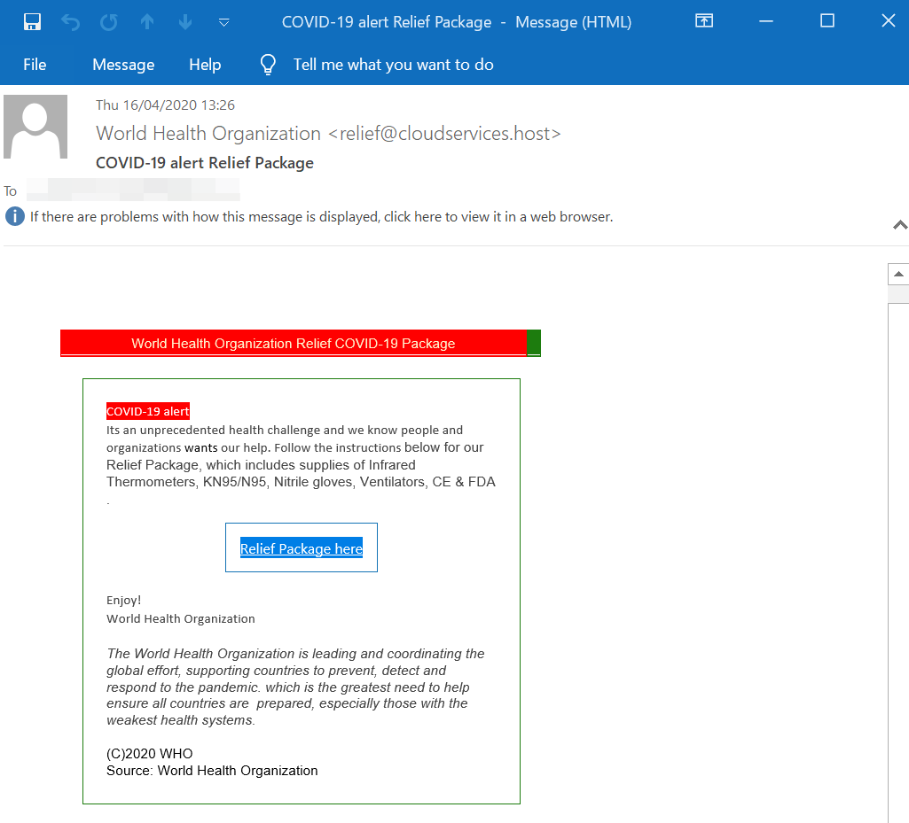
Campaign 2 Phishing: “Well designed WHO website”.
OVERVIEW.
In this campaign, the end-user receives an email that appears to come from the World Health Organization, including a somewhat legitimate-looking domain. The email encourages the recipient to click a link in order to get more information about the “Relief Package”. The link leads to a malicious phishing site which is requesting “donations” and attempts credential theft.
IOCS.
- Subject: COVID-19 alert relief package
- From: World Health Organization <[email protected]>
- Source IP: 37.221.113.93
- Extracted Phishing Link: https://m3928.us-south.cf.appdomain.cloud/[email protected]&3883=99–