Some of these campaigns have added new levels of complexity, such as the use of evasion techniques, as well as evolving with the attack story line itself.
Phishing Campaign 1:
3-stage Evasion Attack.
OVERVIEW.
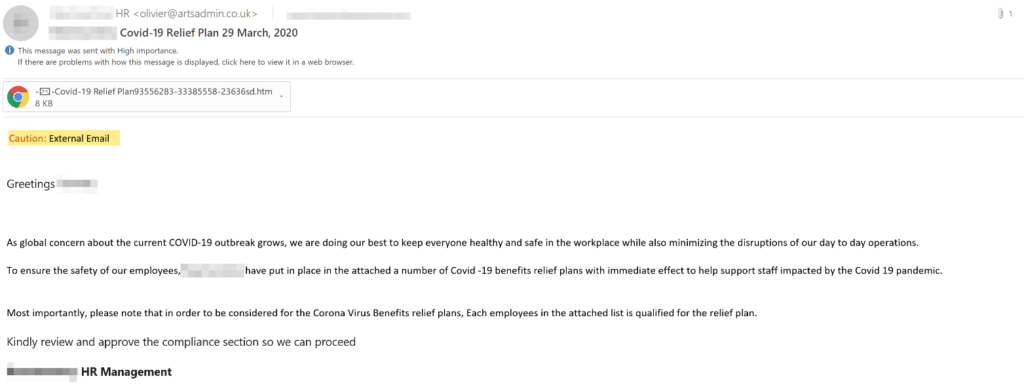
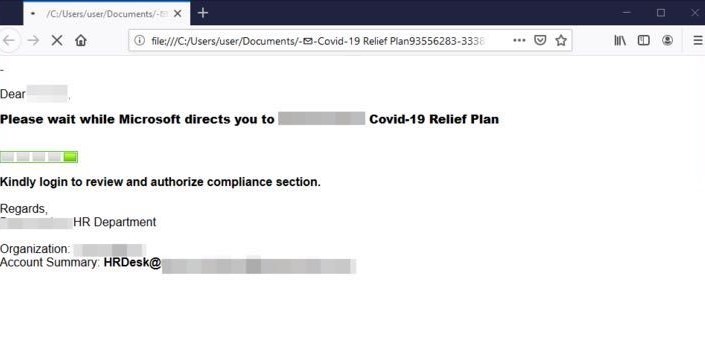
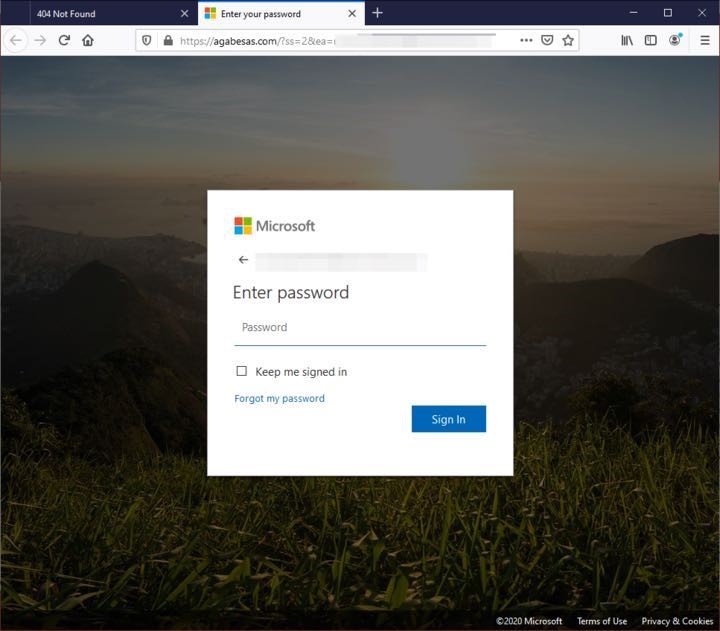
The following campaign was very targeted (name spoofing of actual organization); however, we have seen it change shape and forms in many organizations. The email is spoofed to look like it comes from the customers’ HR department and is supposed to offer employees “COVID-19 benefits relief plans with immediate effects to help support staff”. This invokes the employee to click on the attachment. Once the html file is opened, it shows the below “loading screen” and only after a few seconds does it redirect to an Office 365 phishing login page. This “loading screen” adds another step in the sophistication of the attack as it is an evasion technique.
IOCS.
Subject: “Customer Nae” COVID-19 Relief Plan 29 March, 2020
From: “Customer Name” HR < [email protected]>
Source IP: 146.20.161.110
HTML Filename: -✉-Covid-19_Relief_Plan93556283-33385558-23636sd.htm
HTML SHA256: 1f640760beeaeb96b0c489da769a1ea8e5c0828be7df8d854a9a0cedd40222d
Malware Campaign 2:
The “Vaccine” Has been found.
OVERVIEW.
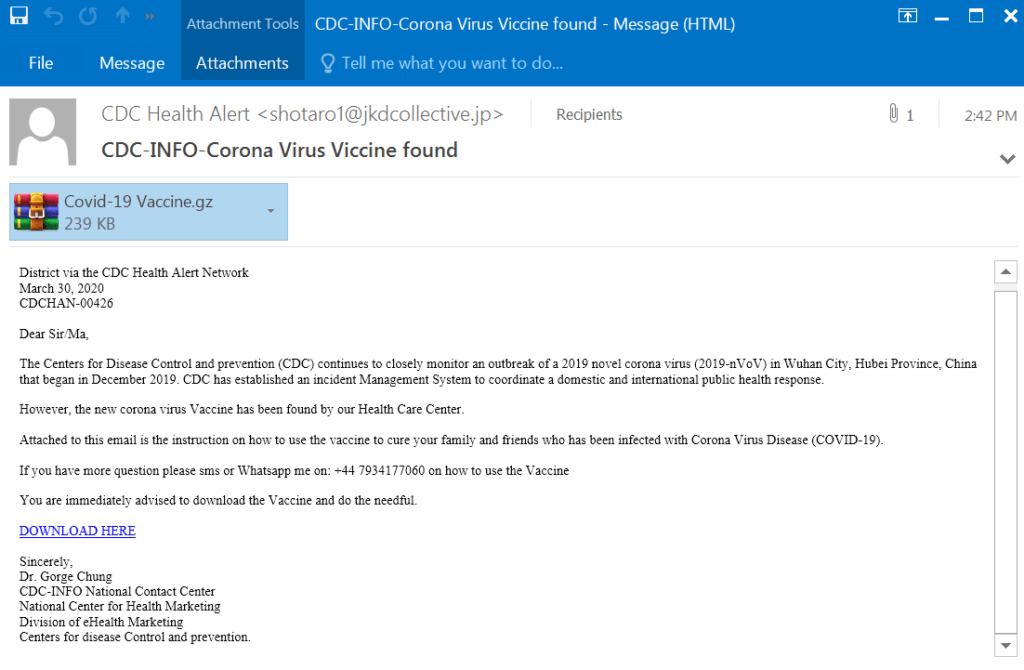
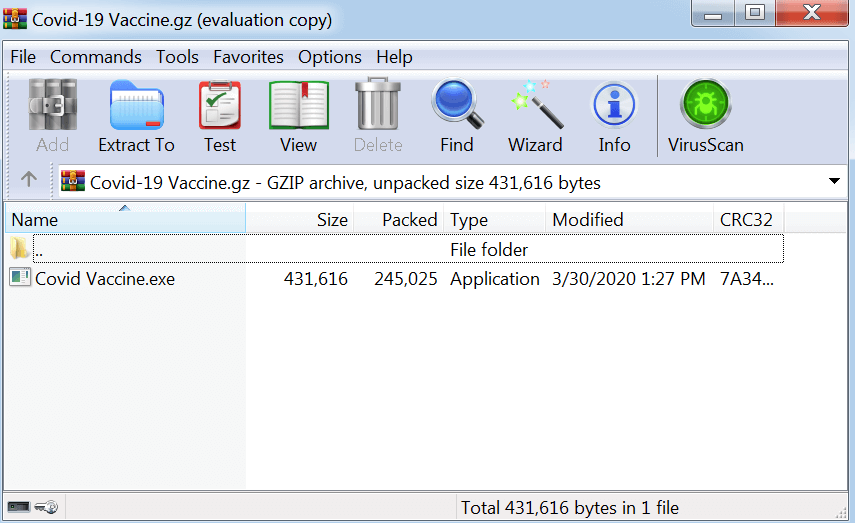
This is the first of a new trend we have been detecting. The attacker is changing the story-line to claiming that the Vaccine for COVID-19 has been found. The attacker has spoofed their name to be CDC Health (the official US health protection agency), and enticing the end user to click the “Download Here” button, which downloads a compressed file with a malicious executable file that is called “Covid Vaccine”. After the user runs the file, a malicious code (a variant of MSIL/GenKryptik.EGQS trojan) will run in the background of the end-user’s host.
IOCS.
Subject: CDC-INFO-Corona Virus Viccine found
From: CDC Health Alert <[email protected]>
Source IP: 120.136.10.54
Filename: Covid Vaccine.exe
HTML SHA256: d0a8b39bc4bd58191a4b6db1a71621e7d9e2e124c05ad01922aafb9eba72205a
Phishing Campaign 3:
Local Outbreak.
OVERVIEW.
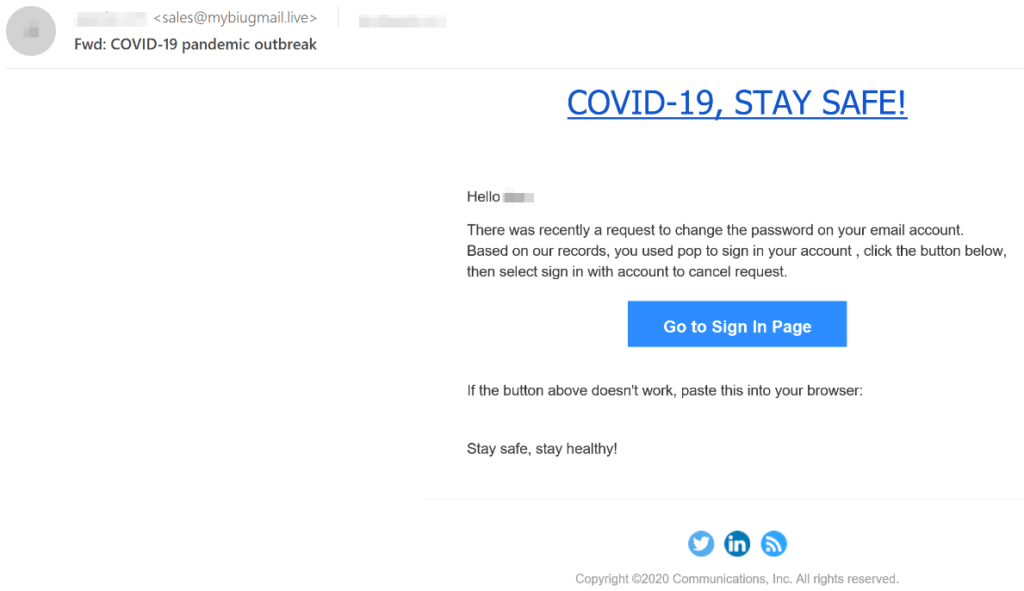
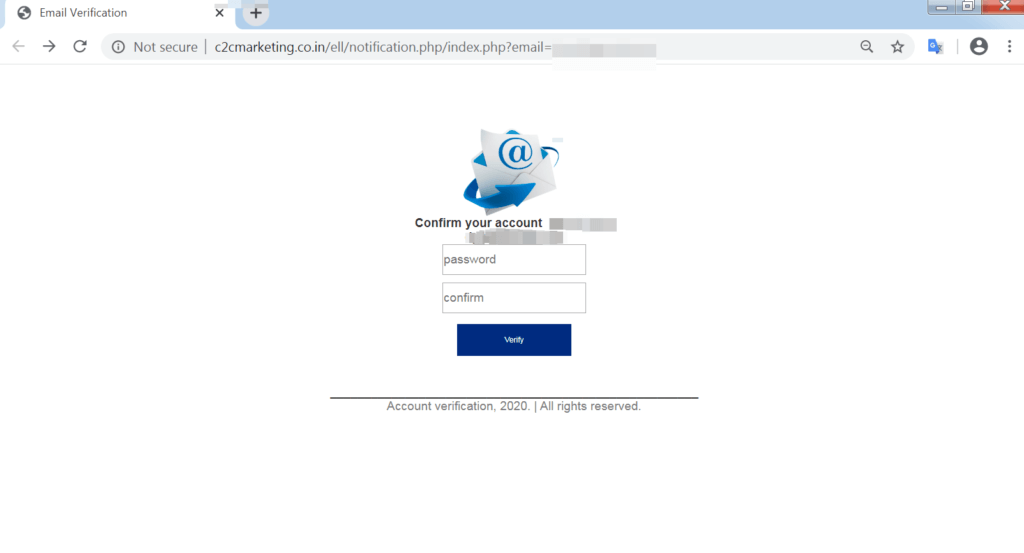
This attacker made it look like he is the DPO officer of the targeted enterprise. In this case it is using the very COVID-19 campaigns that we warn about, as a Phishing Attack itself! The email informs the user that someone has requested to change their password, and if it is not them, they must cancel the request by “signing in”. Once the user clicks on the link; a well-designed phishing page will come up in order to still the user’s credentials.
IOCS.
Subject: COVID-19 pandemic outbreak
From: “Customer Name” < [email protected]>
Source IP: 106.75.107.11
Extracted Links: http[:]//c2cmarketing[.]co[.]in/ell/notification.php/index.php?email=
Phishing Campaign 4:
Missed COVID-19 Voice Call.
OVERVIEW.
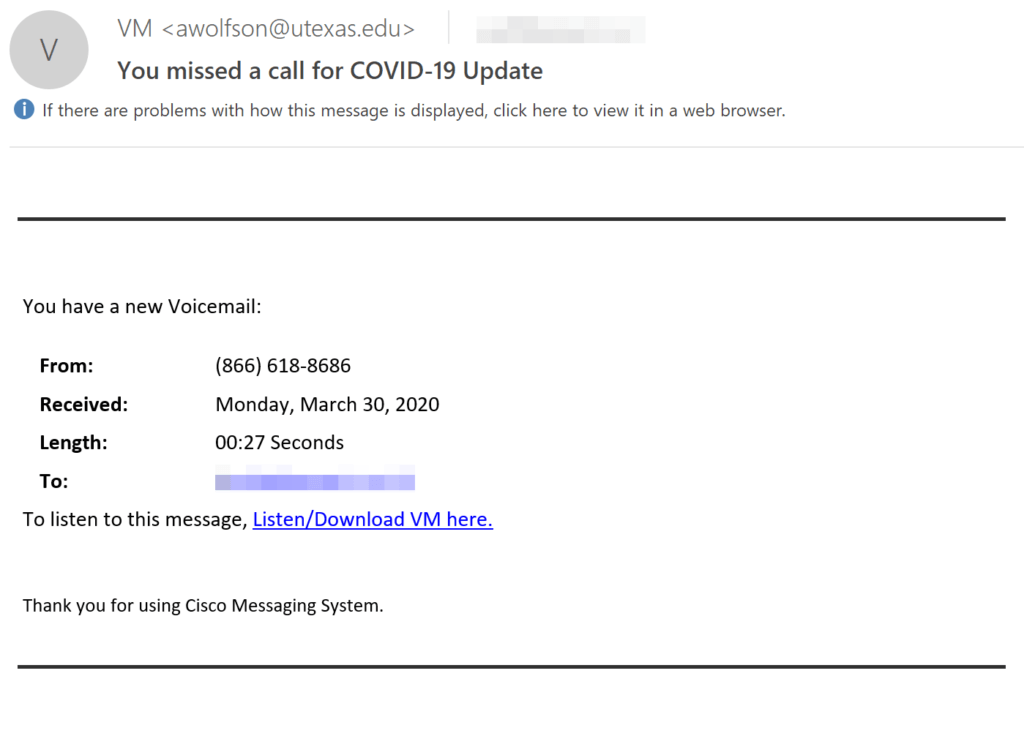
Many who follow our COVID-19 campaign updates, will have seen this campaign before. Taking advantage of organizations that use voice-call services with email notifications, as well as the remote-working situation. The email advises that there is a new voice message regarding COVID-19 Updates to the organization, with a link imbedded to take them to the voice message. This link leads to a malicious phishing website, tricking the end-user to think that he needs to “safely” log-in to hear the voice message, thus stealing credentials.
IOCS.
Subject: You missed a call for COVID-19 Update
From: VM ([email protected])
Source IP: 128.83.139.110
SHA256: c1fa9d46e9978ca1b645b2edf549ef53811a5be1ef911b5a481c4146963ccc18
Extracted Links:
https://adminplanner.blob.core.windows.net/marketingstore/117-Crl.html?sp=r&st=2020-03-30T05:19:49Z&se=2020-04-11T13:19:49Z&spr=https&sv=2019-02-02&sr=b&sig=vYMJxstg63R0VQv0VaN1xZp01xMTchrI1xtMm6rF4Ls%3D#