In the following update we collected 3 different phishing attacks which demonstrate how attackers have evolved.
We would like to highlight the “Key notes” for Phishing Campaign #2. These insights give CISOs and security experts additional information on recent phishing techniques Perception Point intercepts on a daily basis. Please feel free to share these insights, we are more than happy to share findings with peers and enterprises in order to help prevent future cyberattacks.
1. Phishing Campaign 1: Fake Corona “lab results”.
OVERVIEW.
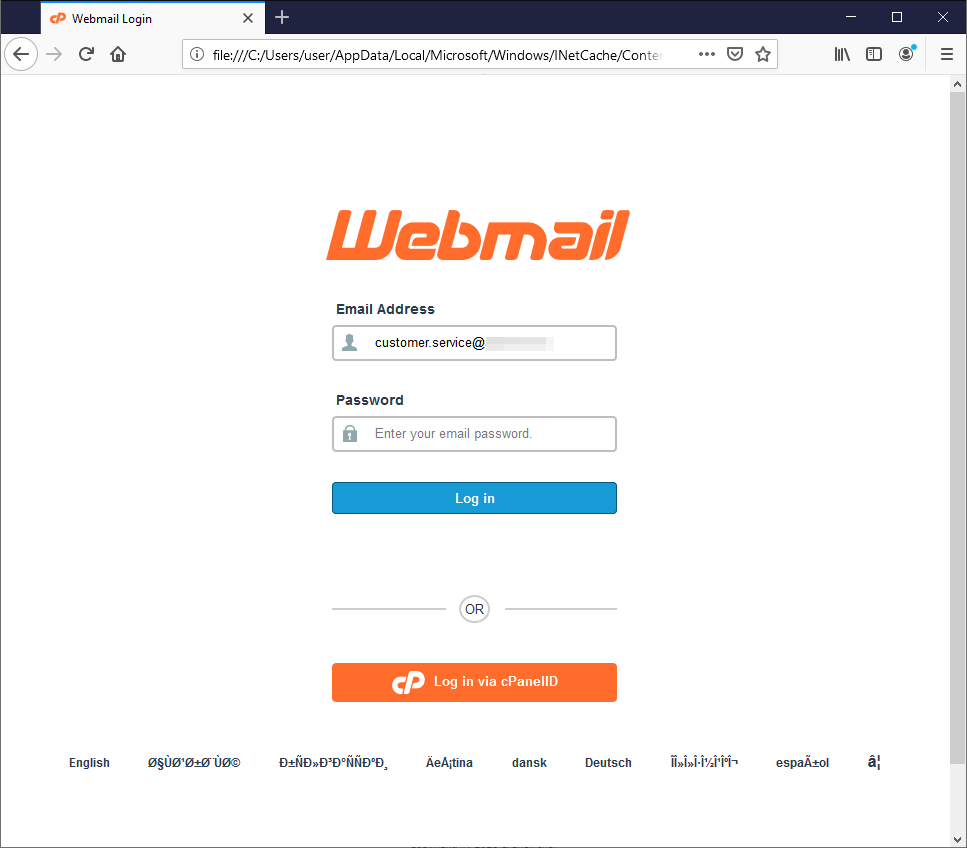
In this phishing campaign the attacker pretends to be someone from within the targeted organization by using the organization name in the “from address”. In this attack, the malicious actor sends an email confirming that someone within the Organization is positive for COVID-19, hoping that people will want to open it in order to find out who it is. In the end, the email contains an html attachment with a login-page attempting to steal the end users’ credentials.
IOCS.
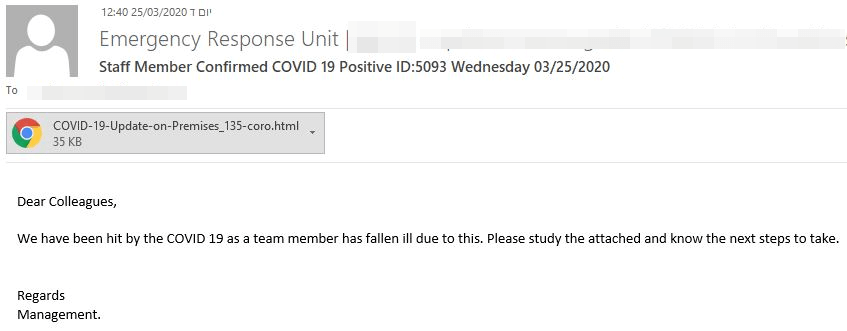
Subject: Staff Member Confirmed COVID 19 Positive ID:5093 Wednesday 03/25/2020
Attached HTML Filename: COVID-19-Update-on-Premises_135-coro.html
Attached HTML Sha256: 71c9931f88d8c4b5b806d5b37d3c49ba6bf879222cde0ec22e2d2116f426d290
Source IP: 69.89.18.3
Sender Domain: bh-ht-16.webhostbox.net
2. Phishing Campaign 2: Fake emergency update.
OVERVIEW.
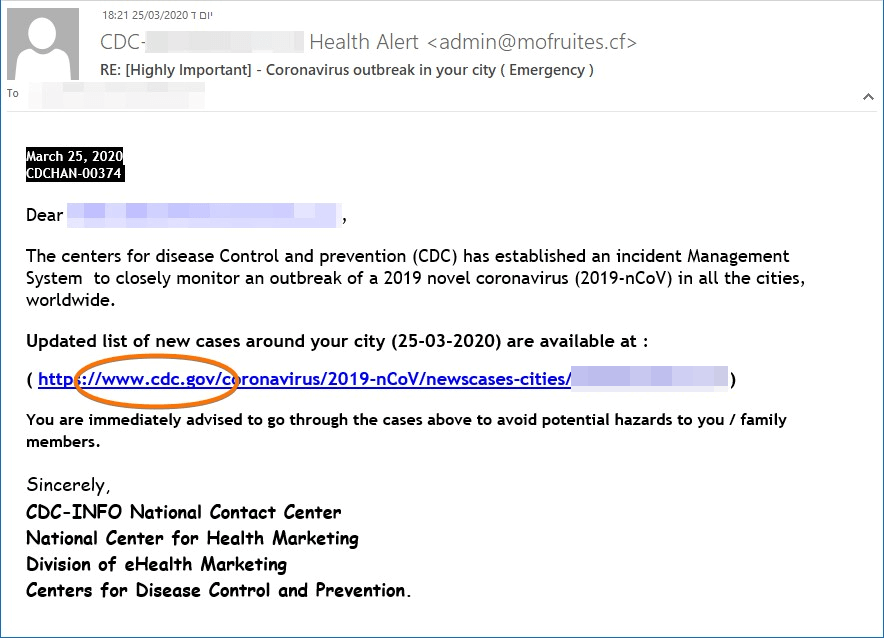
In this campaign, the attacker pretends to be from the CDC (Centers for Disease Control and Prevention). It has a “call to action” link that urges the recipients to click on in order to see if there is an outbreak of the COVID-19 virus around them and how to avoid “hazards to them and their families”. The link is disguised to come from a known domain: cdc.gov, but in reality, it is actually a login page stored on googleapis.com, allowing the attacker to steal the target’s credentials.
IOCS.
Subject: RE: [Highly Important] – Coronavirus outbreak in your city ( Emergency )
Source IP: 89.40.115.244
Sender Address: [email protected]
Phishing URL: https[:]//storage[.]googleapis.com/ghfr46e57r6gug7tiguh.appspot.com/g5r76t87h/[email protected]
Redirect URL: https[:]//x4reyd5du[.]gb.net//vc65dtcu/smoth/[email protected]
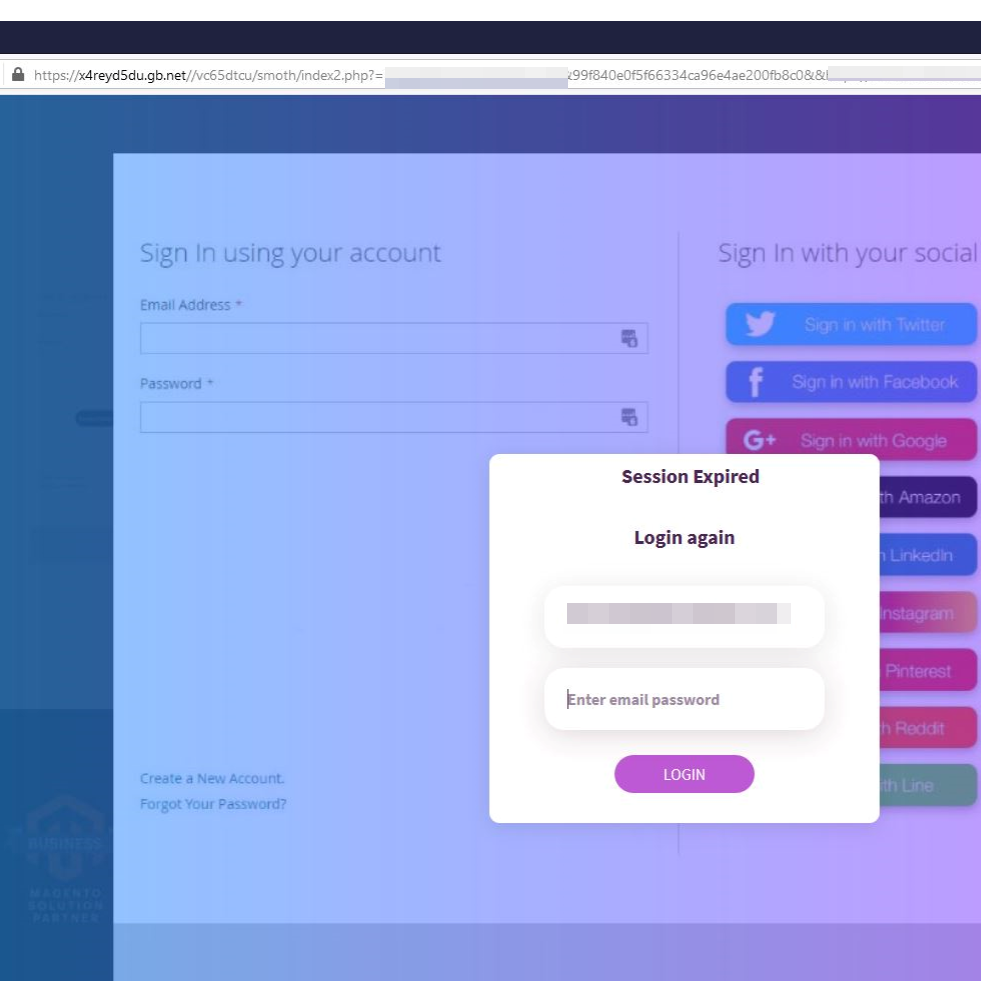
Key Notes.
- Lately Perception Point’s system has been witnessing an increasing number of phishing websites that are hosted on Google, AWS & Azure Web Sites. These attacks are leveraging a legitimate domain (for example “windows.net”) but are in fact hosting malicious content.
- This attack was most likely executed by a easily downloadable “phishing kit”. Within a few clicks of a button, this kit can create phishing campaigns hosted on those cloud providers and themed as corona-related (or any other).
3. Phishing Campaign 3: Missed call COVID-19 Update.
OVERVIEW.
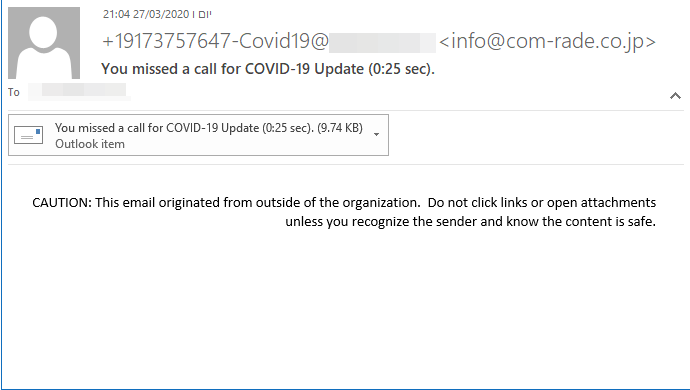
This campaign which we catch often, mostly targets organizations that use voice call services with email notifications. As usual, the attacker makes an attractive subject “You missed a call for COVID-19 update.” In this attack, the malicious actor sends an empty email with an “.eml” file attached. Once the attached file is opened, there is another “.html” attachment – which, in its turn, leads to a phishing website hosted on windows.net. This is a known evasion technique, trying to hide something malicious within a clean file.
IOCS.
Subject: You missed a call for COVID-19 Update (0:25 sec).
Attached HTML: .htm
Attached HTML Sha256: 8b6c31b9124f0ddb1553034eea4c90ca89fce1751ca947e50b5df57308abef17
Sender IP: 27.116.29.65
Sender Address: [email protected]
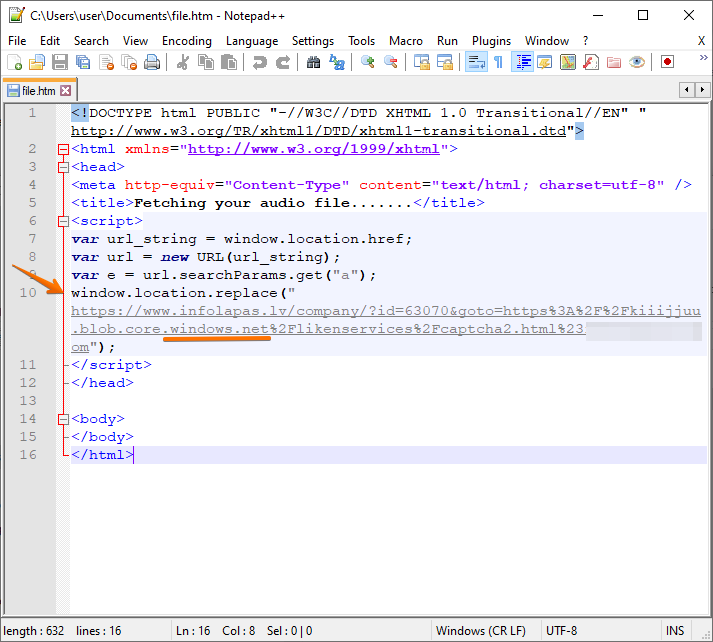
Phishing URL: https[:]//www[.]infolapas.lv/company/?id=63070&goto=https%3A%2F%2Fkiiijjuu.blob.core.windows.net%2Flikenservices%2Fcaptcha2.html%[email protected]
Redirect URL: https[:]//kiiijjuu.blob.core.windows.net/likenservices/captcha2.html#[email protected]
The html contains a JavaScript code that leads to a phishing website attempting to steal credentials: