Overview
Since COVID-19 became a global issue, threat actors have been capitalizing on the pandemic and leveraging the situation to do what they do best: trick people. Recently, our advanced threat detection platform has detected an increase in campaigns related to the COVID-19 pandemic. In these campaigns attackers pose as different health organizations around the world including the World Health Organization (WHO). In this post, we discuss some of the campaigns caught by our anti-phishing engine and analyzed by our Incident Response team. Read on to learn more.
1. Malware: Ostap/Trickbot spoofing the World Health Organization
This first example involves attackers trying to spoof the World Health Organization:
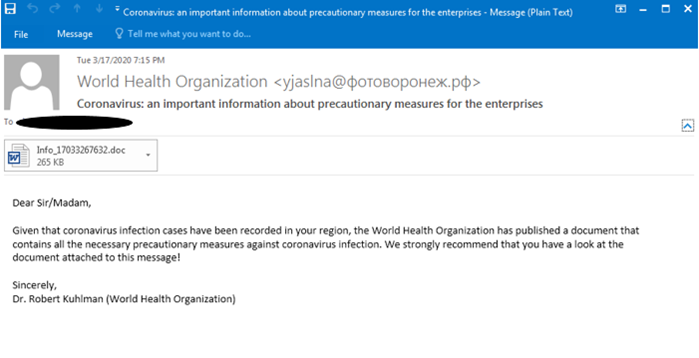
In the email above attackers try to take advantage of global hysteria by creating a campaign impersonating the WHO. While the sender’s email address and the subject line are enough for us to flag the email, the recipients of this message may not be as savvy. The attacker emails individuals a document supposedly containing official precautions against COVID-19. Instead of the alleged precautions, what the attachment really contains is a Word document with malicious macros. If the recipient enables macros on the attachment, it will drop and run a JavaScript downloader that installs ostap/trickbot malware, completing the attacker’s goal.
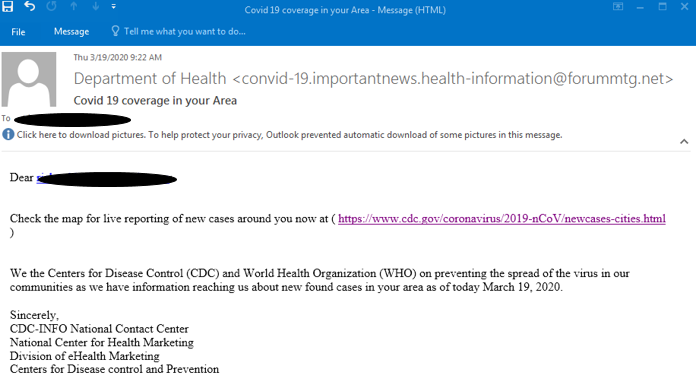
2. Credential Phish spoofing the “Department of Health”
Next, attackers try to spoof the Department of Health:
In this example, attackers try to leverage the fear of COVID-19 by tricking the victim into clicking a link. The link is supposed to be a legitimate government page. However, once the victim clicks on it, they are redirected to a spoofed Outlook login page:
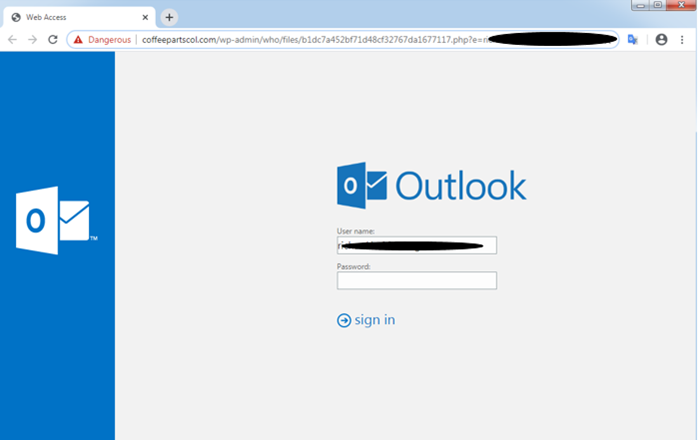
Similarly to many phishing campaigns, the motive is made clear: gain user credentials. However, unlike most phishing campaigns attackers try to achieve this goal by capitalizing on the fear surrounding the COVID-19 pandemic. This added bit of manipulation somehow makes this phishing attempt even more malicious than usual.
Recommendations
- Stay alert. Attackers will continue to leverage whatever they can to infiltrate your organization for financial gains. Train your employees to be vigilant especially in these troubled times.
- Scan all content, across channels. Attackers are waiting for the right moment to hit. Make sure you monitor and actively scan all inbound traffic to intercept any form of attack.
- Adopt tools with robust anti-spoofing capabilities. Only advanced email security measures can properly handle and prevent the new phishing and BEC attempts that “flourish” now.
For more information about how you can protect your organization from a suite of advanced threats, read our brochure today!