Train the machine—not just the employee. Hackers know that many companies rely on security employee training alone, so they’ve been upping their game to trick even the most trained employees into phishing scams.
Phishing email attacks are nothing new.
These attacks have been around for 15 years, but they are still one of the top risks for businesses today. A quick Google search of “how to spot phishing email scams” will show you articles from as far back as 2006. Yet they still happen all the time.
So Why Are These Scams Still Happening?
According to Verizon’s latest Data Breach Investigations Report, more than two thirds of data breaches involved social engineering attacks such as phishing.

1. Advice is Static.
Advice to employees has remained the same. So, that means that with 15 years of knowledge about phishing (and training employees), the attacks still happen. In fact, these types of attacks have been increasing, meaning employee training is not enough.
Here’s advice from US-CERT that was created in 2005 (then updated in 2008). You can find the entire report here.
- Filter spam.
- Don’t trust unsolicited email.
- Treat email attachments with caution.
- Don’t click links in email messages.
2. Incentive for hackers is strong.
It’s a lucrative business for hackers. According to a new report from Coveware, a typical total now stands at $84,116. That’s a little over double the previous figure of $41,198.
3. It’s easy.
Companies that rely on training alone are still highly susceptible, according to the most recent research. A research group from Vanderbilt, Dartmouth, and MITRE put test subjects through extensive training on detecting and avoiding phishing scams. 90 days later, the subjects had forgotten most of what they learned and were susceptible to phishing emails at the same rate as before the training.
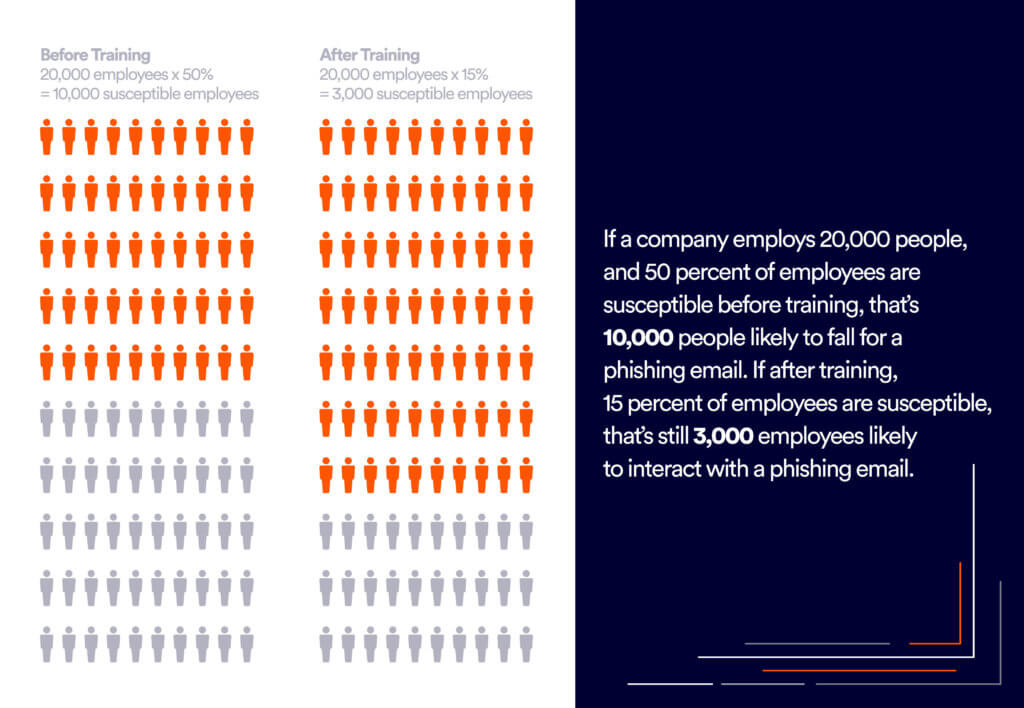
According to the stats above, training only solves 70% of the problem.
A study from Carnegie-Mellon, came to similar conclusions: that employee training alone is not enough. So, while security awareness training helps organizations meet their regulatory and legal requirements, it’s not enough to stop phishing breaches.
How Hackers Search for Companies to Phish
It’s easy for hackers to find companies that rely on employee training and on insufficient built-in email security features by checking which email security they use. This information can be found for free by using tools such as BuiltWith and MXToolBox.
Cons of Using Phishing Training Programs Alone
- Not always up-to-date. You simply can’t train on the unknown. New phishing scams pop up regularly and can hit without warning—unless you have the right protection in place.
- Error-prone. Humans aren’t computers. We make mistakes. For anything security-related, we shouldn’t be the only line of defense. For example, as long as a fake email looks more or less as they expect them to, then most users will continue on with their normal routine.
- Not Flexible. Companies that see a lot of employee turnover will have a hard time making sure each new employee receives the correct training at any given time.
- Labor-intensive. Training can be labor-intensive and time-consuming. In companies with regular turnover, it can be difficult to keep up. You have to constantly be training new employees.
- Costly. There are many programs out there dedicated to training employees. The prices vary depending on the type of training. Not all have the same features. Some offer pen testing, phishing simulations and more. One of the most well-known training companies is KnowBe4.
Security Awareness Training Programs
We put together the following list of some of the most popular training programs available today. Paired with the right built-in email security features, the following programs will greatly reduce your chances of successful attacks.
- Wizer
- Awarego
- Inspired eLearning
- KnowBe4
- Infosec Institute
- usecure
- Hutsix
- Cybsafe
- TechGuard
- CybeReady
- Dcoya

Perception Point Hack
You shouldn’t rely on employees to notice sophisticated phishing attacks themselves. Instead, we suggest following Gartner’s advice about installing extra security protocols.
Unfortunately, training is not going to stop the problem 100 percent of the time. And even with other security controls to prevent or contain an incident, there still may be a breach and cleanup. As with any control, the goal is to reduce the risk to an acceptable level, then live with the residual risk.
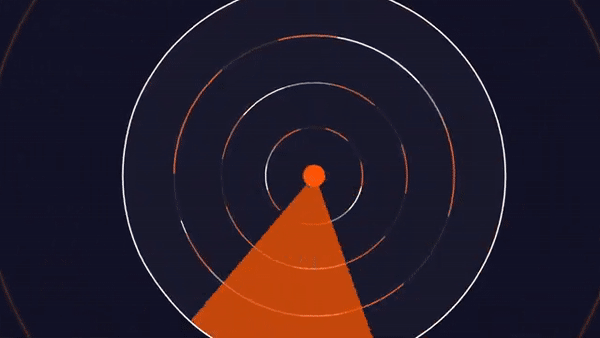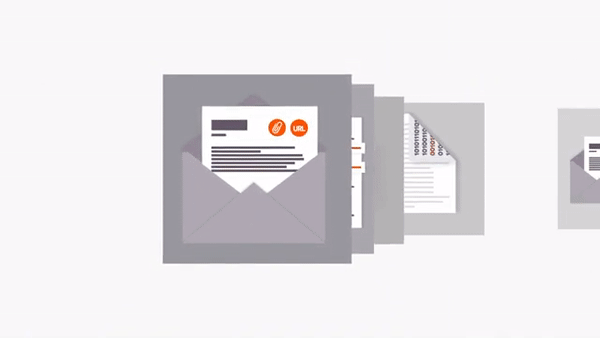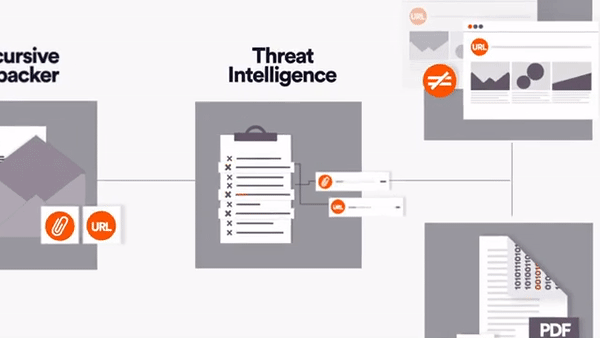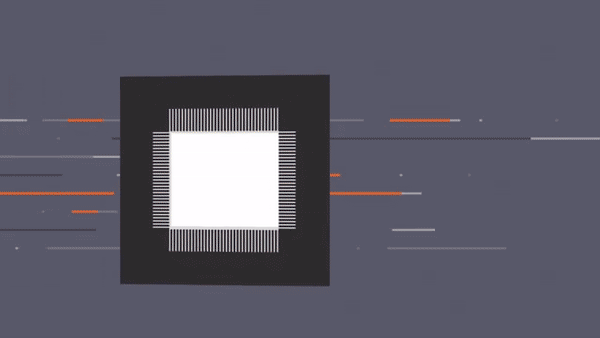
The Perception Point Solution.
Unlike a person, Perception Point’s unique tools (see below) can tell when an email is a forgery, and send it straight to quarantine or deliver it with disabled links and warnings.
By combining four layers of anti-phishing prevention, Perception Point’s unique engines have been developed specifically to outsmart any advanced phishing attempts, and keep pace with the latest techniques: