Background
With an annual revenue of almost $42 billion, Microsoft takes the lead as a software provider for a majority of companies in a wide variety of industries. Recognized and trusted by victims, the well-known brand is a favorite target of attackers for a variety of email phishing campaigns.
Here we’ll be presenting a recent phishing campaign intercepted by Perception Point’s advanced email security service and how users can identify this type of dangerous campaign and prevent them from occurring.
In this article, we present an attack campaign delivered through an email that spoofs Microsoft. In this campaign, attackers are trying to convince the victims that they have purchased Microsoft Defender Protection. The email lures them into voluntarily calling a toll-free number to cancel their subscription and “verifying” their payment details with the attackers.
The Microsoft Phishing Email
The attacker sends the victim an email with an order confirmation for Microsoft Defender Protection. The email also contains a phone number that the attacker hopes the victim will use to call and cancel the order. The user’s personal details and credit card are compromised once the user makes the phone call to the toll-free number within the email to verify his payment details cancel the order (credit card number, expiration date, etc).
Below you can find two distinct emails that were using the same type of attack.
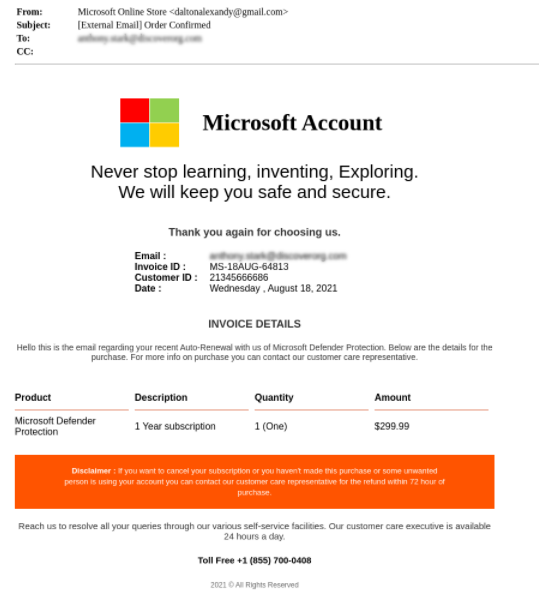
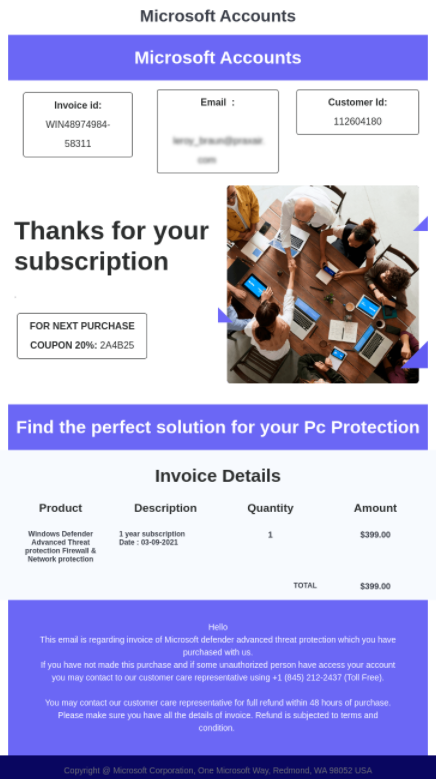
In this campaign we have noticed a variety of ways attackers use to legitimize their emails:
- Fake auto-renewals. Some emails claim the purchase is not new but an auto renewal.
- Fake Customer Care Support. Attackers also attempt to give themselves credibility by mentioning that the phone number belongs to Microsoft’s customer care or a self-provided customer care service authorized and approved by Microsoft. Some emails in these campaigns eliminate any sign of urgency which makes the email seem more legitimate.
- A Toll-free Call Number. A toll-free number strikes users as a legitimate and safe number used by enterprises for the convenience of their customers.
The First Warning Signs for a Phishing Attack
Let’s highlight some of the major red flags for the user that reveals the actual goal of these emails:
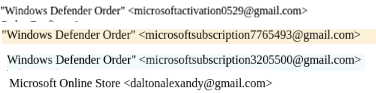
- From address: When looking at the “From” address we see a classic example of brand impersonation.
The mail “From” name is Microsoft-related (Microsoft Online Store or Windows Defender) but the domain is Gmail.
2. Missing Account Name: Services often collect emails and names of users who have signed up for their services in the past and are stored in their marketing databases.
This is the reason emails usually begin with greetings that include a user’s name.
Here is an example:

The Microsoft phishing emails do not contain such a greeting. This tells us that the attacker does not have that information, which is a strong indication of a phishing attack.
That raises the question: How was the attacker able to find these email addresses?
Most often, attackers use emails that were leaked as part of a data breach. It is always good to check if your email address was leaked (using free websites such as Firefox Monitor).
3. Urgency: Giving the victim a sense of urgency is one of the major red flags of phishing. Although not all emails in this campaign use it, some mention that the victim has only 24 or 48 hours to make the call to successfully get a refund.
The Fine Line Between Scam and Authenticity in Phishing Attacks
Many of the emails in this phishing attack include designs that correctly imitate that of the brand (in this case, Microsoft). Users that are in a rush or not educated can easily be tricked into thinking these emails are from the brand.
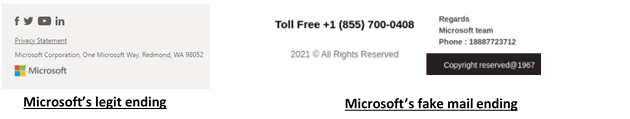
- Logo: Not all of the emails contain a Microsoft logo (or even a fake).

- Email ending signature: Microsoft emails will usually contain social media logos (Twitter, Facebook, YouTube, Linkedin) that redirect users to the official Microsoft profile in the social media platform after clicking on them.
In addition, legitimate emails contain Microsoft’s copyrights.
- Grammar: The emails contain numerous capitalization errors. Legit purchase order emails are formal, auto-generated and free of these types of mistakes.
Here are a few of the errors:
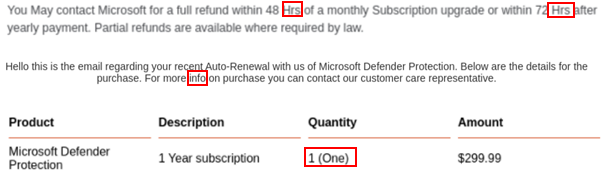
- Design: Although the attackers claim to be Microsoft, none of the emails actually look similar in design. The attackers use backgrounds and bold text to lure the victim into contacting the attacker via a phone call.
Recommendations to Avoid Phishing Attacks
- Regularly check if your email address has been leaked and is vulnerable to phishing attacks.
- Never give personal information, especially over the phone.
- Be aware of your organization’s technical stack and services.
- When in doubt, ask for a second opinion from your company’s security expert or IT team.
- Try and validate information with a third party. For example, in this case you can check with your credit card company if you recently purchased Microsoft Defender.
- For organizations, use an advanced email security solution with dynamic analysis of files and URLs, so that these types of email attacks won’t ever land in your user’s inbox. By intercepting these emails, you don’t need to rely on your employees’ ability to catch these sophisticated phishing attacks.
Read more about Perception Point’s advanced Email security detection technology to help secure your business.
Here’s some related content you may enjoy: How to Prevent Phishing























