Over the last week the analysts on Perception Point’s IR team have noticed an emerging phishing threat involving Dropbox. While attackers spoofing Dropbox in their malicious campaigns is not new, this particular effort stands out due to its scope and sophistication. Read on to learn more.
How it works
This new attack is classified as a 2-step phishing campaign, meaning that unlike most phishing attacks that lead the victim directly to a malicious site, the user is first directed to a clean site with a button or clickable text. By notifying the user that they have received a fax or document, the threat actor attempts to lure the victim into pressing on the button or text. Once the user clicks on the button or text, they are led to a malicious site and asked to log into their account. The user unknowingly falls for the attacker’s scam, hook, line, and credentials.
Figures 1-4: Attack examples
How it spreads
What makes 2-step phishing attacks unique is that they are usually delivered by emails that have already been compromised in the same attack.
Once an attacker gains access to a mailbox, they typically use it to further the campaign by sending more phishing emails to the victim’s contacts. This causes the attack to scale exponentially. Recipients are more likely to trust a message from a known sender, which thus leads them to falling for the phishing attack and continue the cycle.
What is the scope
When the Perception Point IR team initially reported on this campaign, 49 different companies had at least one compromised employee fall for this attack. We knew this because our advanced threat detection platform prevented this phishing attack from entering a client’s environment.
Since their initial findings on Thursday, August 19, 2022, our platform detected over 30 more compromised companies.
For example
We have seen many examples of why this attack is so successful. For now, let’s zero in on one:
A ShopperLocal employee was compromised. The attacker uses this compromised account to send out this 2-step phishing attack to various contacts and known vendors. In our experience, if a phishing email comes from someone you know and work with, there is a high probability that you will fall victim to the attack. Based on the success of this campaign, it is likely that the attackers are savvy enough to know who to target for the best results.
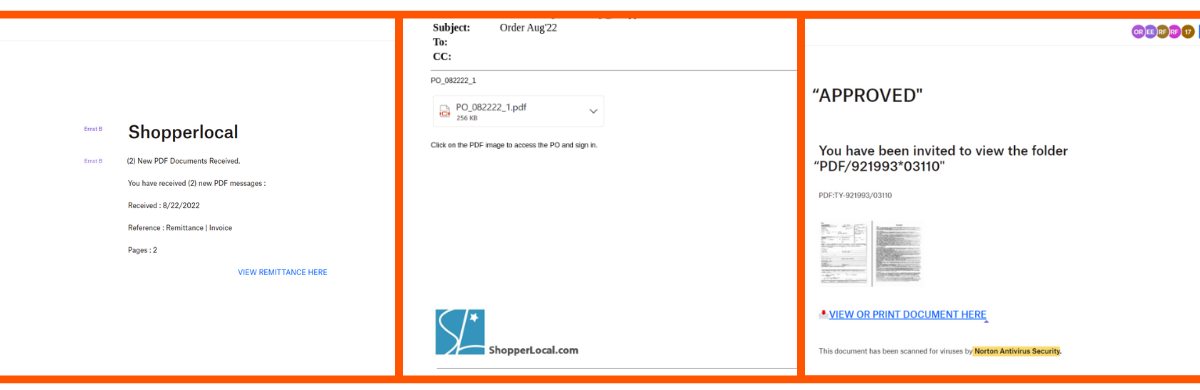
Figures 5-7: ShopperLocal attack
As you can see in the images above, there is a template for the attack that changes according to the compromised company. There are also minor changes between different pages (the location of a hyperlink, a random Microsoft/Adobe icon, etc.) that make it difficult for visual detection algorithms to detect.
We have also noticed customized templates for spreading the attack internally. Instead of using the company name in the malicious site, these attacks will feature generic wording like “shared folder” or the like.
The bottom line
This is a major phishing campaign that is currently and actively harming many individuals and organizations. We haven’t seen many phishing campaigns as successful as this one. It is important for people to know that this attack is occuring, as one of the only ways to stop this campaign is through user awareness. The other way is by implementing a strong, effective email security platform that is able to detect and prevent advanced attacks like these.
Learn more about Perception Point’s anti-phishing technology here.
Here’s some related content you may enjoy: How to Prevent Phishing























