Over the weekend Perception Point’s IR team discovered a 2-step phishing campaign that utilizes a video to deliver its payload – a link to a phishing site. The email account used to send this was taken over (ATO) making it even more dangerous. Read on to learn more about this advanced attack.
How the Phishing campaign works
This attack appeared in an email sent to our client. However, due to the content of the email, the message was flagged by our advanced threat detection platform and never made it to our client’s inbox. It was analyzed by the Perception Point Incident Response team, who reported that the email contained a fake invoice seemingly delivered via Egress, a British company that provides email security services like encryption and, ironically, anti-phishing software. *Note how the email body also contains the sender’s signature, alluding to an external account takeover (ATO), but more on that later.

Figure 1: The phishing email
When you click on the invoice, it leads to Powtoon’s website, a platform that allows people to share visual content. A site like this is ideal for cyber attackers, as using a legitimate platform to execute their malicious payload increases an attack’s “legitimacy”. Here, the attacker uploaded a video that reveals the malicious payload – a link to a malicious site – when played.
This is a 2-step phishing attack, meaning that the attacker prompts the user to click on a button or link within the initial web page in order to redirect them to the malicious site. It is on this secondary site that the attacker attempts to steal the user’s credentials.
A phishy and tricky attack
While this may seem like an obscure phishing attack that surely no user would fall for, the attacker employs a series of tricks to increase the attack’s success rate:
- The fake invoice originates from a “legitimate email account,” which was actually compromised, and appears to be using an email encryption service (Egress). The message contains the company’s logo and assures the recipient that they “have received a secure email” (Figure 1).
- The first malicious payload is a clickable link within a video hosted on a legitimate platform, Powtoon.
See the video below.
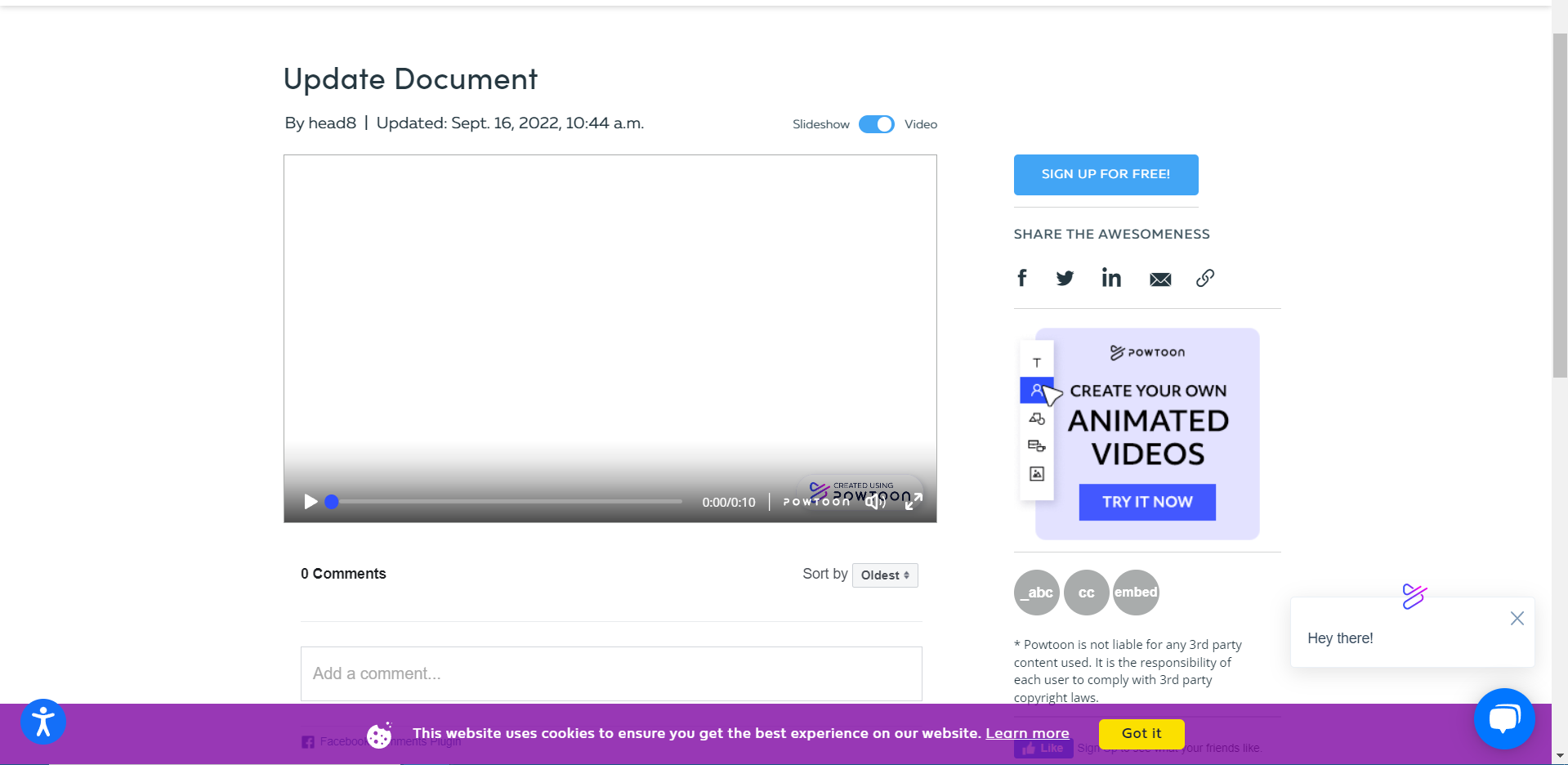
Figure 2: The video hosted on Powtoon – which has since been removed by Powtoon, after they were made aware of the attack
- When played, the video displays an Outlook logo (a known brand), and prompts the user to click, to view the document.
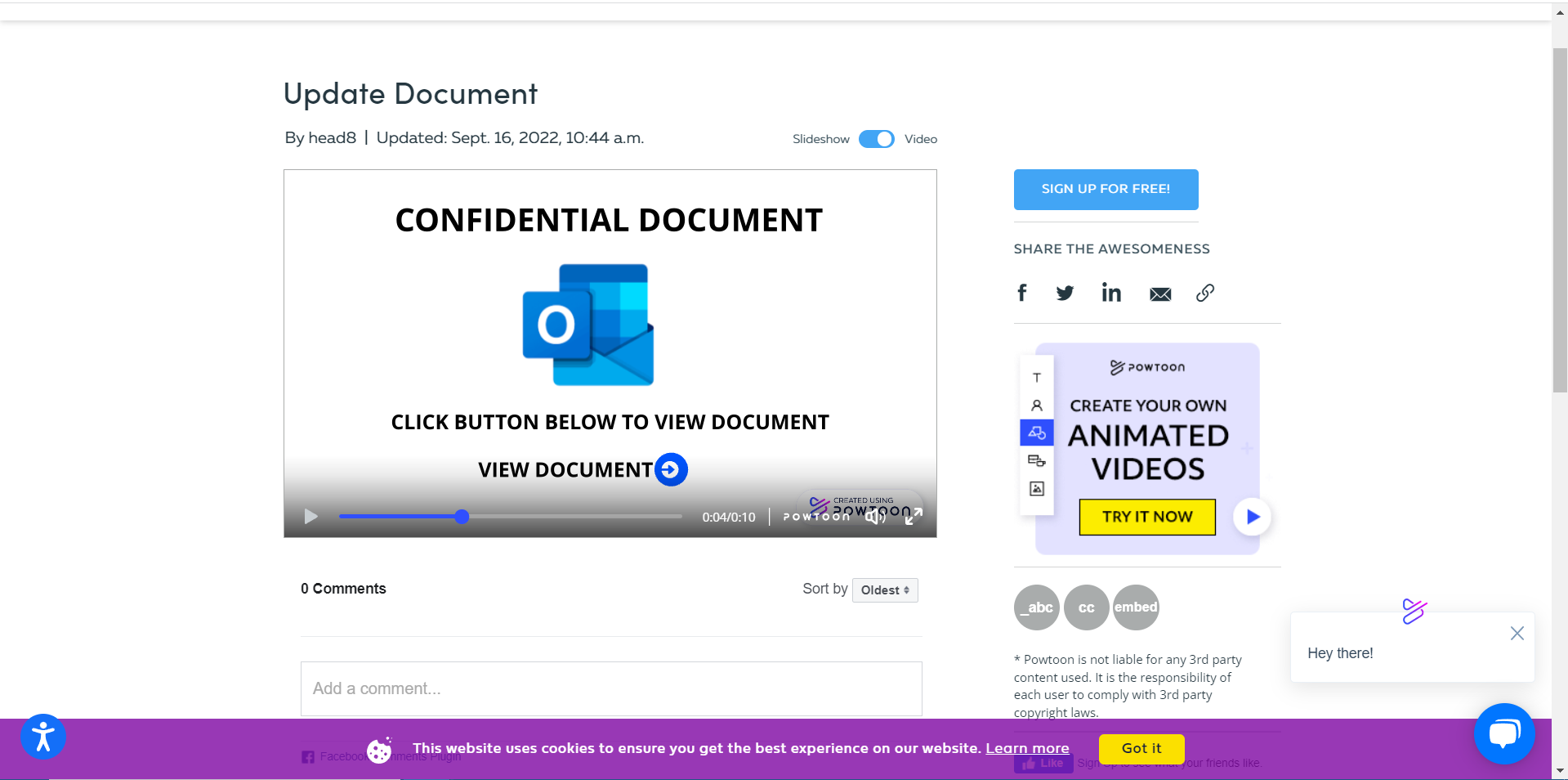
Figure 3: The Outlook logo in the video
- When the user click’s the second malicious payload (the malicious site that steals the users credentials) appears as an extremely accurate, spoofed Microsoft login page.
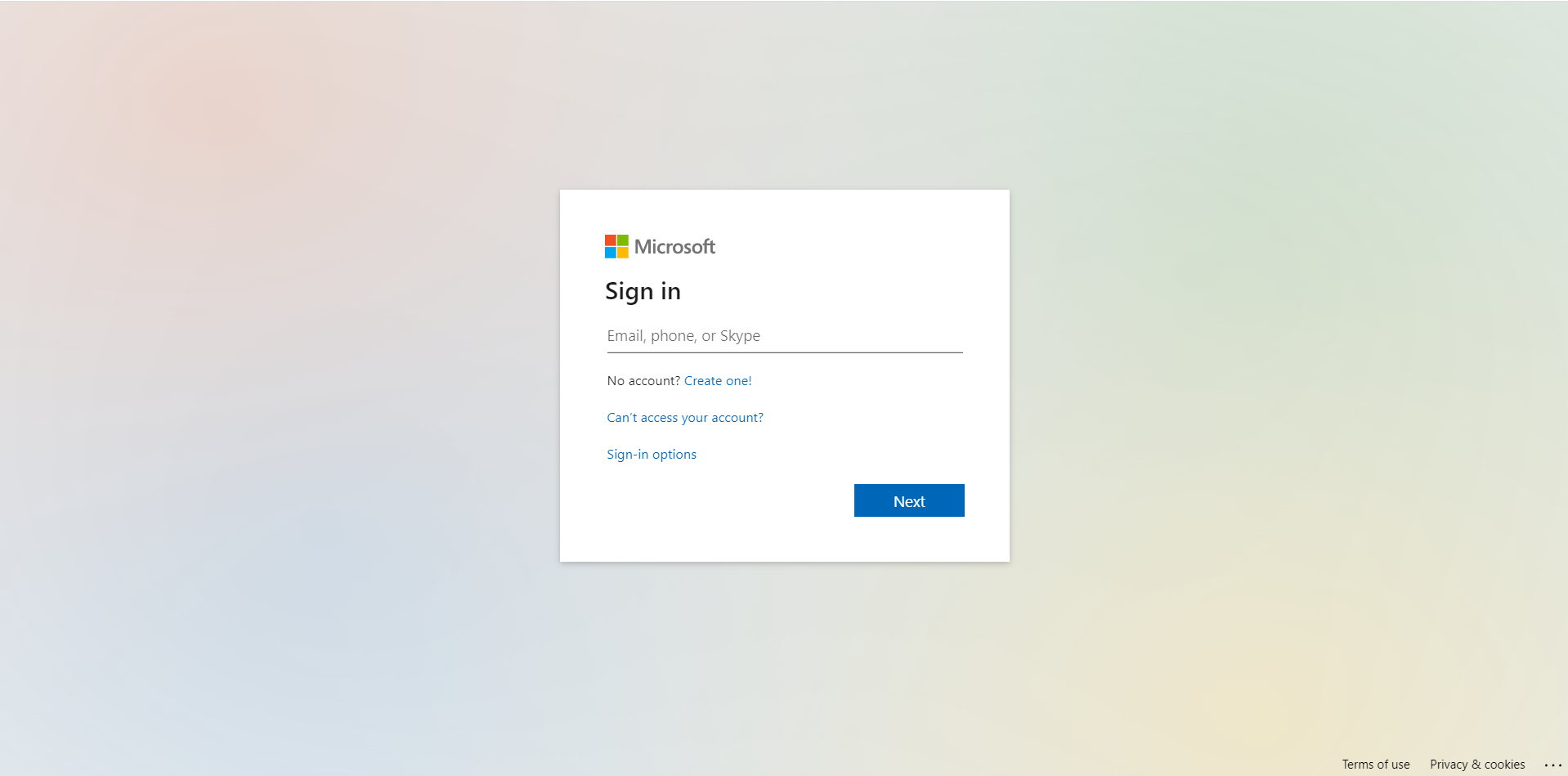
Figure 4: Spoofed Microsoft login page
- Perhaps most importantly, the sender of the email is an actual person whose account had been recently compromised and taken over. From our experience, 2-step phishing attacks usually come from actual email accounts that have been compromised.
It is clear that this an ATO because 1) the original email body contains the sender vendor’s signature and 2) it passes SPF and is sent from Microsoft.
Because 2-step phishing attacks are typically sent by compromised accounts makes this type of phishing attack all the more dangerous, especially if the recipient knows and trusts the sender.
The bottom line
This a highly sophisticated phishing attack that involves multiple steps, ATO, video and a phishing site. Due to a similar attack that had used video to deliver a payload, and was analyzed by our IR team, threat intelligence powered the system’s prevention of this attack from reaching the user’s inbox.
Remember: attackers leave patterns. Our platform has the ability to detect those patterns and implement new detection rules based on them very quickly. Typically, however, there isn’t a need to create new rules. Even when attackers sample a new technique (like using video as their payload), some part of the attack will contain a pattern our system already recognizes as malicious and knows how to prevent.
For more information regarding our advanced threat detection capabilities, contact us here.
Here’s some related content you may enjoy: How to Prevent Phishing























