Two-step phishing attacks have become a cornerstone of modern cybercrime, leveraging trusted legitimate platforms like DocuSign and SharePoint to deliver malicious content in layers to evade detection. In a recent twist, threats have begun exploiting Microsoft Visio files in two-step phishing campaigns. This analysis dives into how .vdsx files are increasingly weaponized in phishing attacks as a new evasion technique in the attacker’s arsenal.
What Are Microsoft Visio Files?
Microsoft Visio is a tool designed for creating and designing professional diagrams like flowcharts, network maps, and process charts, commonly saved in the .vsdx format. These files are widely used in business environments for visualizing complex data and workflows. In recent phishing campaigns, Visio files are being weaponized to deliver malicious URLs, creating a deceptive delivery point in a two-step attack path. Let’s break down how attackers are leveraging Visio files for phishing purposes.
A Surge in Visio-Based Credential Theft
Perception Point’s security researchers have observed a dramatic increase in two-step phishing attacks leveraging .vsdx files – a file extension rarely used in phishing campaigns until now. These attacks represent a sophistication of two-step phishing tactics, targeting hundreds of organizations worldwide with a new layer of deception designed to evade detection and exploit user trust.
Diagramming Danger: A Step-by-Step Breakdown of Visio Files Attacks
Phish Perfect – Compromised Email Accounts
The attack begins with threat actors leveraging breached email accounts to send out emails to their targets. Because the messages are sent from real accounts, they pass standard authentication checks like SPF further reinforcing their legitimacy in the eyes of both recipients and security systems. In some cases the attacker would add an .eml file (Outlook email message) as an attached to the message there they would plant the a URL.
The social engineering component of these campaigns often involves an important document like a business proposal or a Purchase Order (PO) that the recipient is instructed to view immediately.
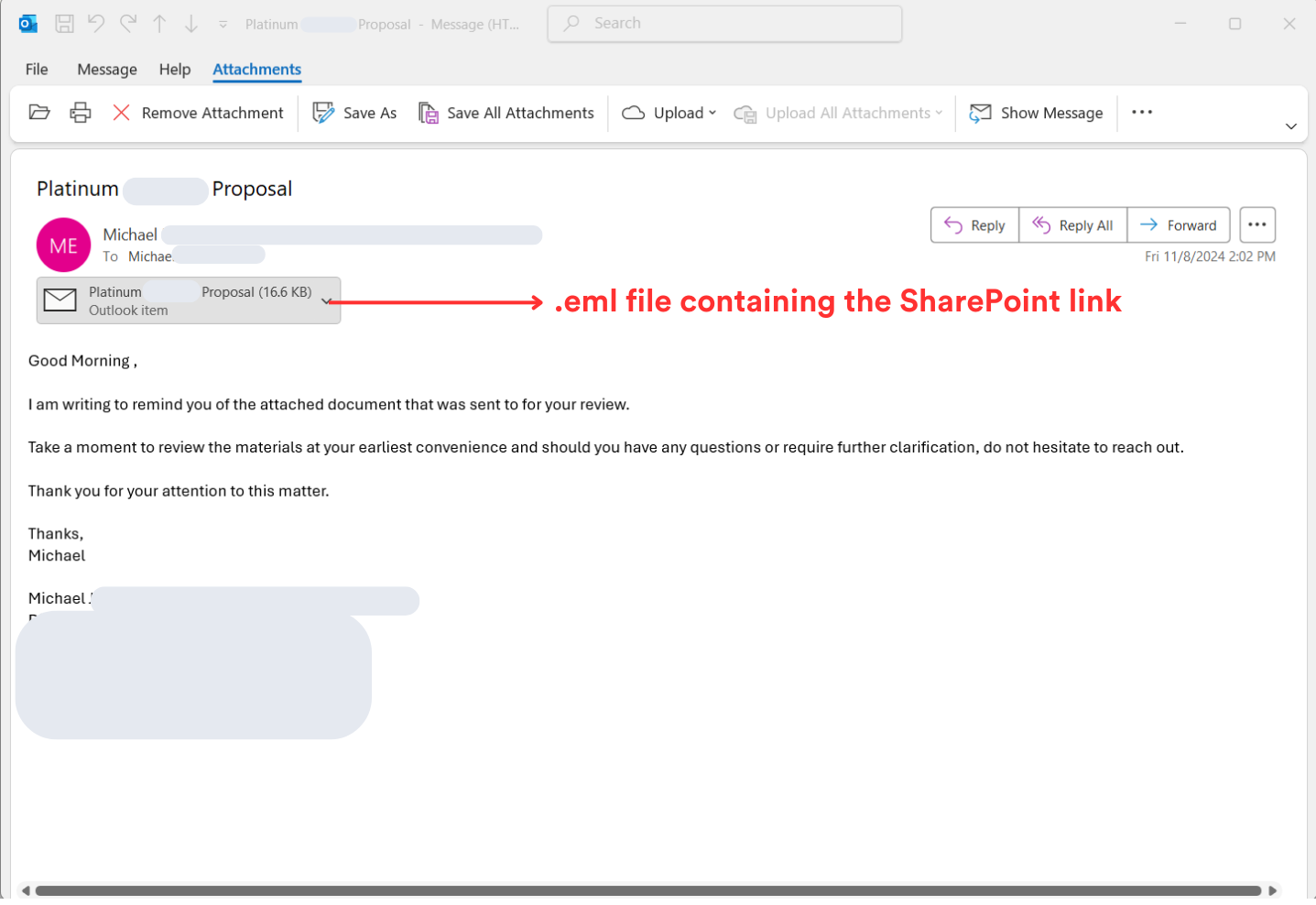
Attack Sample 1: A proposal email sent from a breached user with an .eml attachment
Attack Sample 1: The .eml file contains a URL leading to a SharePoint-hosted file
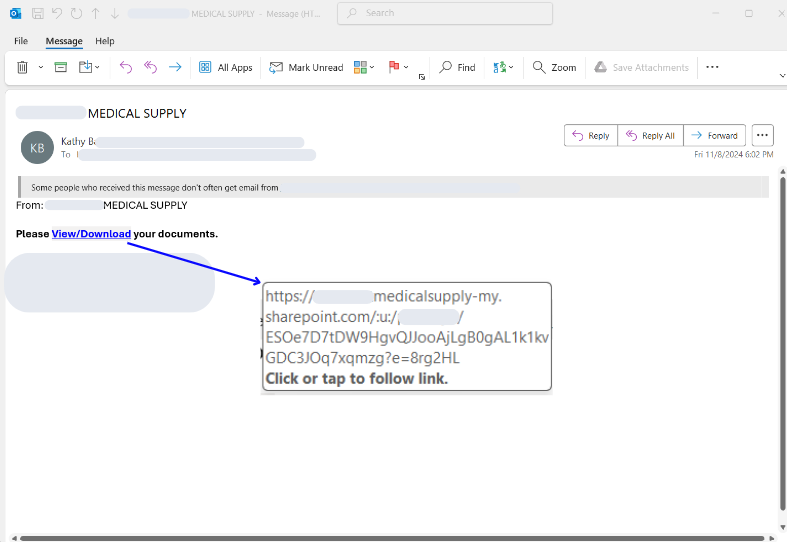
Attack Sample 2: SharePoint hosted “PO document’
A Clear Visio(n) for Deception – SharePoint-Hosted .vsdx File
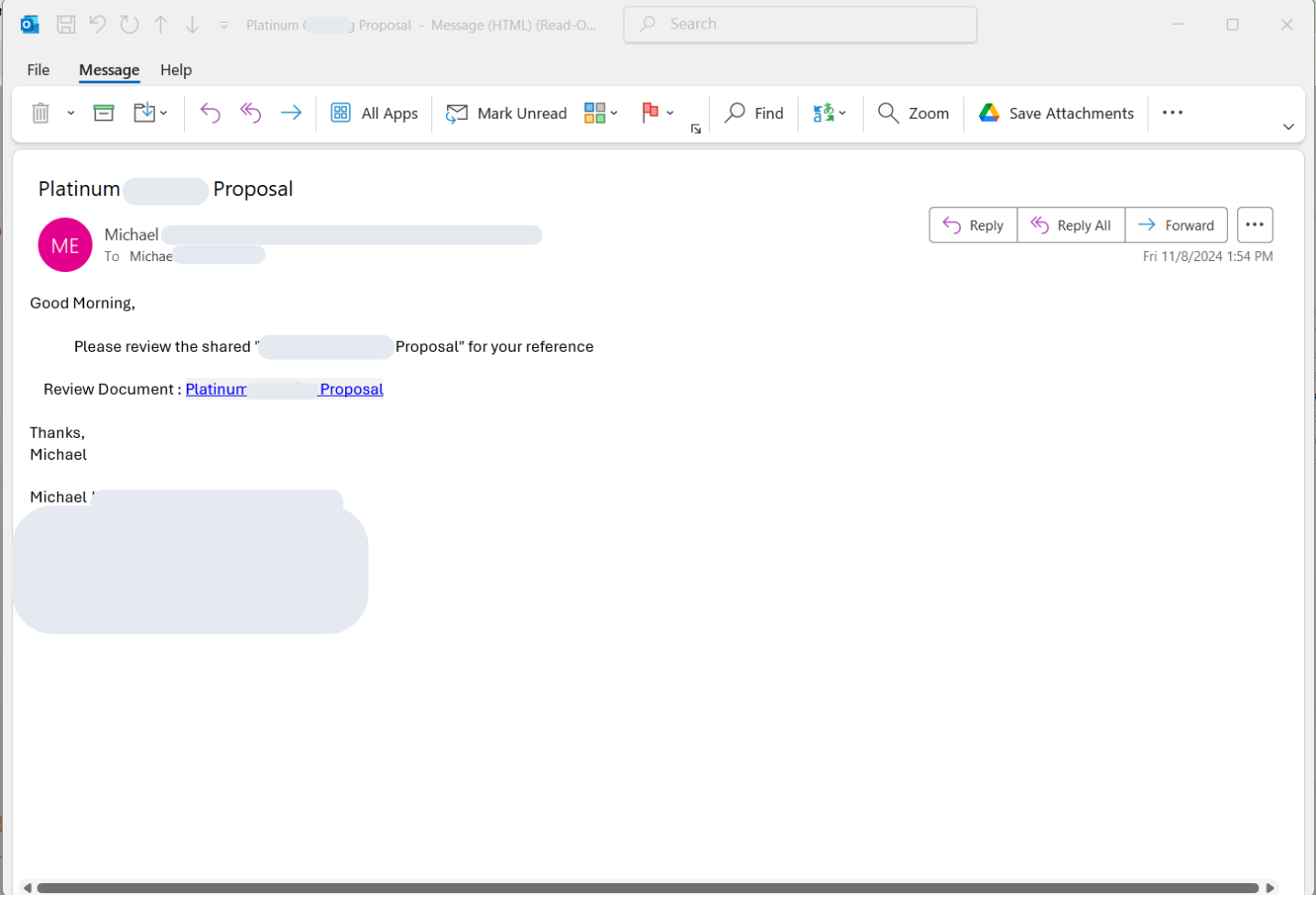
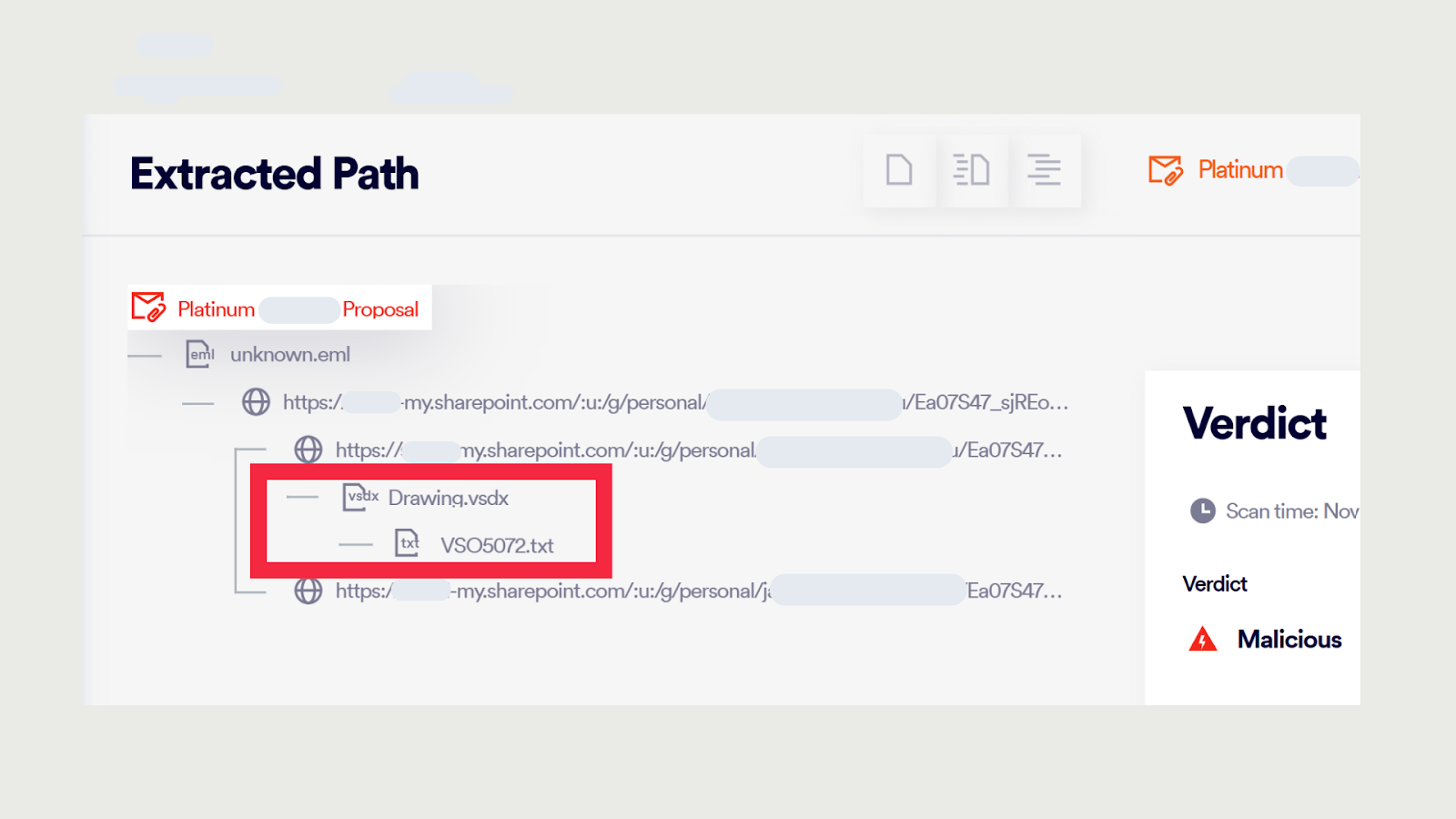
Clicking the provided URL in the email body or within the attached .eml file leads the victim to a Microsoft SharePoint page hosting a Visio (.vsdx) file. The SharePoint account used to uploading and hosting the .vdsx files is often compromised as well.
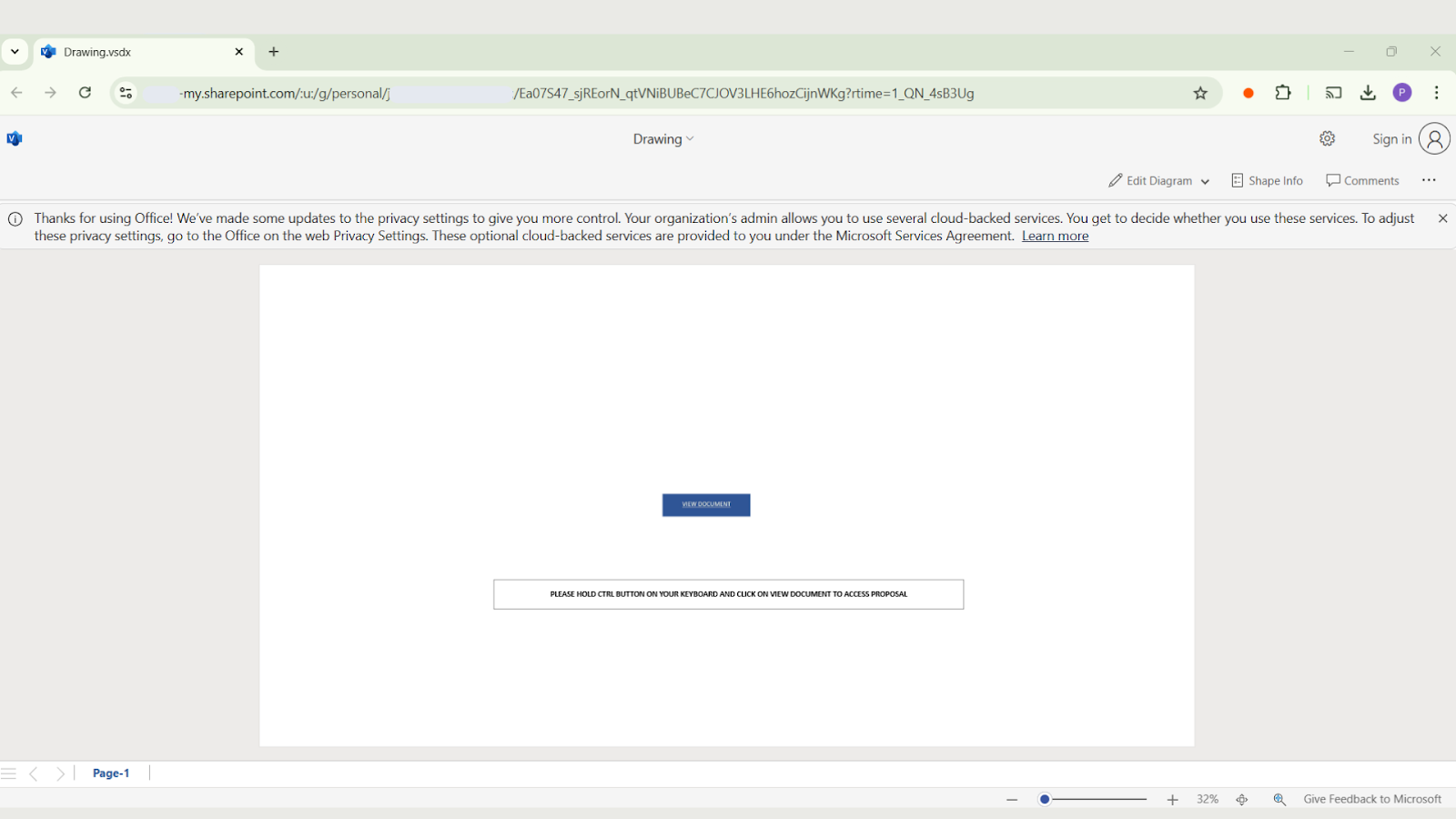
Attack Sample 1: Clicking the “View Document” while holding the Ctrl button lead to the malicious payload
Inside the Visio file, attackers embed another URL behind a clickable Call-To-Action, in most cases we’ve observed it was a “View Document” button. These files vary in appearance, with some even incorporating the breached user organization’s logos and branding to enhance credibility.
To access the embedded URL, victims are instructed to hold down the Ctrl key and click – a subtle yet highly effective action designed to evade email security scanners and automated detection tools.
Asking for the Ctrl key press input relies on a simple interaction that a human user can perform, effectively bypassing automated systems that are not designed to replicate such behaviors.
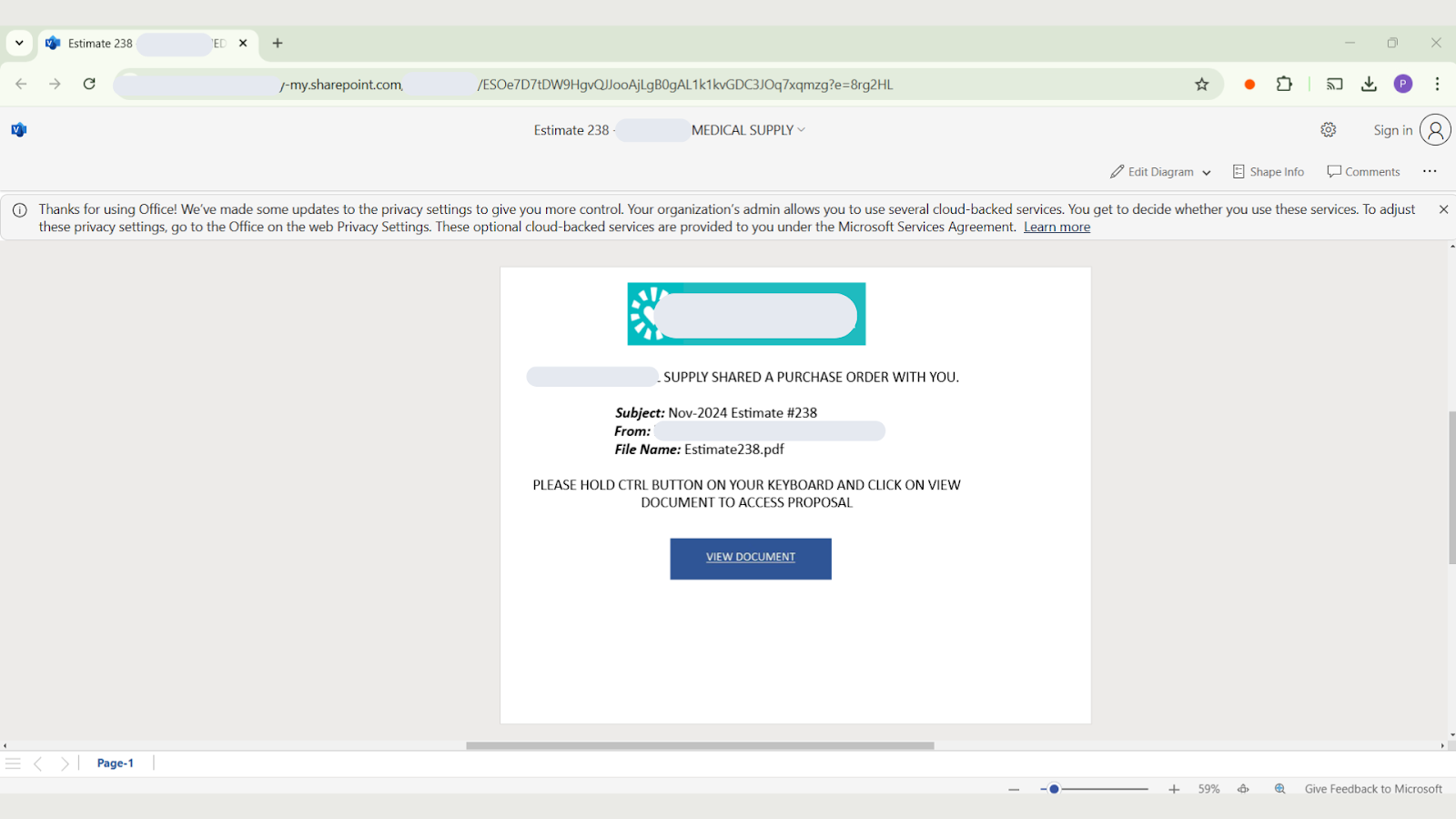
Attack Sample 2: “PLEASE HOLD CTRL BUTTON ON YOUR KEYBOARD AND CLICK ON VIEW DOCUMENT TO ACCESS PROPOSAL”
Losing Ctrl – Redirected to a Phishing Page
Interacting with the link on the Visio file redirects the victim to a fake Microsoft login page, crafted to mimic the legitimate Microsoft 365 portal and steal the target’s credentials.
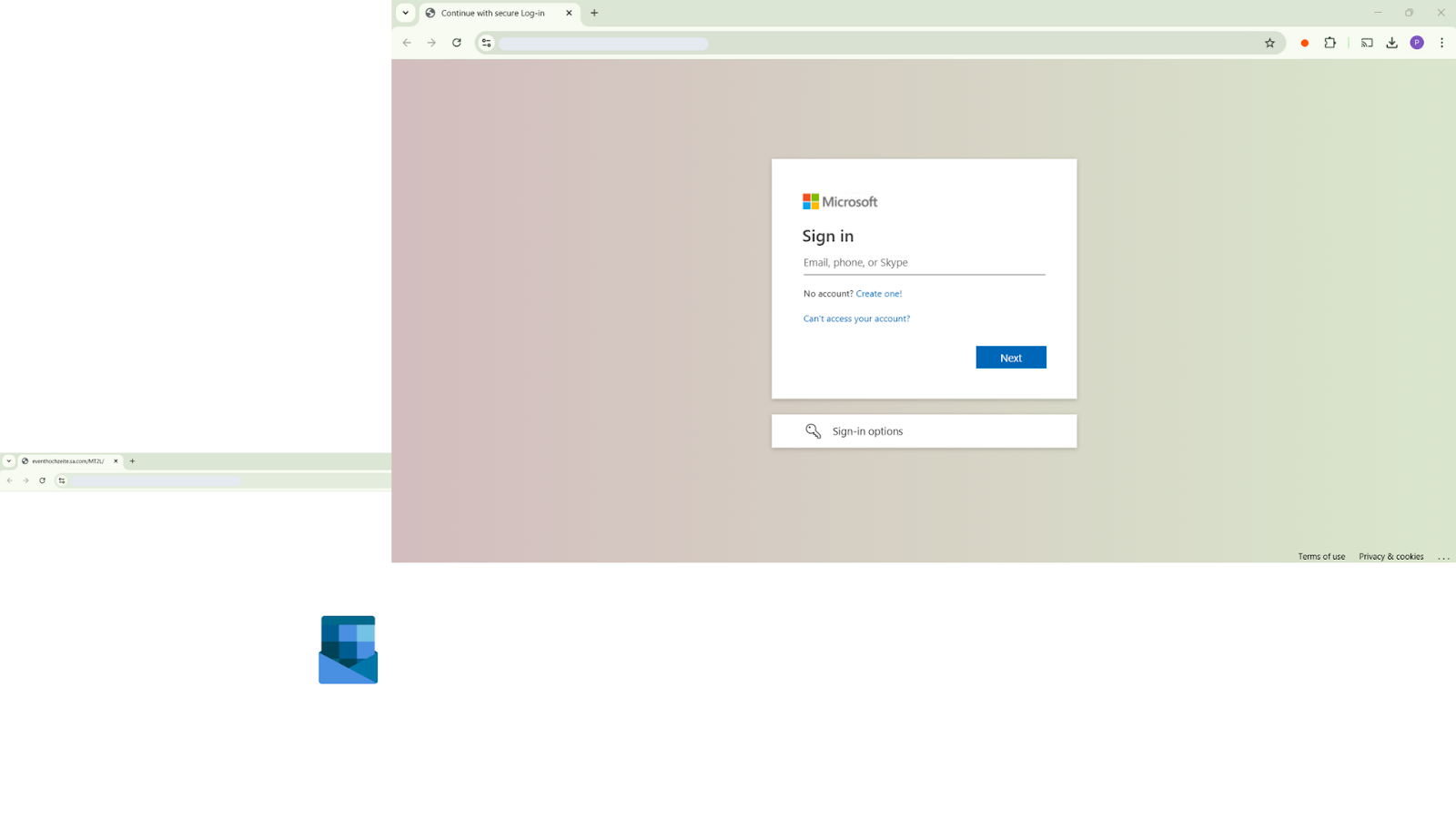
Attack Sample 1+2: the first malicious payload – a phishing page impersonating Microsoft 365
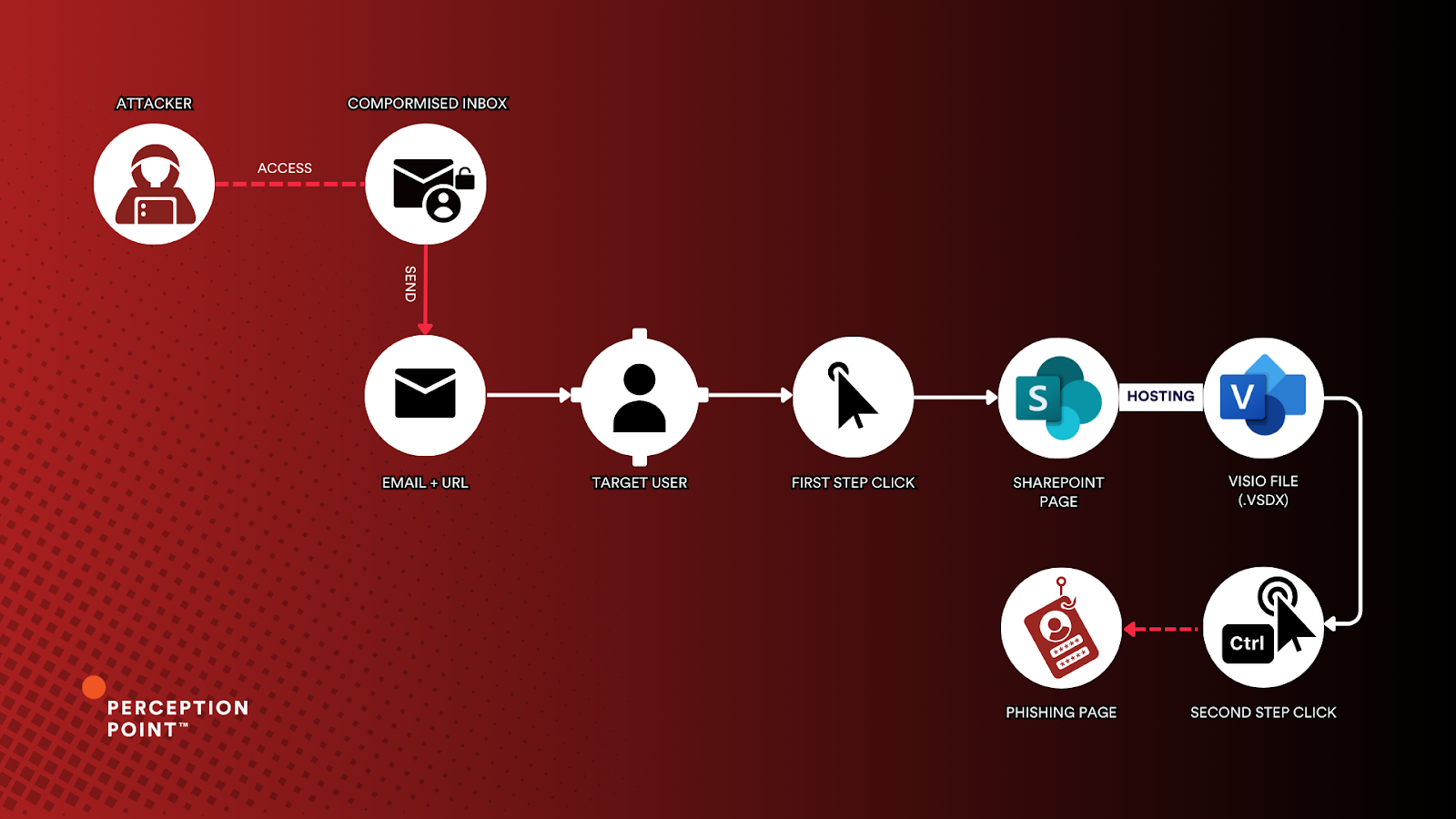
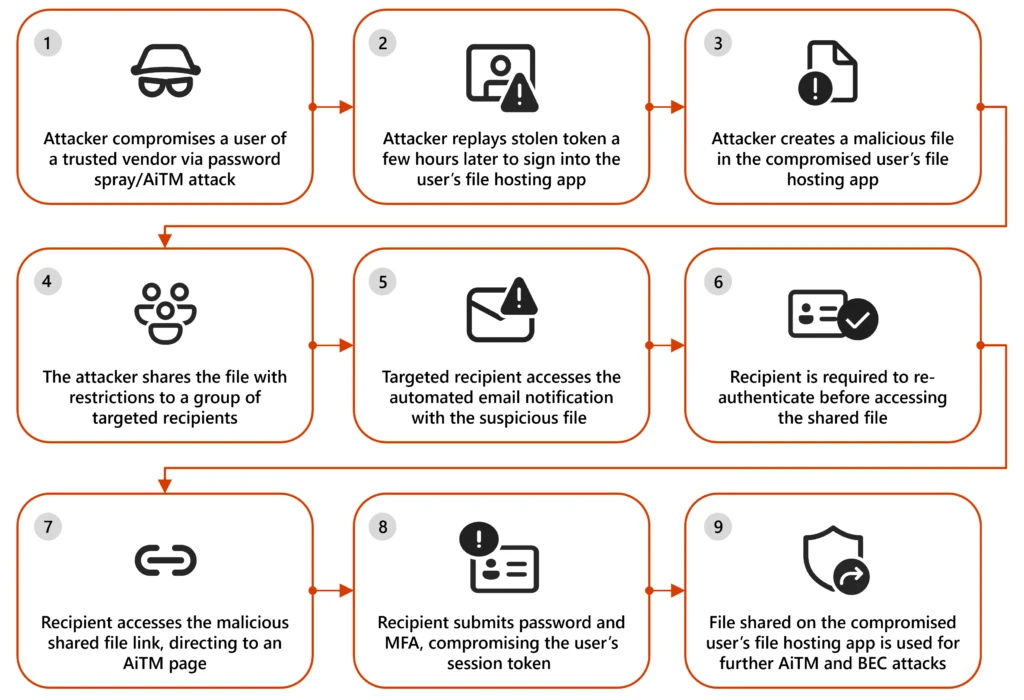
Breaking down the two-step phishing attack leveraging a malicious Visio file source:Perception Point X-Ray
A New Standard in Phishing?
Microsoft’s recent acknowledgment of the misuse of their services in phishing campaigns underscores a worrying trend: two-step phishing attacks leveraging trusted platforms and file formats like SharePoint and Visio are becoming increasingly common. These multi-layered evasion tactics exploit user trust in familiar tools while evading detection by standard email security platforms.
Source: Microsoft Threat Intelligence
At Perception Point, we’re committed to staying at least one step ahead. Our advanced detection technologies, including Dynamic URL Analysis and Object Detection Models, are designed to uncover and neutralize complex threats like two-step phishing. Whether it’s a cleverly disguised Visio file or the next evolution of phishing like QR codes, we provide real-time threat prevention to keep organizations safe.
Ready to secure your organization? Contact us today to learn more.























