Overview.
Phishing is still one of the most common types of cyberattacks. By leveraging social engineering techniques, high-quality disguises, advanced mapping of targets, and a wide array of evasion techniques, attackers have been able to lure end-users into giving away PPI and their own credentials, resulting in severe damage to organizations across all sizes and industries.
In this blog, we chose to focus on the brands that are highly used in phishing campaigns. On top of mapping the most abused brands, we uncovered an interesting statistic on the importance of protecting not just prominent brands or your own – but the ones related to your stakeholders.
The findings of this short analysis can (and should) be translated to actions by CISOs. We summarized some key recommendations for you to start with, in the end of this article.
Most phished brands and industries.
Perception Point’s Incident Response team has mapped the most phished brands and industries – i.e. the brands used most by attackers in their phishing schemes to trick end-users.
Based on Perception Point’s information, the most “phished” brand in the world is Microsoft. Following this Tech giant are DHL, Google, LinkedIn, Zoom, WeTransfer, and PayPal. The Top-10 list ends with Netflix, Facebook, and Maersk, the shipping enterprise.

Analysis of the entire dataset of phishing attacks targeting Perception Point’s clients in the last 90 days revealed that the most phished industry is Tech & Collaboration which includes known brands, such as Microsoft, Amazon, Zoom, and Skype. It is followed by the Telecom, Shipping & Deliveries, and Finance verticals.
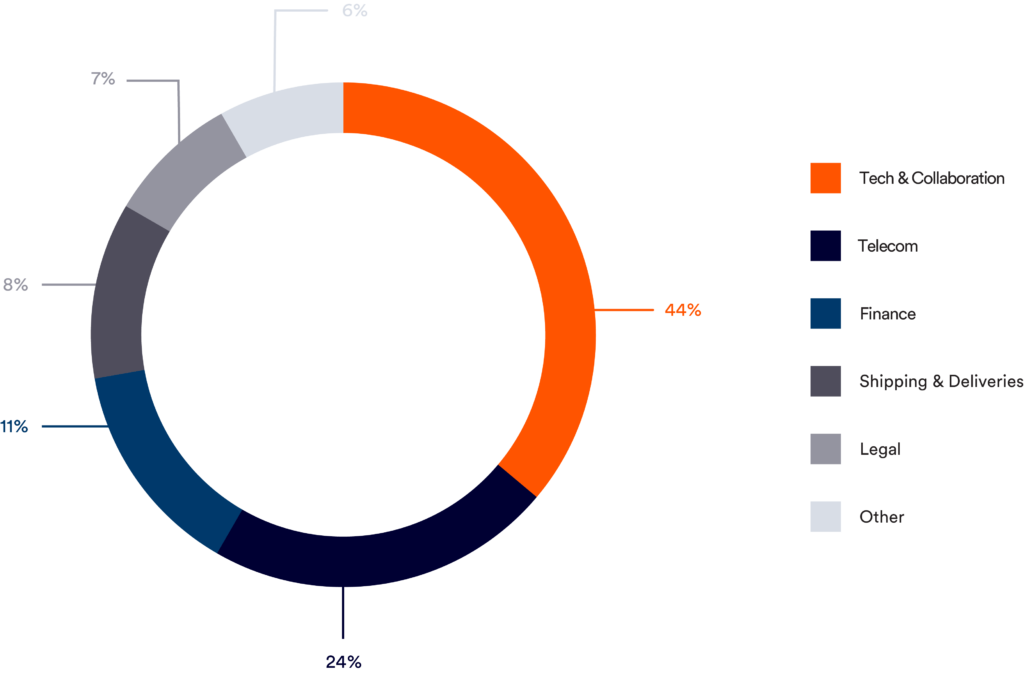
Another interesting segment is the use of Social Networks as their attack’s brands. We see a steady rise in the malicious use of Facebook and LinkedIn login pages to steal credentials (both are in the Top-10 most phished brands as shown above).

“Commodity” vs. Assets-based phishing.
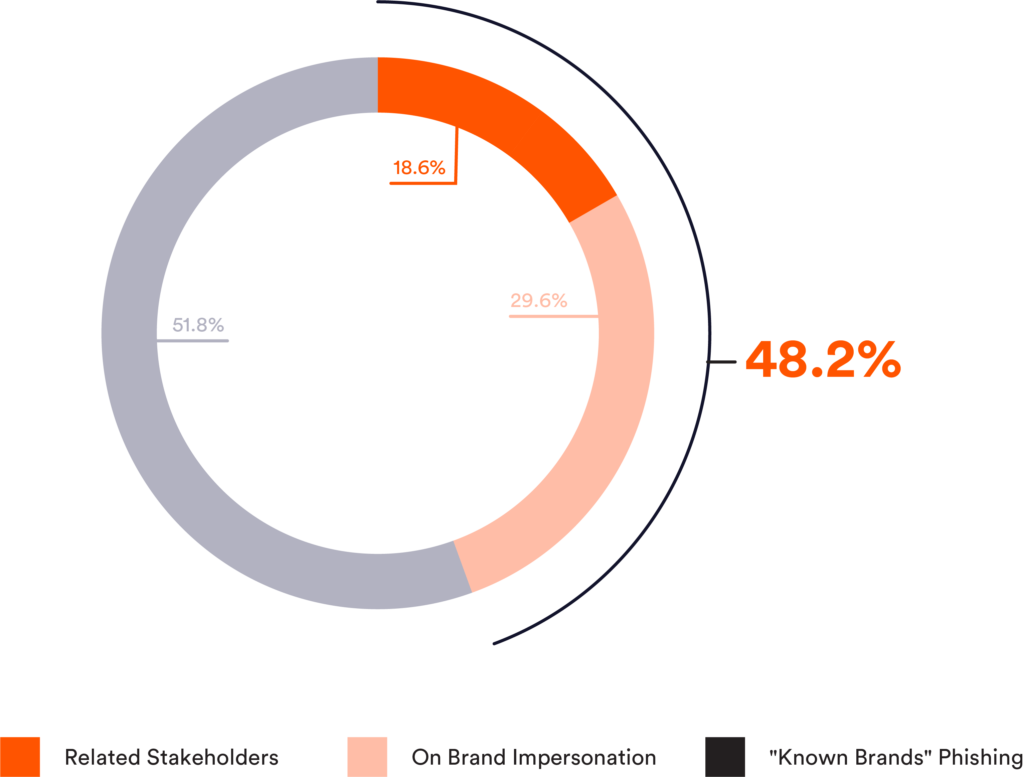
Perception Point has collected the information regarding each and every phishing attack that targeted our clients and mapped the brand that was used for each incident. These were then categorized into 3 groups:
- Known brands – prominent, common brands known in every household. For email security vendors, these brands are “commodity” brands (although they can be used in advanced attacks).
- Own-brand impersonation – using the brand of the targeted company against itself – i.e. using “ACME” logo to attack the “ACME” employees.
- Related Stakeholders – using brands of stakeholders related to the targeted company against it. These can include customers, suppliers, partners, and other organizations that work closely with the employees of the targeted company.
The results below show that protecting against known brands, is simply not enough. Almost 50% of attacks are actually using the company’s brand or the brands of its stakeholders to try and phish their end-users for information. This can vary between login pages, credit card inputs, or direct emails with malicious links.
Recommendations.
- Ensure your email security solution has the ability to learn your traffic and offer asset-based anti-phishing technologies. You can’t rely on solutions that excel in preventing “well-known” brands.
- Deploy solutions with BEC protection. Stats show that many phishing attacks can be prevented by utilizing strong anti-payload less algorithms
- Invest in security awareness solutions and create protocols that test both popular phished brands as well as the brands of your company and its stakeholders. A good vendor would be Wizer, but you can choose any of the leading ones out there.
- Test your email solutions regularly. Attackers constantly evolve and improve. Engage with pen-testing companies that stay up to date with the latest attack trends and use them to ensure your email security solutions can prevent phishing attacks that are using your company’s brand or assets.
Our Angle.
Perception Point’s service provides 360-degree next-gen phishing protection. On top of advanced algorithms uncovering advanced phishing attacks that leverage known brands, the platform includes unique algorithms that learn the traffic of the protected customer to provide protection for both own-brand impersonation and related stakeholders. This means that each customer benefits from complete customer-based, asset-based protection on top of the day-to-day phishing protection it needs.

Here’s some related content you may enjoy: How to Prevent Phishing
























