Over the past few months, one of the top concerns for our customers has been Account Takeover (ATO). Just as its name implies, ATO is when an attacker gains access to your email or cloud collaboration application via stolen credentials. What is most alarming about ATO is that there are no telltale signs to look out for if your organization has been breached.
Recently, our Advanced Threat Detection platform detected a trend of attempted ATO attacks that, like most ATO attacks, originate from phishing emails. Analyzed by the cybersecurity experts from our Incident Response team, some of our customers have received phishing emails from seemingly legitimate vendors. Upon further look, it is clear that the vendors had undergone ATO attacks in which their email accounts were compromised. Also called Vendor Email Compromise (VEC), attackers are able to amplify the harm of one ATO by leveraging a vendor’s trusted contact list. In this post, we detail a few different phishing attempts that were sent from vendor’s email accounts that had been taken over.
As per my last email, please don’t click the link!
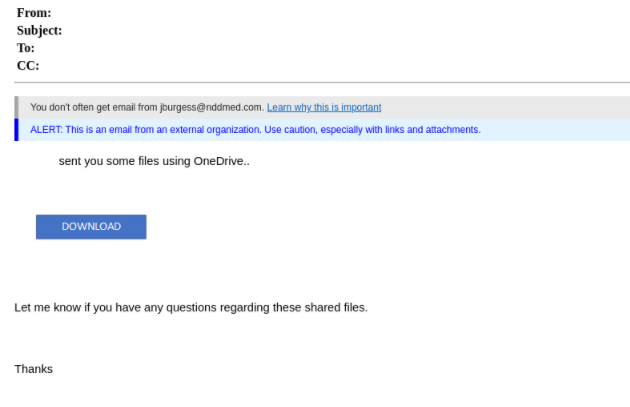
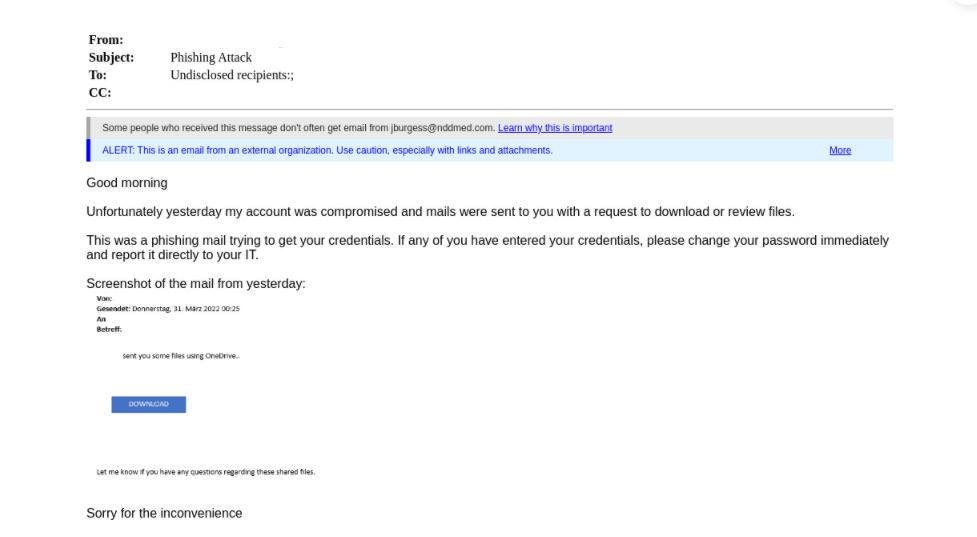
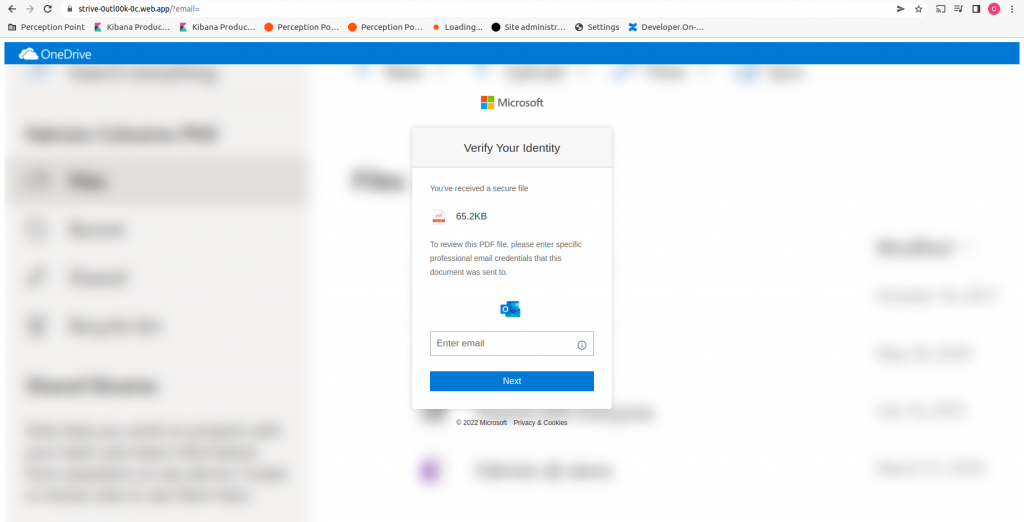
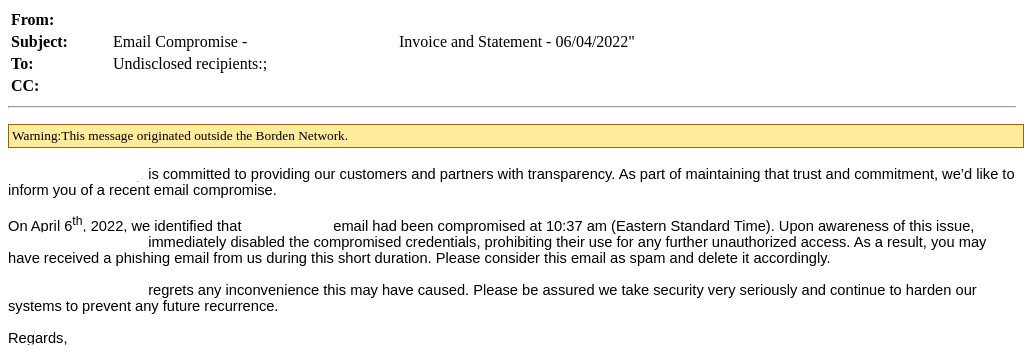
In this first attack, one of our customers received a malicious email from a vendor that had their email account taken over. The attacker posed as the vendor and sent our customer a message impersonating Microsoft OneDrive with the goal to obtain email credentials. Hours later, the same vendor sent a follow-up email, explaining that his account was hacked.
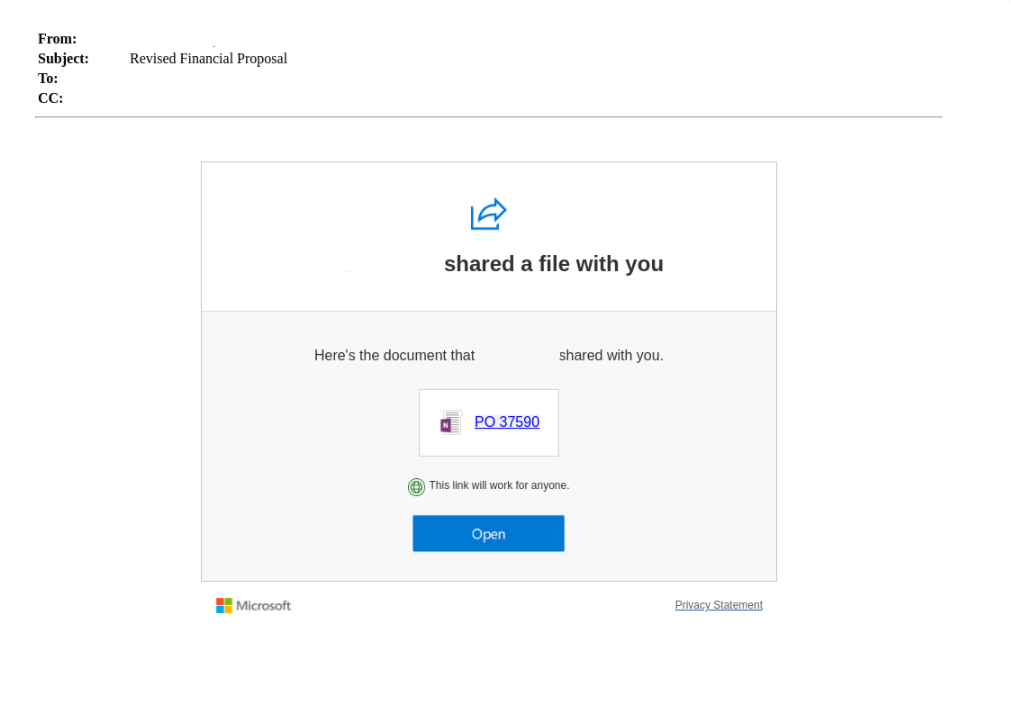

What stands out about this attack is the layered method. By first taking over the vendor’s account, the malicious message was legitimized, as it came from a known and trusted source. Had our Advanced Threat Detection platform not prevented the email from entering our customer’s inbox, they could have easily fallen for this phishing scam, subsequently continuing the chain of ATO, followed by more phishing attempts and potential breaches of additional accounts.
Please find my hacked email attached
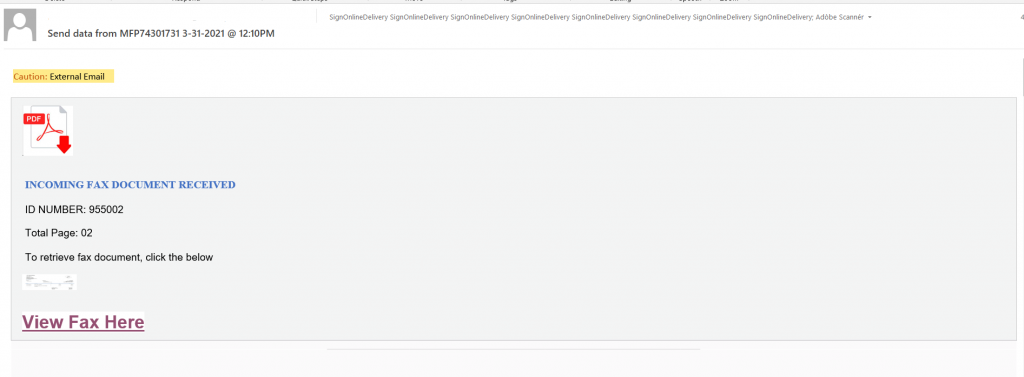
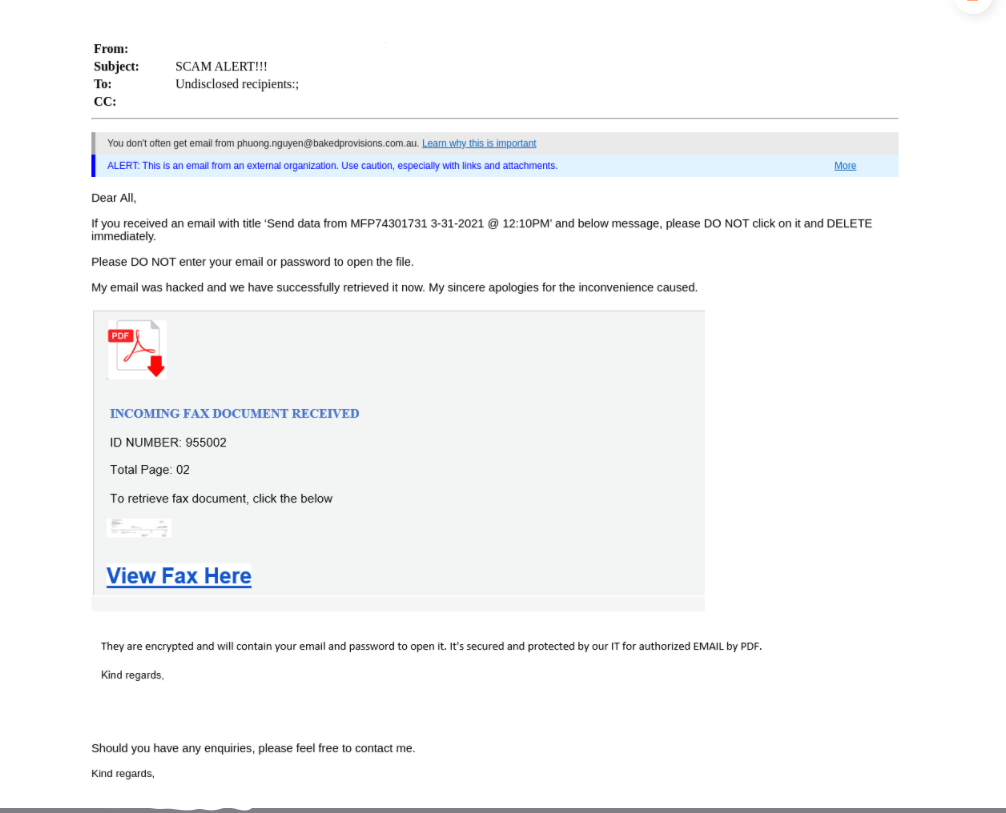
This next example of ATO involves a known vendor that works with two of our customers. The compromised “vendor” sent a malicious email to our customers that resulted in a 2-step phishing campaign, meaning that they were redirected twice before being asked to enter their credentials.
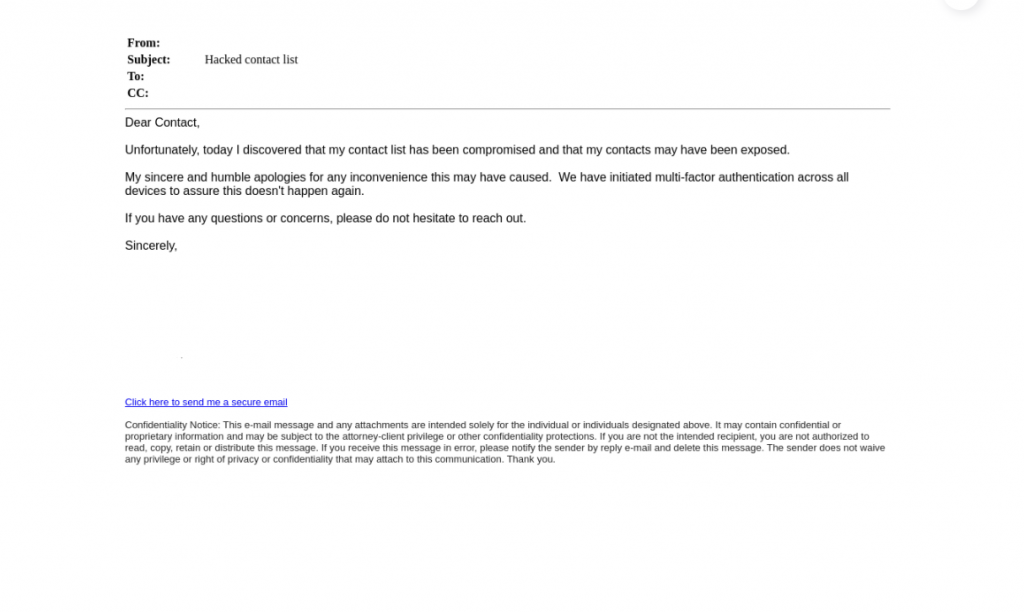
Two hours after sending the phishing email, the actual vendor followed up with his recipients and instructed them not to open his previous emails, as he had experienced ATO.

I look forward to ending this ATO soon
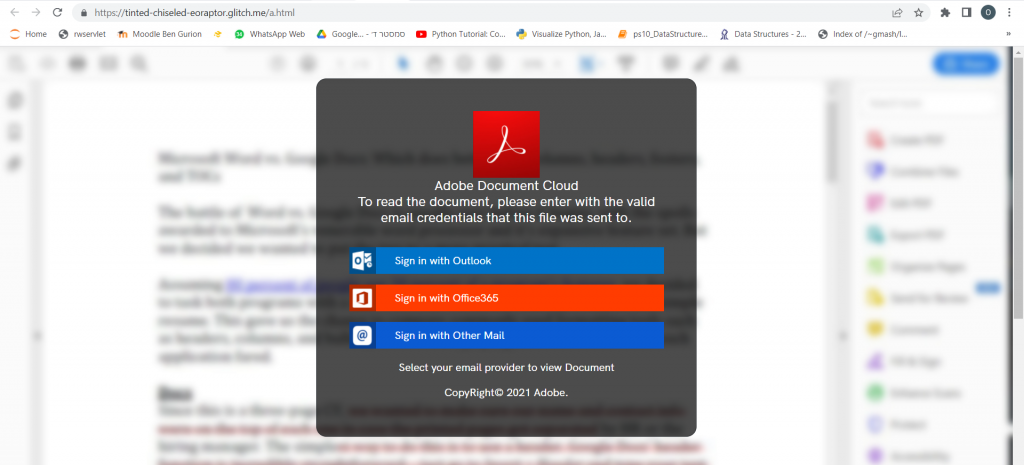
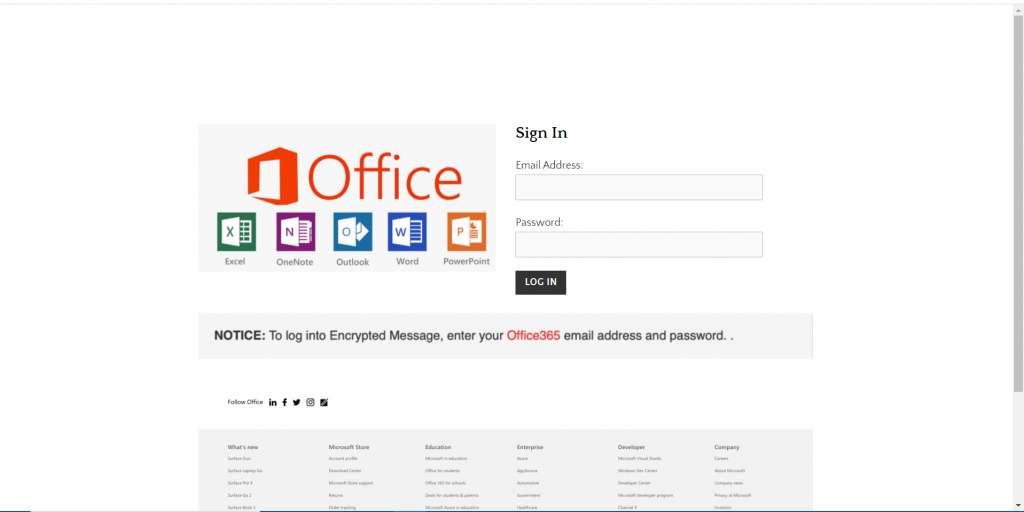
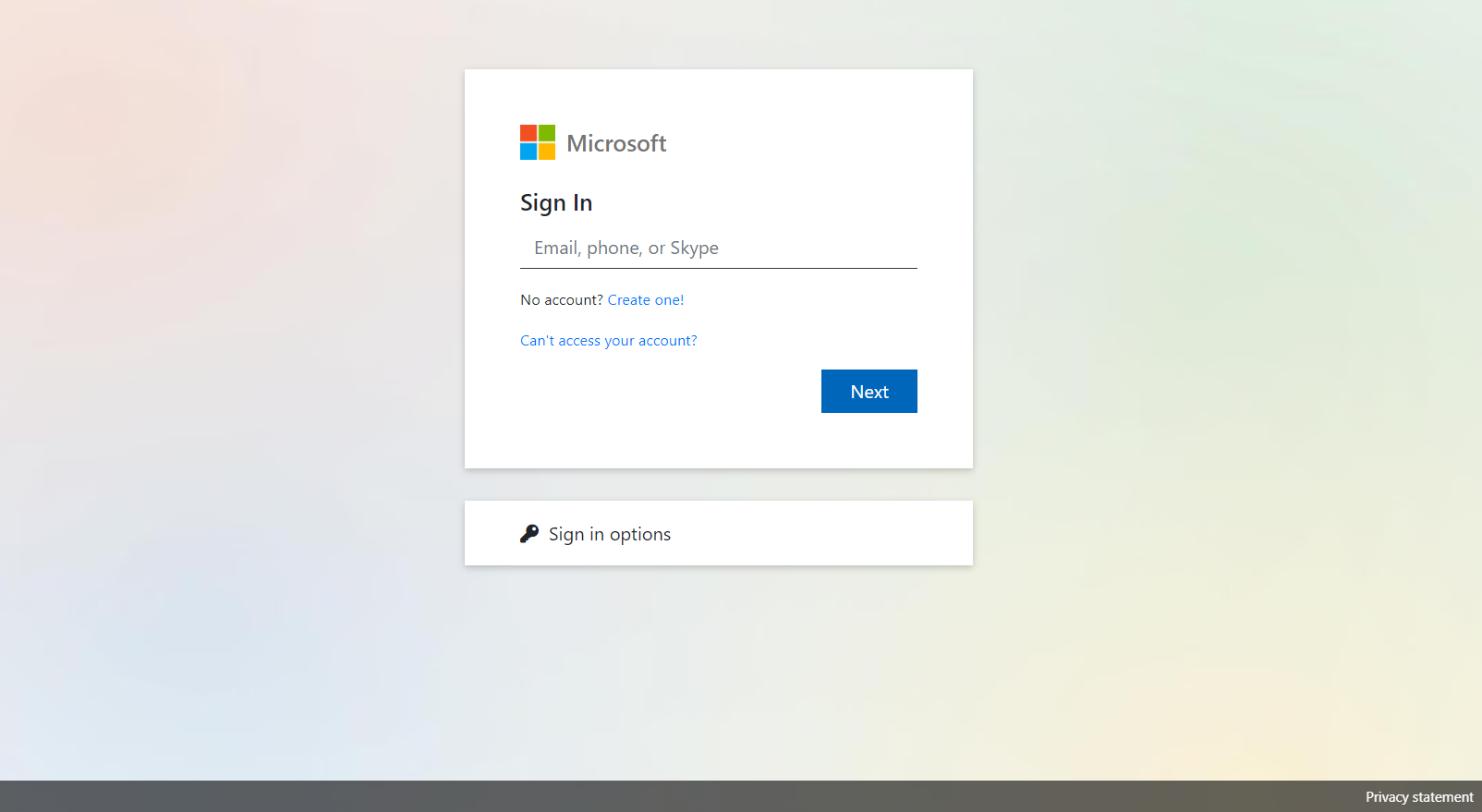
In this VEC, an attacker spoofs the Microsoft 365 login page. Similarly to the previous attack, this is an example of when attackers leverage redirection for phishing attacks. Here, the attacker nestles one link inside another to further conceal the true intent of the attack: gaining user credentials.
These types of phishing campaigns are difficult to detect by themselves, so what is impressive about this incident is that our technology was able to catch the phishing attempt despite coming from a “trusted” source.
I can’t seem to Excel at this
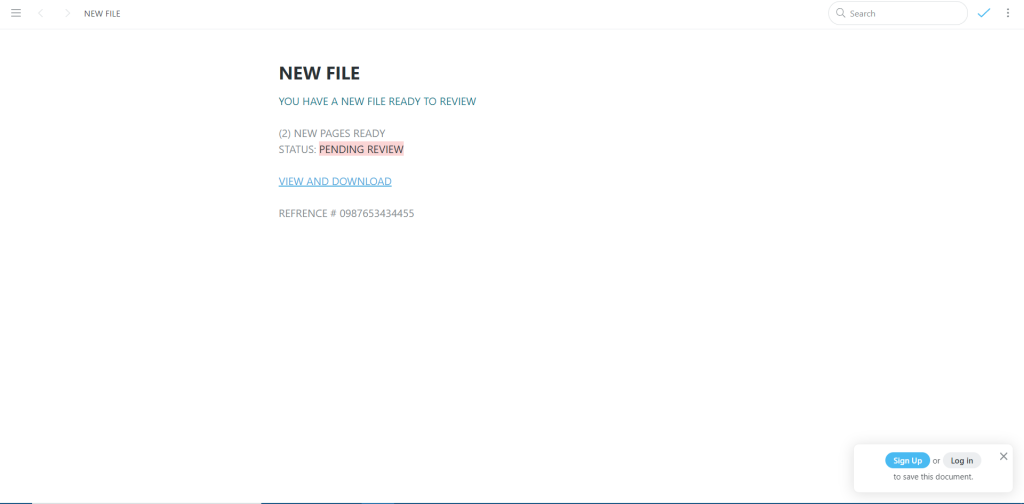
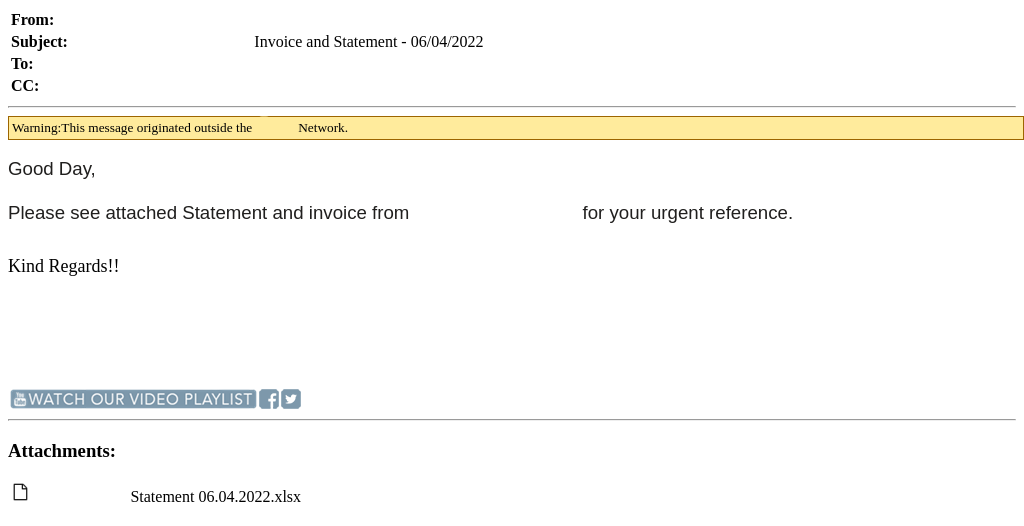
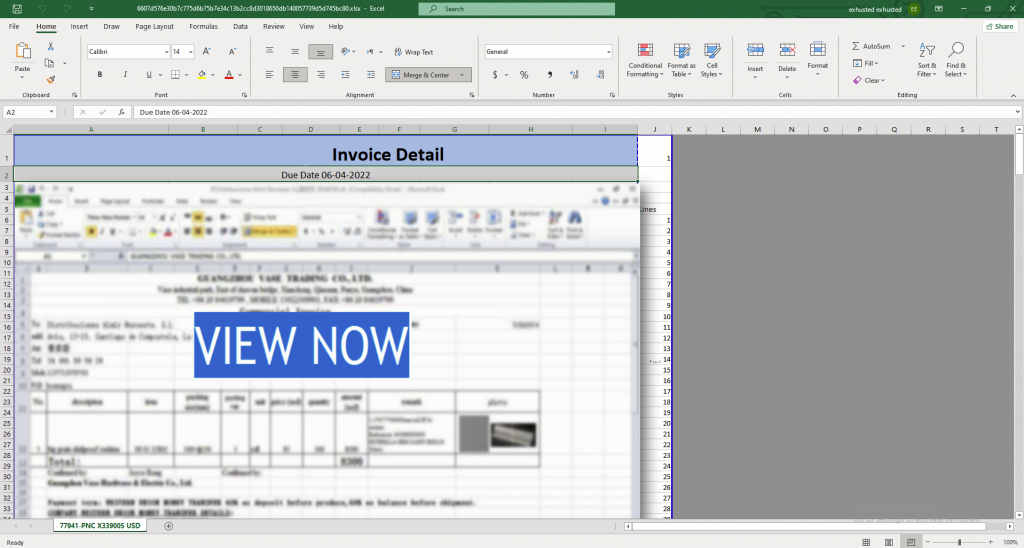
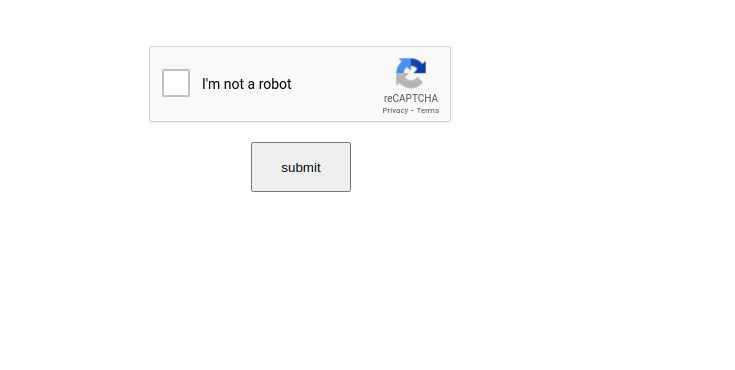
Last but not least we have a VEC-spurred phishing attempt that should seem pretty standard at this point in the blog post. Our client received an email from a trusted vendor, whose account has been compromised. The “vendor” sent an “urgent” invoice, prompting the recipient to open a fake Excel document. After clicking on the document, the user is directed to a phishing website.
What stands out about this website is that it presents a reCAPTCHA to the user before leading to a login page. This aims to provide the user with a sense of security before they enter their credentials; it also engages the user to further interact with the page. This is a technique designed to evade email security solutions by first presenting a reCAPTCHA as opposed to the true phishing site. What is unique here is that our advanced threat detection technology has the ability to recognize the evasion technique and detect that the site is malicious.
The cycle concludes like most: recipients obtain a follow-up email from an individual in the vendor’s organization, apologizing and urging users not to engage with links sent in the malicious email.
Detection is difficult
Throughout these examples, one thing is clear: detection is difficult. While it is challenging enough for an endpoint user to identify most malicious messages, it is nearly impossible for the user to determine if a message is malicious when it is sent from a trusted source, like in these VEC examples. ATO is unfortunate and damaging to the individual targeted, but that harm only amplifies when an attacker leverages their successful ATO to gain access to additional accounts, across multiple organizations.
If you’re interested in learning more about how ATO occurs and ways to prevent it, please refer to our ATO resources here.























