Two-step phishing attacks are rapidly evolving, exploiting the trust users place in legitimate services to deliver malicious payloads via email. In recent research, the Perception Point team uncovered a new wave of attacks abusing DocuSign’s Web Forms—a feature designed for data collection and document management. These attacks represent yet another escalation in sophistication and volume, exploiting user trust and legitimate domains.
What Is DocuSign Web Forms?
DocuSign Web Forms is a feature available to Enterprise Pro and Business Pro users, enabling the creation of customizable, mobile-friendly forms. Users can input information into predesigned templates, which seamlessly integrate into documents for electronic signing. This no-code solution is intuitive and offers flexibility through multiple pages, embedded links, and custom buttons.
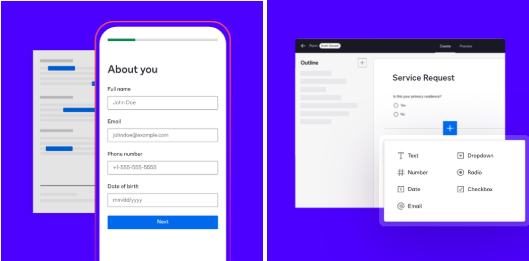
While these features enhance productivity, they also make Web Forms a prime candidate for abuse. Threat actors have turned this convenience into a tool for highly deceptive phishing campaigns.
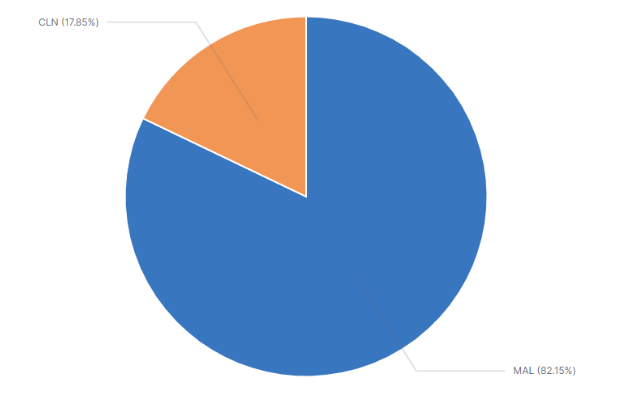
In the past month, the forms feature has been observed being abused about 4 times more than it was observed being used legitimately.
The Two-Step Phishing Campaign
Step 1: Luring the Target
The attack begins with compromised accounts sending emails to targets. By using real email accounts, the messages easily bypass standard authentication checks such as SPF and DKIM.
Attackers leverage social engineering, crafting emails with urgent language to prompt users into clicking on links. Common examples include: “You’ve received a confidentiality agreement requiring your signature.” or “Important: New invoice available for review and signature.”
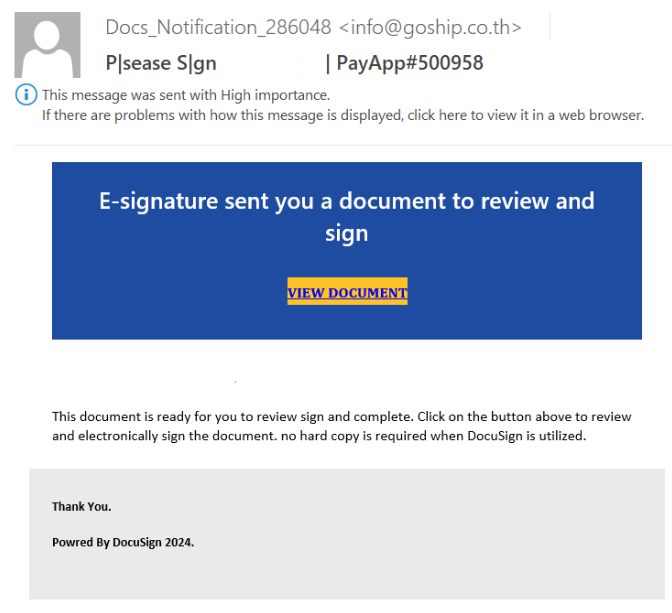
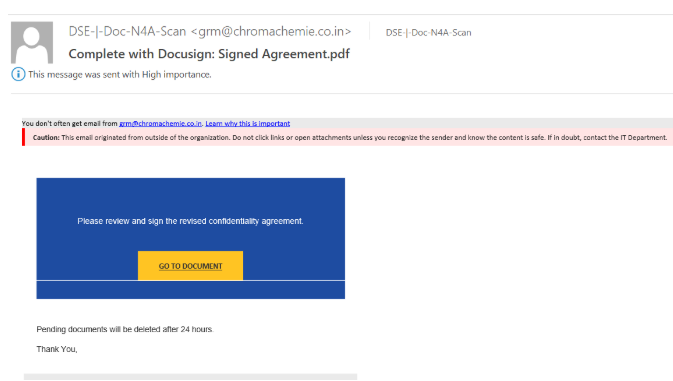
These emails appear to originate from legitimate DocuSign accounts, further deceiving recipients and bypassing traditional security filters.
Step 2: The Form
Targets are directed to a DocuSign Web Form hosted on DocuSign’s official site.
The form uses social engineering tactics to maintain legitimacy, with each page tailored to appear unique. This variability not only enhances believability but also evades detection by security systems that rely on pattern recognition.
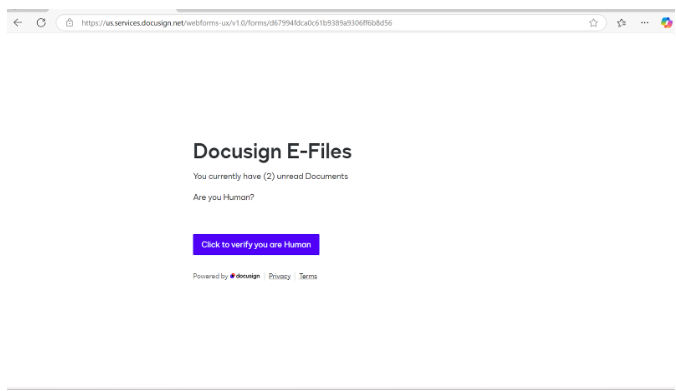
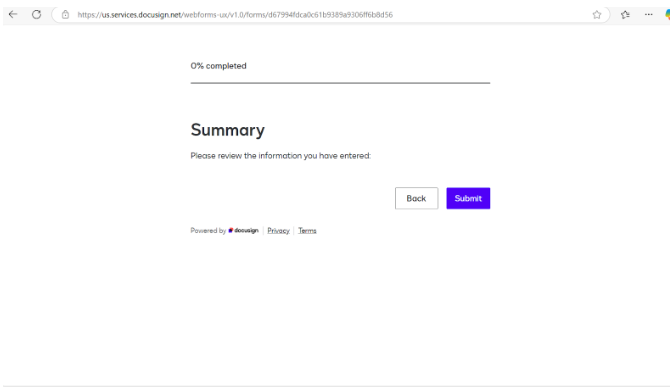
On the final page of the form—typically labeled “Thank You” – a button promises to allow users to access their document. This button mirrors earlier ones in the form, maintaining the façade of legitimacy.
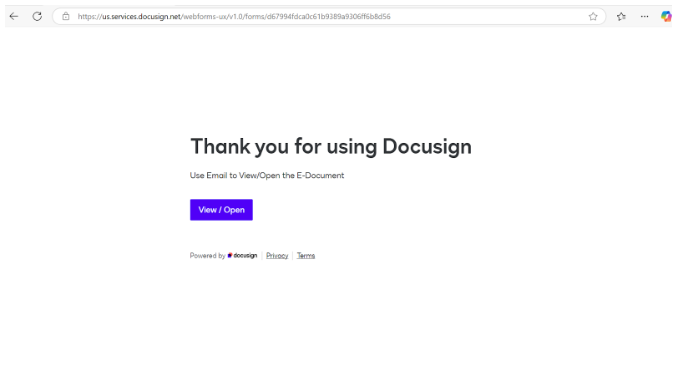
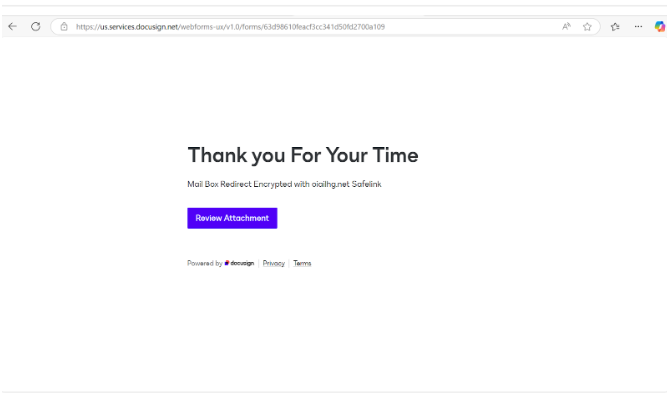
The Payload
Clicking the final button redirects targets to a phishing page mimicking Microsoft’s 365 login portal. This page is designed to steal user credentials, often using dynamic elements to reflect the branding of the target’s organization for additional authenticity.
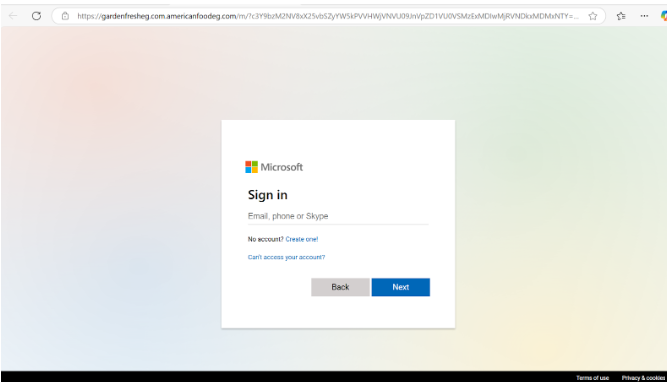
Why This Attack Is Effective
- Legitimate Service Abuse: The use of DocuSign’s official platform ensures high trust and bypasses many automated security measures.
- Dynamic Customization: Web Forms’ flexibility allows attackers to create unique, unrecognizable forms for each target, defeating pattern-based detection.
- Social Engineering: The combination of urgency and familiar branding makes recipients more likely to engage without suspicion.
Mitigation and Detection
The abuse of DocuSign Web Forms exemplifies how threat actors adapt legitimate services to deceive even the most vigilant users. As these attacks evolve, the need for advanced email and browser security solutions becomes increasingly critical. Stay ahead of attackers by choosing tools designed to prevent threats at first sight.
To combat these advanced phishing tactics, organizations and individuals must adopt robust security measures, such as:
- Dynamic URL Analysis: Analyzing links in real-time for redirection patterns.
- Behavior-Based Detection: Monitoring form interactions for signs of phishing intent.
- User Training: Educating employees to recognize subtle signs of phishing, such as unexpected forms or requests for credentials.
Perception Point’s advanced detection mechanisms, including real-time dynamic analysis and computer vision models, provide proactive protection against these threats.
For more insights into the latest phishing tactics and defenses, contact Perception Point.























