End of semester ATO, anyone?
Since the beginning of May, the cybersecurity analysts of Perception Point’s Incident Response (IR) team have seen an uptake in account takeovers (ATO) specifically targeting major American universities. Some of the ATO victims include Indiana University, New Hampshire University, Illinois State University, and Oregon State University.
While analyzing malicious emails caught by our advanced threat detection platform, our IR team noticed something irregular: of the flagged, malicious emails coming from legitimate senders, many originated from university domains. Upon further review, it was clear that these incidents were textbook cases of ATO.
Below are some examples of the emails our clients have received, sent by university domains. Each email spoofs Microsoft 365 and leads to a spoofed Microsoft login page:
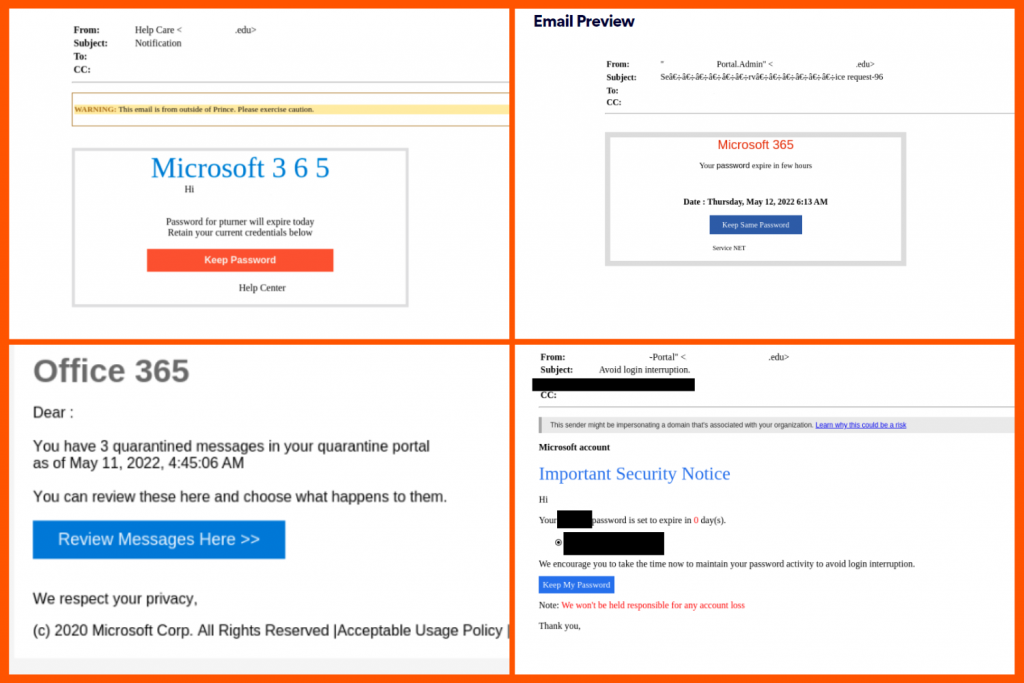
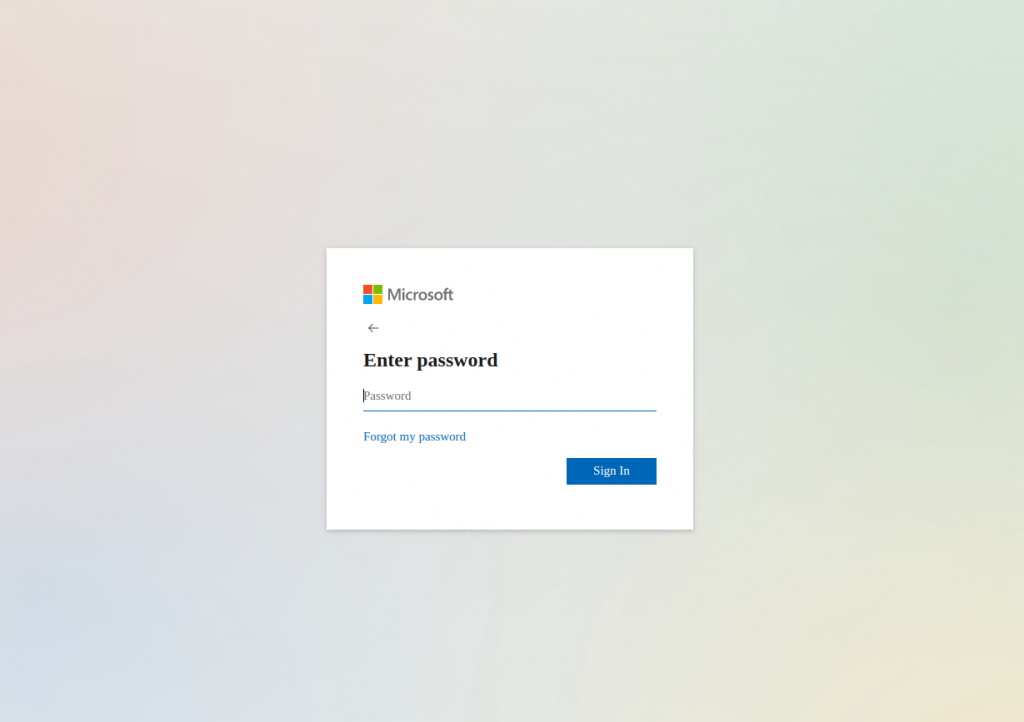
Let’s learn about ATO
What makes ATO attacks particularly dangerous is the ability to amplify damage. If an account takeover is not caught and remediated promptly, it can lead to far worse consequences. Moreover, when an attacker gains access to a legitimate email account, they often use the compromised account to send more malicious (phishing) emails.
When someone receives a message from a known source or vendor, they trust that the content is legitimate and safe. It is under the guise of this trust that attackers strike and continue the ATO cycle by luring more unsuspecting victims into their phishing campaign. Once an attacker obtains a new victim’s credentials, they can add another legitimate email account to their portfolio and continue the ATO/phishing sequence.
But wait, there’s more!
Now that we have explained the impact of typical ATO attacks, let’s go deeper into why ATO attacks targeting universities are especially problematic:
- University networks and email accounts host sensitive data belonging to students, faculty, and staff. This information spans from phone numbers and addresses to bank details and social security numbers. No organization wants this type of information leaking – especially an educational institution.
- As major research institutions, many universities have relationships and share projects with external organizations from both the private and public sectors. While it is obvious that professors don’t want their personal work stolen, on a larger scale, universities also don’t want major, confidential projects and research taken or made public.
- A common consequence of ATO is ransomware. Ransomware can impact an organization’s reputation and lead to significant financial losses, but for universities specifically, it can also affect day-to-day student life if a threat actor chooses to employ double or triple extortion techniques.
The bottom line
Our IR team sees ATO attacks all the time. What they don’t see are ATO attacks targeting university domains over such a short period of time. This is not the first time universities have been targets for cyber attackers, but it is the first time we have seen such widespread examples of compromised university-affiliated accounts reaching out to our clients. Therein lies the gravity: if we have noticed this trend within the sample set of our clients, it is likely that there are even more compromised universities, undergoing ATO that we have not seen.
Say what you will about a college education, but it seems like right now universities are easy targets for cyber attackers.
A special thanks to Ofek Ronen and the Perception Point IR team for contributing the sources for this article.























