Every modern enterprise in this day and age is under threat of information theft. Hackers use several types of phishing techniques to steal information from your organization. Barrel phishing, also known as double-barrel phishing, is rapidly becoming more prominent and is targeting organizations worldwide.
Barrel phishing targets people with two separate phishing emails, a technique that sets it apart from other types of phishing. The first email is not always malicious; it is simply “bait” to lure the user into believing that it is coming from a trusted source. Shortly after, the hacker will follow up with a more aggressive email containing malicious content. These pressure tactics can lead to oblivious users giving their information to hackers, putting their data and company at risk.
This article is part of a series about phishing.

A Real-life Example of Barrel Phishing
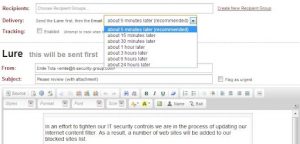
This real-world example of barrel phishing shows a hacker posing as someone from an IT security company. The hacker emailed the victim twice, with the first email “baiting” the victim through a light-hearted message.
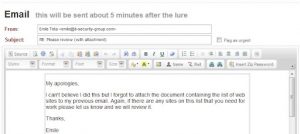
Later, the hackers then send an email with the “missing” attachment. This second email gives a sense of credibility to the previous one, leading the reader to think that the sender is trustworthy.
Most of the time, the second email will also push the user into sending over personal information or other files containing sensitive data.
Related content: Read our guide to phishing types.

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERTS
- Leverage behavioral analytics. Implement user behavior analytics (UBA) to monitor for anomalies in email engagement. For example, if an employee suddenly starts responding to external emails outside of their usual patterns, it could indicate a compromised account or a successful phishing attempt.
- Develop a layered phishing response protocol. Have a predefined, multi-step process for investigating suspicious emails. For example, after identifying a phishing attempt, ensure your team checks for any subsequent communications that may follow the initial contact to catch double-barrel phishing early.
- Integrate phishing-resistant MFA. Implement multi-factor authentication methods that are resistant to phishing, such as hardware tokens or app-based authenticators that are not reliant on SMS or email. This can mitigate the impact even if credentials are inadvertently disclosed.
- Simulate advanced phishing attacks regularly. Conduct phishing simulations that specifically include double-barrel scenarios. By mimicking real-world attacks, you can train your employees to recognize the subtle differences between legitimate follow-ups and phishing attempts.
How Can Barrel Phishing be Prevented?
Despite being a constant threat, there are several ways to prevent the worst effects of barrel phishing:
- Check the sender’s email address and domain to see if it is coming from a trusted and legitimate source.
- Analyze the link before clicking to ensure it points to a legitimate website. Look for inconsistencies in grammar and spelling (this is a common trait and surefire way to differentiate phishing emails from authentic emails).
- Focus on improving cyber security literacy within your organization, including educating your team on detecting phishing emails.
- Organizations can use an advanced email security solution with a dynamic analysis of files and URLs to intercept these email attacks before they even get to the user’s inbox. This preventative measure eliminates the need to rely on your employees’ ability to catch these sophisticated phishing attacks.
Perception Point’s email security solution prevents clone phishing through advanced detection technologies, keeping your team safe from malicious online actors and hackers.
Here’s some related content you may enjoy: How to Prevent Phishing

Barrel phishing targets people with two separate phishing emails, a technique that sets it apart from other types of phishing. The first email is not always malicious; it is simply “bait” to lure the user into believing that it is coming from a trusted source. Shortly after, the hacker will follow up with a more aggressive email containing malicious content. These pressure tactics can lead to oblivious users giving their information to hackers, putting their data and company at risk.
Despite being a constant threat, there are several ways to prevent the worst effects of barrel phishing:
– Check the sender’s email address and domain to see if it is coming from a trusted and legitimate source.
– Analyze the link before clicking to ensure it points to a legitimate website. Look for inconsistencies in grammar and spelling (this is a common trait and surefire way to differentiate phishing emails from authentic emails).
– Focus on improving cyber security literacy within your organization, including educating your team on detecting phishing emails.
– Organizations can use an advanced email security solution with a dynamic analysis of files and URLs to intercept these email attacks before they even get to the user’s inbox. This preventative measure eliminates the need to rely on your employees’ ability to catch these sophisticated phishing attacks.