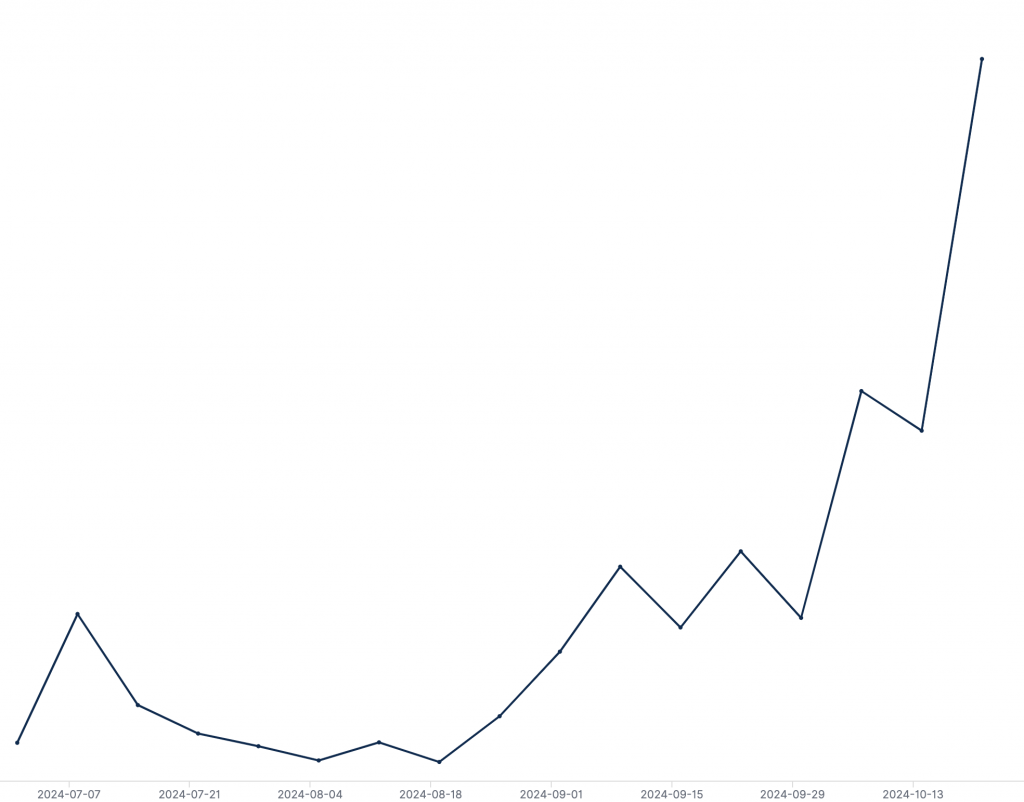
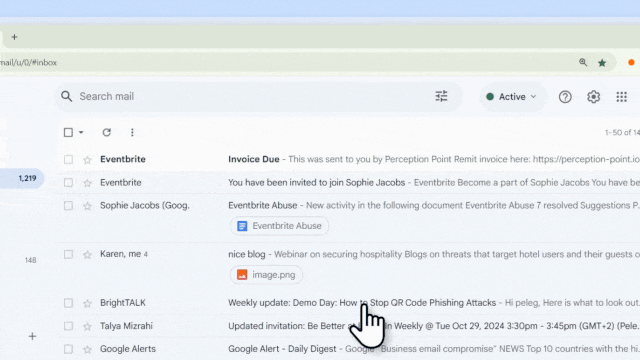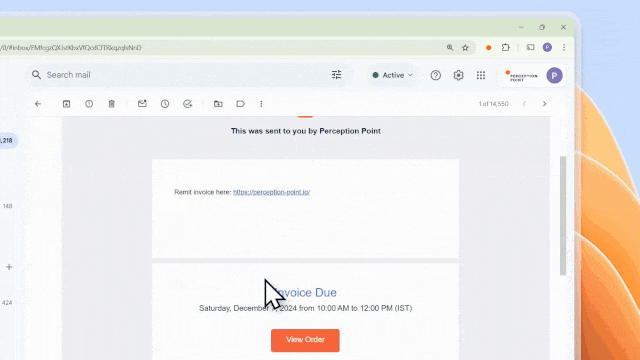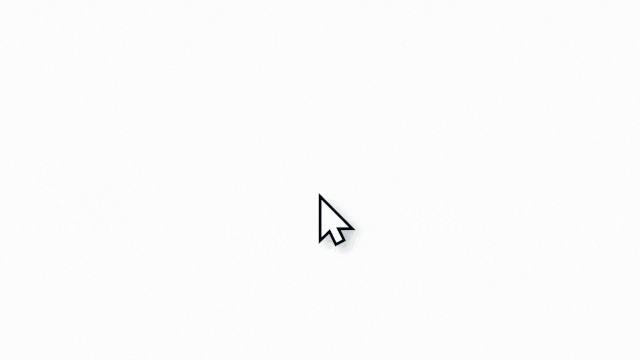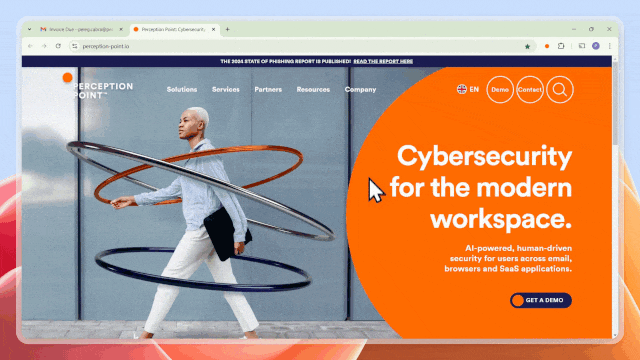
With over 5 million events annually on Eventbrite, attackers have found a new, trusted entry point for phishing – now showing a 900% growth rate in attacks.
Perception Point’s security researchers recently identified a mounting wave of phishing attacks, in which threat actors misuse Eventbrite’s services to steal financial or personal information. Within days, Perception Point has prevented thousands of these phishing emails, targeting both individuals and organizations worldwide across various industries–impersonating banks, airlines, postal services, energy companies, and more.
In this blog, we unpack the campaign behind this rampant Eventbrite abuse.
Eventful Phishing: Invite Only Attack
Attackers are using Eventbrite’s platform to mask their activities under the pretense of authentic Eventbrite notifications. Eventbrite is a U.S.-based platform for managing events and ticketing. It enables users (and evidently attackers) to discover, set up, and advertise local and virtual events.
Perception Point researchers observed phishing emails delivered via “[email protected]”. Despite being presented as legitimate events created on the Eventbrite platform, attackers use these messages to impersonate known brands like NLB, DHL, EnergyAustralia, and Qatar Post. Each email urges the recipient to take action: reset your PIN code; verify your delivery address; pay for an outstanding bill; pay for a package. These time-bound requests employ a social engineering tactic threat actors use to prompt the target to act fast.
In addition, the messages are sent in multiple languages, including English, German, and Slovenian, as seen in the examples below. By personalizing emails by language and branding, the campaign is not only global but also highly adaptable, evading detection by traditional security measures.
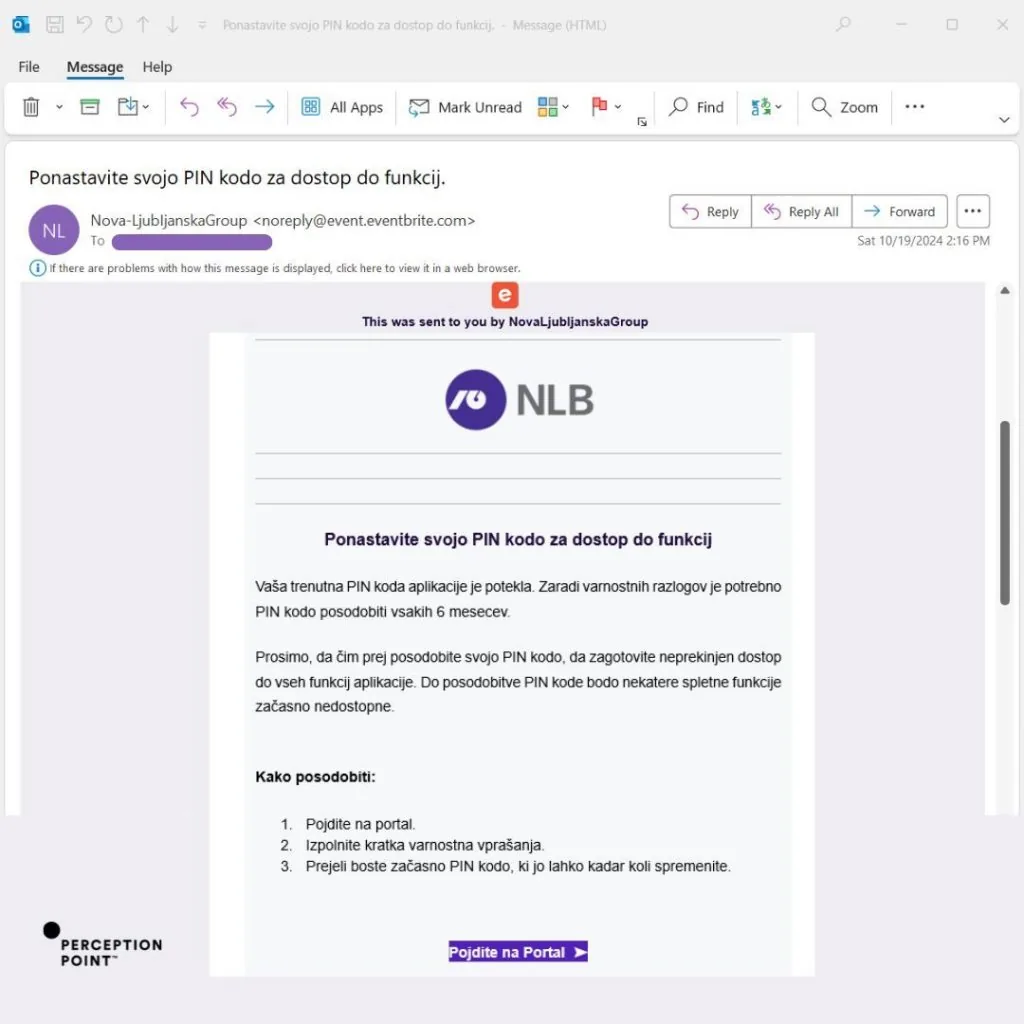
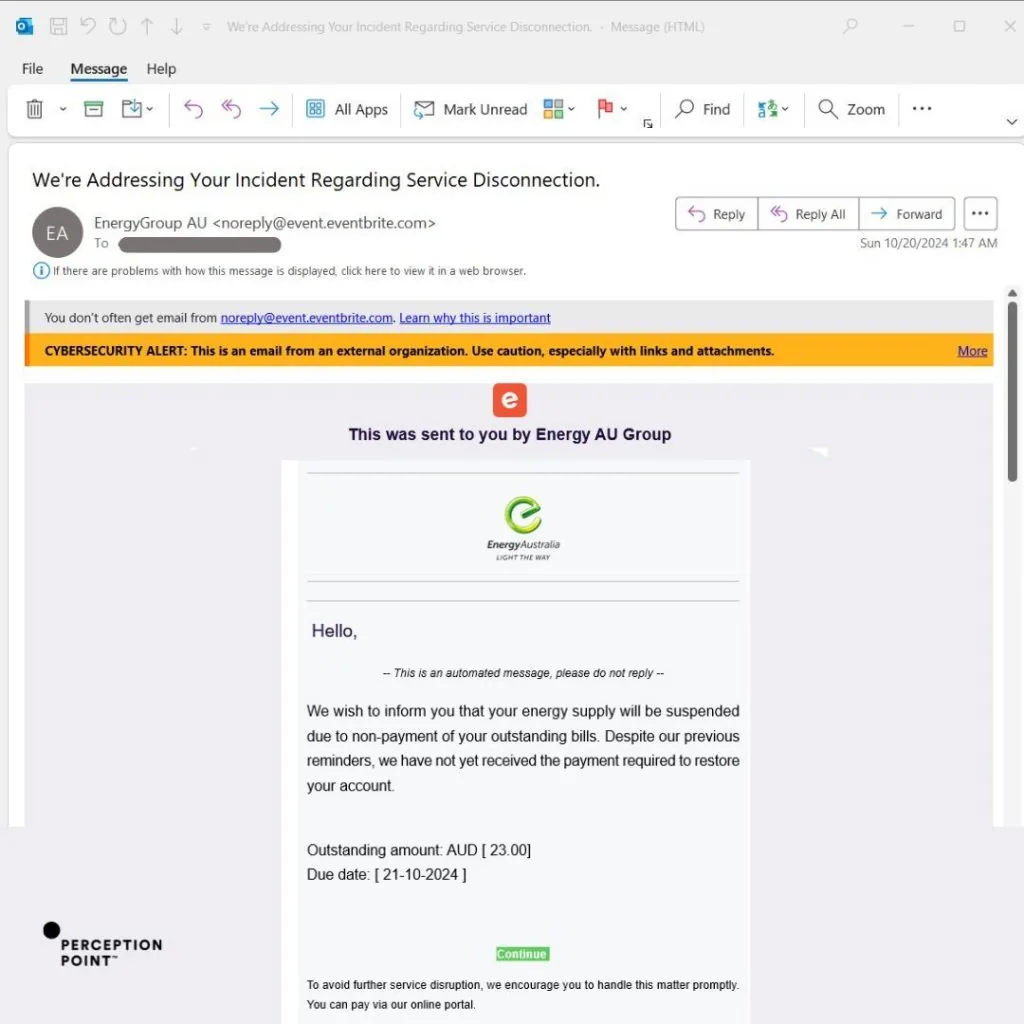
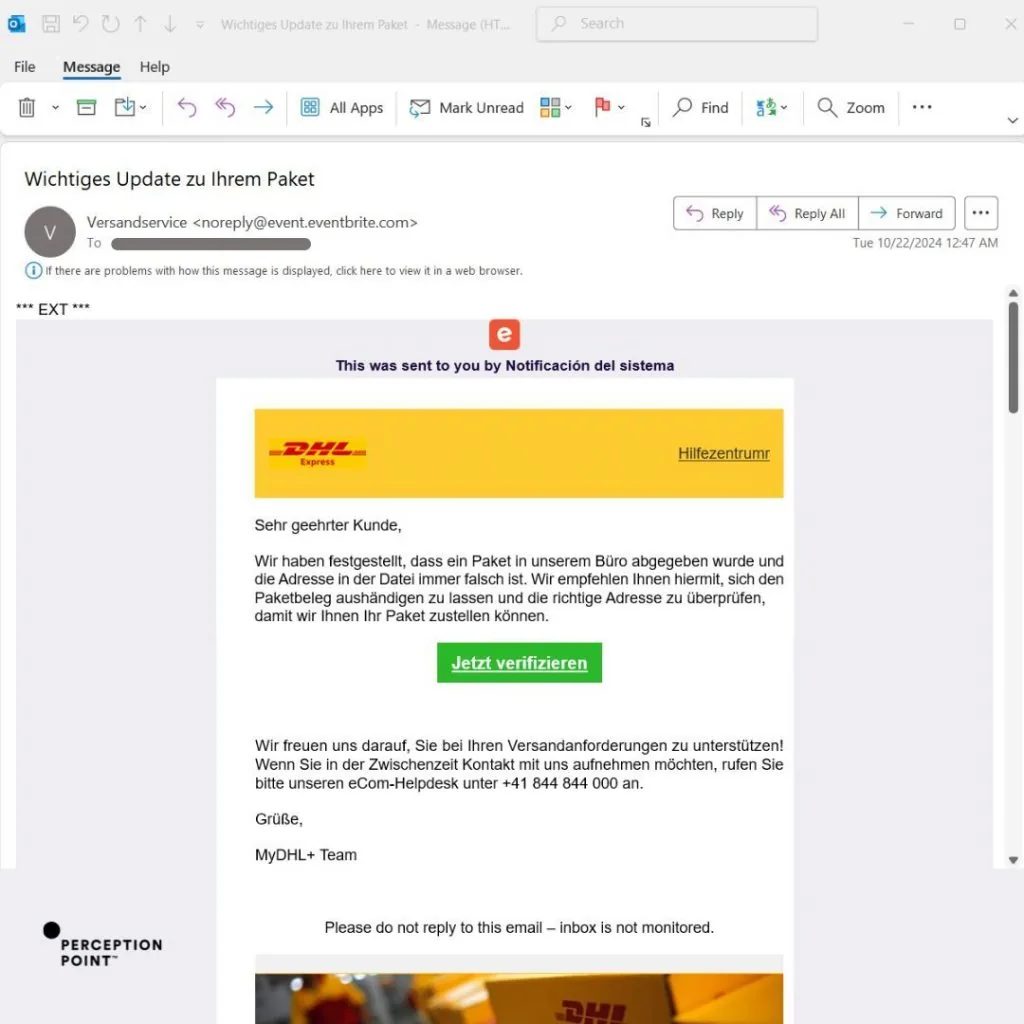
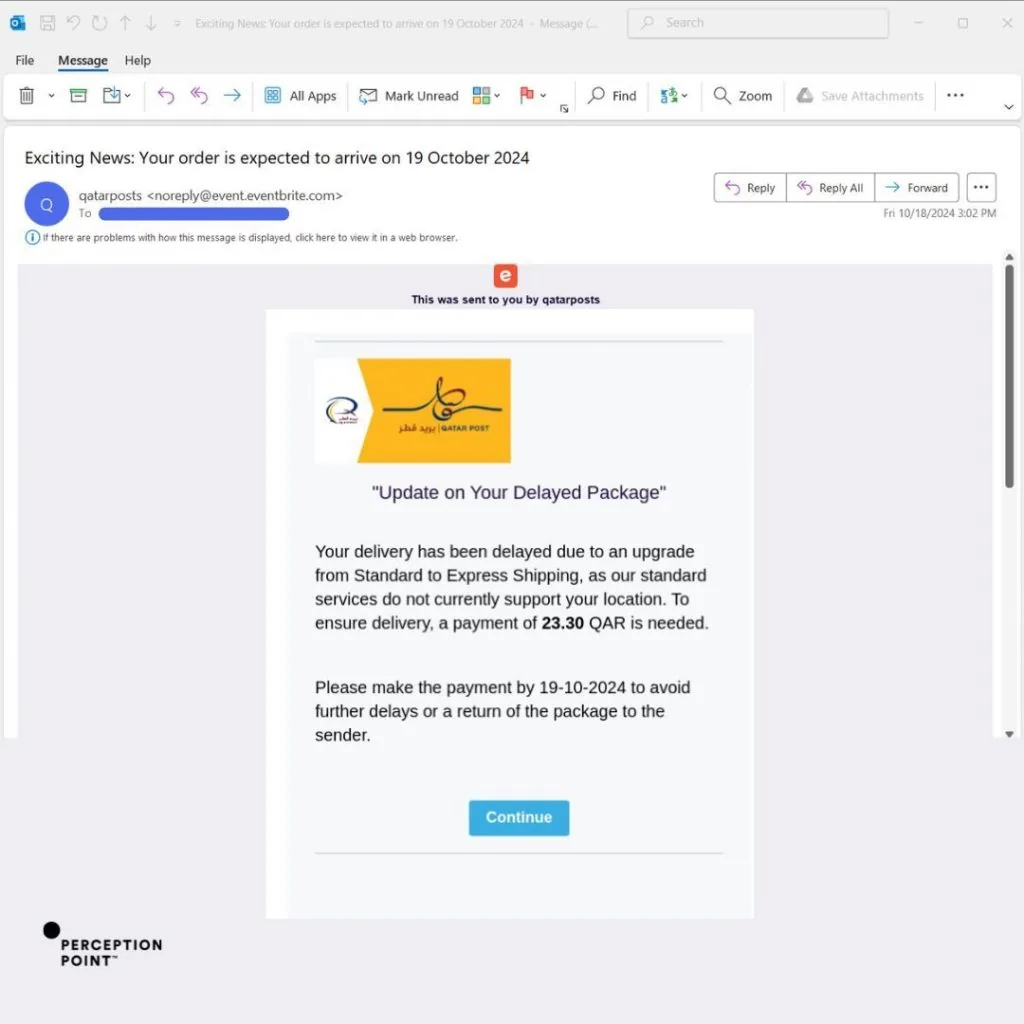
Once the target clicks on the phishing link, they are redirected to a phishing page. We found examples spoofing Quantas airline, Brobizz toll collection, web hosting platform One(.)com, European financial institution NLB, and many more. Designed to look like legitimate websites, targets are asked for personal information, like their login credentials, tax identification numbers, phone numbers, credit card details, and more.
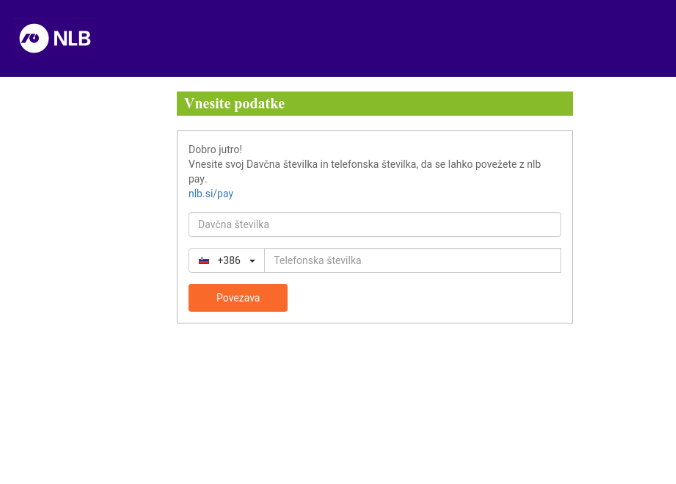
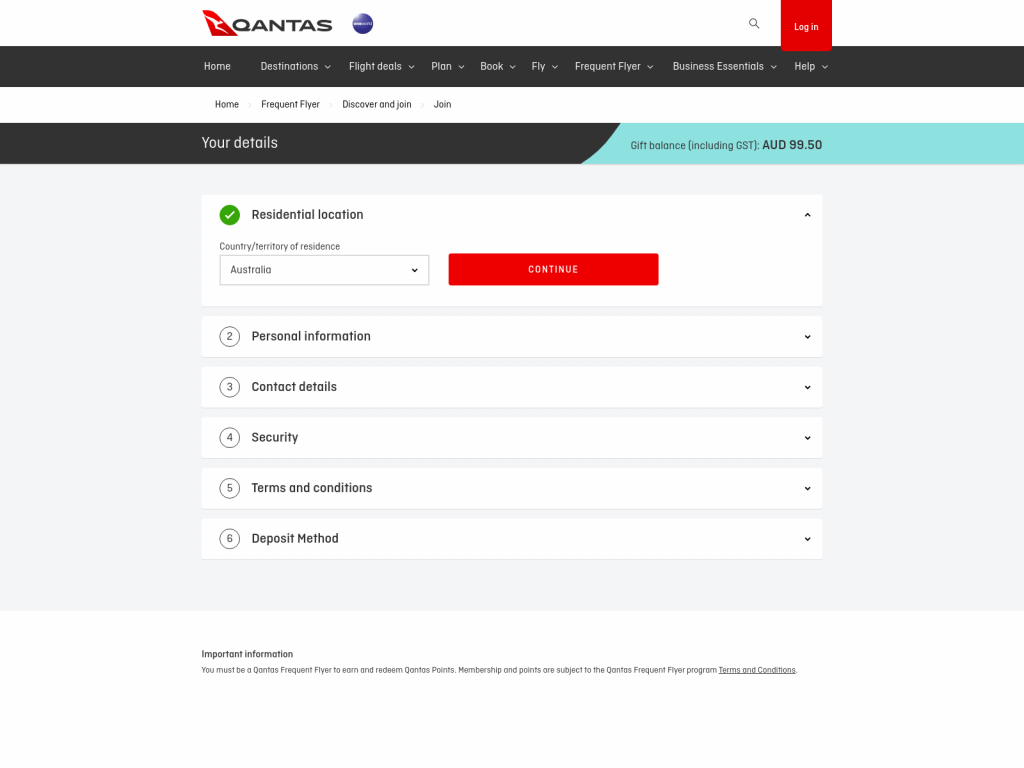

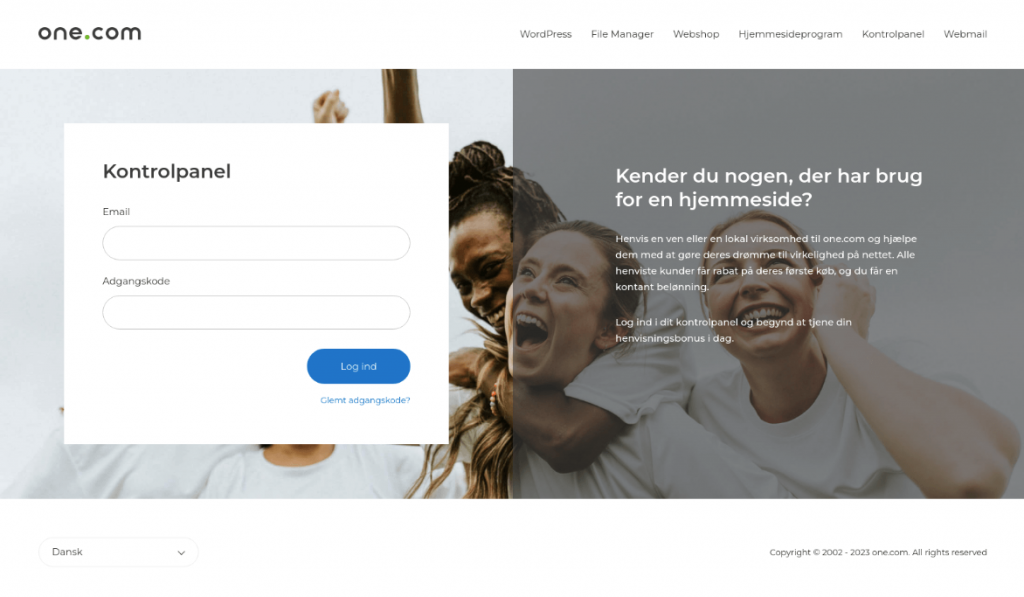
Once the target submits their information, the phishing scam is complete.
Behind the Attack: Planning is Key
In order to understand the intricacies of the attack, Perception Point researchers reverse engineered the process. Here’s how it works:
First, the attackers sign up to the Eventbrite site and create legitimate accounts. They then set up a fake event under the guise of a reputable brand, embedding phishing links within the event description or attachment.
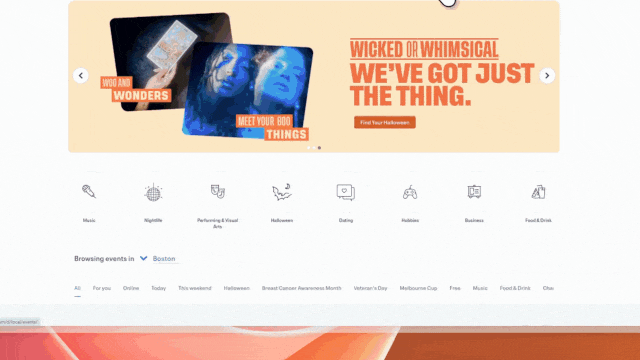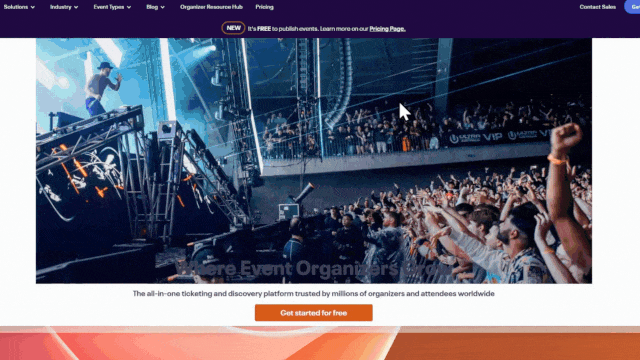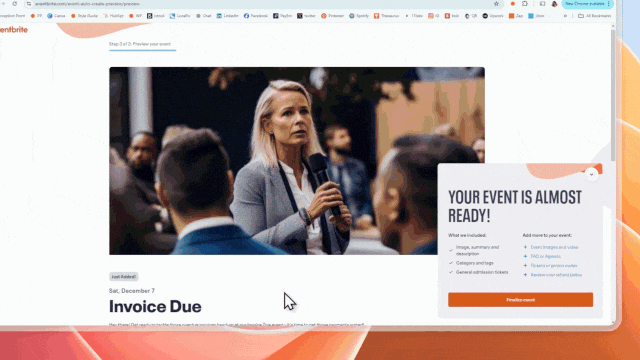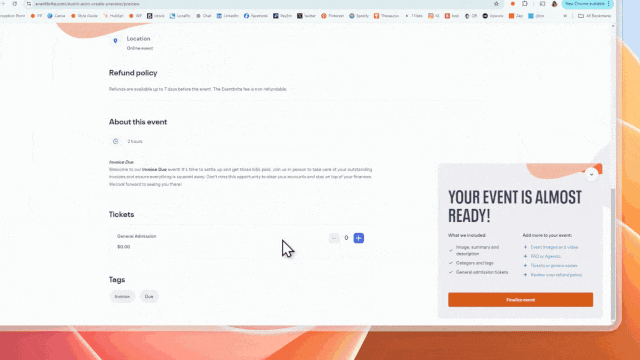
Once the attacker creates an event, they can then create emails from within the Eventbrite platform to be sent to attendees. These emails can include text, images, and links, all of which are prime opportunities for attackers to smatter in malicious content.
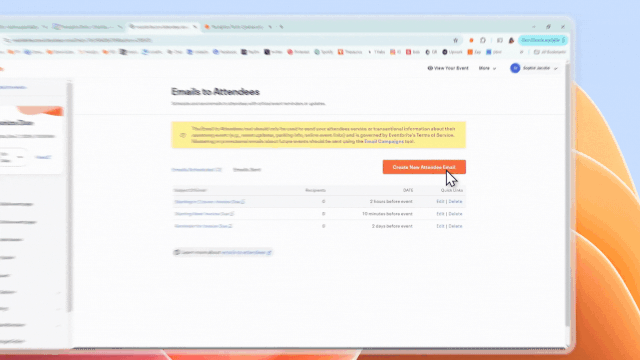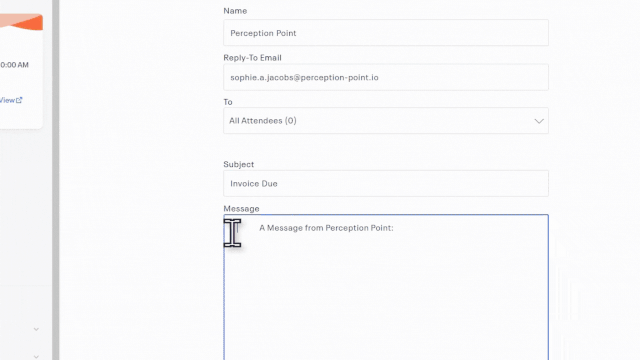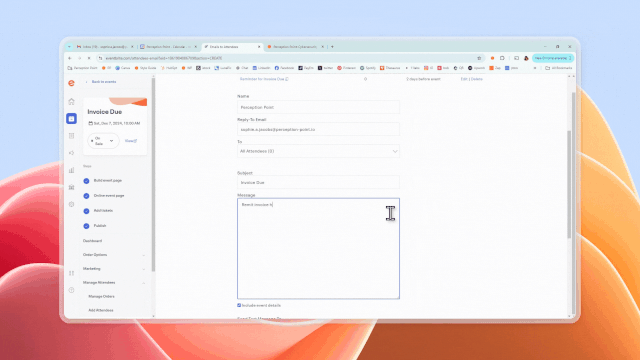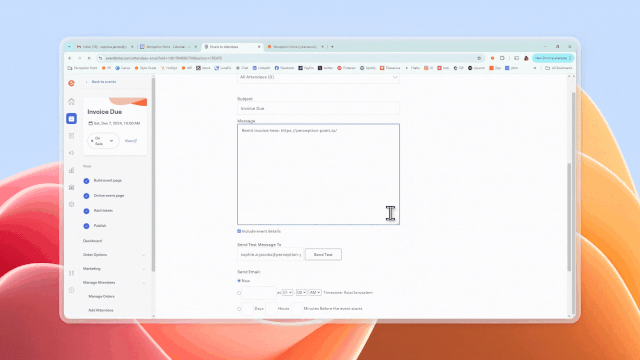
The attacker then enters their list of targets (or “attendees”) and sends them the invite email.
Once sent, the target receives an email from “[email protected]”, containing all of the malicious details the attacker included.
Because the email is sent via Eventbrite’s verified domain and IP address, it is more likely to pass email filters, successfully reaching the recipient’s inbox. The Eventbrite sender domain also increases the likelihood that recipients will open the email and click through to the phishing link. This abuse of Eventbrite’s platform enables the attackers to evade detection, ensuring higher delivery and open rates.
Preventing the (Main) Event
This sophisticated phishing campaign was caught through a multi-layered approach combining Perception Point’s advanced machine learning (ML) models, cutting-edge infrastructure, and obfuscation detection capabilities.
Trained on multilingual data, Perception Point’s ML content models flagged these emails as suspicious, recognizing clues in the message content and context that hinted impersonation and credential phishing attempts. Perception Point’s platform infrastructure was able to detect and analyze the large volume in email traffic, identifying unusual patterns in sender behaviors, subject lines, and content structure. By leveraging anti-evasion models, Advanced Email Security platform detected and decoded hidden text, URLs, and encoded strings that would otherwise bypass detection mechanisms.
From “Save the Date” to saving the day, Perception Point’s proactive threat prevention stopped this phishing wave before it reached inboxes, shielding users from a complex two-step attack. However, similar campaigns remain active, with attackers continually adapting their tactics. We urge all readers to stay alert for unexpected event invitations and keep security defenses updated to counter these Eventbrite-abusing threats.























