General recommendations.
- Ensure your security solution has strong anti-spoofing and anti-BEC algorithms, uncovering advanced text and display-based attacks.
- Ensure your solution can uncover archived-based attacks. Attackers are no longer sending “plain-vanilla” campaigns. They evolve and conceal their intent.
- Educate your employees. More so now than ever with employees working from home, you still need to make sure they are up to date. Send newsletters, testing emails and share samples of attacks. Employees are a critical link in the chain!
Phishing Campaign 1: The LinkedIn phishing.
OVERVIEW.
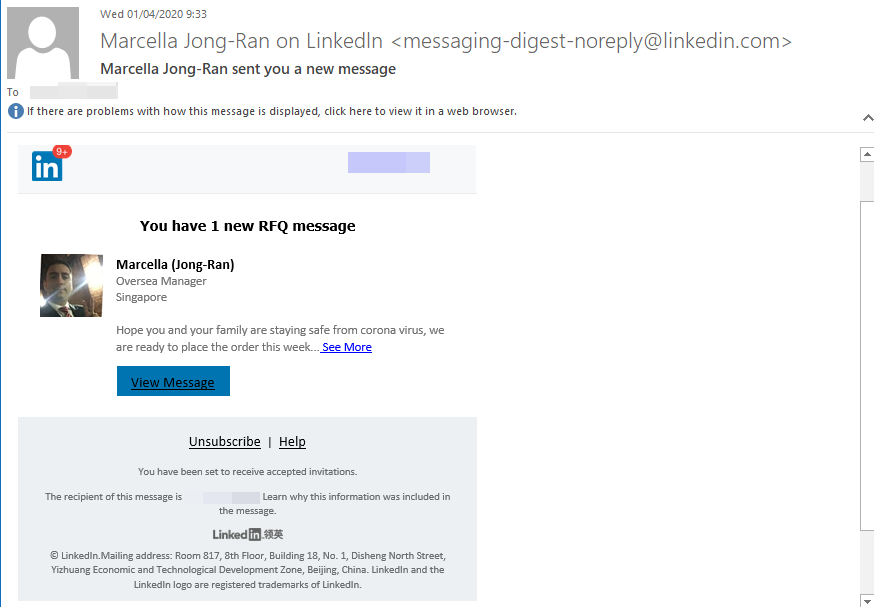
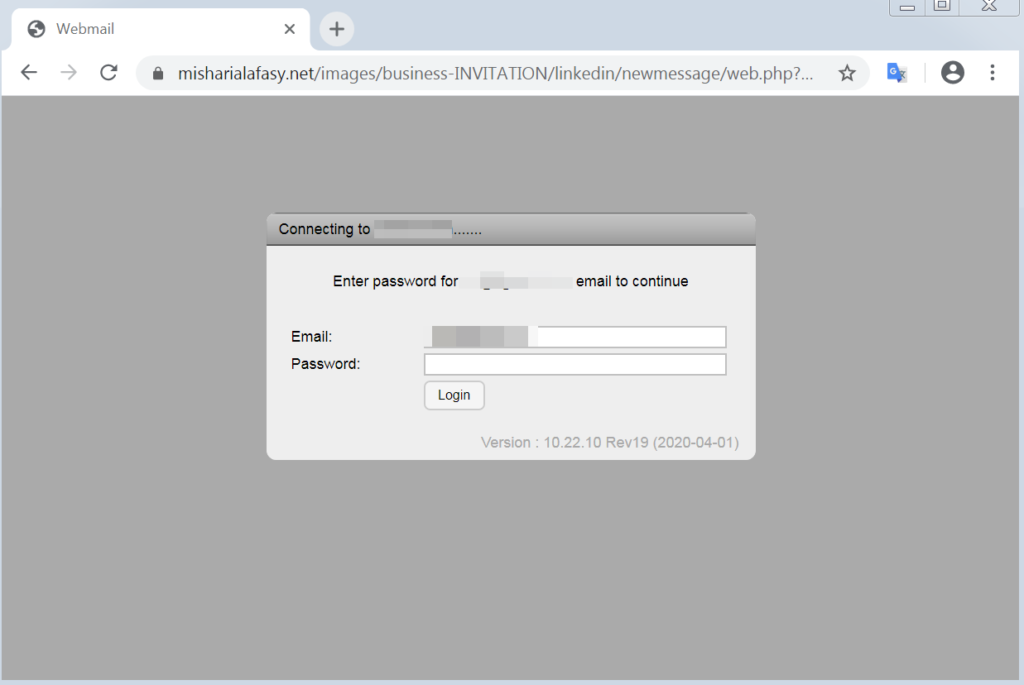
In this attack, we see again how the Coronavirus is used as the “background story” of the attack. This time that attacker sends an email with a fake LinkedIn message appearance, trying to trick the end user and make him open the full ’InMail’ he supposedly has just Received to his LinkedIn. However, this is a phishing attempt – once clicking on the link, a fake login page pops up where the attacker attempts to steal the target’s credentials.
It is important to add that the attacker also spoofs the email address to look like an official email was sent from LinkedIn.com. This extra level of sophistication can sometime mislead the target to believe this is a real attack.
IOCS.
Subject: Marcella Jong-Ran sent you a new message
From: Marcella Jong-Ran on Linkedln <[email protected]>
Source IP: 125.227.146.130
Extracted Link: https://misharialafasy.net/images/business-INVITATION/linkedin/newmessage/web.php
Phishing Campaign 2: The not so Safe Masks.
OVERVIEW.
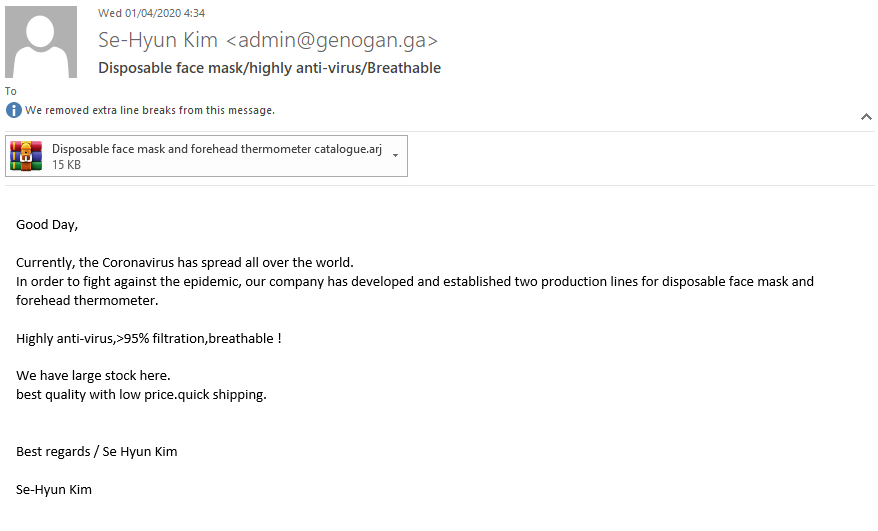
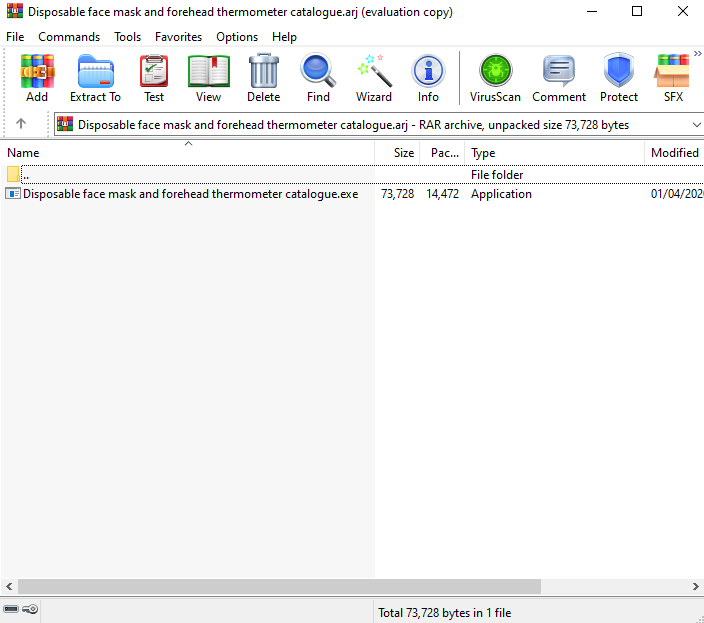
In this campaign, the attacker pretends to be a supplier who sells masks and thermometers, products with very high demand due to the current health situation. The attacker hopes that intrigued targets will open the archived file which has malware embedded within. The use of this evasion technique is on the rise since many legacy email security vendors allow these files to pass through the organization, which can cause significant damage. In this case, (as can be seen in our previous blog), the targeted victim would have opened the file, leading to malicious code running on the background of the end-user’s host.
IOCS.
Subject: Disposable face mask/highly anti-virus/Breathable
From: Se-Hyun Kim <[email protected]>
Source IP: 89.36.212.249
Filename: Disposable face mask and forehead thermometer catalogue.exe
SHA256: ed0771cbd1d5785eae5fdc6da1490083ef270df4b644f65f77736148fcdf224a
IOCS.
Subject: Marcella Jong-Ran sent you a new message
From: Marcella Jong-Ran on Linkedln <[email protected]>
Source IP: 125.227.146.130
Extracted Link: https://misharialafasy.net/images/business-INVITATION/linkedin/newmessage/web.php
Subject: Disposable face mask/highly anti-virus/Breathable
From: Se-Hyun Kim <[email protected]>
Source IP: 89.36.212.249
Filename: Disposable face mask and forehead thermometer catalogue.exe
SHA256: ed0771cbd1d5785eae5fdc6da1490083ef270df4b644f65f77736148fcdf224a























