Zero Trust is becoming a standard approach to securing access to enterprise applications (both cloud and on-prem). With Zero Trust, access is granted based primarily on user authentication and risk level, and not on the user’s presence in the corporate network.
Based on the user’s credentials, the enterprise can grant access to a subset of enterprise resources and employees can work from any network without relying on a VPN connection. The architecture is called “Zero Trust” because the enterprise shouldn’t automatically trust endpoints within the corporate perimeter. Instead, it should verify all users and endpoints.
This is part of a series of articles about Zero Trust.

Why do “Zero Trust” approaches blindly trust endpoints?
While being a great step in the right direction, common Zero Trust approaches have a fundamental design flaw that is the result of a wrong assumption. The wrong underlying assumption is that the Zero Trust broker can check the health of user endpoints and then trust them with access to enterprise resources.
This might be true for some extremely locked-down endpoints. However, most enterprise user endpoints run operating systems like Windows and have a very large and potentially vulnerable code base, a wide variety of legacy applications/middleware, and access to risky malicious networks or internet resources.
These endpoints can easily be compromised by determined attackers. Once a device is compromised, the operating system can no longer be trusted as malware resides in the same operating system kernel and can tamper with operating system health checks.
This means that many enterprises that adopt Zero Trust may still mistakenly trust user endpoints. This is a critical flaw as it allows attackers to breach a user’s device and then ride the user’s authenticated session to do harm. Gartner recommends granting access only after getting strong attestation of device identity. Gartner also suggests leveraging 3rd party products that ensure deeper device security and can isolate access on both the endpoint side and on the network side.
Without this missing link of strong device identity, Zero Trust creates a false sense of security as it encourages enterprises to allow access to corporate resources from personal/unmanaged/BYOD endpoints, relying on basic (and easily forgeable) health checks to prevent malware from getting in. This makes things worse, as personal/unmanaged endpoints have a higher probability of getting infected.
Some enterprises try to close this gap by deploying a slew of endpoint detection/protection agents on the user’s device, but this ends up being a cat-and-mouse game with endpoint malware. Furthermore, such agents and restrictions often limit what users can do and can lead to issues with user privacy.
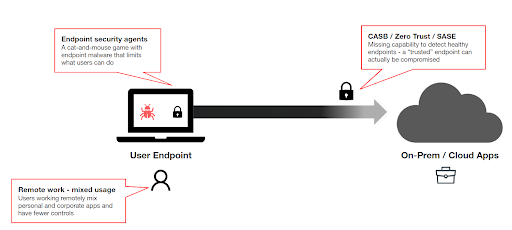
With COVID-19 and the remote-first era we live in, things get worse as more and more employees work remotely and mix both legacy corporate apps and brand new collaboration tools on the same endpoint, opening it up to new types of threats (not to mention the increasing personal usage of endpoints in unmanaged home network environments).
To make Zero Trust a true end-to-end security solution, organizations must design their endpoints to be trusted. However, IT cannot just extremely lock down their endpoints to achieve that level of trust – IT must make sure end-users get a great user experience and can get their jobs done in an efficient, easy, way.
Solutions that limit which apps users can use or remove local admin rights will not fly for today’s knowledge workers. Users need a way to use the latest tools and apps, without having IT whitelist every app, website, and service.
Related content: Read our guide to application whitelisting.

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERTS
- Regularly audit and update endpoint security baselines
Continuously review and update the security configurations and baselines for your endpoints. As threats evolve, so should your security policies, ensuring that they remain effective against the latest attack techniques and vectors. - Employ risk-based adaptive authentication
Implement risk scoring for each access attempt based on contextual factors such as user location, device health, and behavior. Adjust authentication requirements dynamically, such as requiring multi-factor authentication (MFA) when accessing higher-risk resources or during unusual access patterns. - Integrate continuous user behavior analytics
Use machine learning to continuously analyze user behavior for anomalies. Even if a user is authenticated and the endpoint is verified, unusual behavior patterns can trigger additional security measures or revoke access in real-time, further minimizing the risk of a compromised endpoint. - Implement granular access controls with just-in-time access
Instead of providing broad access based on a one-time authentication, employ just-in-time access provisioning. This minimizes the time window an attacker has if they compromise a session and reduces the attack surface by granting access only when absolutely necessary.
Zero Trust with Perception Point
The good news is that you can eat the cake and have it too. With Perception Point’s Advanced Browser Security, you can have endpoints that make end-to-end “Zero Trust” a reality, while allowing users to productively use their endpoints.
Here’s a few examples of how:
- Zero Trust, IAM, PAM – by adding a reliable indication for OS health via OS isolation, Perception Point lets identity, privilege, and access management systems make better decisions and enforce access to enterprise assets exclusively through a trusted OS. This can also apply to legacy VPN gateways that can run host health checks to verify endpoints.
- Secure Web Gateways – switch from blocking risky traffic to securely allowing it, enabling full user productivity. The gateway redirects untrusted content (website / document), into the risky OS. Perception Point seamlessly integrates with existing gateways to do this redirection, without needing any additional data center/cloud infrastructure.
- VDI – Perception Point can offload some of the heavy web apps that are currently hosted on VDI. For example, browsers that require lots of IOPS/CPU/GPU resources can now run locally in the isolated browser instead of hogging the VDI infrastructure. Web apps that require a lot of cloud traffic no longer need to go through the corporate network and can go directly from the endpoint to the cloud, via the secure browser.
- MDM/UEM – instead of asking users to enroll their personal laptops and desktops into your MDM/UEM solution, you can manage a separate disposable VM on their endpoints, without violating their privacy or requiring them to install multiple intrusive agents.
Related content: Read our guide to Zero Trust security.
Perception Point Boosts the Entire Enterprise Security Stack
Perception Point complements many of the existing enterprise security investments, not just Zero Trust.
Perception Point Advanced Browser Security adds enterprise-grade security to standard browsers like Chrome, Edge, and Safari. The solution fuses advanced threat detection with browser-level governance and DLP controls providing organizations of all sizes with unprecedented ability to detect, prevent and remediate web threats including sophisticated phishing, ransomware, malware, exploits, Zero-Days, and more.
By transforming the organizational browser into a protected work environment, the access to sensitive corporate infrastructure and SaaS applications is secure from data loss and insider threats. The solution is seamlessly deployed on the endpoints via a browser extension and is managed centrally from a cloud-based console. There is no need to tunnel/proxy traffic through Perception Point.
An all-included managed Incident Response service is available for all customers 24/7. Perception Point’s team of cybersecurity experts will manage incidents, provide analysis and reporting, and optimize detection on-the-fly. The service drastically minimizes the need for internal IT or SOC team resources, reducing the time required to react and mitigate web-borne attacks by up to 75%.
Customers deploying the solution will experience fewer breaches, while providing their users with a better experience as they have the freedom to browse the web, use SaaS applications that they require, and access privileged corporate data, confidently, securely, and without added latency.
With Perception Point’s Advanced Browser Security you could:
- Reduce the time and money spent on whitelisting applications.
- Your team can access untrusted websites and SaaS apps, without security concerns and without added latency.
- Untrusted web content is deeply scanned reducing the risks from viruses and other downloadable threats.
- A seamless user experience as users are working in their native browser which is now protected
- Secure access to IT, DevOps, and other privileged web apps in their everyday environment
- Access to enterprise web apps from 3rd party/unmanaged devices
Contact us for a demo of our Advanced Browser Security solution
























