Within days of launching our anti-impersonation capabilities, we have detected within our clients multiple attack attempts using BEC techniques.
What is Business Email Compromise?
BEC or Business Email Compromise is a form of an impersonation-based attack leveraging social engineering. BEC attacks are on the rise, and given their com-bination of payload-less and payload-based methods, are often difficult for legacy email security systems to detect.
Below are several examples of active business email compromise attempts Perception Point’s platform recently intercepted.

Business Email Compromise Example #1 – Display Name Extortion.
This sample leverages Display Name Deception as the main infiltration technique. With this method the attacker claims to have taken over the end user’s email and sends him an email from what looks like his own email address. In order to create a sense of fear and urgency, the attacker tries to extort the user, claiming to have personal footage of the user that will be distributed to all of his/her contacts.
However, this is far from the truth. Actually, the email was sent from a domain that is not even in the organization. The attacker only changed the display name and did not actually gain control of the targeted user’s account.
Our engine detected the attack by identifying the fake headers used in the email.
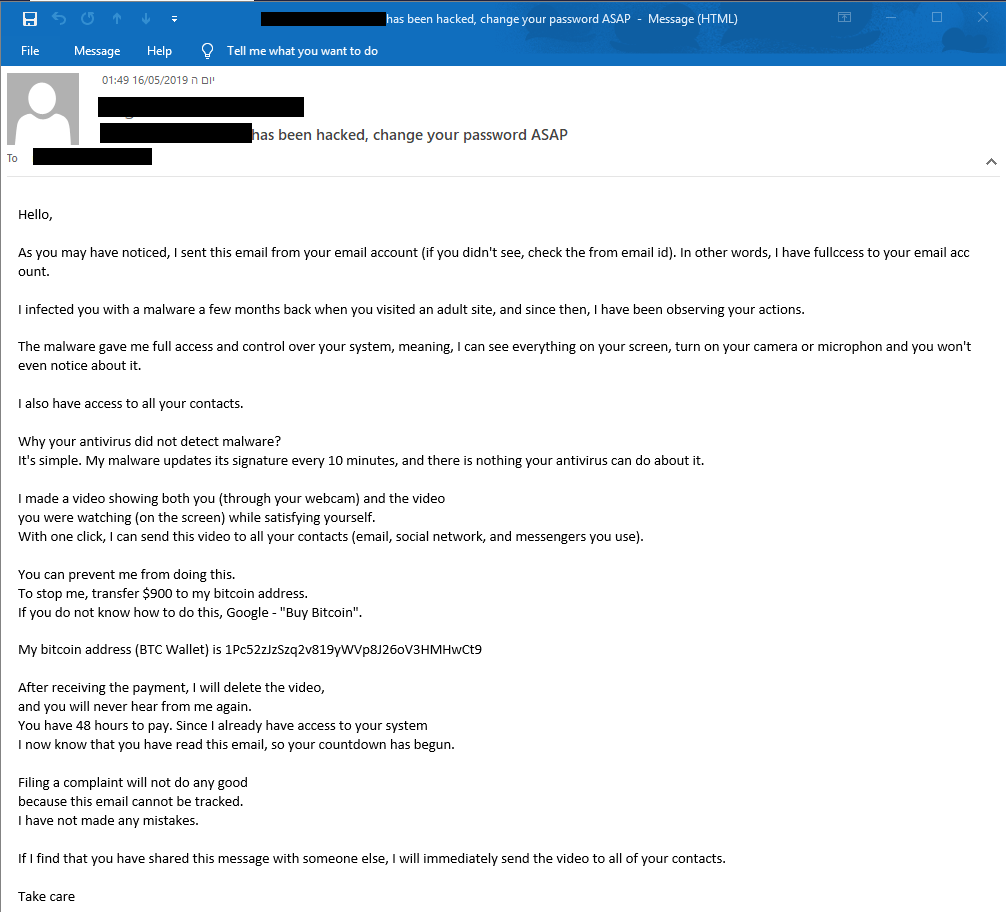
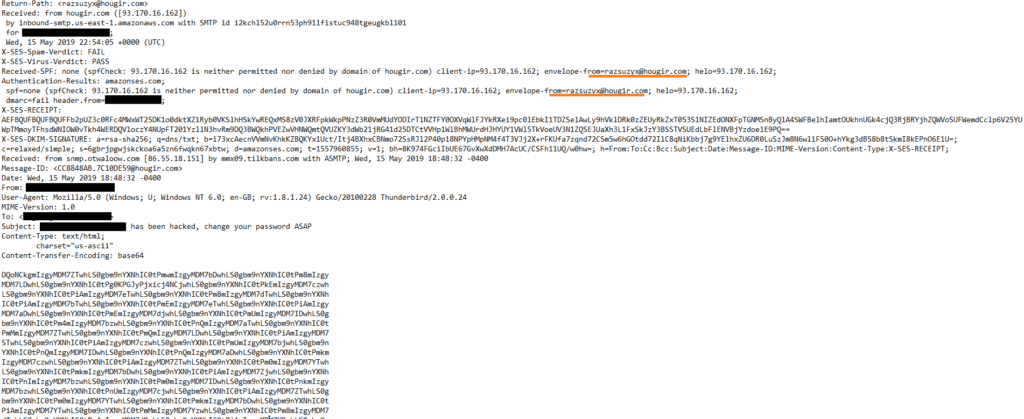
As you can see the attacker sends the email from an external address and changes the headers of the email to make them look like it was sent from the same email address.
Related content: Read our guide to BEC scams.

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERTS
- Leverage DMARC with strict alignment settings. Implement Domain-based Message Authentication, Reporting, and Conformance (DMARC) with strict “reject” policies for email spoofing. Ensure that both SPF and DKIM are correctly aligned to your primary domain to minimize domain impersonation risks.
- Utilize behavioral analytics to flag anomalies. Employ machine learning models to analyze and flag unusual patterns in email communication, such as abnormal requests for financial transfers, even if no payload is present. These models can be refined over time to catch sophisticated social engineering attempts.
- Simulate advanced BEC scenarios in phishing training. Include simulations of advanced BEC tactics in your phishing training programs, such as domain impersonation and CEO fraud, to increase employee awareness and response to such threats.
- Monitor for anomalies in email thread replies. Set up monitoring for unusual reply-to patterns within existing email threads, especially if the conversation suddenly involves unusual requests. This can help detect man-in-the-middle BEC attacks where the attacker inserts themselves into an ongoing conversation.
Designated Name Deception.
The following example is another form of Display Name Deception, but using a slightly different approach that seems to have involved more pre-attack information gathering.
Perception Point’s system detected an attempt to impersonate one of our client’s business emails. The attacker conducted basic research on the target user and found out she is affiliated with the financial department. Moreover, the attacker studied the names of other contacts in the same company and chose one name he believed might trick the user.
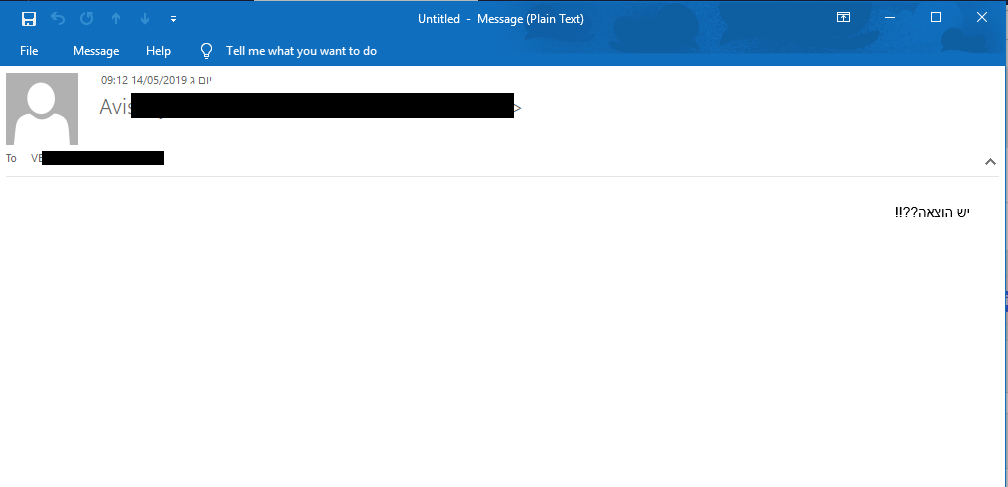
The content of the mail is very limited, showing that the attacker wanted to initiate a conversation about expenses and to later trick the user into acting wrongfully by wire transferring money.
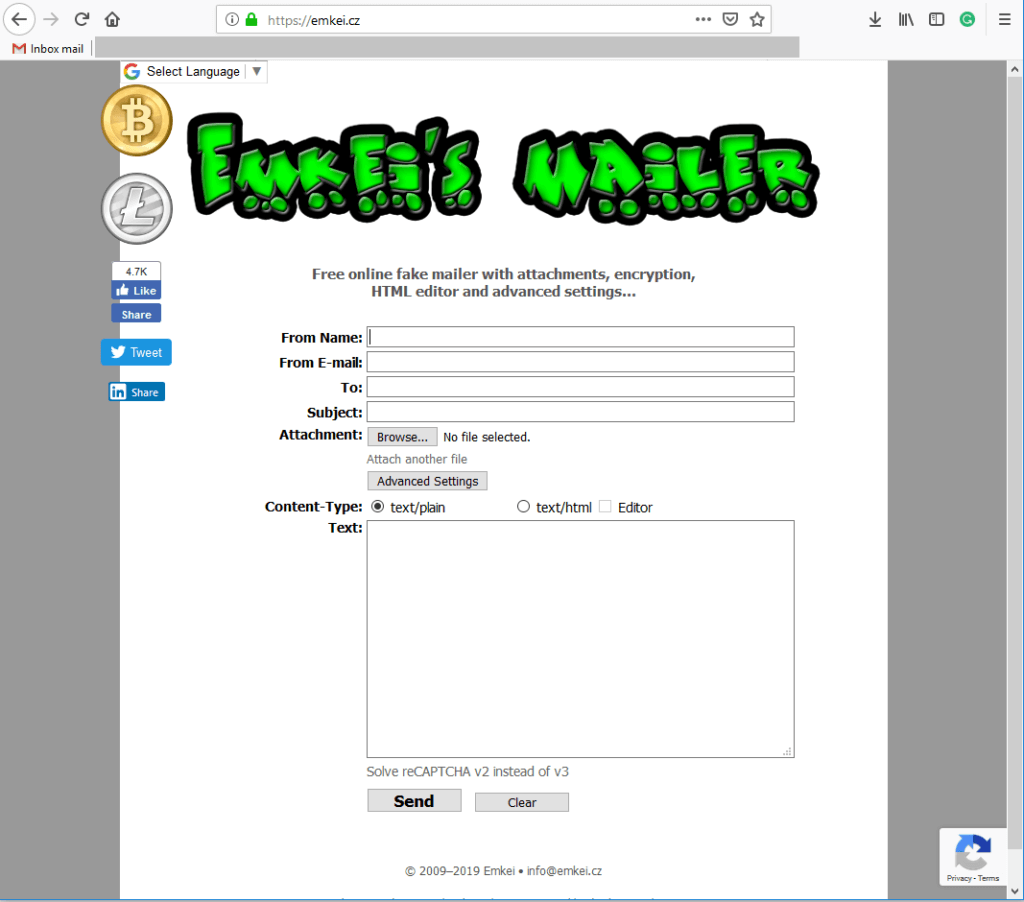
Perception Point’s algorithms identified the attempt in the very first email. A deeper investigation, including checking the headers of the email and its real source, found that the email was sent from an anonymous email sending service, which is outside of the organization. This can be seen in the screenshot below.
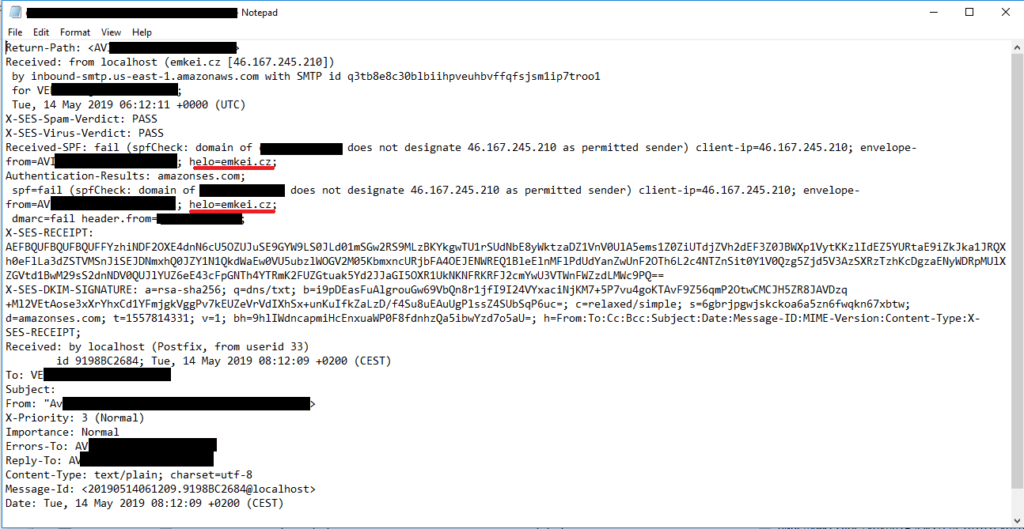
The email service the hacker used is “emkei.cz”, described as a “free online fake mailer”.

Whaling BEC attack.
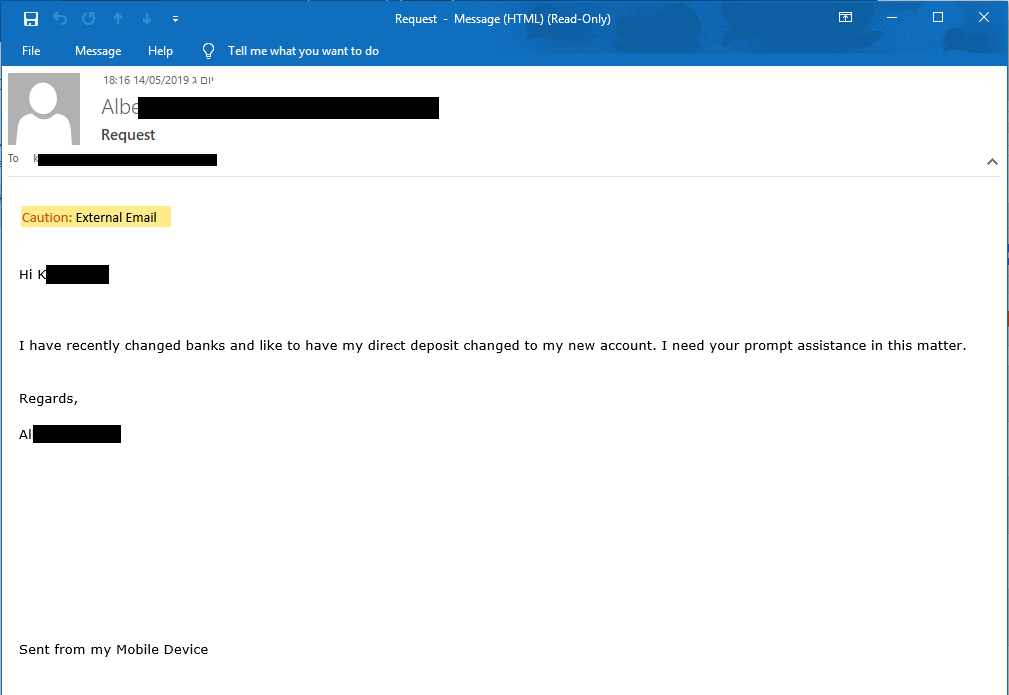
In this Whaling BEC attack, the attacker targets a high-profile user with access to business information in the organization, attempting to trick him into revealing sensitive information. In the example below, the attacker tried to initiate an email correspondence to make the target to wire transfer to a new bank account. This does not involve any payload and is pure social engineering.
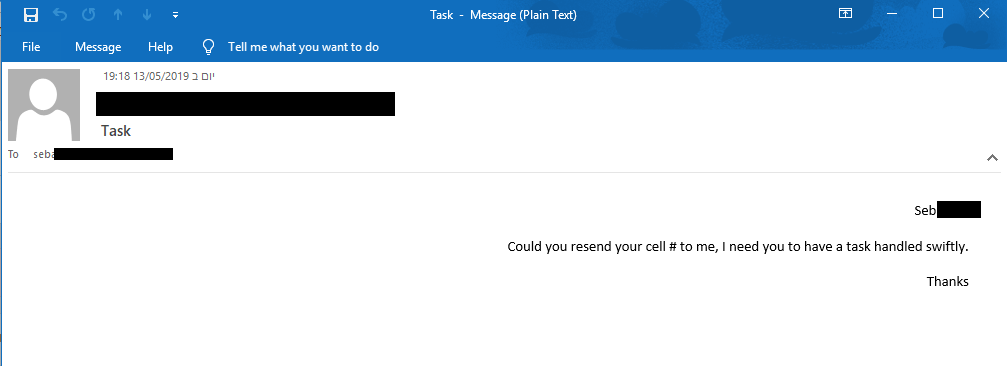
Another interesting example is the one below, in which the attacker impersonates he CEO of the company, asking a lower-level employee to call him for an urgent task. Leveraging the sense of urgency from upper management is known to push employees into acting without thinking whether the content of the email makes sense.
Domain Impersonation attack.
Another type of incident using BEC techniques is Domain Impersonation. The attacker creates an email that resembles the legitimate email address of the organization, trying to trick the user into believing the email address is legitimate and is part of the internal email users.
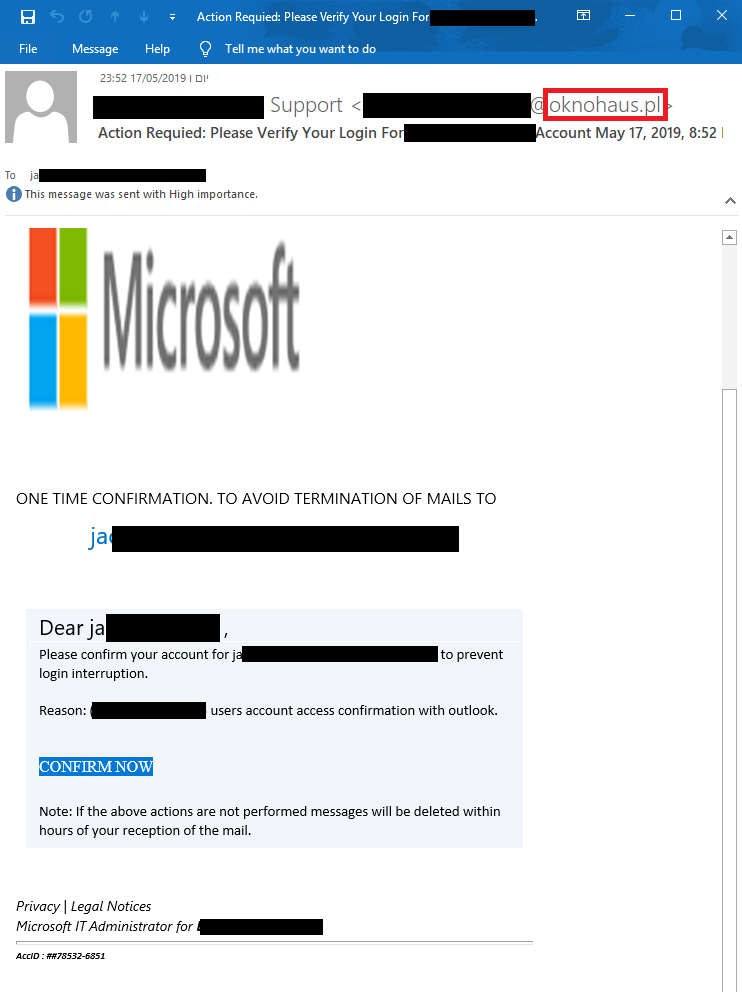
As can be seen above, the email is made to mimic the client’s IT support sending a legitimate email to the user. However, after looking carefully, you can see the domain does not belong to the organization, but rather from an external domain (Oknohaus.pl).
All of these attacks were detected by the BEC layer of Perception Point’s Advanced Email Security platform. Learn more about BEC in our whitepaper here.

BEC or Business Email Compromise is a form of an impersonation-based attack leveraging social engineering. BEC attacks are on the rise, and given their com-bination of payload-less and payload-based methods, are often difficult for legacy email security systems to detect.























