What Is Malware?
Malware (malicious software) is designed to disrupt the normal functioning of a computer or other device. It is an umbrella term for viruses, trojan horses, and other destructive computer programs that attackers use to compromise systems and networks, sabotage systems, and gain access to sensitive information.
Malware is usually a file or piece of code, often passed over a network, which can infect systems, steal data, grant unauthorized access, and otherwise advance an attacker’s goals. With millions of variants of malware commonly seen in the wild, there are many ways to infect a computer system.
Malware typically has one of the following goals:
- Giving the attacker remote control over the infected system.
- Investigating the local network and helping attackers perform lateral movement.
- Identifying and granting access to sensitive systems and data, and exfiltrating data.
- Stealing funds using accounts or credentials on the victim’s device.
- Using the victim’s device to perform illegal or unwanted activities, such as sending spam or mining cryptocurrency.
Ransomware is rapidly growing in importance and becoming a top priority for security professionals. It is another type of malware that encrypts files on a victim’s computer and requires a ransom in exchange for a decryption key, which, even if the victim pays up, is often not provided. Global-scale ransomware attacks have illustrated the devastating impact that malware can have on individuals, organizations, and entire industries.
This is part of an extensive series of guides about cybersecurity.
In this article

Tal ZamirCTO, Perception Point
Tal Zamir is a 20-year software industry leader with a track record of solving urgent business challenges by reimagining how technology works.
TIPS FROM THE EXPERT
- Adopt a zero-trust security model Implement a zero-trust approach where all users, devices, and applications are considered untrusted by default. This involves continuous verification and strict access controls, reducing the risk of malware infiltration.
- Utilize machine learning for anomaly detection Incorporate machine learning algorithms to identify anomalies that could indicate the presence of malware. These models can adapt and improve over time, offering enhanced detection capabilities for sophisticated threats.
- Strengthen email authentication mechanisms Use advanced email authentication protocols such as DMARC, DKIM, and SPF to reduce the risk of email-based malware attacks. These measures help verify the legitimacy of email senders and prevent phishing and spoofing attempts.
- Enhance user training with simulation exercises Conduct regular phishing simulation exercises to train employees on recognizing and responding to malicious emails. These simulations help reinforce awareness and improve the organization’s overall resilience to social engineering attacks.
Common Malware Types and Examples
Virus
A computer virus is malicious software that, once activated, copies itself from one folder to another and inserts its own code. Viruses can spread quickly and can infect systems to steal personal and financial information, send spam, or lock users out of their devices.
Worm
Worms are very similar to viruses in that they replicate themselves within a system, but unlike viruses, they cannot infect other programs. Once installed, the worm starts running silently, infecting computers without the user’s knowledge. Worms can replicate themselves hundreds of times, consuming system resources and damaging devices.
Trojan
A Trojan Horse is a type of malware that masquerades as legitimate software but is actually used for malicious purposes. Trojans claim to be free updates, games, or antivirus programs and can trick users into installing them on their devices. Once installed, Trojans run silently in the background to steal important data, install backdoors and perform other harmful activities.
Ransomware
Ransomware has massively grown in recent years and causes damage estimated at more than $8 billion worldwide by the end of the year. Ransomware is malware that encrypts a victim’s data and blocks access until a ransom is paid. The most common way ransomware is delivered is by clicking on a link in an email or opening a malicious attachment.
Spyware
Spyware is software that is installed on a device and secretly monitors a victim’s online activities. It collects data such as passwords, credit card numbers, and browsing activity.
Adware
Adware is malicious software that, once downloaded, displays unwanted advertisements on victims’ computers. Adware doesn’t always do immediate damage, but it can be very annoying as it leads users to unwanted advertisements, opens intrusive pop-up windows, and might redirect users to malicious sites.
Botnet
A bot is a malware-infected device that performs harmful tasks without the user’s knowledge. A botnet is a network of infected devices working together under the control of an attacker. Botnets can be used to conduct phishing campaigns, send spam, or conduct distributed denial-of-service (DDoS) attacks.
Fileless Malware
Fileless malware is malicious software that does not rely on download of malicious files. Instead, it uses legitimate programs to infect a system. It is hard to detect and remove, because it only operates in memory and does not leave any footprint on the target system.
Fileless malware is a powerful type of attack that can evade most security tools—only behavioral analysis and other advanced techniques can identify and address them.
A Short History of Malware Development
1980s: The Morris worm
One of the first and most prominent malware incidents in history was the Morris worm, introduced in 1988. Developed in academia, it could spread to other systems over a network, primarily by exploiting vulnerabilities in software called sendmail which was then commonly deployed on computers. The worm did not check whether the target system was already infected. It created multiple copies of itself on each system, consuming all system resources of the victim and rendering them unusable.

1990s: The first hacker communities
The Morris worm showcased the power of malware, and led to the first conviction for malware development. Since then, many other types of malware have emerged. In the 1990s, computers became more ubiquitous and affordable to the general public, and the first hacker communities began to develop worldwide.
Gradually, their focus shifted to making money. Programming started to be taught in schools and universities, and new high-level programming languages were created, making it easier for inexperienced people to start writing code. The same skills were exploited by criminals to write malicious code.
2000s: Organized cybercrime and economically motivated threat actors
Over the next decade, malware development has become a lucrative and organized illicit activity. Specialized cybercrime organizations with clearly defined responsibilities began to emerge.
Many of these groups focused on attacking individual computer users and stealing funds or carrying out fraud. They used all available money laundering methods, initially using money mules and later turning to cryptocurrencies to avoid being tracked. These groups are often referred to as economically motivated threat actors.
2010-2020s: Ransomware and the shift to larger targets
In recent years, the focus of cybercriminal groups has gradually shifted from attacking consumers or small businesses to bigger and more attractive targets—large institutions. The most common example is using ransomware to encrypt an organization’s files before demanding a ransom to restore access. Modern attacks make use of double extortion tactics—threatening either to encrypt files or to release sensitive material to the public.
State sponsored malware
Governments are also making use of malware for cyberespionage and cyberwarfare. The Stuxnet attack, which was used to sabotage Iranian nuclear centrifuges, gained public attention due to its ability to cause physical destruction.
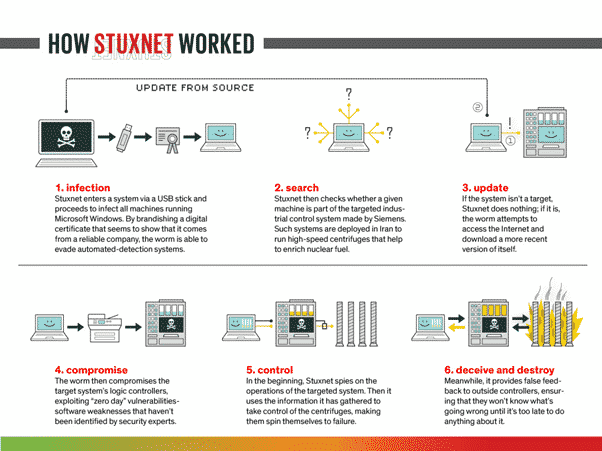
Malware development groups involved in this process are often state-sponsored. In addition, some companies openly develop advanced surveillance malware and sell it to governments. One example is NSO Group, which sells the Pegasus threat.
Malware targeting popular computing platforms
Malware tends to have best coverage on the most popular computing platforms. On desktop and laptop computers, Windows-based systems have the most malware threats. In the mobile market, Android is the market leader and is the target of most malware families. Finally, Internet of Things (IoT) malware is on the rise, targeting poorly secured smart devices, which are mostly Linux-based.
Malware Prevention Challenges
Relying on outdated security solutions can result in a low malware detection rate (less than 70%). Many threats evade detection and protection measures to reach users due to the following challenges.
Disguised Malware
Attackers pack malicious files to avoid detection using encryption, compression, or modified formats. Packed malware is difficult for antivirus and malware analysis software to identify.
Signature-Based Detection Is Not Enough
Malware analysts often rely on signatures and standard AV scanners to detect malicious content (i.e., static analysis). However, this approach is not comprehensive, allowing some threats to evade detection. Hackers can modify code to create a new, unrecognized signature. Malware databases will not include new threats with unknown signatures.
Sandboxing Is Inefficient
Dynamic scanning is a popular alternative to static analysis, identifying malicious code by executing it in a sandbox. However, this process is often slow, and some threats can bypass the sandbox.
For instance, some malware requires command-line execution or has a sleep period before executing commands. A traditional sandbox cannot run these malware types.
How Anti-Malware Technology Works
Signature-Based Malware Detection
Signature-based malware detection works by comparing the digital signature of a piece of software or file against a database of known malware signatures.
When a piece of software or file is suspected of being malicious, the antivirus software will first calculate its digital signature. This is typically done using a cryptographic hash function, which produces a unique string of characters (the signature) based on the content of the file.
The signature is then compared against a database of known malware signatures. If there is a match, the antivirus software will flag the file as malicious and take appropriate action, such as quarantining or deleting the file.
Pros and cons: The main advantage of signature-based malware detection is that it can quickly and accurately identify known malware. However, it is not effective against new or unknown malware, as the database of known signatures does not yet contain a signature for the new malware.
Behavior-Based Malware Detection
Behavior-based malware detection works by monitoring the behavior of a piece of software or file to determine whether it exhibits characteristics that are typical of malware.
When a piece of software or file is suspected of being malicious, the antivirus software will begin monitoring its behavior. This typically involves tracking the actions that the software or file takes on the system, such as creating new files or modifying existing ones, and comparing them against a set of known malware behaviors.
If the software or file exhibits behavior that is consistent with known malware, the antivirus software will flag it as malicious and take appropriate action, such as quarantining or deleting the file.
Pros and cons: An advantage of behavior-based malware detection is that it can identify new or unknown malware, even if it does not have a known signature. This is because the detection is based on the behavior of the malware, rather than its signature. A disadvantage of behavior-based detection is that it can generate false positives, where benign software is mistakenly flagged as malware.
Recursive Unpacking
Recursive unpacking involves unpackaging, or decompressing, a piece of software or file multiple times to uncover any hidden malware that may be embedded within it.
When a piece of software or file is suspected of being malicious, the antivirus software will first attempt to unpack it using a decompression or decryption algorithm. If the software or file contains multiple layers of packaging, the antivirus software will continue to unpackage each layer until it reaches the innermost layer, scanning the content of each layer for known malware signatures.
If it finds any, it will flag the file as malicious and take appropriate action, such as quarantining or deleting it.
Pros and cons: Recursive unpacking can uncover malware that uses packers, compression algorithms, or similar methods to evade detection by signature-based detection systems. However, it can be computationally intensive, and may not be suitable for real-time detection of malware in high-throughput environments.
Next-generation Sandboxing
Sandbox technology is a method used by antivirus software to detect malware. It involves running suspicious software or files in a controlled environment, known as a sandbox, to observe their behavior and identify any malicious activity.
Modern sandbox solutions can run the suspicious software or file in a virtual machine, which is a software-based emulation of a computer system. This allows the antivirus software to observe the behavior of the software or file in a controlled environment, without exposing the host system to any potential harm.
Another technique is processor tracing, which involves monitoring the instructions that the suspicious software or file executes on the host system’s processor. This allows the antivirus software to identify any potentially malicious instructions, such as those that attempt to modify system files or download additional malware.
Pros and cons: Sandbox technology is effective at detecting malware that is designed to evade detection by other methods, such as signature-based detection or recursive unpacking. While modern sandbox techniques can analyze files in seconds, rather than minutes for traditional solutions, they are still computationally intensive, and less suitable for real-time detection.
Malware Attacks Protection and Prevention Best Practices
Install Anti-Malware Software
While this sounds obvious, organizations can find it difficult to deploy anti-malware solutions on all their devices. Employees commonly use personal devices to access corporate systems, and those devices might not have adequate anti-malware protection. Some computing systems or devices may not support installation of anti-malware solutions —for example, legacy systems or internet of things (IoT) devices.
The first step to protect against malware is to ensure that all devices have strong anti-malware protection installed, and devices that don’t have it should be severely limited in their ability to access the network and sensitive systems.
Learn more in our detailed guide to anti-malware protection
Keep Software Updated
Software vendors regularly provide patches and updates to address new vulnerabilities as they arise. Many of these vulnerabilities could result in attackers deploying malware in the corporate environment.
It is critical to check for and install all new software patches—this applies to operating systems, software tools, browsers, and plug-ins. It is advised to automate the patch management process to ensure updates happen quickly, and reduce the burden on IT teams.
Secure Browsers
Users are often infected by malware via their web browsers. A primary method for causing users to download malware is malicious pop ups—malicious sites and adware programs can create pop-ups to deliver malware or spyware to a user’s device, hijack the browser session, or perform other malicious actions.
Other commonly exploited weaknesses in web browsers include malicious redirects, insecure plugins, DNS attacks, and insecure use of stored passwords and form data.
There are two main ways to protect against these threats. Use technological solutions that can limit impact, such as browser isolation and web filtering, and educate users on safe browsing habits.
Regulate Networking and Storage
These methods can help block common threat vectors that lead to malware infection:
- Install or implement firewalls, intrusion detection systems (IDS) and intrusion prevention systems (IPS).
- Do not allow users to connect USB drives or use unsanctioned cloud storage services.
- Close unused ports and disable unused communication protocols.
- Delete inactive user accounts and limit permissions to active accounts according to the least privilege principle.
Implement Email Security and Spam Protection
Email is an essential business communication tool, but it is also a common malware distribution channel. To reduce the risk of infection:
- Ensure all incoming email messages, including attachments, are scanned for malware.
- Use a sandbox to safely “detonate” suspicious files to protect against unknown threats.
- Set up a spam filter to reduce spam and inappropriate or suspicious emails.
- Only allow users to click company-approved links
- Clearly warn about emails that come from non-company or unknown email addresses.
Learn more in our detailed guide to prevent malware attacks.
Preventing Malware with Perception Point
Perception Point developed next-gen static and dynamic engines that detect and prevent any attempt to deliver malware.
These dynamic and static engines are broken up into several elements: In the front line stands the Recursive Unpacker which extracts all files and URLs transferred, thus uncovering and thwarting evasion techniques. Next is the Threat Intelligence layer – The best-in-class intelligence sources coupled with internally developed engines scans all content to identify any “known” malware. Following the threat intelligence, is a stack of the leading Anti-virus engines in the world in addition to Perception Point’s Signature Analysis engines for highly complex malware. The last piece of the “Everyday Malware” stack, is Perception Point’s phishing engines which use in-house build image recognition capabilities to prevent any type of URL based malware delivery.
New, sophisticated malware attacks all rely on the usage of an exploitation technique. This means that prior to any advanced malware release, the attacker will try to use an exploit to set the ground ready for installing one of any millions of malware options he has in his hands.
Perception Point knows how attackers think. This is why we invented the HAP – a proprietary next-gen dynamic engine that has visibility into the exploit level. In other words, instead of chasing the many malware out there, we “cut off the root” and prevent the malware from even being delivered, not to mention from running.

Malware (malicious software) is designed to disrupt the normal functioning of a computer or other device. It is an umbrella term for viruses, trojan horses, and other destructive computer programs that attackers use to compromise systems and networks, sabotage systems, and gain access to sensitive information.
There are many types of malware, including:
– Virus
– Worm
– Trojan
– Ransomware
– Spyware
– Adware
– Botnet
– Fileless Malware
Many threats evade detection and protection measures to reach users due to the following challenges including:
– Disguised Malware
– Signature-Based Detection Is Not Enough
– Sandboxing Is Inefficient
– Signature-Based Malware Detection
– Behavior-Based Malware Detection
– Recursive Unpacking
– Sandboxing
There are 5 best practices for preventing malware attacks:
– Install Anti-Malware Software
– Keep Software Updated
– Secure Browsers
– Regulate Networking and Storage
– Implement Email Security and Spam Protection
See Additional Guides on Key Cybersecurity Topics
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of cybersecurity.
What Are TTPs
Authored by Exabeam
- What Is Lateral Movement and How to Detect and Prevent It
- What Are TTPs and How Understanding Them Can Help Prevent the Next Incident
- 9 Lateral Movement Techniques and Defending Your Network
Zero-Day Attack
Authored by Cynet
- Zero-Day Attacks, Exploits, and Vulnerabilities: A Complete Guide
- Zero-Day Attack Prevention: 4 Ways to Prepare
- What is a Zero-Day Exploit?
AWS Backup
Authored by N2WS
























