Phishing is cybercrime’s oldest threat and since it appeared in the mid 1990s, continues to be one of the most trending attacks on individuals and organizations alike.
One of the reasons phishing remains so pervasive is that cybercriminals have been continually perfecting their abilities over time, utilizing techniques that make deploying phishing attacks at scale relatively easy.
In this blog post we’ll discuss recent players on the cyberattack scene: script kiddies, and their methods that make phishing so easy, even for the inexperienced.
What is a Hacker
Often, the word hacker conjures up imaginary worlds populated by malevolent, hooded pirates. Hackers are often perceived as a shadowy, secretive or even marginal grouping, which certainly helps to fuel wild rumors about them.
This imagery is fueled by pop culture (in TV series like Mr Robot) to online image banks, where it is hard, often impossible, to find a picture of a hacker that is not an anonymous figure in a black hoodie.
However, there is actually a range of hacker profiles. There are black hats – cybercriminals attracted by bank fraud – and white hats – hackers who promote ethics and see themselves as cyber-activists rather than cybercriminals.
And somewhere in the middle between these two opposing camps, there are grey hats. Microsoft has invented its own term, blue hats, to refer to cybersecurity experts tasked with repairing vulnerabilities in security systems.
However, this article isn’t about black hats, white hats, grey hats, blue hats or even the well known hackers such as Kevin Mitnick, Brett Johnson, Julian Assange or Edward Snowden.
In this post, we’ll be discussing a prevalent group of hackers, known as script kiddies, that are wreaking havoc for organizations and individuals.
Script Kiddies
The term “script kiddies,” derives from a Carnegie Mellon report prepared for the U.S. Department of Defense in 2005:
“The more immature but unfortunately often just as dangerous exploiter of security lapses on the Internet. The typical script kiddy uses existing and frequently well known and easy-to-find techniques and programs or scripts to search for and exploit weaknesses in other computers on the Internet—often randomly and with little regard or perhaps even understanding of the potentially harmful consequences.”
What is so special about script kiddies compared to their more experienced counterparts? They have at their disposal a large number of effective, easily downloadable programs capable of breaching computers and networks without barely needing to know how to code.
It turns out that it’s not so hard to run a simple phishing exploit that any script kiddie could do. I sat down with our Incident Response Team, whose focus at Perception Point is to understand whether incoming emails and their associated content, file attachments or URLs are malicious, how they behave, and how they infiltrate customers’ inboxes in the first place.
Before the Phish
Before deep diving into the attack chain, let’s review 3 general principles about hacking.
Principle #1: Cybersecurity attacks are all about finding the weakest link in the chain. In most instances, human beings, unlike technology or processes, are actually the weakest link. People will make the same mistake multiple times because they are unpredictable and in many cases act from emotional queues. At the core, the inability to find a way to prevent all potential victims from making the same mistake more than once makes them the weakest link in the chain and this is exactly what hackers will exploit.
Principle #2: In most news stories about cybersecurity attacks, we hear all about the breach, about how much damage was incurred from the amount of sensitive data exposed, financial loss, or reputation damage. In most cases there will be an analysis of how the attacker could have potentially gained access to the system but not about the many steps taken, before actually breaching the system.
Principle #3: Before any breach, most attackers will do some form of information gathering on their target. In today’s socially connected world, it is very easy to find information about anyone online without doing any hacking at all. That information then can be used in a variety of ways, for example:
- The attacker can decide to impersonate an employee within an organization to conduct a phishing campaign and harvest credentials in order to gain access to all of the organization’s systems. The easiest way to do this would be through some form of social engineering, and then a phishing (or if targeting a specific person which is known as spear-phishing) campaign via email.
- The attacker can also decide to target an endpoint, .e.g., a computer or mobile device. One popular way to do this is through a technique known as reverse shell in which the attacker uses a bit of social engineering to get the target to download software so that they can access the victim’s device remotely, and ultimately gain entry to the organization that way.
Using Existing Tools and Setting Up Your Phishing Attack
In this article, we’ll take a look at some readily available tools available online that require zero programming knowledge in order to conduct a phishing campaign.
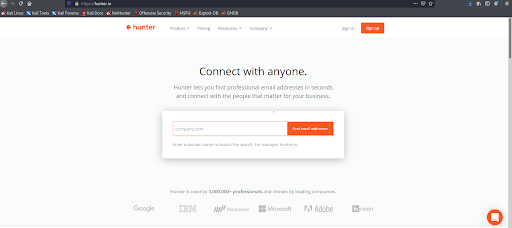
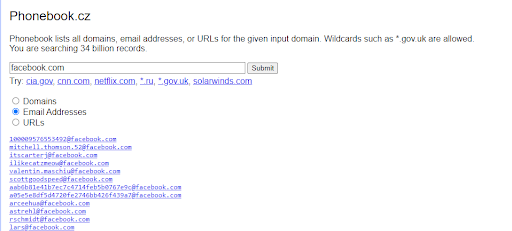
Step 1: Understanding Domain and Email Conventions
Using tools such as Hunter.io and Phonebook.cz, you can determine the domain and email conventions of the organization you are targeting. For example, we entered https://www.perception-point.com and quickly determined that the email convention at the company is {firstname}.{lastname}@perception-point.com.
Step 2: Generating Email Addresses
Now knowing how email addresses are structured, we can use Github Crosslinked. The program will look up every person associated with the organization via LinkedIn and then generate an entire list of email addresses to send a phishing email to.

Step 3: Time to Go Phishing with GoPhish
Armed with the list of targets, now we can go phishing. We can use GoPhish, which is essentially a one-stop-shop for conducting a phishing campaign.
1: Linking GoPhish with an SMTP Server
SendinBlue is an email marketing platform for sending and automating email marketing campaigns. Unlike other email marketing platforms, which requires you to authenticate your organization’s domain, anyone can use SendInBlue with zero authentication requirements. Within SendInBlue, we generated the SMTP server name, and port.
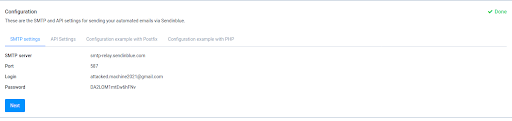
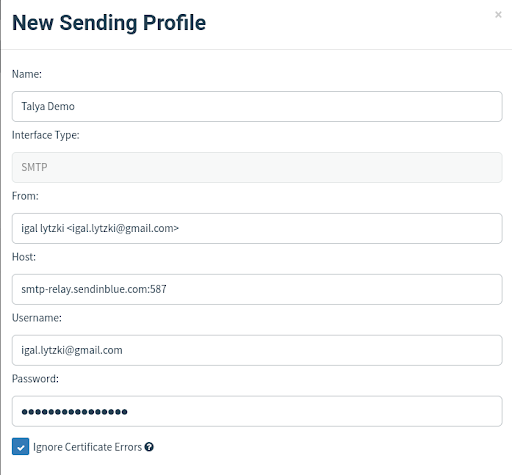
2: Spoofing the Sender
Now GoPhish has the ability to send emails using SendInBlue’s SMTP server. Here is where we configure who the email is “supposed” to be coming from. In this instance we are sending it “from” Igal. If you want to make it look like it’s coming from the CEO of the company, all you need is their email address and put it in the “From” field.
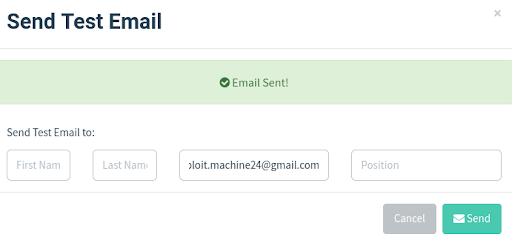
3: Send a Test Email
You can even send a test email within GoPhish to check your configurations.
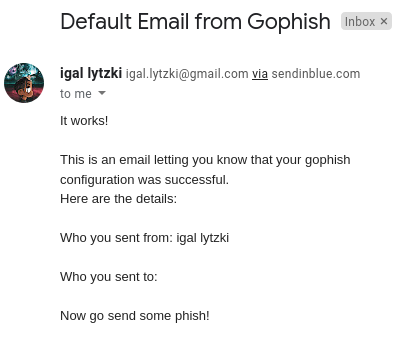
And it works! We wanted to make it look like we were sending an email from Igal Iytzki, the only notable difference is that it says it’s via sendinblue.com.
4: Upload the victims email list
Now we can upload the entire list of email addresses that GitHub CrossLinked generated.
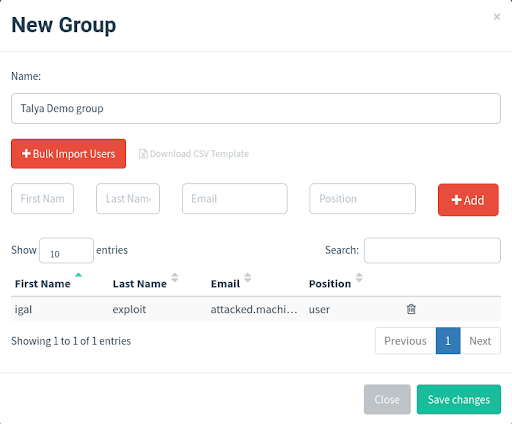
5: Perfecting the Spoofed Brand
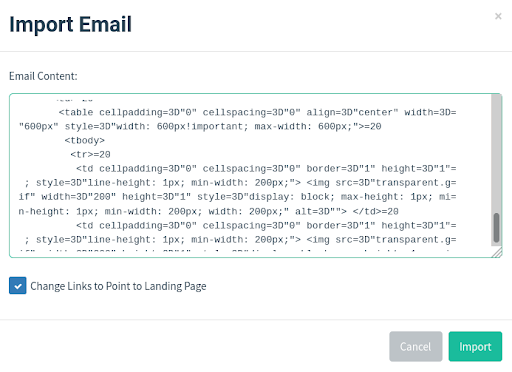
Let’s say we want to harvest credentials of the targets’ Facebook accounts. So we want to send them an email that looks like it’s coming from Facebook. By importing a legitimate email from Facebook requesting its users to reset their password, we can create a spoofing email that looks almost indistinguishable from the real thing.
Notice the “Change Links to Landing Page,” GoPhish will automatically change all the links within the email to point to the “fake” reset password page (otherwise known as a landing page).
After we imported the Facebook page, this is how it looks like in the email template editor.
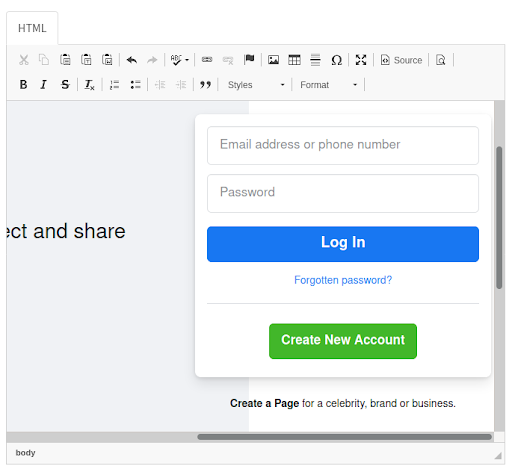
Step 4: Creating the Phishing Site
Now we need to create the actual spoofed Facebook reset password website page. There are a few ways to do this. More advanced attackers will buy a domain that is almost the same as the legitimate site, e.g., face-book.com as opposed to facebook.com. Another way is to use a tool called ZPhisher. Just press on Option 1, and it will generate the spoofed reset password page, and will also allow you to choose where you want to host it, either Ngrok or CloudFlare.
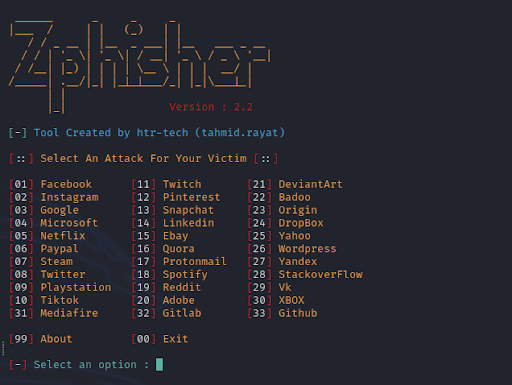
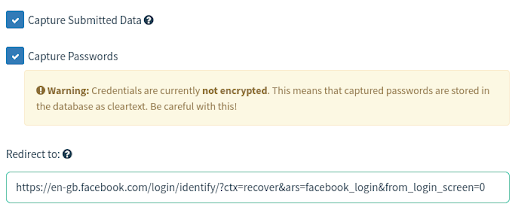
In GoPhish, you can configure it so that the spoofed reset password landing page captures any submitted data and passwords that the target enters and also redirect them to a legitimate page within the next of the reset password flow so they do not suspect that their data has been stolen.
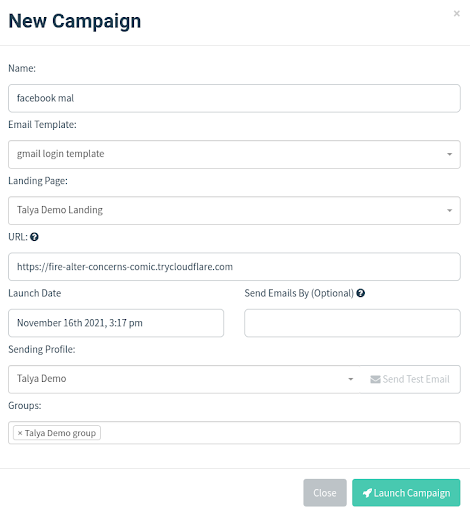
Step 5: Timing the Campaign
You are now ready to send out your phishing campaign. You can schedule when exactly you want the email to go out, as timing of the campaign is another crucial factor in its success. Should the email be sent out when members of the organization are just getting into the office, or during their lunch break, or perhaps right before they sign off for the day?
New Trend: GenAI Attacks
The first half of 2023 has witnessed a concerning trend—the emergence of generative AI-based cyber attacks. Cybercriminals are leveraging the power of GenAI platforms (ChatGPT, Google Bard, etc.) to create increasingly sophisticated and deceptive malicious content. This trend poses significant challenges for organizations in terms of threat detection and mitigation.
GenAI is fueling social engineering attacks like business email compromise (BEC) and phishing.
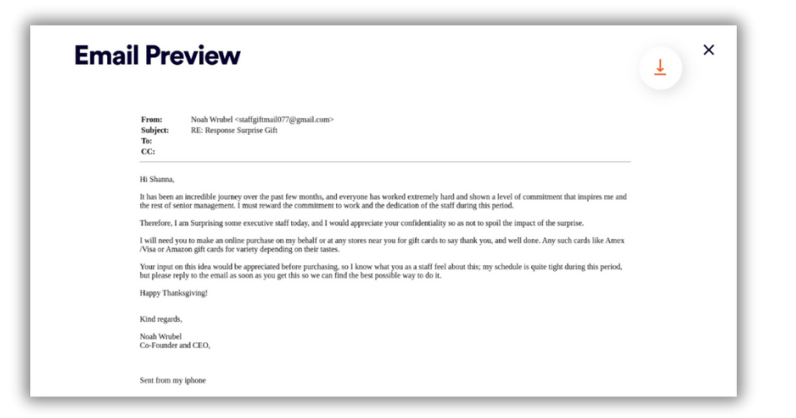
BEC attacks involve cybercriminals impersonating legitimate business stakeholders via fake emails to request money or confidential data from employees or business associates. These impersonation-based attacks are increasingly difficult to detect as attackers exploit the vulnerability of employees, who are often preoccupied and easily tricked. While legacy security systems like secure email gateways were designed to prevent malicious files and URLs, BEC attempts primarily rely on text-based social engineering tactics, rendering traditional email security solutions largely insufficient.
Throughout H1 2023, BEC attacks grew by 20% per user. This increase may be partly attributed to cyber attackers’ rapid adoption of AI-based tools in their BEC efforts.
Adversaries utilize GenAI tools to craft convincing content, impersonate trusted individuals or vendors, and increase the likelihood of successful BEC attacks. It is not only extremely difficult for humans to distinguish between legitimate and AI-generated content, but also for many cybersecurity solutions.
To combat this rising threat, Perception Point has developed an LLM-based detection engine to identify BEC attacks generated by LLMs. This innovative approach empowers organizations to strengthen their defenses and detect these sophisticated attacks, mitigating the potential financial losses and reputational harm associated with BEC incidents.
As the trend of GenAI-based cyber attacks continues to evolve, organizations must remain vigilant and proactive in their cybersecurity measures. By leveraging cutting-edge technologies and methodologies like Perception Point’s LLM-based detection, organizations can bolster their resilience and protect their critical assets in the face of these sophisticated threats.
Conclusion
The hackers’ motivations vary – the thrill of gaining entry to systems and/or data they shouldn’t be privy to? Monetary gain? Political havoc? Using their skills for good in the case of white hats?
The fact that anyone can become a “hacker”, albeit a script kiddie if they put their mind to it, opens the door to even more hackers and increases the scope of potential damage. There are enough tools available on the web, and not just the dark web, to conduct simple exploits such as the phishing campaign we demonstrated above. What does this mean for individuals and enterprises alike? While we should be worried about “big name” attacks that appear in the news every so often, we should be equally wary of “simple” hacks that can happen at any time of day, to any of us.
While this mantra is repeated over and over again, we should never tire from its message: be vigilant, be aware. Double, triple check links before clicking on them. Never download files from or give credentials to unknown sources. It doesn’t take much to exploit human weaknesses.

Here’s some related content you may enjoy: How to Prevent Phishing
Hackers are often perceived as a shadowy, secretive or even marginal grouping, which certainly helps to fuel wild rumors about them. However, there is actually a range of hacker profiles. There are black hats – cybercriminals – and white hats – hackers who promote ethics and see themselves as cyber-activists rather than cybercriminals. And somewhere in the middle between these two opposing camps, there are grey hats. Microsoft has invented its own term, blue hats, to refer to cybersecurity experts tasked with repairing vulnerabilities in security systems.
Step 1: Understanding Domain and Email Conventions
Step 2: Generating Email Addresses
Step 3: Time to Go Phishing with GoPhish
Step 4: Creating the Phishing Site
Step 5: Timing the Campaign























