While hackers have always been lurking around in one way or another, the ongoing pandemic and adaptation to remote roles paved the way for cyber felons to further increase attacks on enterprises.
Businesses constantly face security challenges, including the need to protect themselves against ever increasing cyber threats, with the most common being phishing and malware attacks. Although some organizations are aware of such dangers to some extent, not many understand that the consequences can lead to complete business disruption, including loss of profit, customers, or even stolen data.
No matter how informed employees of an organization are, it can still be difficult to foresee every potential threat. For this reason, adopting quality cybersecurity measures and tools, such as Prevention-as-a-Service solutions, should become an integral part of an enterprise.
To discuss cyberattacks and their prevention, we are joined here today by Karen Krivaa, the Chief Marketing Officer of an enterprise that offers advanced cyber threat protection solutions called Perception Point.
Tell us more about the story behind Perception Point. Which company achievement are you most proud of?
Perception Point was founded by three innovators who served in elite cyber units in the Israeli Intelligence Corps. They initially developed a patented technology focused on Zero-days and N-days; highly dangerous advanced persistent threats (APTs), which are extremely hard to detect and even harder to prevent. The HAP™ (hardware-assisted platform) was born. HAP is a dynamic scanning engine (next-gen sandbox) that detonates content on Windows and macOS, leveraging CPU Tracing to rapidly detect malware and zero-day attacks at the exploit stage, without relying on known signatures or historical data. Each file is dynamically scanned in seconds, compared to legacy sandboxes that take up to 20 minutes.
Cloud migration and digital transformation trends began changing the way companies do business and how people communicate (leveraging 5–20 communication channels). Combining these trends with the increasing aggressiveness and growing numbers of cyberattack techniques, influenced the company’s offering in four ways:
- Development of Perception Point’s SaaS-based Advanced Threat Protection System – cloud-native from its original design
- Development of a holistic offering with 7 layers of advanced protection (the HAP as one of them) providing rapid prevention of any content-based attack across all collaboration channels – email, cloud applications, and cloud storage
- Ability to dynamically scan emails, files, embedded files, and URLs in seconds at an unlimited scale
- Building an Incident Response service fueled by combining machine learning, automation, and close engagement with cyber experts
In 2021, the company tripled annual recurring revenue and customer base for the second year in a row and has been recognized by Gartner for three years running as a leading Integrated Cloud Email Security Solution (ICES).
Can you tell us a little bit about what you do? What set of tools do you use to detect threats?
Perception Point is a Prevention-as-a-Service company, offering fast interception of any content-borne attack across all collaboration channels, including email, cloud apps, cloud storage, and messaging platforms. The solution prevents phishing, BEC, ATO, spam, malware, Zero-days, and N-days well before they reach enterprise users. Cloud-native by design, it is a SaaS solution and is deployed with a few clicks in just minutes, with no change to the enterprise’s infrastructure, and requires zero fuss from IT teams.
Perception Point provides the most effective detection leveraging 7 layers of detection, including static and rapid dynamic scanning that combines the HAP engine, as mentioned above, for APTs and zero days, innovative software algorithms, and computer vision to detect and intercept threats in seconds. With the scale of the cloud and the ability to scan in near real-time, the solution can dynamically scan 100% of emails, files, embedded files, and URLs for best protection – eliminating the organization’s blind spots.
Advanced detection layers running on all email and collaboration channels are combined with an included Incident Response service at no additional cost. This gives the customer access to a service that combines machine learning, automation capabilities, and our cybersecurity experts, so that every incident is analyzed and managed efficiently. The service is an extension of the customer’s SOC team and ensures continuous optimization of the system’s detection rates. Management overhead is greatly reduced and customers can save up to 75% of their SOC time.
This enables Perception Point to not only intercept more incidents prior to compromising end-users but also to fully and rapidly contain and remediate any threat.
How do you balance security and user-friendliness when it comes to collaboration channels?
CISOs want to protect their organization as well as their customers, and at the same time, they cannot disrupt their business processes. To ensure that malicious content is intercepted before it causes damage, our advanced threat protection (which delivers over 99.95% detection rates), can scan 100% of content and is also extremely fast. Because no one wants to wait for an email or for a file to arrive via a collaboration channel, and online services whose promise is “real-time” cannot afford to use inefficient and slow threat protection, the accuracy combined with the speed provides the required service.
Although no malicious email, file, or URL should get to an end-user, no system is 100% foolproof. For this reason, we have designed the product to include an Incident Response service at no added cost. Cyber experts analyze incidents 24/7 to ensure that if something bypasses the system it is immediately remediated across all protected channels. New rules are urgently created to incorporate the new threat intelligence to intercept this type of attack the next time it is encountered. End-users can upload any file or URL that they think may be malicious to be checked by the system and the Incident Response service. Customers appreciate this service which saves them time and provides the best protection.
As a SaaS application with an intuitive user interface, deployment is accomplished in just a few minutes with no need to change the network infrastructure. There are no 300-page manuals, and customers receive the most updated software without the need to touch the system.
How do you think the pandemic reshaped cybersecurity? Have you implemented any new features as a result of the recent global events?
The pandemic has accelerated the already strong digital transformation trend, making way to innovation, but also a larger attack surface. Many cloud apps and services allow the sharing of content between customers and companies. From digital payments, online insurance claims, automated processes, CRMs, media storage and sharing, and more the adoption of digital services and the risks of content-borne attacks through these channels have drastically increased.
Remote work has also accelerated the adoption of collaboration and messaging apps and access to them from outside the organization – including OneDrive, SharePoint, Box, G-Drive, Slack, and more. Organizations are blind to the potentially malicious content that can be uploaded and shared.
Perception Point has protected email and cloud collaboration apps, cloud storage, and more from before the pandemic. And in 2021, we added a one-click deployment to protect AWS S3 Buckets which are increasingly used by medium and large enterprises to store files that serve digital services and require scanning in almost real-time. The Advanced Threat Protection for S3 is also available on the AWS Marketplace.
The addition of dynamic scanning of MAC files was also released due to the growing number of attacks that can penetrate macOS.
Also, with the growing usage of emails and corresponding internal threats, BEC and ATO attacks, Perception Point added the ability to scan internal emails.
In general, the threat landscape has evolved over the pandemic and all detection layers are enhanced and improved with advanced proprietary algorithms and AI techniques.
When it comes to cyberattacks carried out by email, what are the most common ones?
Phishing is one of the oldest tricks in the cyber attacker’s playbook. An attack uses URLs, files, and social engineering techniques to deceive its victim. These attacks are becoming very sophisticated and cyber criminals are using available phishing toolkits to build their campaigns. They also employ evasion tactics that make them more difficult to detect. Spear Phishing is when the attacker targets specific people in an organization. Whale Phishing is when one of the most important people in the organization is the target.
Some very well-produced phishing campaigns that we have intercepted include a recent one spoofing PayPal. See the initial email below:
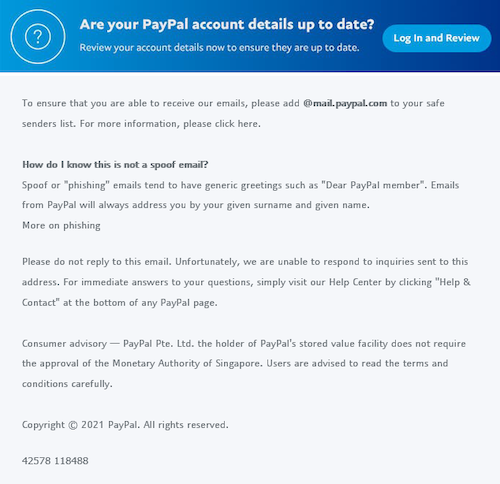
Then comes the phishing email and the request for the victim’s credentials:
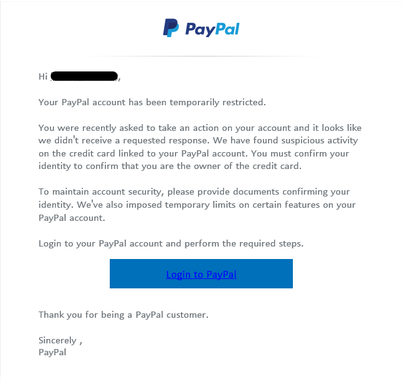
And they even include a security check:
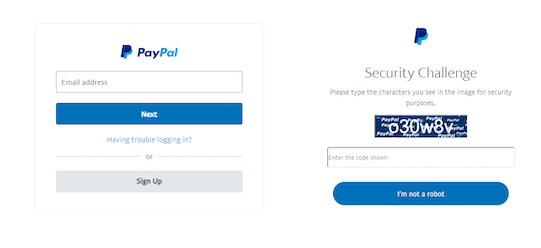
BEC is also on the rise. BEC (Business Email Compromise) is similar to phishing emails but does not have a payload such as a URL or attachment. They are looking for a fast payoff – and are recognized as the costliest type of email attack. The attackers can leverage Account Takeover (ATO) or impersonation (ie. spoofing a CEO) and combine that with knowledge of the company to trick employees to wire money or data or to change bank account information for pending payments.
We should not forget malware which is a huge threat to organizations. Malware includes viruses, ransomware, spyware, worms, trojans, keyloggers, and more. It is transported in files and URLs. Clicking on the Excel file that you think has a new list of orders can actually be the start of a malware kill chain.
We’ve published a lot of information on the many attacks that we have intercepted, and they can be viewed here.
What precautions would you suggest companies take to protect against such threats?
Specifically for emails and collaboration applications, advanced threat protection solutions that cover all threats and multiple channels are the first line of defense.
As attacks become more sophisticated, legacy email security technologies can no longer provide the protection that organizations need. It is therefore imperative that organizations ensure the following:
Next-gen advanced security solutions that:
- Are equipped with the ability to detect packed programs that hide malware
- Do not rely only on file signatures
- Leverage Image Recognition to validate if any URL is a legitimate site
- Use Threat Intelligence that combines multiple sources with internally developed algorithms that scan URLs and files in the wild to warn about potential or current attacks
- Use next-gen technology that surpasses slow and inaccurate sandboxes, so that the malicious email, file, or URL never reaches the end-user
- Are agile to adjust rules and logic to handle new attack vectors
Leverage an Incident Response service that can:
- Monitor, analyze, and report all email security incidents 24/7
- Provide rapid alerts and analysis of malicious attempts
- Optimize the security system’s engines for advanced scenarios in an agile manner
Continue to educate and train your employees about email security and the risk of clicking on unknown URLs and attachments
- Better safe than sorry. Avoid clicking on links that you’re not 100% sure about, and even if you end up clicking on a link from within an email, inspect the website thoroughly even if it seems to display non-malicious content.
Do you feel like different sectors (for example, financial, healthcare, etc.) should have security features tailored specifically for them or should such solutions be universal across industries?
With the growing transition to the cloud, real-time collaboration and real-time services are key to every business. In specific industries such as insurtech, fintech, and providers of online services, digital transformation is changing the way people do business. Sadly, along with it, new opportunities for security attacks emerge. Companies across industries require the ease of deployment and usage that our SaaS solution delivers. They all desire the best protection which is provided by the ability to deeply scan all emails, files, embedded files, and URLs in seconds without slowing down emails and supporting real-time applications and services to meet customer SLAs.
The unique approach of combining a SaaS service with an Incident Response team provides the best continuous protection as well as containment and remediation when necessary for all customers, including enterprise and SMBs across all industries.
There are indeed some industries that have stricter compliance requirements and these can include, how and if the content is stored, GDPR, SOC-2, and many more.
Talking about individual users, what security measures do you think everyone should invest in?
Individuals should be vigilant in checking for the red flags discussed above, and when in doubt – do not click!
Would you like to share what is next for Perception Point?
Our mission is to protect organizations and we continue to develop the most advanced algorithms to deliver unmatched detection. We are also adding new channel support and continuing to foster collaboration with endpoint vendors. We are always optimizing the efficiency and speed of the solution to meet our customers’ business needs – keeping them happy and safe.
This article originally appeared in Cybernews by Kristina Jarusevičiūtė on February 8th, 2022.























