X-Ray + Falcon
360-degree Threat Remediation.
Our X-Ray deployed on top of the CrowdStrike Falcon endpoint protection delivers the fastest and most comprehensive incident containment on
the market. Transform your threat remediation today.
Available in the CrowdStrike Store.
For Falcon clients, the X-Ray is a game changer in preventing the spread of advanced attacks across content-sharing channels, post endpoint detection.
CrowdStrike VP Product
One point of failure – an infinite number of ways to damage the organization. Stop the attack at its source, in no time.
Vast damage can be caused by even one successful attempt and in today’s multi-channel world, it’s nearly impossible to manually quarantine every attack before it spreads.
X-Ray + Falcon ends the cat and mouse game.
With a seamless integration between the two, the instant Falcon detects an incident on the endpoint, the X-Ray scans all content-exchange channels (email, CRM, cloud storage, etc.) to identify where else the incident spread, which users have been affected and prevent further transmission.
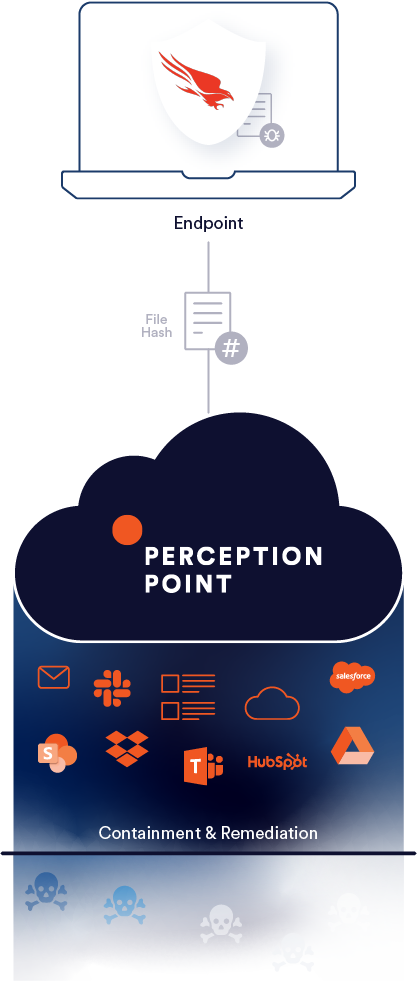
How it works
Seamless integration between the two systems ensures ultra-efficient containment time.
Proofpoint, like many other email security vendors, is based on outdated technologies, such as Sandboxing. See below how our unique technology and built-in agility enable us to outmatch Proofpoint in all aspects.
- Falcon sends hashes of malicious files discovered at the endpoint to the X-RAY.
- The X-RAY will automatically scan all organizational content-exchange channels to map the extent of the breach across users.
- Within minutes, the SOC team will receive a full channel audit.
- The X-RAY will actively remediate and contain the incident to prevent further spread.

Watch the Demo
Lightning Fast Containment. 360-degree Coverage.
100% Automated
Automated incident containment and remediation across all users and channels.
Max Speed & Scale
Lightning speed scans and unlimited scale ensures the full collaboration network is fully analyzed. No path is left unscanned.
Source-Agnostic
Source-agnostic, the X-Ray can analyze and contain the threat regardless of where it originated.
Deploys in Minutes
Deployed on the cloud, integrates with Falcon in minutes, with zero fuss to the IT team.
Full Threat Coverage
Contain every type of technique including Zero-days, N-days, BEC, phishing, spam, malware, and evasion.
Expert Insights
Access to experienced cybersecurity personnel that provides in-depth post-breach analysis.
TALK TO SALES























